Tenants
Overview
FusionAuth is fundamentally a single tenant solution, so you may be surprised to learn that we support multiple tenants.
FusionAuth will always be a single tenant solution, this means that your instance of FusionAuth is your own and even when FusionAuth is hosting, we do not co-mingle your data with other clients. FusionAuth was built as a single tenant solution, and we have no plans to change anytime soon.
It is entirely likely that our clients may wish to be multi-tenant or offer their services to more than one client. In these scenarios it may be useful to separate Users, Applications and Groups for each of your clients.
For example, let’s assume you are building a payroll offering using a SaaS model. In this case it is possible that monica@piedpiper.com works for two of your clients, Acme Corp and The Umbrella Company. Because Monica is not aware that Acme Corp and The Umbrella Company both are buying their Payroll software from the same vendor it would be surprising for Monica to share the same password and account details between these two companies. In this scenario you would likely want to utilize the FusionAuth Tenant to ensure that monica@piedpiper.com exists once for each instance of your Payroll offering.
See Tenant API Authentication for more details about making API requests in a multi-tenant configuration.
Here’s a brief video covering some aspects of tenants:
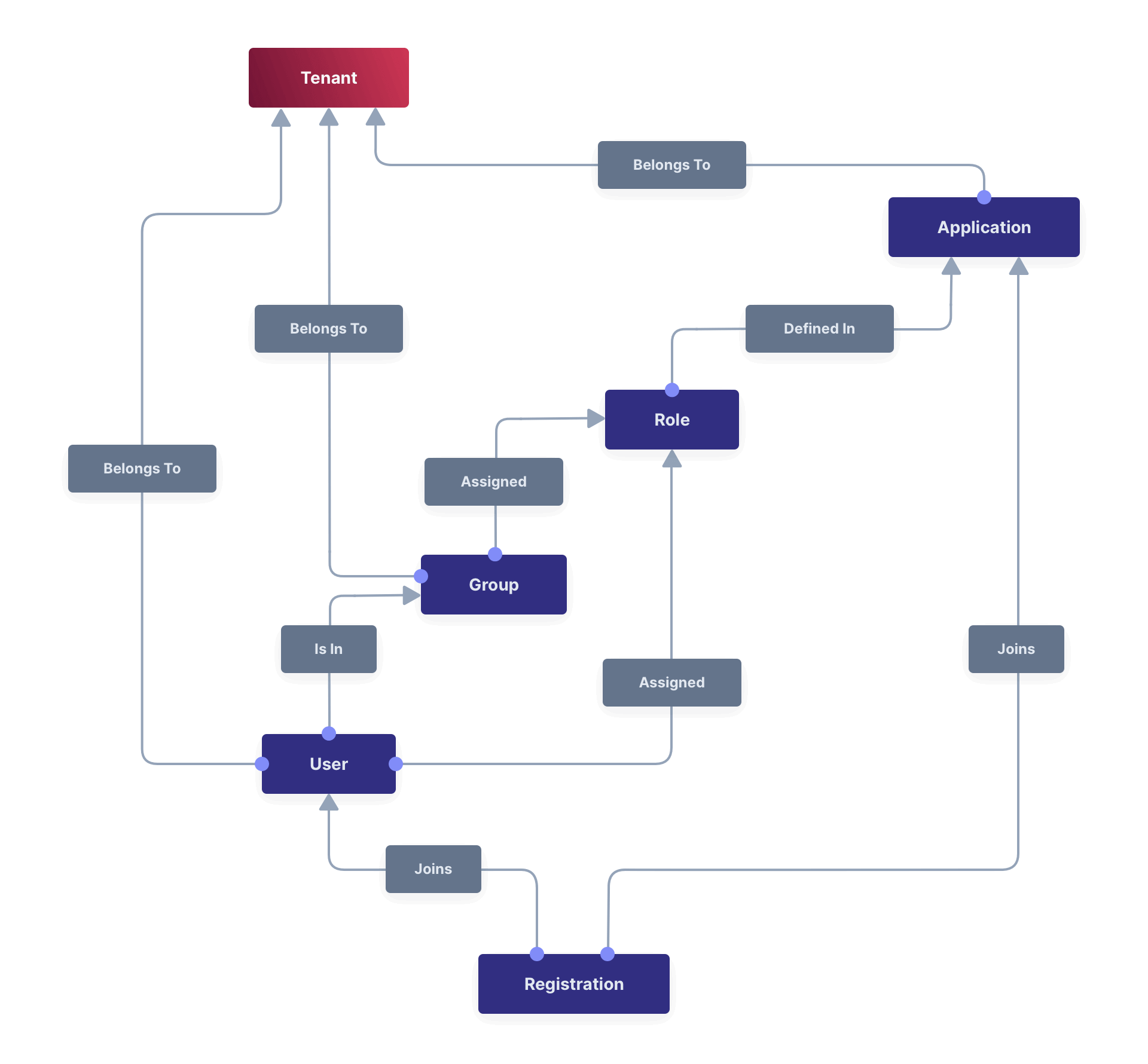
Core Concepts Relationships
Below is a visual reminder of the relationships between FusionAuth’s primary core concepts.
