
Your Token Proves Who You Are, Not What You Own
Sammy Azdoufal spent $2,000 on a DJI Romo robot vacuum. It's a sleek, impressive machine — DJI's first foray into the consumer robotics market. Sammy, being a...
February 26, 2026
Categories

Sammy Azdoufal spent $2,000 on a DJI Romo robot vacuum. It's a sleek, impressive machine — DJI's first foray into the consumer robotics market. Sammy, being a...
February 26, 2026

There's a lot of conversation right now about the challenges of AI agents, and much of it centers on identity: how do you distinguish an agent from the human...
February 18, 2026

These Questions Matter If you're evaluating identity infrastructure—or reconsidering an existing provider—several questions deserve direct answers: What...
February 2, 2026
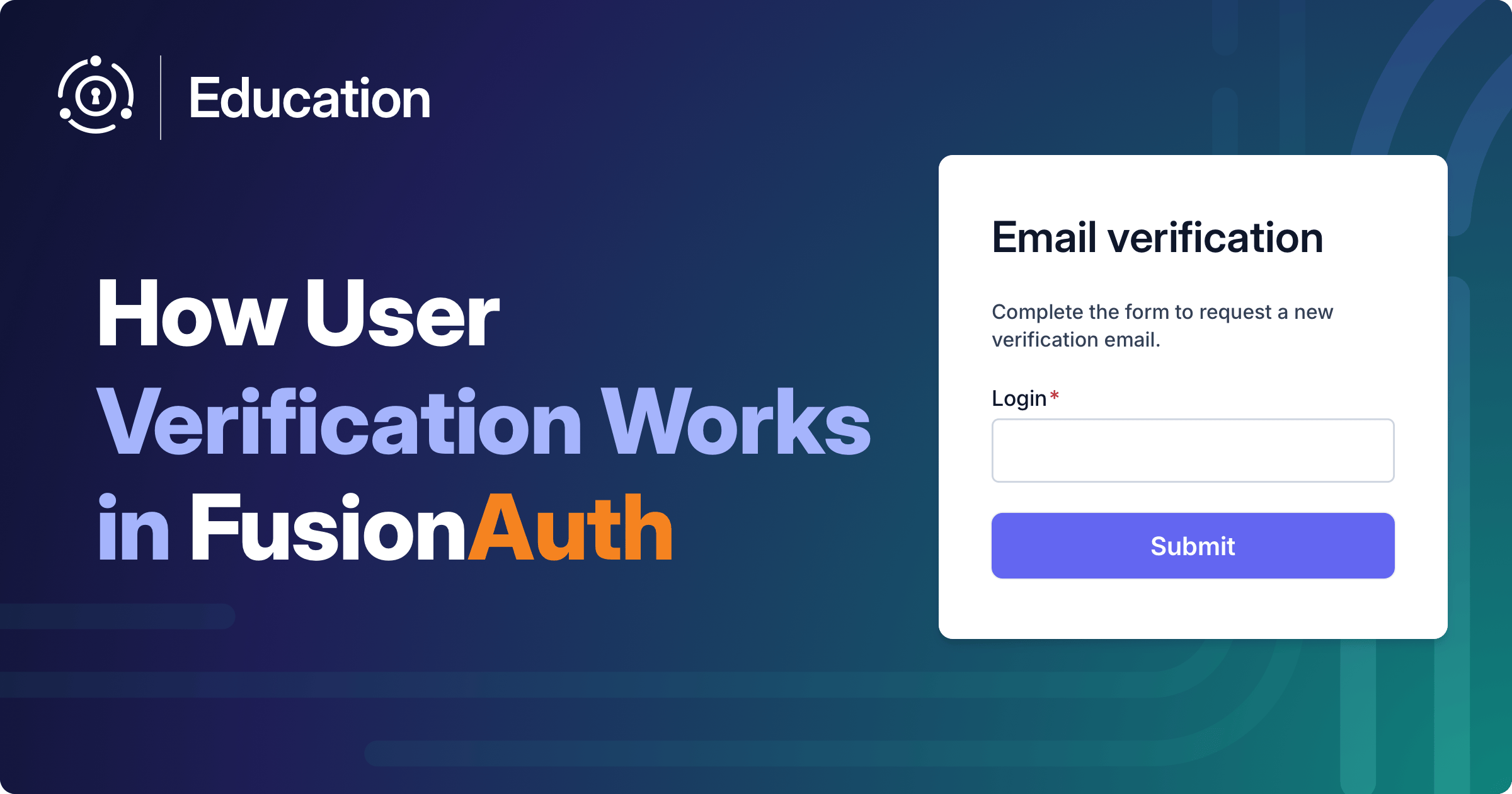
In FusionAuth, users verify their identities by entering a code or clicking a link sent to their registered email address, or in recent versions, phone number...
December 17, 2025

FedCM, or Federated Credential Management, is a web standard being developed by the W3C to create a more secure and privacy-conscious way for users to log into...
October 28, 2025
You may not have previously considered the HTTP server when building a web application. It may already be packaged as part of an application server such as...
October 6, 2025
If you're building any application with users, but especially a SaaS application, you've probably found yourself staring at a whiteboard, trying to figure out...
September 16, 2025
Showing 1 to 7 of 80 results
Get updates on techniques, technical guides, and the latest product innovations coming from FusionAuth.
Just dev stuff. No junk.