Setting up SAML authentication for your application can feel a bit like poking around in the dark sometimes. So many nerd knobs to tweak. You have read the documentation, triple checked your settings, but you’re still not sure if you have everything dialed in.
Good news! There is a way to test and make sure your SAML v2 configuration is set up correctly. Enter IAMShowcase. IAMShowcase is a site that acts as a SAML v2 SP (service provider) to test your FusionAuth IdP (Identity Provider). The authentication world is full of acronyms and that last sentence is no exception.
So, grab a cup of coffee (or something stronger if you’re so inclined) and let’s break it down.
Understanding Common Acronyms in Identity
Acronyms and jargon and bears, oh my! If you are familiar with acronyms like SAML, SP, and IdP feel free to skip to the next section. For those of us that are merely mortal, here are some definitions.
SAML v2 stands for “Security Assertion Markup Language”, the second version. SAML is like a digital passport. It lets users log into one service and also gain access to another service without needing to log in again. It is a standards based way to verify a user’s identity and authorize access to applications and services. The user can log in once and access multiple applications.
IdP is short for “Identity Provider”. An IdP is a service that verifies your user’s identity and communicates that identity in a secure way to any applications that depend on it. This is where the user logs in. FusionAuth is the IdP for this tutorial.
SP is an acronym for “Service Provider”. Think of this as any application or service your user wants to access. The SP delegates identity ownership to the IdP. In this tutorial, IAMShowcase is the SP.
FusionAuth supports SAML both as a SAML Identity Provider (IdP) and as a Service Provider (SP). Using FusionAuth for both makes this blog post more murky. For this post, FusionAuth is always the IdP.
Test FusionAuth SAML Configuration With IAMShowcase
There are generic instructions on the IAMShowcase site, but the rest of this tutorial describes how to set up and test FusionAuth as a SAML IdP.
