
How To Choose The Right Authorization And Authentication Deployment Model
Last week, FusionAuth and Cerbos co-hosted a webinar featuring myself and Alex Olivier, Cerbos CPO and co-founder. We shared insights on deploying both...
April 24, 2025
Tags

Last week, FusionAuth and Cerbos co-hosted a webinar featuring myself and Alex Olivier, Cerbos CPO and co-founder. We shared insights on deploying both...
April 24, 2025
This inaugural State of Homegrown Authentication Report: 2025, sponsored by FusionAuth and Cloudelligent, is the first to dive into the experience and tech...
April 2, 2025
24 billion. That's how many passwords hackers exposed in a single year. That's a staggering enough figure, and even more sobering when you realize that it gets...
March 12, 2024
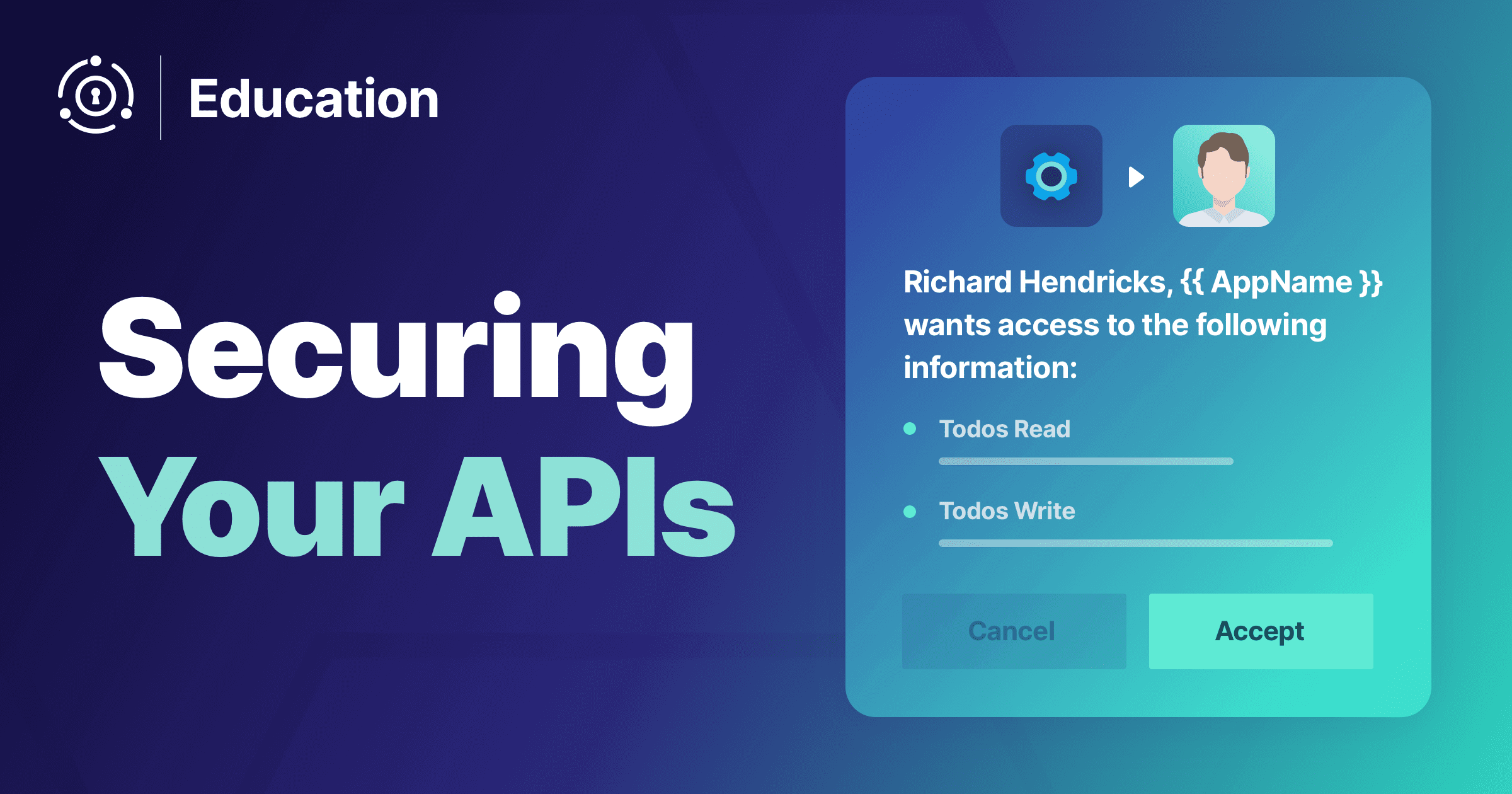
When you are building out APIs for web applications, desktop apps or mobile applications, you must authenticate these requests. You may say to yourself, "of...
February 5, 2024

Remix is the new hotness in web development! It is an attempt to solve some of the performance issues of React by cleverly splitting up server-side code...
April 25, 2023
At the end of the OAuth Authorization Code grant, after a user presents their credentials at login, a code is returned which can be exchanged for one or more...
January 19, 2023

FusionAuth, the developer-focused authentication platform, today announces the addition of passkeys to its long list of authentication features. This enables...
October 27, 2022
Showing 1 to 7 of 14 results
Get updates on techniques, technical guides, and the latest product innovations coming from FusionAuth.
Just dev stuff. No junk.