Security
Exploring The Roles Of The Blue Team, The Red Team, And The Purple Team In Cybersecurity
By Jennifer Watkins
Are you a leader building a cohesive security function at your company? Or perhaps you’re an employee looking to understand security teams? This article is for you.
After introducing the fundamental concepts of the Blue Team and Red Team, this article explores specific tools employed by each. The roles of Blue and Red Teams are examined in detail, featuring a real-world scenario orchestrated by a Red Team, complemented by an imagined Blue Team response. This practical example provides valuable insights into the decision-making processes of companies regarding security.
Furthermore, the article discusses a Purple Team and what it brings, emphasizing the significance of team culture and company posture. Serving as a liaison between Blue and Red Teams, Purple Teams actively participate in both offensive and defensive strategies, working collaboratively towards the shared objective of protecting assets and human lives.
Let’s kick things off!
Blue Team: The Defensive Masters
Imagine a world without resilient defense. In competitive sports, coaches often use the phrase, “defense wins games.” This can also be true of the defense of Blue Teams. Their defense impacts the success of the entire team. Critical components like meticulous logging, threat analysis, and improvement plans serve as the backbone of cybersecurity. These components can help prevent predatory threat actors from dominating both the physical world and technological infrastructure. Without these safeguards, both the internet and physical world would transform into a frightening and largely unusable space, leaving companies vulnerable and defenseless.
The Blue Team is the defensive unit,protecting organizations against internal threats. They perform threat assessments, risk evaluations and identify vulnerabilities in order to strengthen security posture and shield organizations from attacks. Through these methods, Blue Teams generate new found weaknesses, comprehensive reports, and solutions for the organization, equipping companies with the necessary protection and response measures.
Blue Team tactics challenge Red Teams to devise successful attacks, creating an ongoing cycle of action and reaction. This dynamic cultivates growth, enhances awareness, and augments knowledge on how to effectively combat cybercriminals.
Blue Team Tools and Strategies
Defensive strategies are not improvised; they require rigorous tools and the implementation of standard policies and procedures. Having a comprehensive understanding of available tools and their uses empowers leadership to make informed decisions crafted to their specific security needs. Below are some key tools that support the defensive capabilities of a Blue Team.
Blue Teams can harness simple yet effective tools such as antivirus software to defend systems and networks against viruses and remove malicious elements. Regular updates are essential to maintain the effectiveness of antivirus software, and Blue Teams can ensure consistency by implementing verifiable, automated updates. Additionally, integrating intrusion detection and protection software or hardware (IDS/IPS) can safeguard the network, block suspicious activities, and alert administrators to potential threats.
A more advanced analysis tool that Blue Teams use, is Security Information and Event Management (SIEM) software. SIEM is a central platform that simplifies the task of storing, analyzing and sorting through large amounts of machine data from various sources throughout an enterprise.
Splunk is a popular SIEM software that monitors files, detects file changes, listens on ports, and runs scripts to collect log data. With the help of Splunk, Blue Teams can efficiently review machine-generated logs, identify suspicious behaviors, discover potential weaknesses, and respond or mitigate effectively.
Blue Teams can also deploy honeypots, a tool crafted to attract attackers into simulated environments where their actions can be observed and analyzed. Honeypots enable Blue Teams to establish controlled and secure environments that lure hackers without causing harm to systems or people. The term ‘honeypot’ suggests something alluring yet problematic: a “sticky situation” for intruders. These honeypots are intentionally designed with vulnerabilities and weaknesses to attract attackers. For example, Blue Teams intentionally configure environments with weak authentication and authorization management. When the attackers infiltrate the honeypot, the Blue Teams study their methods and strategies.
While entrapment is illegal, honeypots do not fall under this category. They are legitimate defensive tools employed by cybersecurity professionals to enhance threat detection and response capabilities.
Red Team: Offensive Champions
The Red Team plays a central role in continually improving security frameworks, enabling organizations to stay ahead of evolving cyber threats. By integrating Red Team discoveries into thorough risk management strategies, companies can enhance their resilience against cyberattacks and mitigate potential damages to their operations and reputation.