You will need an instance of FusionAuth up and running. You can do so using Docker, using Homebrew, or a number of other methods.
1. Create A New Application Named IAMShowcase Example
Log into FusionAuth and select Applications . Give the application a name such as IAMShowcase Example. If you have more than one tenant, select the default Tenant . Then click the blue disk to save the configuration.
2. Retrieve The Configuration Values From The IAMShowcase Website
The IAMShowcase site provides a metadata file that some IdPs can import. You can get the XML from the IAMShowcase site by clicking on Get Metadata. FusionAuth does not support importing of the metadata file. To see the values used, view the XML and manually enter the information in the SAML tab of the application configuration in FusionAuth.
Here is an example of metadata provided by IAMShowcase:
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" entityID="IAMShowcase" validUntil="2025-12-09T09:13:31.006Z">
<md:SPSSODescriptor AuthnRequestsSigned="false" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sptest.iamshowcase.com/acs" index="0" isDefault="true"/>
</md:SPSSODescriptor>
</md:EntityDescriptor>3. Configure The IAMShowcase Example Application For SAML
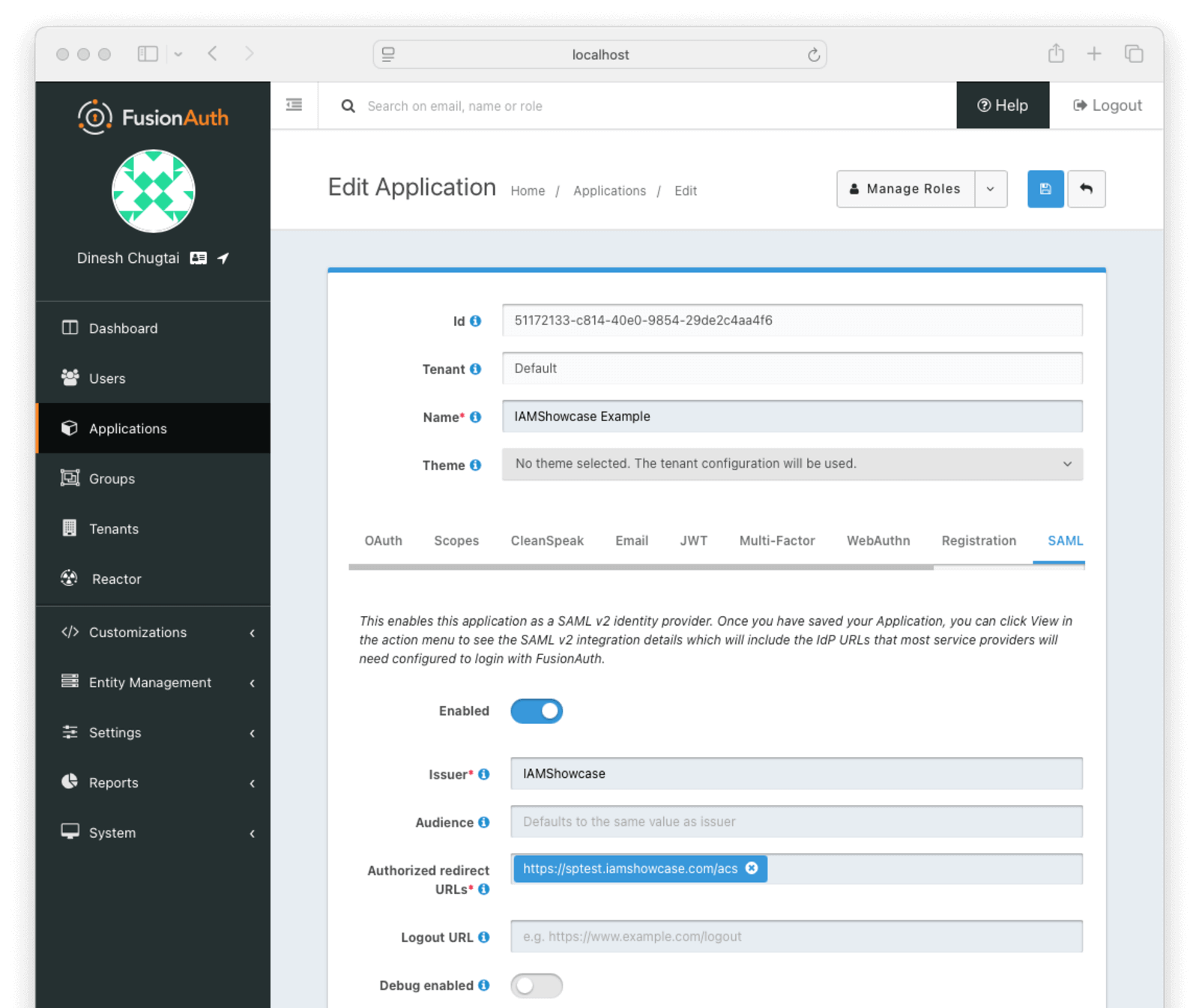
Select Applications and Edit the IAMShowcase Example application in FusionAuth. Select the SAML tab of the application and configure it with the following values.
Enabled True
Issuer IAMShowcase
This is the entityID from the EntityDescriptor node in the metadata provided by IAMShowcase. Here’s the relevant excerpt from the example XML above.
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" entityID="IAMShowcase" validUntil="2025-12-09T09:13:31.006Z">Authorized Redirect URLs https://sptest.iamshowcase.com/acs
This is the Location from the AssertionConsumerService node in the metadata provided by IAMShowcase. Here’s the relevant excerpt from the example XML above.
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sptest.iamshowcase.com/acs" index="0" isDefault="true"/>Signing key Auto generate a new key on save...
Leave all other defaults the same, and click the blue disk icon button to save it.
