
What is WebAuthn and why should you care?
WebAuthn is a new way for people to authenticate themselves to web applications. It's a widely supported standard years in the making. All major browsers work...
September 13, 2022
Tags

WebAuthn is a new way for people to authenticate themselves to web applications. It's a widely supported standard years in the making. All major browsers work...
September 13, 2022
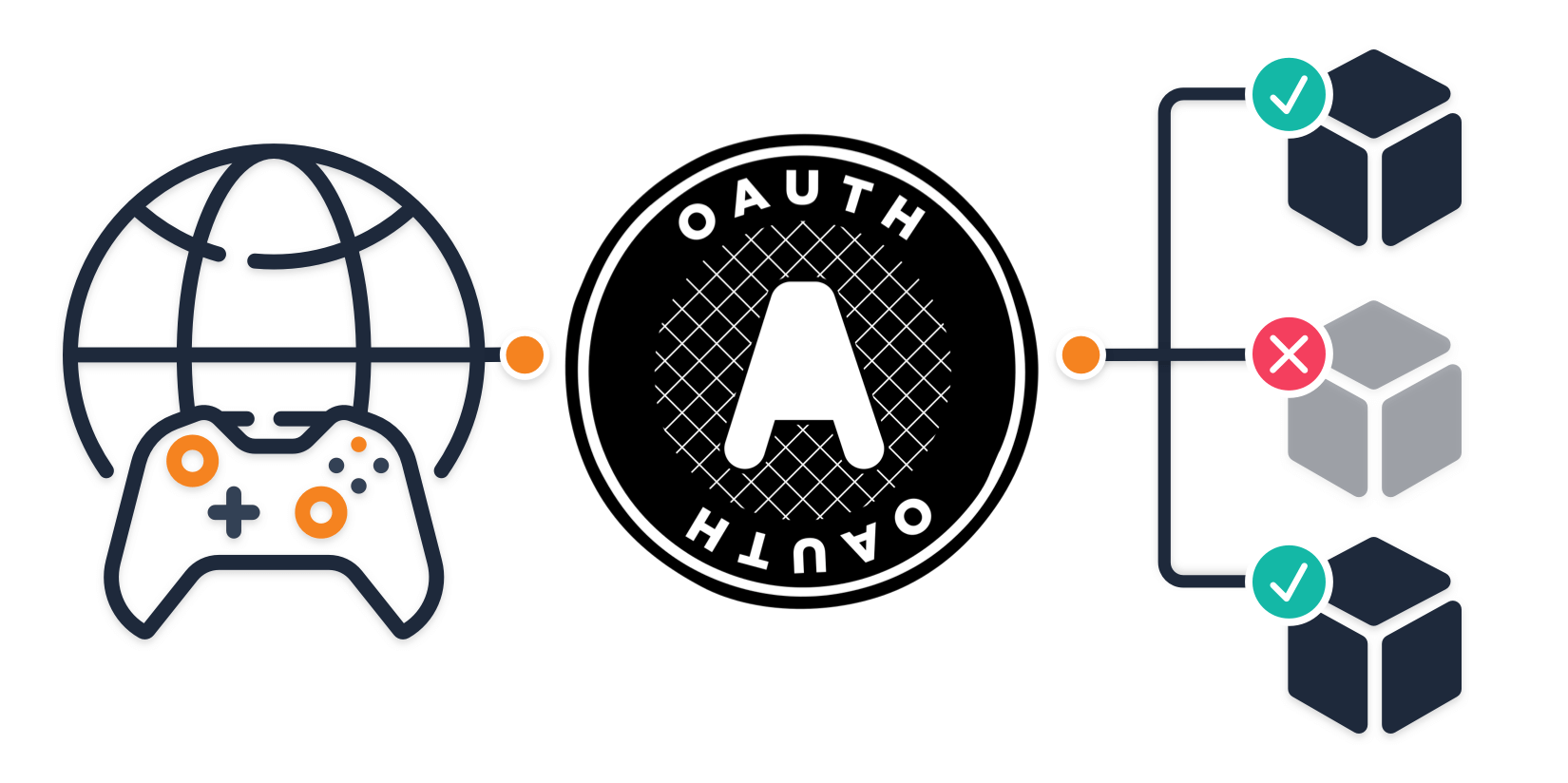
The OAuth device authorization grant is an extension of OAuth 2.0. Because OAuth is an authorization protocol, it enables users to gain access to an...
September 1, 2022
Once a user registers, you can view their data in the administrative user interface. But how can you allow the user to view or change their data themselves?
June 20, 2022

OAuth, a standard for securely delegating authorization information, and OIDC, a profile written on top of it to securely transmit user profile data, both rely...
June 14, 2022

Inversoft, Inc., the parent company of software products FusionAuth and CleanSpeak, today announced the addition of Andy Grolnick and Kendall Miller to its...
February 28, 2022

Inversoft, Inc., the parent company of software products FusionAuth and CleanSpeak, reported record results for the year ending December 2021, posting 168%...
February 3, 2022

FusionAuth, the authentication and authorization platform built for developers, has been chosen by Omedym as its customer identity and access management (CIAM)...
December 14, 2021
Get updates on techniques, technical guides, and the latest product innovations coming from FusionAuth.
Just dev stuff. No junk.