
OIDC vs SAML: What's the Difference?
It's essential for digital platforms to keep their data and resources secure, which is why authentication protocols are so necessary. Authentication protocols...
January 9, 2023
Categories

It's essential for digital platforms to keep their data and resources secure, which is why authentication protocols are so necessary. Authentication protocols...
January 9, 2023

Single sign-on (SSO) is an authentication method that allows users to access multiple applications with one set of login credentials. It provides secure access...
December 8, 2022

"Ladies and gentlemen.... ASP.NET!" The crowd goes wild. The presenter, on stage, has just scaffolded out a fully-functional TODO list application using...
November 21, 2022
Unless you use two-factor authentication (2FA) with your password logins, you're prone to cyberattacks. This is where Passkeys (WebAuthn) can help. WebAuthn is...
November 1, 2022
More and more games are launching across two or more platforms. One of the prime reasons why game developers go cross-platform is to leverage a larger market....
October 6, 2022

WebAuthn is a new way for people to authenticate themselves to web applications. It's a widely supported standard years in the making. All major browsers work...
September 13, 2022
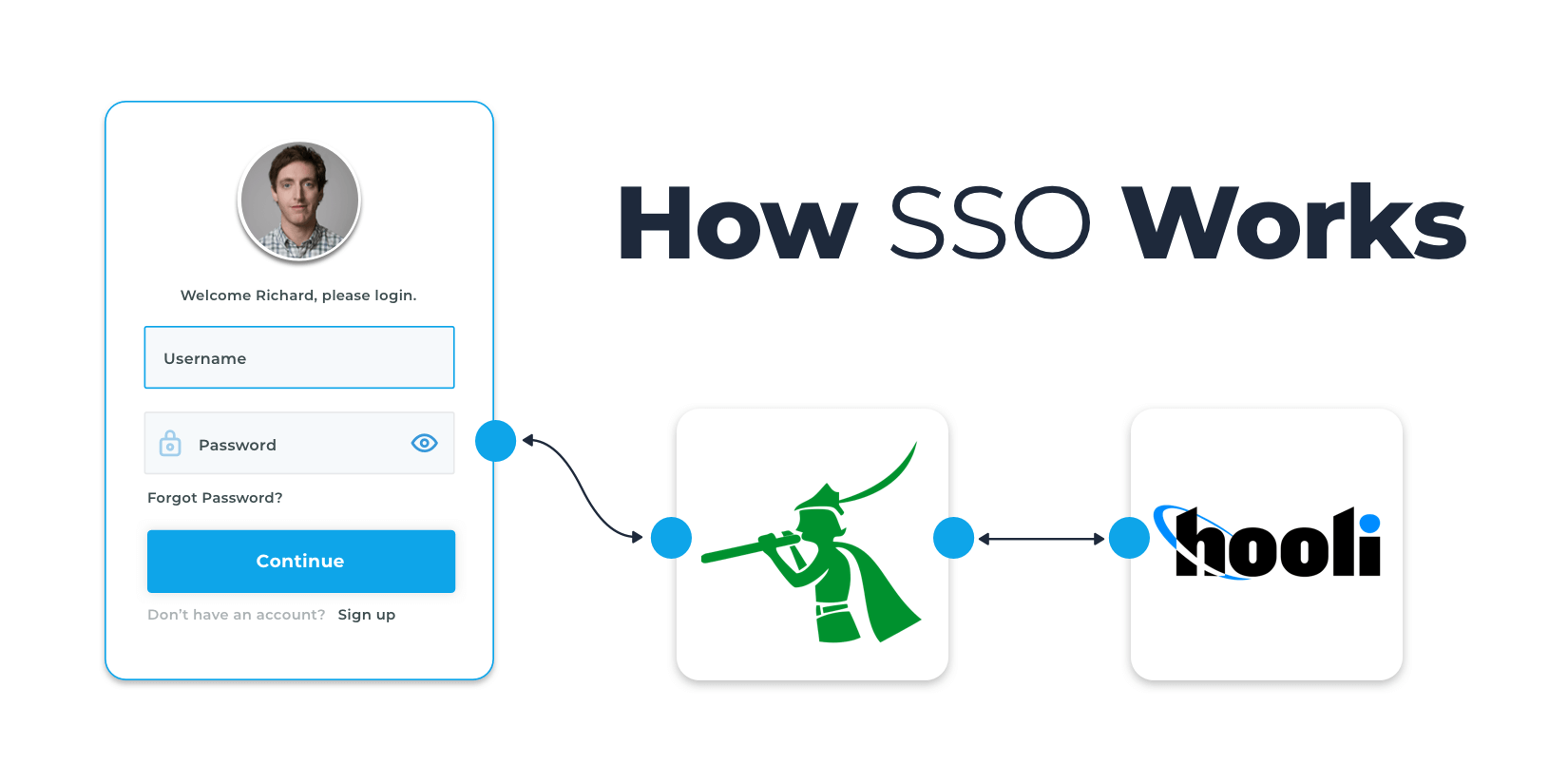
Single sign-on (SSO) is a key part of any customer identity and access management (CIAM) strategy. Why? Because your organization will almost always have more...
September 8, 2022
Get updates on techniques, technical guides, and the latest product innovations coming from FusionAuth.
Just dev stuff. No junk.