In this blog post we’ll cover the most common grant types used in OAuth 2.0 to ensure security for your applications.
What is OAuth 2.0?#
OAuth 2.0 is a widely-used framework that enables secure, delegated access to resources without exposing user credentials. It allows applications to request access on behalf of users through different authorization flows known as grant types.
Key Attributes of OAuth 2.0 Grants#
Each grant type includes core components that ensure security and standardization:
- Client ID & Client Secret: Identifies the requesting application. Confidential clients use a secret for authentication.
- Authorization Endpoint: Redirects users for authentication and consent.
- Token Endpoint: Issues access tokens upon authorization.
- Redirect URI: Pre-registered URL to prevent redirection attacks.
- Scopes: Defines permissions granted (e.g., openid, email, read:messages).
- Access Token: A temporary credential allowing access to protected resources.
Exploring OAuth 2.0 Grant Types#
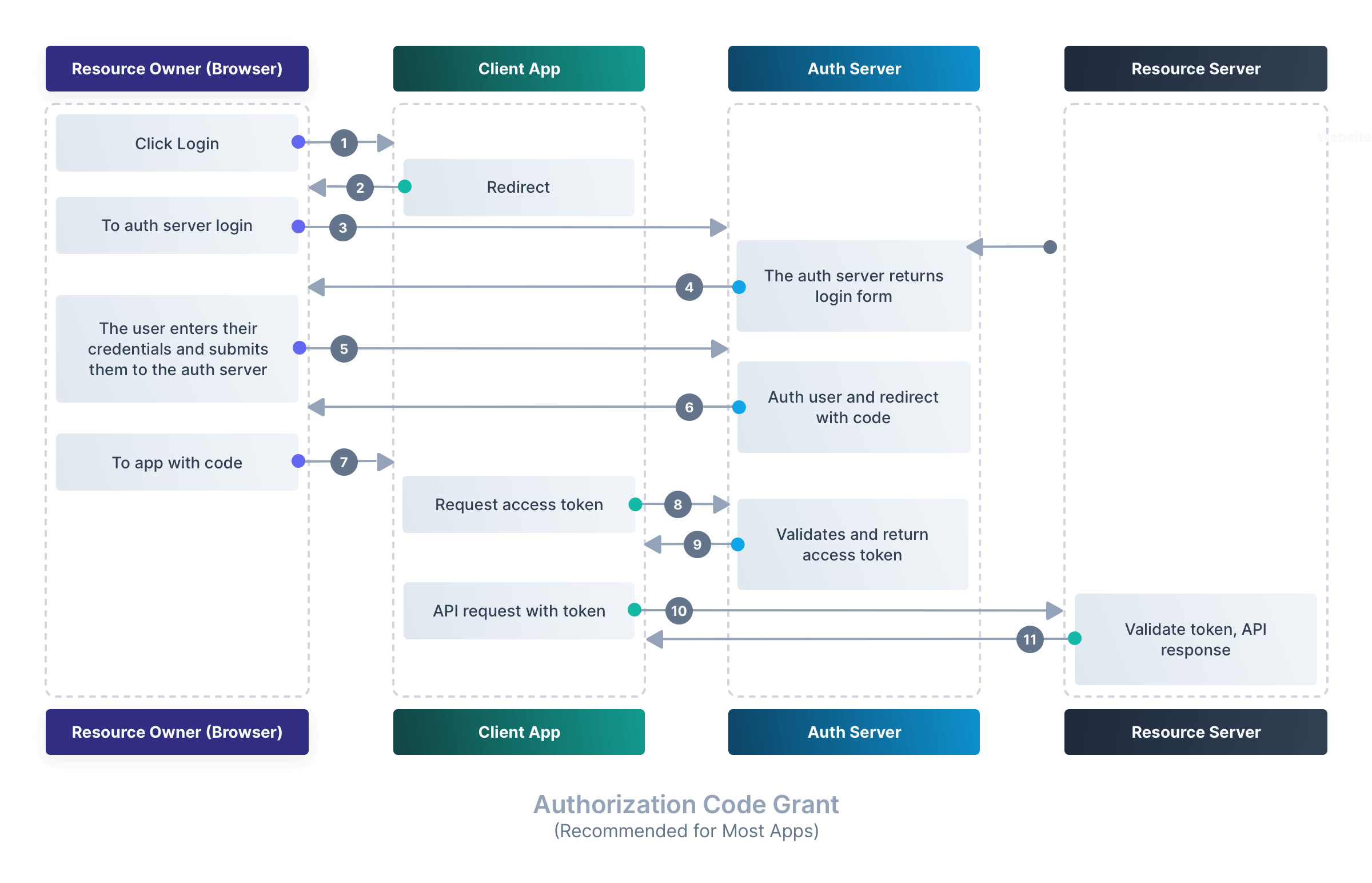
Authorization Code Grant (Recommended for Most Apps)#
Ideal for web and mobile applications with backend servers. The client receives a temporary authorization code, exchanges it for an access token, and secures the communication channel. For a more in-depth look at this grant, see this blog post.