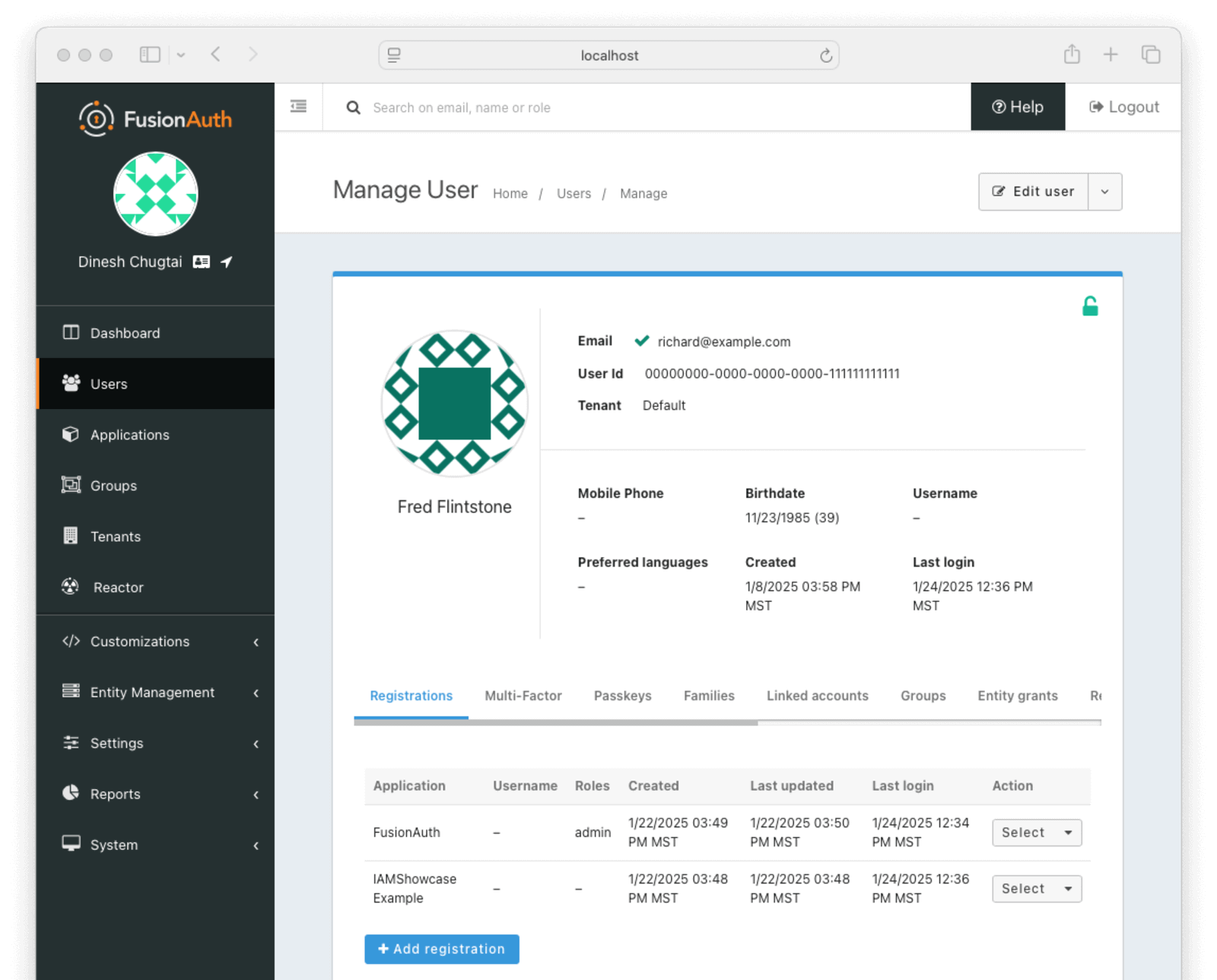
4. Add The User To The IAMShowcase Example Application
Select Users. Choose a user you want to test the SAML log in process with. Select Manage and then click the Add registration button for the IAMShowcase Example application. Click the save icon and you have registered the user for the application.