Admin UI
This page describes the admin UI for creating and configuring a Tenant.
List of Tenants
To display a list of tenants, navigate to Tenants .
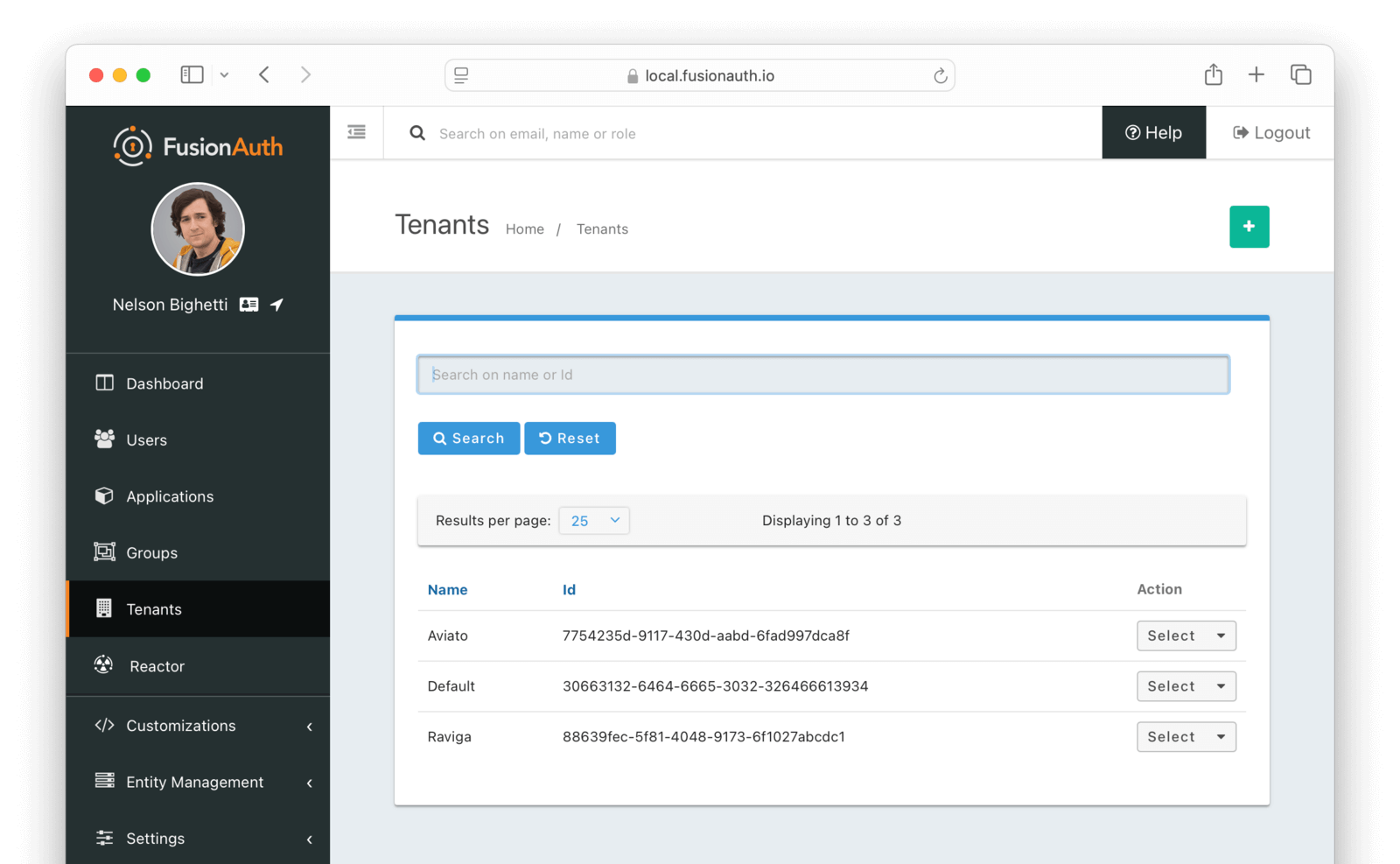
Using the icons on this screen, you can:
- Create a new tenant
- Delete the tenant configuration
- You cannot delete the Default tenant.
