In the last few days, I have taken a look back at what the FusionAuth team shipped in 2024. I wanted to share some of the highlights for our community.
Highlights
While many features were added and bugs squashed, I wanted to hit the highlights. Since FusionAuth is versioned software, many highlights correspond to product releases.
January - March
Throughout the quarter, we released a lot of documentation, including:
- a rust quickstart
- three migration guides
- multiple articles about security and identity
- a guide for using GitHub actions with FusionAuth and a corresponding GitHub action
- a device-limit guide
In March, we released a bugfix and security improvement product release. This had nearly 30 bugfixes and improvements. We all love features, but bugfixes are important too.
We also welcomed our first customer integration engineer, Mike. This role exists because integrating FusionAuth into existing applications and architectures can be complex. Mike provides custom integration support to help larger customers get launched and has helped a number of customers integrate FusionAuth into their prod applications in the months since he joined the team.
April - June
In April, we added in-app first time help, to assist folks new to FusionAuth in setting up their integration.
We also added support for OAuth scopes, which allows you to use FusionAuth as a foundation for an app ecosystem. You can create custom scopes associated with applications. This allows your users to consent to sharing their data held by your application or APIs with third party apps. Anyone who has public APIs can become a platform by using this feature to share their APIs and user data with partners and outside developers.
Finally, we added the ability to customize the UserInfo response using a lambda. The UserInfo endpoint is part of the OIDC standard. It takes an access token and returns information about a user. The UserInfo response usually overlaps with the ID token claims, but with this lambda, you can now control and modify both of these spec-compliant sources of user data.
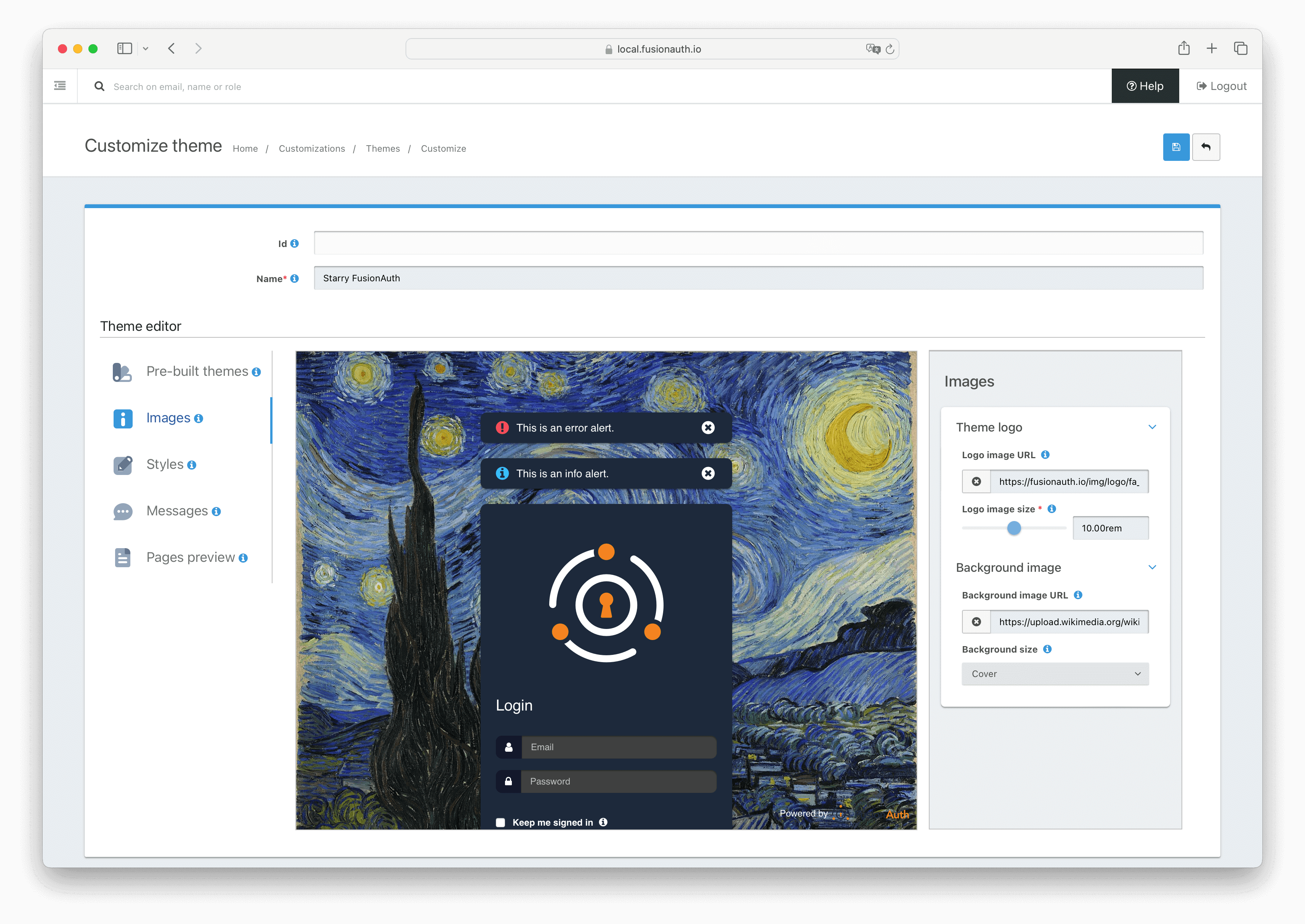
In May, we introduced simple themes. The fully customizable look and feel of FusionAuth themes is unique in the CIAM space, but thirty-plus templates full of Freemarker can be daunting when an engineer is beginning to customize the branding of login pages. Simple themes lets you quickly build a custom look and feel.