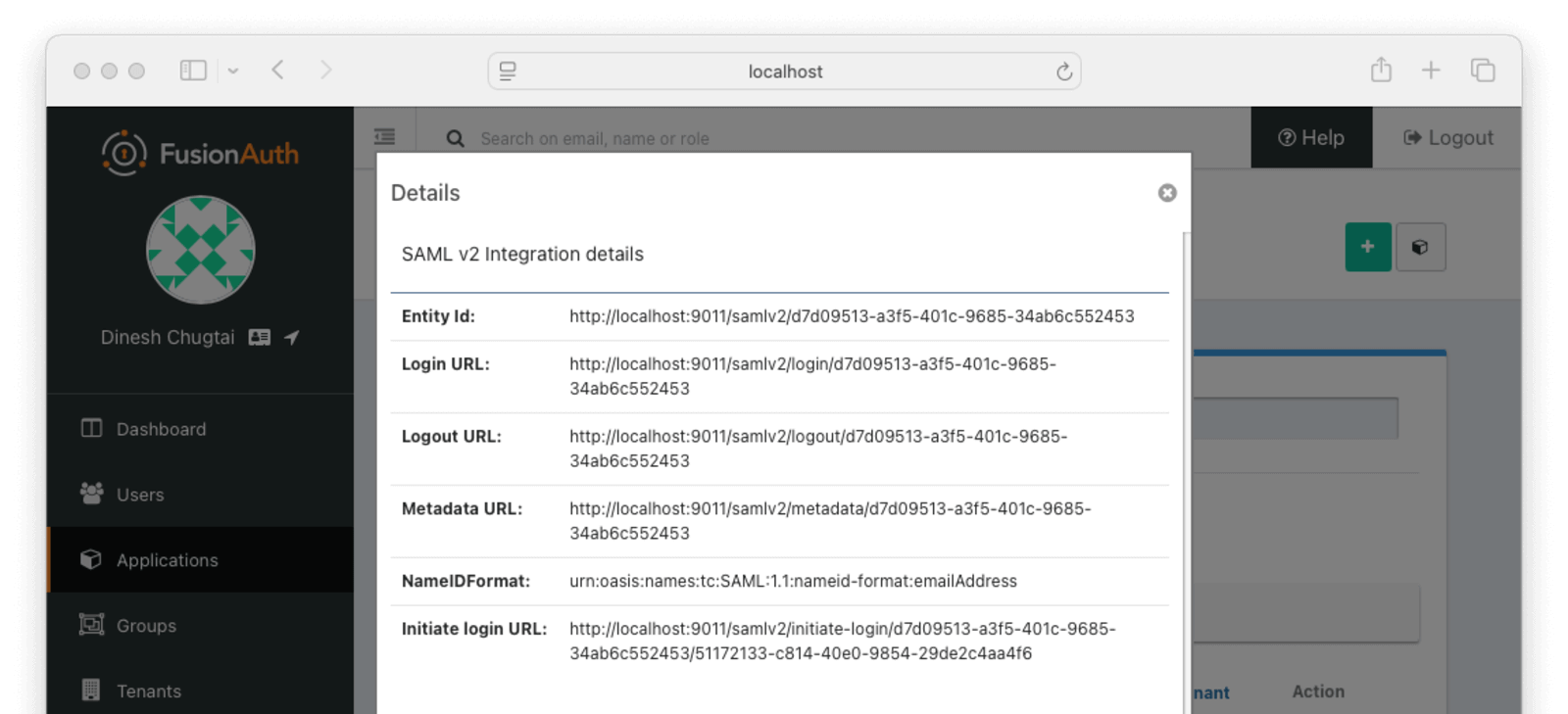
5. Upload The IdP Metadata (For FusionAuth) To The IAMShowcase Site
Now that you’ve told FusionAuth (the IdP) about IAMShowcase (the SP), you need to do the reverse. You have to tell IAMShowcase about FusionAuth.
Click on Applications . Select View for IAMShowcase Example. Scroll down to the SAML v2 integration details section. Copy the Metadata URL and paste that into a new browser window to get the XML metadata.
6. Update The IAMShowcase Site With The Metadata
Paste the XML into the Upload metadata box on the IAMShowcase site. Click Submit XML. Copy the URL that pops up to your clipboard.