- Duplicate the tenant configuration
- Edit the tenant configuration
- View the tenant configuration
Create a Tenant
To create a new tenant, navigate to Tenants .
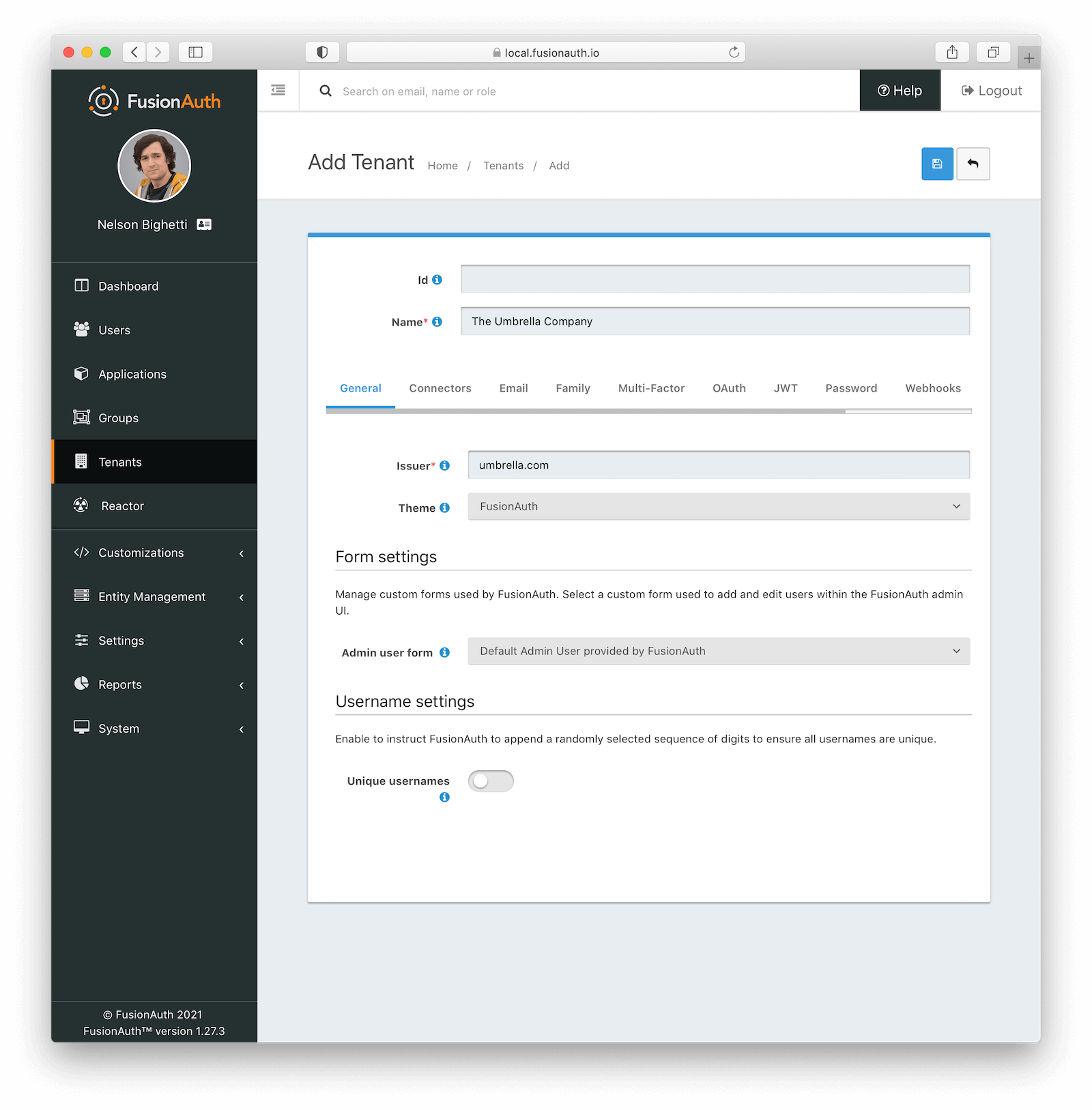
Tenant Configuration
A majority of your FusionAuth configuration is managed at the Tenant-level. Some of these configuration options act as defaults and can be overridden by the Application.