Red Teaming, also referred to as “ethical hacking,” serves as a proactive approach to uncovering vulnerabilities and tightening security measures before malicious actors exploit them. Ethical hackers are not merely hackers guided by a moral compass, but rather skilled professionals who apply their knowledge and tools to protect digital assets and sensitive information. Their role extends beyond penetration testing; they actively engage in threat modeling, security awareness training, and other critical activities.
Red Team Tools and Tactics
Highlighting the tools and tactics of the Red Team illuminates their impact on a company’s security environment. Red Teams rely on resources such as Metasploit, Cobalt Strike, and social engineering. Examining the functionality of these resources sheds light on the nature of cybersecurity offense.
Metasploit is a pen testing tool that systematically scans networks and servers for vulnerabilities and weaknesses, enabling Red Teams to test and exploit systems using pre-written cybercriminal code. Some common attack vectors include buffer overflow, SQL injection, and remote code execution–all of which involve attackers executing unauthorized code. It is a powerful tool that can also evade detection and it remains a staple toolkit for ethical hackers (and cybercriminals alike), allowing them to map systems, identify and exploit security flaws and execute attacks.
Cobalt Strike is a commercial network attack platform used by both Red Teams and cybercriminals to execute sophisticated attacks. It is known for its capacity to establish connections using servers, giving hackers persistent access between targets and themselves. Once a hacker has exploited a system, Cobalt Strike offers a flexible payload called a ‘Beacon,’ where they can penetrate compromised networks without detection and establish connections to systems. A beacon serves as a backdoor, enabling hackers to remotely control breached systems. Cobalt Strike is also used as a pen testing tool. It includes social engineering and post-exploitation tools, which allow hackers to maintain control over infected systems. Cobalt Strike is unique to Metasploit because it features a team server that facilitates data sharing and project collaboration among colleagues, fostering teamwork and enhancing productivity across the network
Social engineers manipulate human behavior. These tactics include pretexting, where the attacker creates a false identity or scenario to extract information, and phishing, which involves sending fraudulent emails or messages to deceive recipients into revealing sensitive data. Additionally, social engineers may employ baiting, offering enticing incentives or rewards to lure individuals into compromising situations.
An Attack Scenario
A 2020 case study conducted by an independent and global provider of information security solutions called Dinoch, vividly illustrates how Red Teams contribute to a company’s complex security needs. This simulation shows the process of real attackers, providing insight into a genuine attack. Testing systems provide valuable resources to companies.
Red Team Strategies
The first step to any successful plan is reconnaissance. In this case, the Red Team immersed themselves into various sources to gather and analyze information about the target company. Their reconnaissance strategies included researching social media profiles, identifying publicly accessible services, noting the company’s physical address, exploring mobile application platforms, and seeking avenues for remote access.
Through their comprehensive research, the Red Team uncovered crucial insights, including the authentication policies of the target organization. They discovered that employees utilized multi-factor authentication (MFA) to access their emails on shared platforms like Outlook. However, they also found that MFA was not a mandatory requirement for employees.
Despite the absence of a mandate for MFA the Red Team refrained from pursuing a brute force attack. Brute force attacks involve relentless trial and error in attempting to breach a system or network. They initiated a phishing campaign instead. The phishing campaign was intended to compromise systems from an external source. Their goal was to acquire credentials from employees. However, their phishing attempts yielded no credentials. Consequently, they devised a plan B.
Successful attackers often use multiple approaches. Their social engineering plan included the creation of a backdoor, a method to bypass standard security measures and gain unauthorized entry. Two members of Dinoch’s Red Team attended a company event, snatching the opportunity for further exploration with the goal to establish a foothold. While one team member was on the lookout to protect his partner, the other covertly distanced himself from the main event, searching for unlocked and unattended rooms. This strategy resulted in a significant breakthrough: upon discovering an unlocked room, he then had time and space to successfully access the network using his mobile phone. Subsequently, he proceeded to gather more comprehensive and specific information about the company’s operations.
Persistence proved beneficial for this Red Team. Now that the Red Team gained a foothold on the internal network of Dinoch, over several days, the team successfully captured password hashes. Hash functions are one-way cryptographic processes that transform human-readable data into unique strings.
