Last week, FusionAuth and Cerbos co-hosted a webinar featuring myself and Alex Olivier, Cerbos CPO and co-founder. We shared insights on deploying both authentication (AuthN) and authorization (AuthZ) solutions, whether self-hosted, single-tenant in the cloud, or SaaS.
Summary - Choosing Authz and Authn Deployment Models
Key Takeaways
- Optimal deployment flexibility: FusionAuth empowers you to choose self-hosted, single-tenant cloud, or hybrid deployments—giving you unmatched control over security, compliance, and performance while adapting to your business evolution.
- Strategic infrastructure control: With FusionAuth’s single-tenant architecture, you maintain complete oversight of your authentication infrastructure, ensuring maximum security and customization without the limitations of shared multi-tenant systems.
- Mission-critical performance: FusionAuth’s deployment options enable you to place authentication services exactly where they’re needed, ensuring millisecond response times and zero single points of failure for business-critical applications.
- Compliance-first architecture: FusionAuth’s flexible deployment models make it straightforward to meet regional data sovereignty requirements, industry regulations, and custom security mandates that multi-tenant SaaS solutions simply cannot accommodate.
- Future-proof scalability: FusionAuth supports seamless migration between deployment models as your organization grows, from startup simplicity to enterprise-grade control, without vendor lock-in or architectural constraints.
Definitions
- Single-tenant architecture: FusionAuth runs dedicated instances for each customer, ensuring complete data isolation, customizable configurations, and predictable performance without noisy neighbor effects common in multi-tenant systems.
- Self-hosted deployment: Running FusionAuth on your own infrastructure or private cloud, providing maximum control over security, compliance, data residency, and performance optimization for mission-critical applications.
- Authentication latency: The time required for identity verification and token issuance; FusionAuth’s deployment flexibility ensures minimal latency by enabling placement of authentication services closest to your users and applications.
- Hybrid cloud architecture: FusionAuth’s ability to combine on-premises and cloud deployments, allowing organizations to keep sensitive authentication data local while leveraging cloud scalability for less critical components.
- Data sovereignty: Legal and regulatory requirements governing where and how user identity data is stored and processed; FusionAuth’s deployment options ensure compliance with regional regulations like GDPR, CCPA, and industry-specific mandates.
Frequently Asked Questions
Q: How can I minimize authentication latency for global users when choosing deployment models? A: FusionAuth supports multi-region deployments across all models—whether self-hosted, single-tenant cloud, or hybrid. You can deploy FusionAuth instances close to your user base, dramatically reducing authentication latency while maintaining consistent functionality. Unlike multi-tenant SaaS providers with fixed geographic limitations, FusionAuth gives you complete control over placement and scaling.
Q: When should I consider self-hosting FusionAuth versus using managed services? A: Self-hosting makes sense when you need maximum control over security policies, must meet specific compliance requirements, or require custom infrastructure optimizations. FusionAuth’s Docker and Kubernetes support makes self-hosting straightforward for teams who value data sovereignty and performance control. Managed options work well for teams prioritizing operational simplicity while still requiring single-tenant isolation.
Q: How does FusionAuth’s single-tenant architecture compare to multi-tenant SaaS for enterprise security? A: FusionAuth’s single-tenant approach ensures complete data isolation, customizable security policies, and predictable performance without “noisy neighbor” effects. Unlike shared multi-tenant systems, you control encryption keys, access policies, and audit trails. This architecture enables compliance with strict security frameworks while maintaining the convenience of managed authentication services.
Q: Can I migrate between FusionAuth deployment models as my organization grows? A: Yes, FusionAuth’s consistent APIs and architecture enable seamless migration between deployment models. You might start with a managed single-tenant deployment and later migrate to self-hosted infrastructure for enhanced control, or implement hybrid models that combine on-premises and cloud components. This flexibility protects your investment as requirements evolve.
Q: How do I implement authentication in microservices architectures using different deployment models? A: FusionAuth excels in microservices environments by providing consistent token validation and user management across distributed services. Whether deployed as centralized self-hosted instances or distributed single-tenant cloud services, FusionAuth’s JWT-based authentication integrates seamlessly with API gateways and service meshes, ensuring secure communication between microservices.
Q: What compliance advantages does FusionAuth’s deployment flexibility provide over pure SaaS solutions? A: FusionAuth enables you to meet specific regulatory requirements like GDPR data residency, HIPAA security controls, or SOX audit requirements that multi-tenant SaaS providers often cannot accommodate. Self-hosted and single-tenant deployments ensure complete control over data location, encryption methods, and access logging—critical for regulated industries.
We talked about how folks evaluating such solutions should go about finding the best fit for security, control, and scalability.