Implicit Grant (Deprecated in OAuth 2.1)#
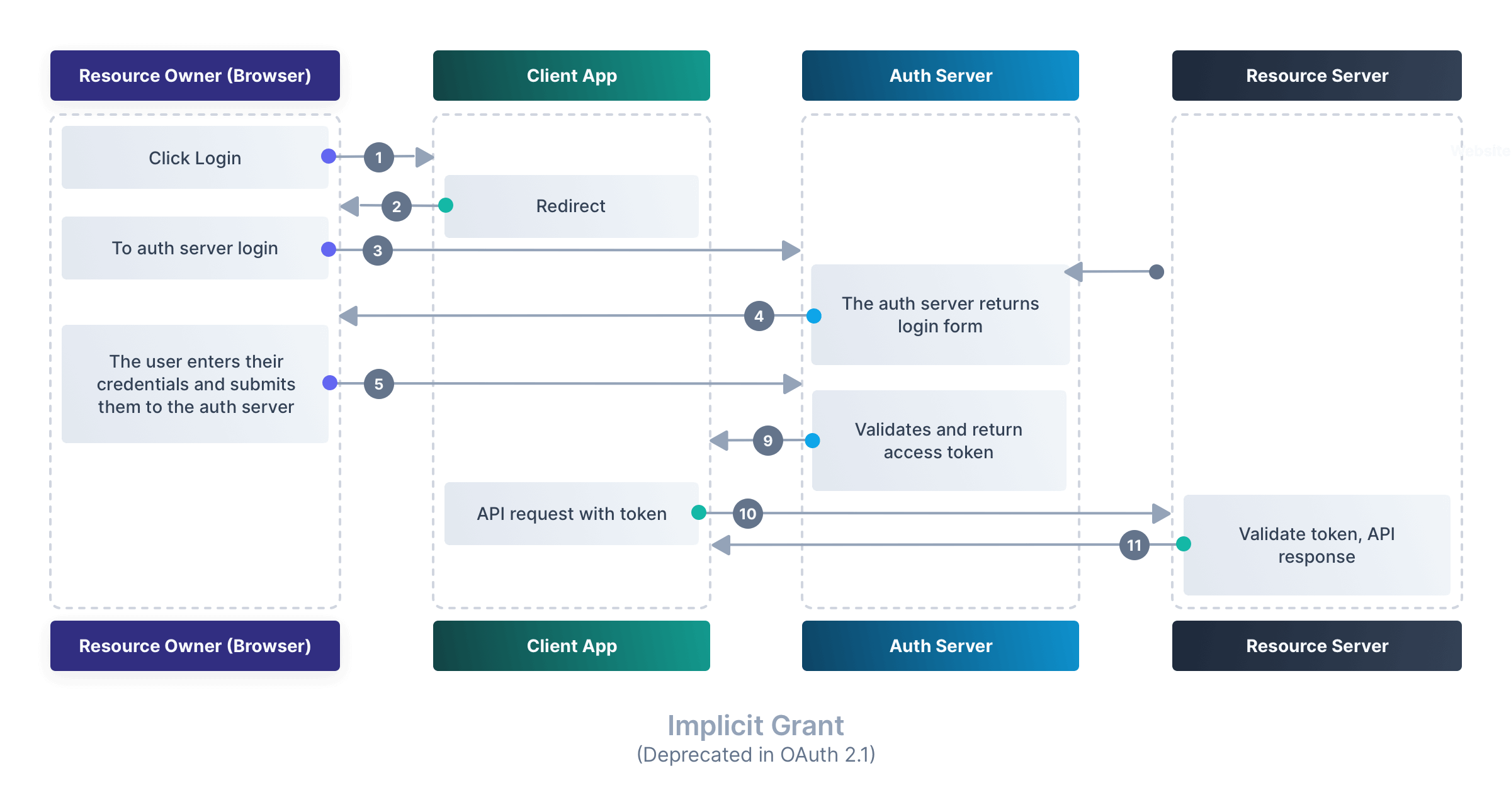
Once used for single-page applications, this flow skips the token exchange step. However, due to security concerns, it is now discouraged in favor of Authorization Code + PKCE.
