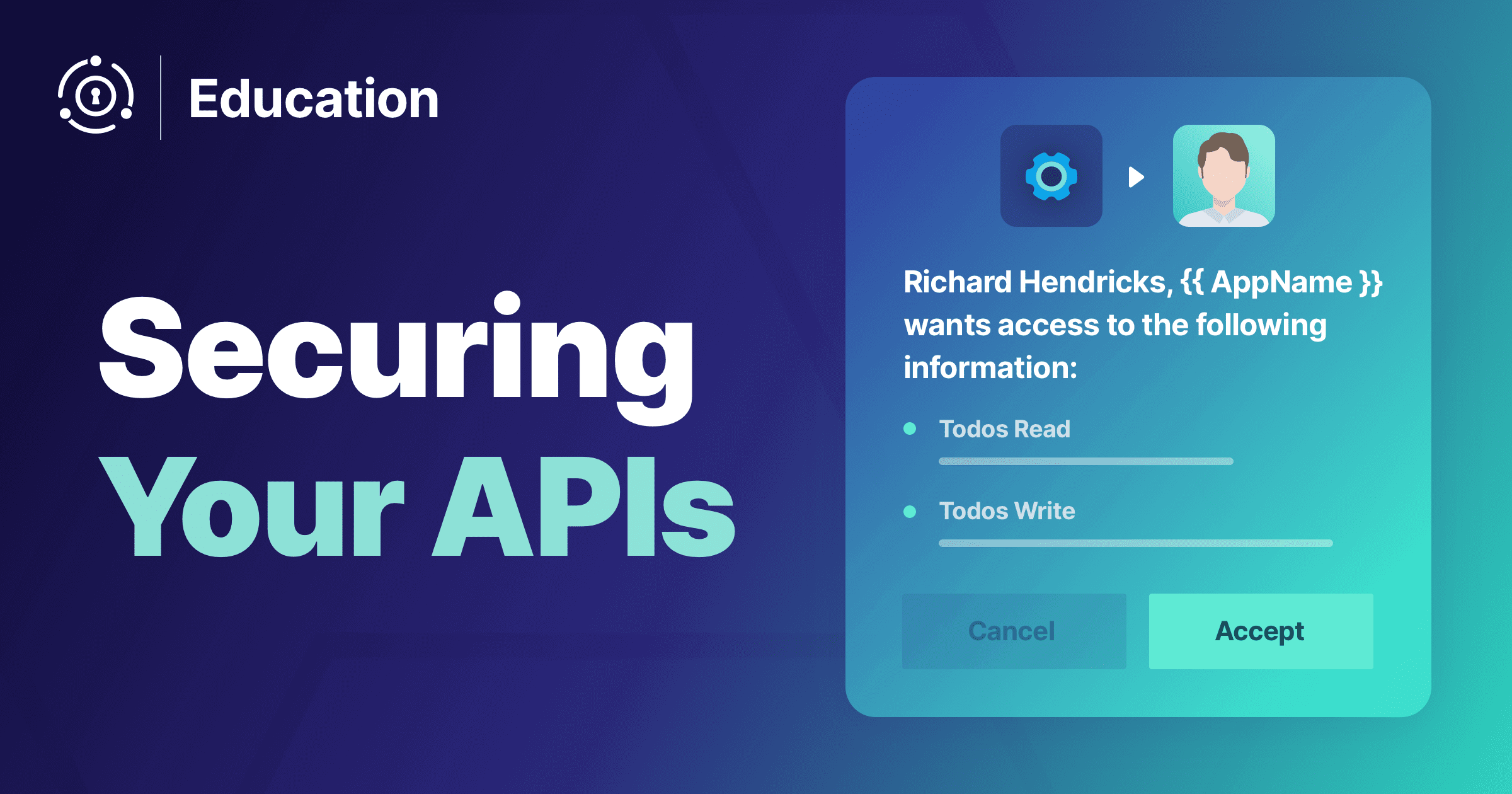
Securing Your APIs: Verifying API Keys And Using Scopes
When you are building out APIs for web applications, desktop apps or mobile applications, you must authenticate these requests. You may say to yourself, "of...
February 5, 2024
Tags

When you are building out APIs for web applications, desktop apps or mobile applications, you must authenticate these requests. You may say to yourself, "of...
February 5, 2024
For many applications, a user is forced to register for application access. You want to know who the user is so you can provide them with individualized...
October 2, 2023
At the end of the OAuth Authorization Code grant, after a user presents their credentials at login, a code is returned which can be exchanged for one or more...
January 19, 2023

Trevor Robinson is a FusionAuth community member and co-founder and CTO of FITT Finder, a meta-search and discovery engine for health and fitness activities....
May 26, 2021
The FusionAuth community has an active online forum, and I wanted to highlight some of the recent topics. Forum discussions vary in topic and depth, but focus...
May 5, 2021

In a recent article, we set up an API gateway with microservices for an eCommerce enterprise. FusionAuth handled our centralized authentication and then we...
November 12, 2020

Ruby on Rails is a modern web framework, but also a great way to build an API. The ability to quickly jam out your business logic, the ease of creating and...
June 11, 2020
Showing 1 to 7 of 7 results
Get updates on techniques, technical guides, and the latest product innovations coming from FusionAuth.
Just dev stuff. No junk.