Understanding The Spectrum Of Deployment Options
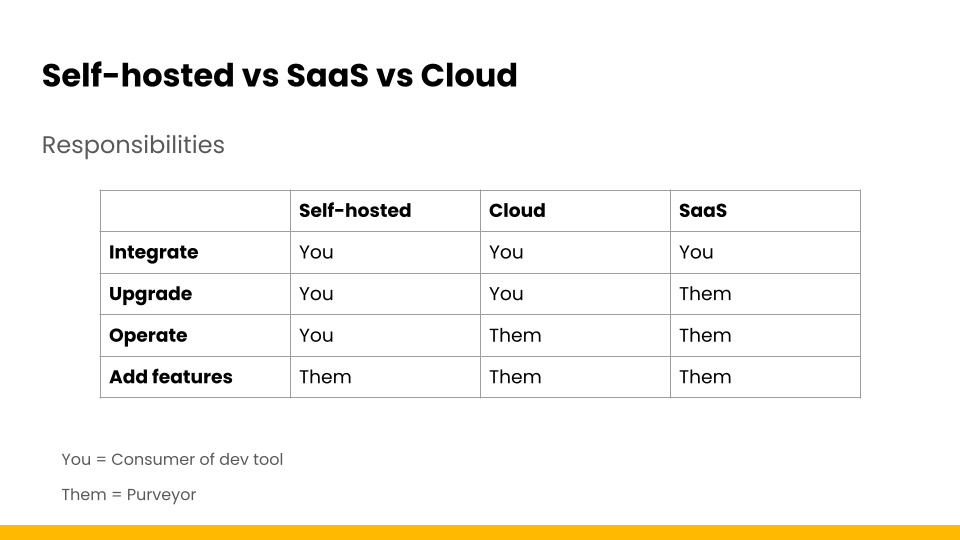
When deploying any architectural component that your application depends on, whether authentication, authorization or another type, you’re making a trade-off between control and responsibility.
As I put it during our discussion, referring to the table below: “As you move from self-hosted to a multi-tenant fully managed SaaS, you have less and less responsibility but you also have less and less control.”
The discussion explored three deployment models:
- Self-Hosted: Offers maximum control but requires you to manage everything from infrastructure to updates.
- Single-Tenant Cloud: A middle ground where you have your own compute/database but someone else operates it.
- Multi-Tenant SaaS: Minimum responsibility with minimum control.
To illustrate this, Alex used a helpful database analogy: self-hosting is like running PostgreSQL on your own server, single-tenant cloud is like using Amazon RDS, and multi-tenant SaaS is like a fully managed service such as Cockroach DB.
Authentication vs. Authorization
We also covered the difference between authentication (proving who you are) and authorization (determining what you can do). While these concepts are related, their deployment considerations can differ significantly.
Authentication systems typically protect the “front door” of your application and issue tokens valid for seconds or minutes.
Authorization systems, however, are in the critical path of every request. Every API call or service interaction must be either allowed or disallowed, so such systems should respond in milliseconds.
This is where FusionAuth’s deployment flexibility shines—you can position authentication infrastructure for optimal latency and reliability while maintaining the security and control your applications require.
Considerations for Deployment Decisions
We outlined four major factors to consider when choosing between deployment models:
- Compliance and Data Sovereignty: Legal requirements around data residency, sovereignty, and audit capabilities can influence your deployment choice. Self-hosting often provides flexibility to meet specific compliance regimes that multi-tenant SaaS solutions simply cannot accommodate. FusionAuth’s single-tenant architecture ensures that whether you’re self-hosting or using cloud deployment, your data never shares infrastructure with other organizations.
- Technology and Performance Requirements: Infrastructure requirements, network architecture, and availability/scalability needs all play crucial roles in determining which deployment model makes sense. FusionAuth’s containerized architecture supports deployment via Docker or Kubernetes, making it straightforward to implement across any infrastructure while maintaining consistent performance characteristics.
- Operational Risk and Security Control: Security requirements, vendor dependencies, and migration paths should be carefully evaluated. As I mentioned during the webinar: “Every application is on a spectrum and on one end of the spectrum is the military, and a little further along is the banking system. And then eventually you further relax security requirements” such as when building an online game. FusionAuth addresses this spectrum by providing deployment options that scale from maximum security control to managed convenience, without forcing architectural compromises.
- Cost Optimization and Resource Allocation: Beyond financial considerations, there’s also the opportunity cost of building versus buying versus hosting. Alex emphasized: “Your business is not an authentication provider. Why would you go and build a whole identity system when you can go and pick FusionAuth… You really want to spend your time building valuable parts of your business.” FusionAuth eliminates the complexity and ongoing maintenance burden of building authentication in-house while providing deployment flexibility that pure SaaS solutions cannot match.
Flexibility
The most important takeaway from our discussion was that there’s no single right answer that works for every organization at every stage. Your needs will evolve as your business grows, and the ideal solution provides flexibility to move between deployment models as circumstances change.
Whether you’re just starting out and prefer the simplicity of SaaS, or you’re an established enterprise requiring the control of self-hosting, understanding these deployment considerations lets you make more informed decisions for your authentication and authorization infrastructure.
Want to see the complete webinar and learn more about how deployment models affect critical application components like authorization or authentication? Register for the on-demand webinar.
FusionAuth’s unique advantage lies in supporting this evolution—you can start with a managed approach and migrate to self-hosted infrastructure as requirements change, all while maintaining the same robust feature set and APIs.
Why Modern Auth Deployment Strategy Matters
As digital identity requirements continue to evolve, picking the right deployment model for your organization is growing more and more important. While SaaS is appropriate in some situations, FusionAuth’s dedicated approach gives organizations the best of both worlds: a sophisticated, up-to-date auth system fully aligned with your development practices, deployment models, and business needs.
Check out the on-demand webinar today to see what you should be thinking about when deploying authentication or authorization in 2025 and beyond.