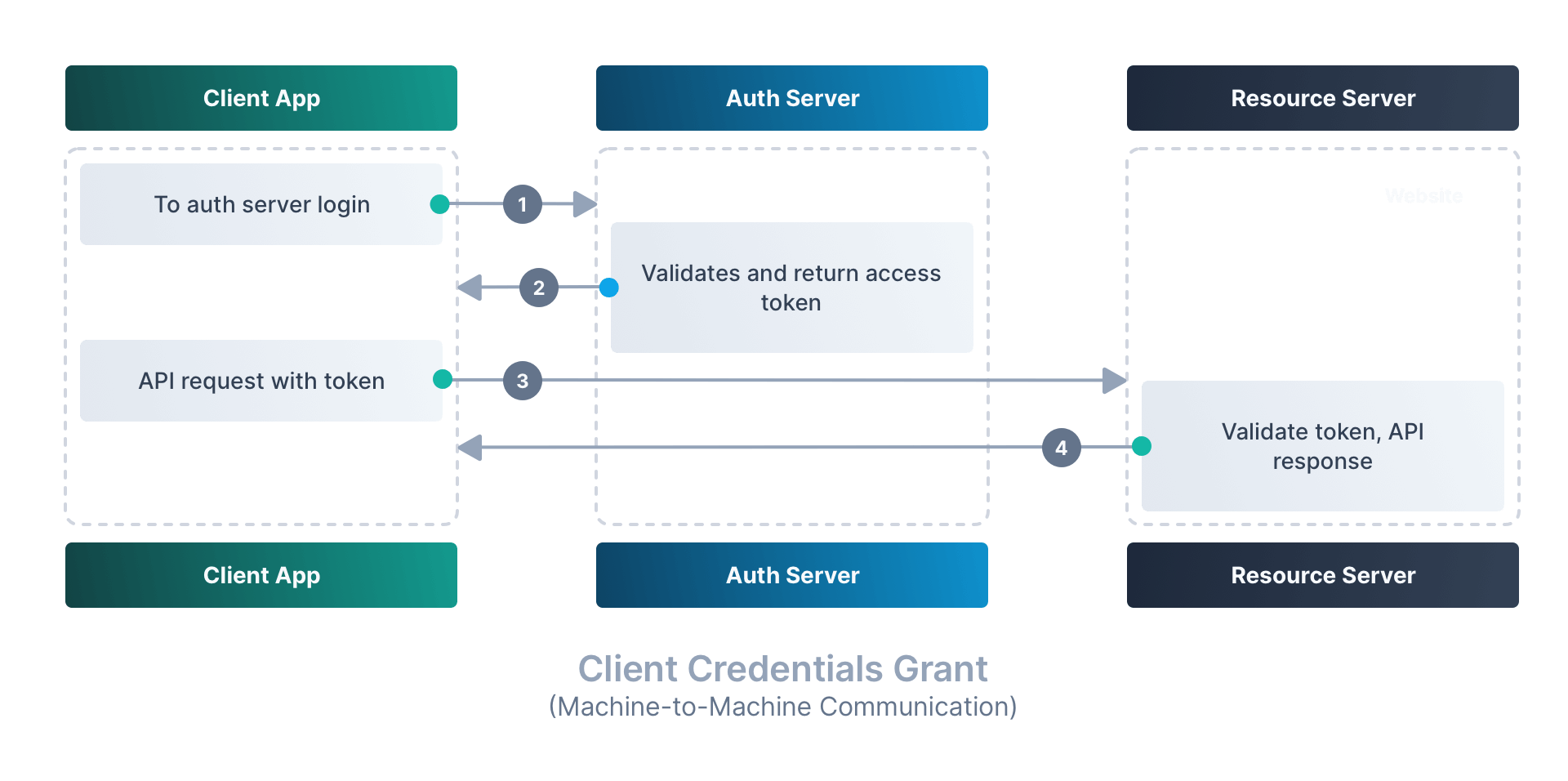
Client Credentials Grant (Machine-to-Machine Communication)#
Used for server-to-server communication where no user is involved. APIs use this to securely exchange credentials and obtain access tokens.
Other Grant Types#
- Resource Owner Password Grant: The Resource Owner Password Grant allows for direct authentication using a username/password (not recommended for modern applications).
- Device Code Grant: Designed for input-limited devices like smart TVs, the Device Code Grant allows users to authenticate via a separate device.
Choosing the Right Grant Type#
To select the best grant type, consider these factors:
- Client Type: Confidential clients (backend apps) vs. public clients (mobile, SPA).
- Security Needs: Use PKCE for public clients and client credentials for machine-to-machine authentication.
- User Experience: Opt for device code flow for limited-input devices and authorization code flow for web apps.
- Use Case Mapping: Web apps favor authorization code, while backend services use client credentials.