These clever hackers persisted despite encountering another obstacle: complex and lengthy passwords that prevented them from cracking hashes. With the network already compromised, the team pivoted and executed lateral movement by targeting an individual user to obtain their hash and gain access. By obtaining the user’s hash, Dinoch’s Red Team successfully accessed an administrative account without the need to crack the hash. Following their success, they executed another phishing campaign, this time from a trusted source, exploiting their access.
Visualizing a standard attack framework and the concepts used to illustrate this simulation is a simple way to imagine the process and mindset of a hacker:
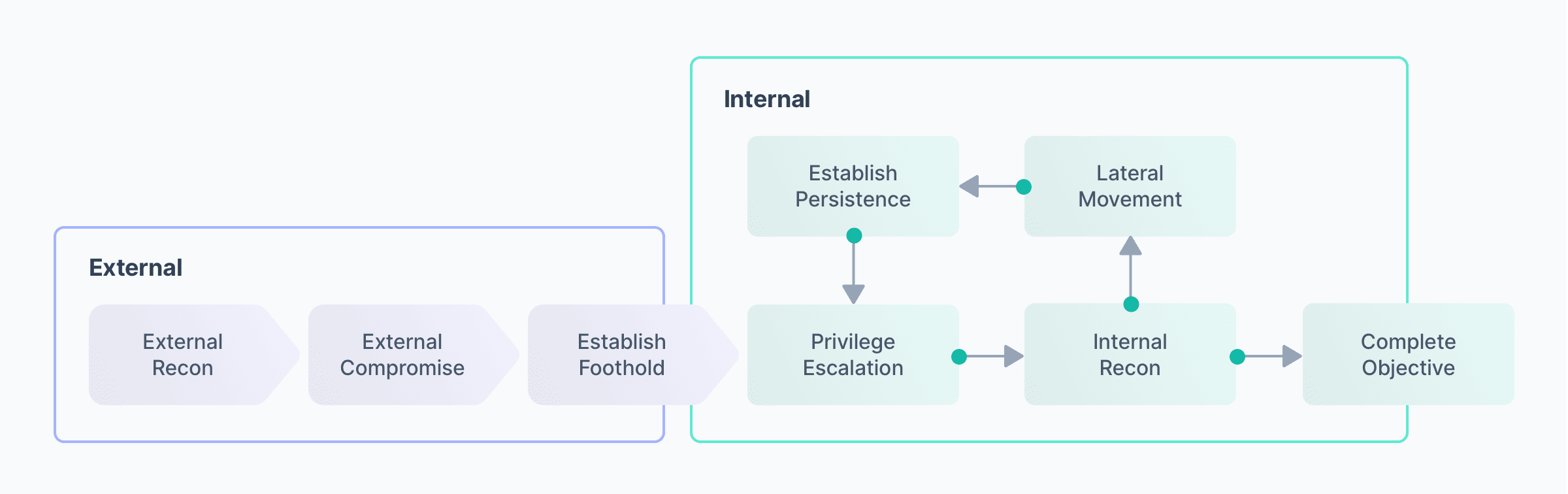
Hypothetical Blue Team Response
In contrast to the real-life Red Team simulation conducted with Dinoch, let’s discuss a hypothetical scenario with a Blue Team demonstrating a proactive approach to countering social engineering. Brainstorming the defensive process allows us to better grasp the roles and responsibilities of the Blue Team.
The Dinoch case study did not mention the existence of a Blue Team; however, there is substantial evidence that Dinoch implemented security measures. In their initial attack, the Red Team discovered that the employees had the option to use Multi-factor Authentication (MFA). The presence of MFA hints at the company’s acknowledgement of layered security protocols. With MFA, users can authenticate with another device. For example, through a unique pin sent to their email, requiring them to login with more information than a password. The adoption of stronger authentication measures like MFA necessitates active participation from every employee, as they play a crucial role in securing their credentials. The implementation of MFA significantly reduces the likelihood of a brute force attack, which is commonly used for accessing accounts to gain privilege escalation. This demonstrates the target’s preparation for a potential attack.