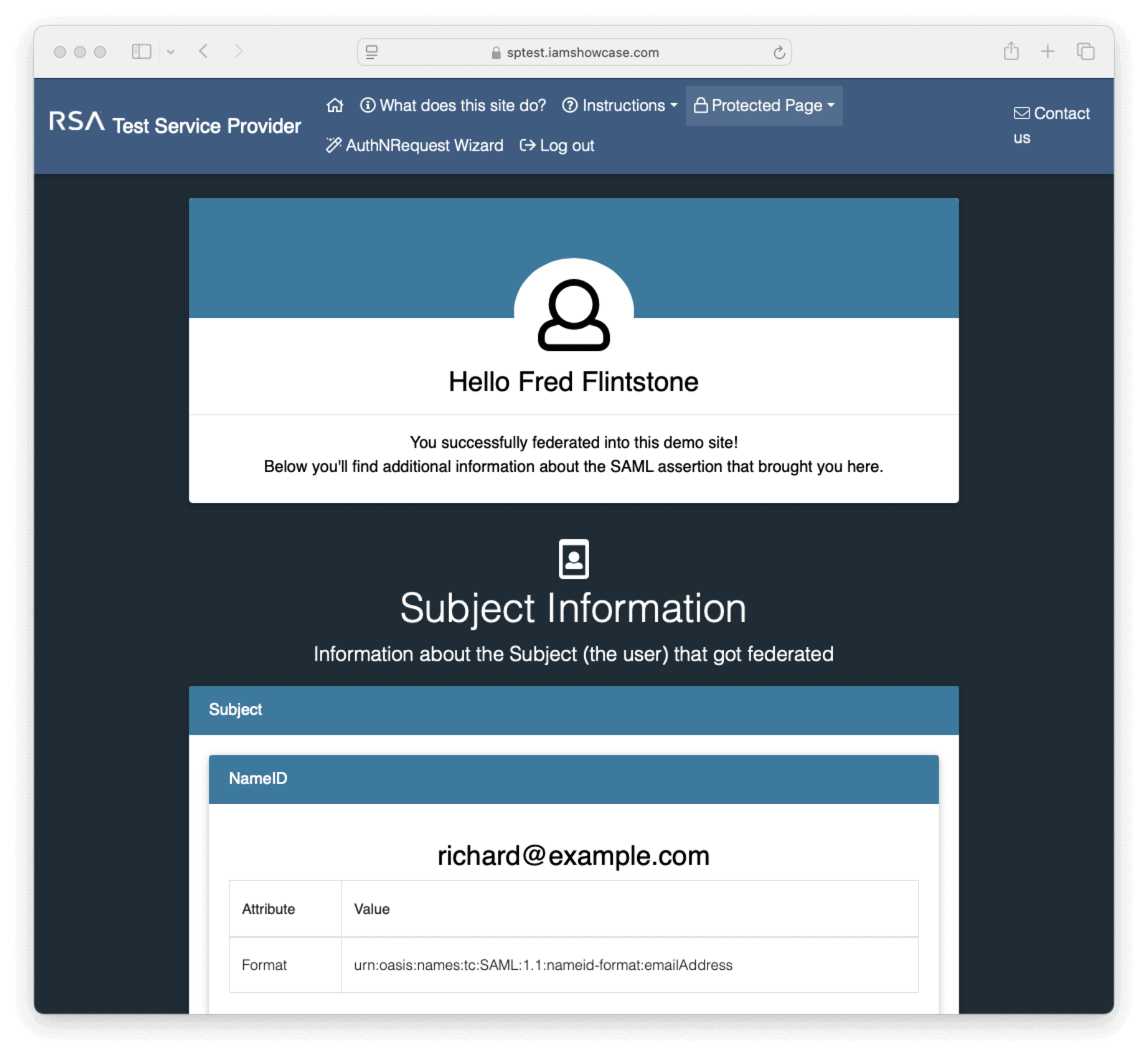
7. See The SAML Workflow In Action
Paste the new URL into a new window in your browser. This will show information for the user that is logged into FusionAuth on the IAMShowcase website.
The flow for this will look like the diagram below:
sequenceDiagram participant User participant SP as IAMShowcase (SP) participant IdP as FusionAuth (IdP) User->>SP: Requests access to resource SP->>SP: Generate SAML AuthnRequest SP->>User: Redirect user to IdP with SAML AuthnRequest User->>IdP: Send SAML AuthnRequest to FusionAuth IdP->>IdP: Authenticate user (e.g., login) IdP->>User: Respond with SAML Assertion User->>SP: Send SAML Assertion to IAMShowcase SP->>SP: Validate SAML Assertion SP->>User: Grant access to resouce
SAML login flow.
Conclusion
SAML might seem intimidating at first. Following these steps is an easy way to make sure that FusionAuth is set up correctly to work with a generic SAML SP. This allows you to test the SAML workflow before integrating FusionAuth with other SAML SPs.
If you are having trouble, set the Debug Enabled toggle to true on the SAML tab. This outputs more information to help you troubleshoot your configuration. You can find the logged information at Logs -> Event Log in the FusionAuth Admin application.

Ensure your SAML configurations are flawless. Schedule a demo to see FusionAuth’s testing tools in action.