Best Practices for Secure OAuth 2.0 Implementation#
- Always use HTTPS to encrypt data in transit.
- Set appropriate token expiration times to minimize risk.
- Never store tokens insecurely.
Example: OAuth 2.0 in Action#
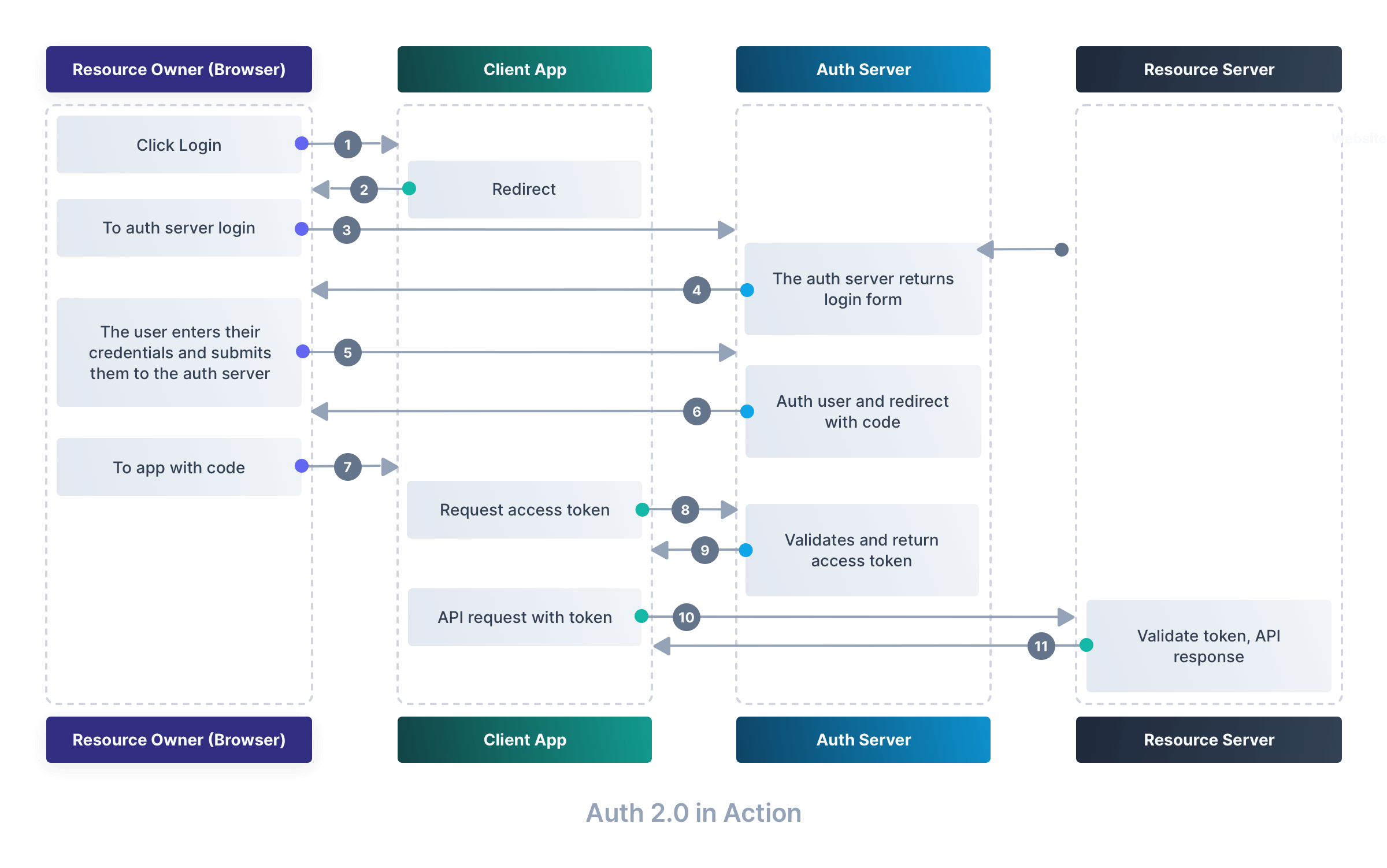
When you sign in using the Authorization Code Grant in FusionAuth, here’s what happens:
- The user visits a page to login to your system
- The user is redirected to FusionAuth’s auth servers to login, and the redirect URL is called with a code.
- The application exchanges the code for an access token—now it can securely access your data!
Conclusion#
OAuth 2.0 is a powerful framework that, when properly implemented, ensures secure authentication and authorization for web apps, APIs, and devices. Choosing the right grant type depends on your application’s security and usability needs.
For a deeper dive, check out the Modern Guide to OAuth.