Security programs allow companies to gain valuable insights and enhance employee training and education. In the case study, the Red Team could not retrieve credentials through a simplistic phishing attack. None of Dinoch’s targeted employees divulged their user credentials, suggesting that they have undergone phishing training. Influential analytics and compliance requirements helped employees to identify untrusted sources and refrain from giving their user credentials. The training shaped by the Blue Team’s analysis would have played a pivotal role in significantly impeding the progress of a sophisticated attack.
Despite potential preparation and previous detection by Dinoch’s would-be Blue Team, these attackers continued to exploit people as the weakest link in security. Social engineering relies on psychological manipulation, and can be challenging to prepare for and detect. Blue Teams can better equip companies with the skills and knowledge to protect against persistent attack strategies. When the Red Team leveraged social engineering tactics to gain unauthorized entry to the work event and to empty rooms, they were able to obtain hashes with ease. However, this company wasn’t completely defenseless. The hackers ran into yet another authentication obstacle, the use of long, complex passwords. This stopped them from cracking the hashes.
The persistence of the Red Team finally led to a breach when they used a single employee’s hash to crack into an administrative account, enabling them to send malicious emails from a trusted source. Once a system has been breached, the Blue Team’s defensive tactics become even more important to try to limit the damage, prevent data theft and protect sensitive information.
An article by Converge Technology emphasizes that a response team should include: forensic, legal, IT, HR, operations, communications, investor relations staff, and management experts. Getting more than a Blue Team involved can further deescalate the attack and highlights the importance for a shared responsibility model. Blue Teams must be skilled in communicating technical information, security risks, and mitigation strategies to various departments of the company.
Once the Blue Team identifies the attack and its source, they are able to isolate compromised systems, disable accounts, change passwords, and move the network offline. Blue Team forensics play an integral role in the identification process, procedures, and attack vectors. Logging, reporting and recovery are all other critical aspects of the Blue Team’s responsibilities.
Dinoch’s situation highlights the importance of securing not only digital access controls but also physical ones. A Blue Team’s post-incident report can detail physical security measures such as locking empty workspaces and unused rooms. A Zero-trust framework covers both physical and digital security needs, requiring all users inside and outside the network to be authorized and authenticated. This can include identification badges for event attendees and implementing a check-in registry to admit only authorized guests. Continuous training with social engineering emulations, patching and updates, spam and web filters, and antivirus solutions can help reduce the success and severity of a phishing attack. Using modern phishing-resistant solutions like passkeys can help you avoid such attacks entirely. The key takeaway is that security is a complex and shared responsibility.
