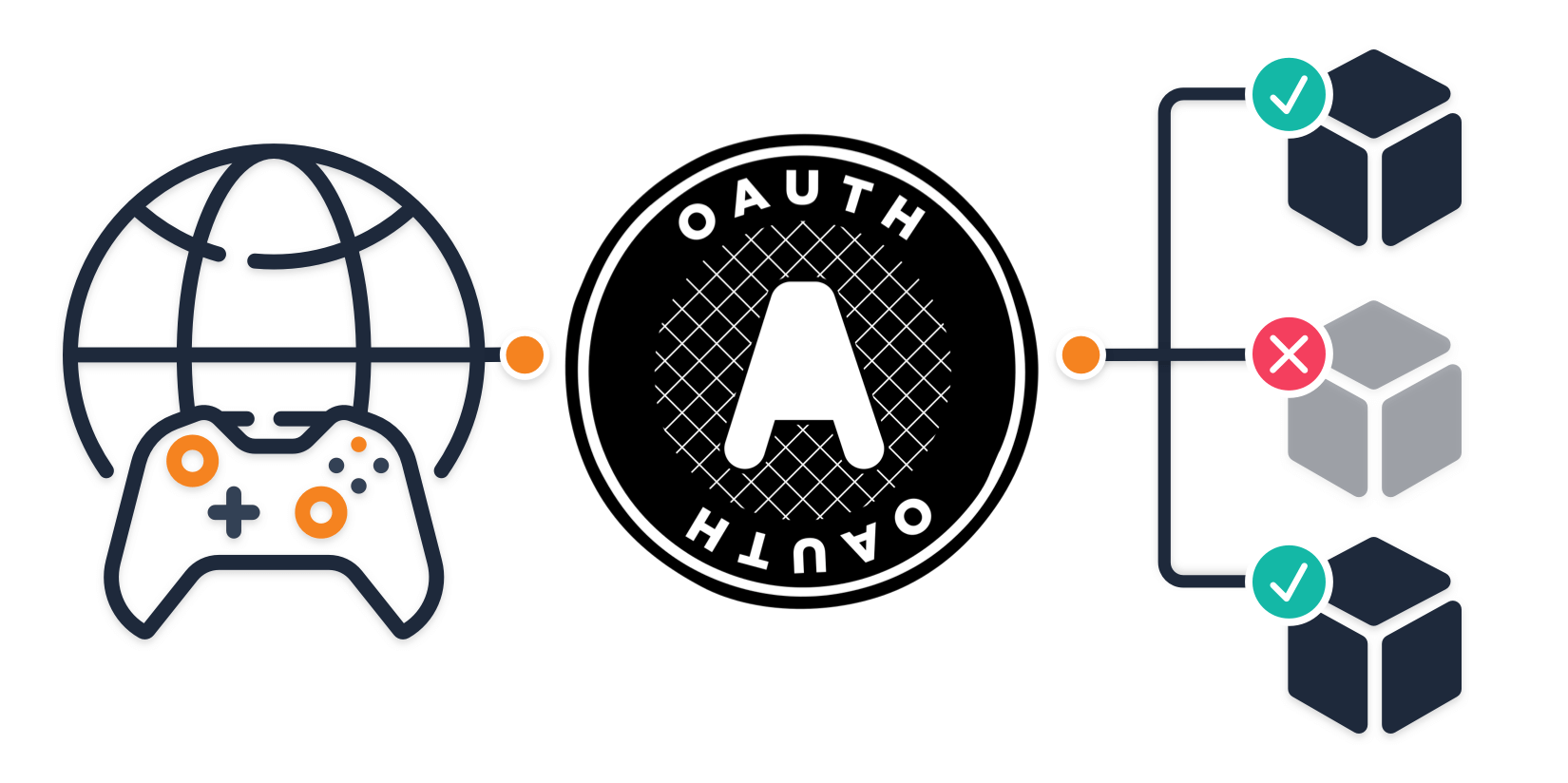
Is the OAuth Device grant right for your game authentication needs?
The OAuth device authorization grant is an extension of OAuth 2.0. Because OAuth is an authorization protocol, it enables users to gain access to an...
September 1, 2022
Tags

The OAuth device authorization grant is an extension of OAuth 2.0. Because OAuth is an authorization protocol, it enables users to gain access to an...
September 1, 2022
Once a user registers, you can view their data in the administrative user interface. But how can you allow the user to view or change their data themselves?
June 20, 2022

OAuth, a standard for securely delegating authorization information, and OIDC, a profile written on top of it to securely transmit user profile data, both rely...
June 14, 2022

Previously, we used .NET Core to build a command line tool to add users to a FusionAuth user identity management system. In this tutorial, we'll build out a...
October 7, 2021

Brittany Roddy is a FusionAuth community member and lead software engineer and architect at CurrentDesk. She chatted with us over email about how she and her...
July 29, 2021
Software applications regularly need to gain access to data from other services on behalf of their users. An application may need to grab a list of user's...
June 10, 2021

The Implicit grant is part of the OAuth 2 RFC, but is one of the features omitted in the OAuth 2.1 specification. With this grant, you don't have to write...
April 29, 2021
Get updates on techniques, technical guides, and the latest product innovations coming from FusionAuth.
Just dev stuff. No junk.