Perhaps more importantly, it offers forward compatibility. When you customize FusionAuth using advanced themes, you are responsible for propagating changes when a new version of FusionAuth lands. With simple themes, the FusionAuth team owns that responsibility.
We also commemorated World Password Day, the first Thursday of May, with a look back at passwords through the ages.
July - September
The third quarter of 2024 saw passkeys enter our Community plan, in August. Anyone using FusionAuth can enable passkeys for their all users, for free.
In September, the webhook event log landed. This feature has been a long time coming. It lets you review events sent by FusionAuth. It also includes timing and result information for each attempt. Since webhooks are heavily used to integrate FusionAuth with other systems, having more visibility into how webhooks are behaving helps with troubleshooting and analysis.
The login validation lambda was delivered in September as well. Like other lambdas, this gives you fine grained control over an aspect of the login process. This particular lambda lets you control whether or not a user’s login succeeds. Your business logic can examine the user, their registration details, the authentication type, and an identity provider, if one was used. Because of all this context, this lambda allows you to offer extremely fine grained control over whether a login succeeds.
Want to allow a user to log in on the third day of the month between 7pm and 10pm, but only if it is a Tuesday and only they use Facebook to log in? Now, if it were me, I’d double check with your product manager about those wacky requirements, but you could implement such rules with this lambda.
This lambda also lets you add custom, localizable error messages, so when that user can’t log in because it isn’t Tuesday the 3rd, you can offer them an explanation. When combined with Lambda HTTP Connect, you can leverage existing APIs as well. Maybe you want to add ‘must be a waxing moon phase’ to the above requirements?
We also added docs over the quarter, including:
- how to use FusionAuth with CloudFlare’s API gateway
- monitoring with Amazon CloudWatch, Datadog, Splunk, and Elasticsearch
- one migration guide
- extending the guide on SMTP configuration to document how to use nine different SMTP providers
- a guide on session management
- a blog post about deploying to Render
- a blog post about Hacktoberfest 2024
In August, we also released a new version of our website, with a beautiful new design, an overhaul of our messaging, and a new information architecture.
Oct - Dec
We released an express free trial in November, allowing folks to kick the tires on FusionAuth Cloud for a month without having to enter any credit card details. We get it, some devs don’t want to install Docker to check out new software.
We also upgraded our cloud infrastructure. These changes were released over time in Q4 and improved FusionAuth Cloud performance and flexibility. While this upgrade is largely invisible to our customers, as it should be, there were two enhancements worth calling out:
- everyone can have least one custom domain, no matter the hosting package
- our webhooks, Lambda HTTP Connect calls, messengers and connectors are coming from a fixed IP address range, making firewall configuration easier if you have one between a FusionAuth Cloud deployment and your systems
In December, we announced AuthCon, the first Customer Identity and Access Management (CIAM) conference, with speakers from ARM, IDPro, GitLab, Alteryx and GitHub, among others. Learn more, submit a talk or register at the AuthCon website.
We also shipped some docs this quarter, including:
- 5k words on how building self-hostable software differs from SaaS
- technical use case documentation
- a case study with Vatix
- a competitor comparison page
Non-Functional Improvements
Developers know that you can’t just ship features. You also need to improve non-functional aspects of the software, such as security, performance and operability. Over the course of 2024, we delivered performance improvements around application areas including:
- database access
- user bulk import
- user and entity search, allowing you to avoid requesting unneeded data
We also improved the security features, including:
- API key security
- upstream proxy trust
- a new confirmation page to improve security and interoperability with corporate link checkers
Finally, software is operated. We run FusionAuth for many customers, but lots of folks self-host and we want to help them do that better. In addition to the monitoring guides mentioned above, improvements in that area include:
- a health check API for better kubernetes compatibility
- upgrading our runtime to the latest Java LTS, Java 21
If you want all the nitty gritty product details, they are in the release notes.
By The Numbers
Here’s some hard numbers about the FusionAuth team’s 2024 public efforts.
- 7 minor and 8 patch releases
- 362 issues opened in our public issues repo
- 174 issues in the public issues repo were closed
- 662 public issues were updated
- 65 significant pieces of content published, from blog posts to case studies to diagram refreshes to documentation updates.
- 503 other documentation changes merged
- 553 forum posts
- 2 security notices
- 12 conferences sponsored or spoken at
- 13 new videos
- 2 years on the Inc 5000
Happy 2024 to you, and here’s to a great 2025.