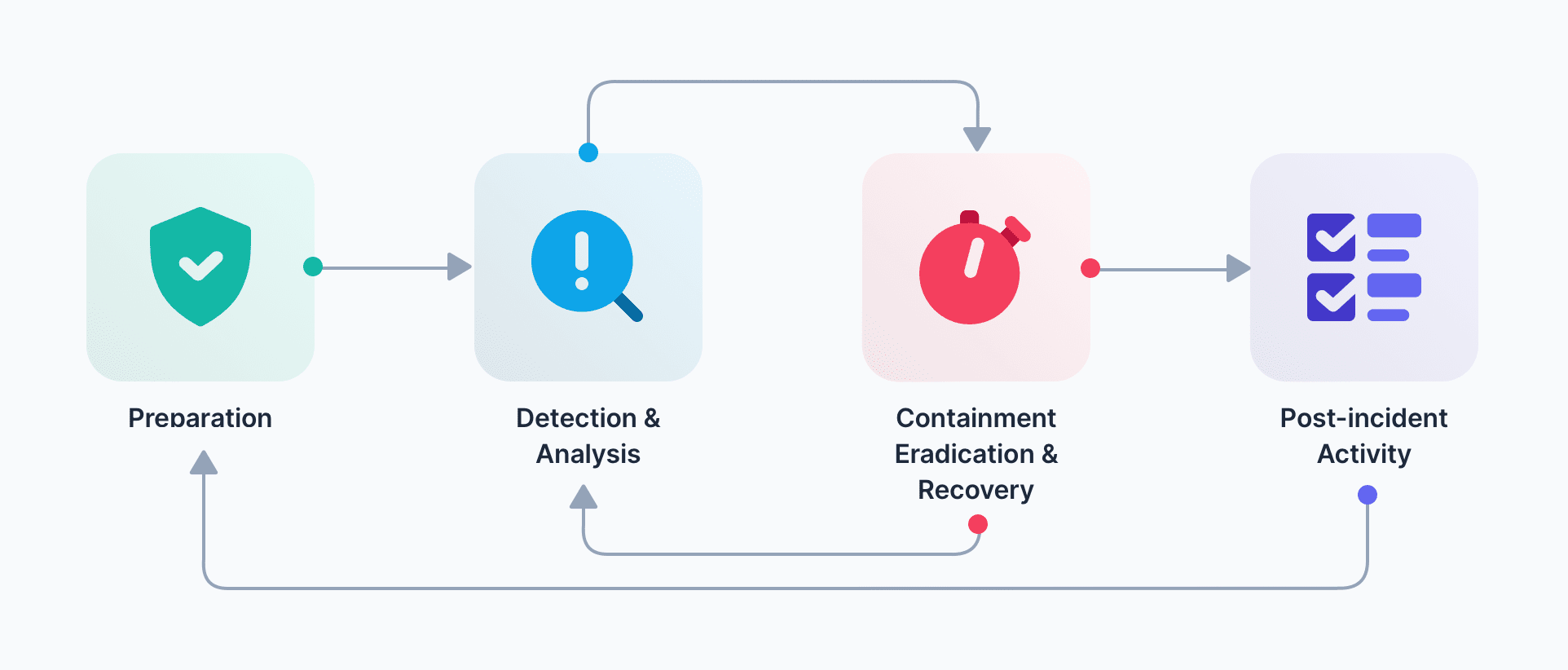
Below is a visualization of the NIST incident response lifecycle that Blue Teams follow for structured defensive applications:
Bridging the Gap: Meet the Purple Team
The emergence of the Purple Team marks a significant advancement in cybersecurity strategies. Combining elements from both the Red and Blue Teams, the Purple Team serves as a catalyst for increased collaboration and feedback between the two. Effective communication becomes paramount in the collective effort to counter cyber threats. For companies with less resources and a smaller budget, automation can function similarly to a Purple Team.
The Purple Team plays a crucial role in cybersecurity operations by creating controlled environments for the Red and Blue Teams to test the security measures of an organization. During simulations, the Purple Team observes the actions of the Red Team and provides feedback to the Blue Team on their defensive effectiveness. After the simulation concludes, all teams convene, and the Purple Team facilitates discussions on the analysis of outcomes, identified vulnerabilities, and proposed actions for improvement. This collaborative approach ensures that lessons learned from the simulation are effectively communicated and integrated into the organization’s cybersecurity practices.
Furthermore, based on findings and input from both the Red and Blue Teams, the Purple Team collaborates with leadership to suggest security implementations that align with organizational objectives and priorities. This includes addressing gaps in training, introducing new security skills to teams, prioritizing risks, and providing recommendations to improve security posture. This ensures that cybersecurity practices remain adaptive and responsive to emerging threats and challenges.
Conclusion
Teamwork, collaboration, and information sharing are paramount for effective cybersecurity practices. Together they create a unified approach toward protecting digital assets and infrastructure. These practices transcend individual organizations and extend to a global network of cybersecurity professionals. The Cybersecurity and Infrastructure Security Agency (CISA) stands as a reputable entity that aggregates cybersecurity data and collaborates with companies to facilitate secure information sharing. Through collaboration with CISA, cybersecurity professionals gain access to playbooks and resources that enhance their ability to mitigate cyber threats effectively.
Engaging as many individuals as possible in the security process extends responsibility beyond one person or team and leads to more successful programs. The main point should be that companies that adapt to a constantly changing environment will have higher success in navigating security challenges. By developing a culture of collaboration, within a company and extending beyond an individual company, organizations can better protect themselves and contribute to a safer and more trustworthy digital landscape for all.