General
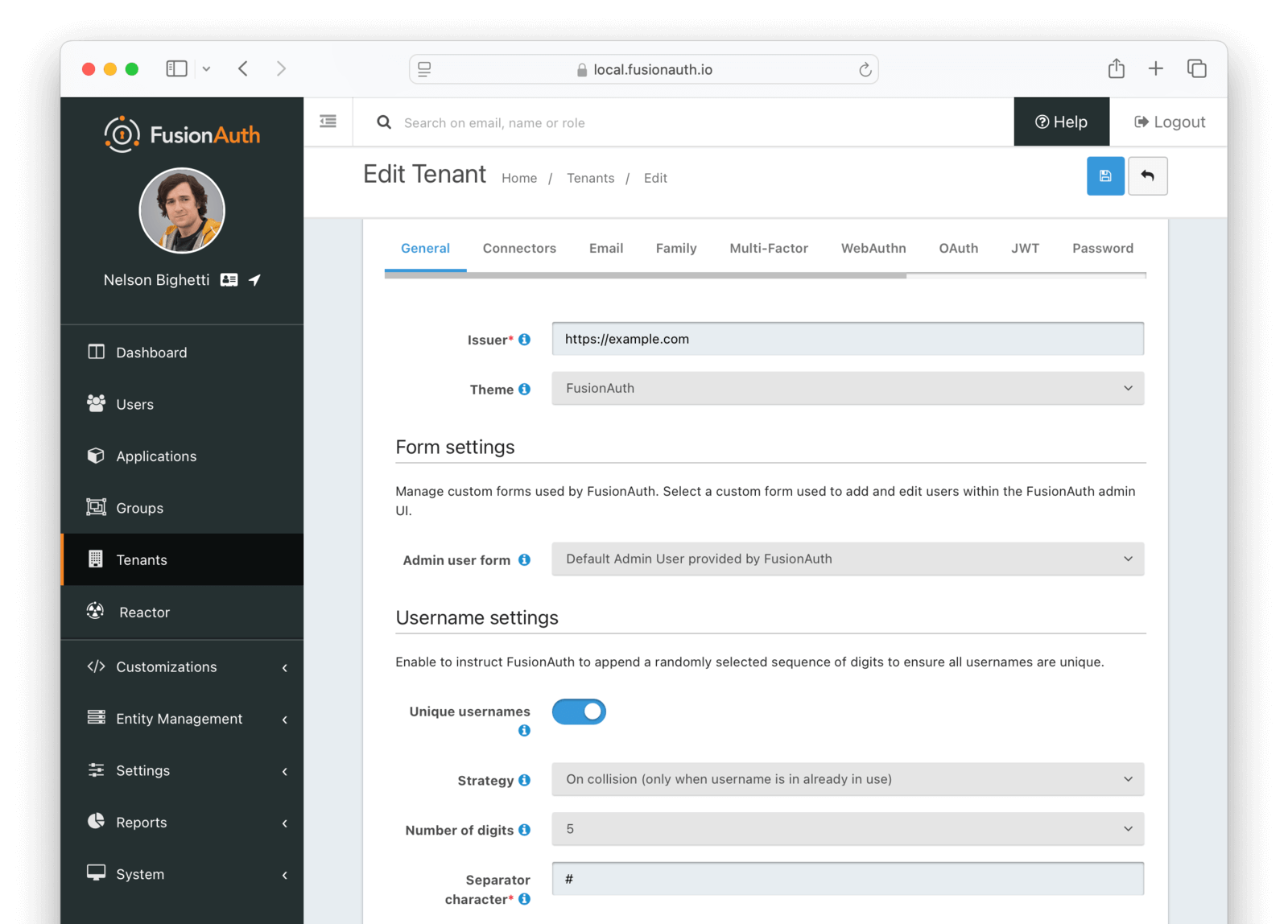
Form Fields
IssuerrequiredThe named issuer used to sign tokens. This is generally your public fully qualified domain with the https:// protocol prefix. For example, https://example.com.
Login ThemeThe Theme associated with this Tenant; determines which templates to render for interactive work-flows.
Form Settings
Admin user formAvailable since 1.20.0The form that will be used in the FusionAuth UI for adding and editing users.

This feature is only available in paid plans. Please visit our pricing page to learn more.
Username settings
Enable Unique usernames to allow multiple users suggest the same username. If there are any collisions, FusionAuth will transparently create a unique username by appending a suffix. The user will continue to use the username without the suffix.
Unique usernamesDefaults to falseAvailable since 1.27.0When true, FusionAuth will handle username collisions.

This feature is only available in paid plans. Please visit our pricing page to learn more.
Number of digitsDefaults to 5Available since 1.27.0The maximum number of digits to use when building a unique suffix for a username. A number will be randomly selected and may be 1 or more digits up to this configured value. The value of this field must be greater than or equal to 3 and less than or equal to 10.
Separator characterAvailable since 1.27.0A single character to use as a separator from the requested username and a unique suffix that is added when a duplicate username is detected. This value can be a single non alphanumeric ASCII character.
Connectors
Connectors can be enabled on a per tenant basis with a Connector policy.
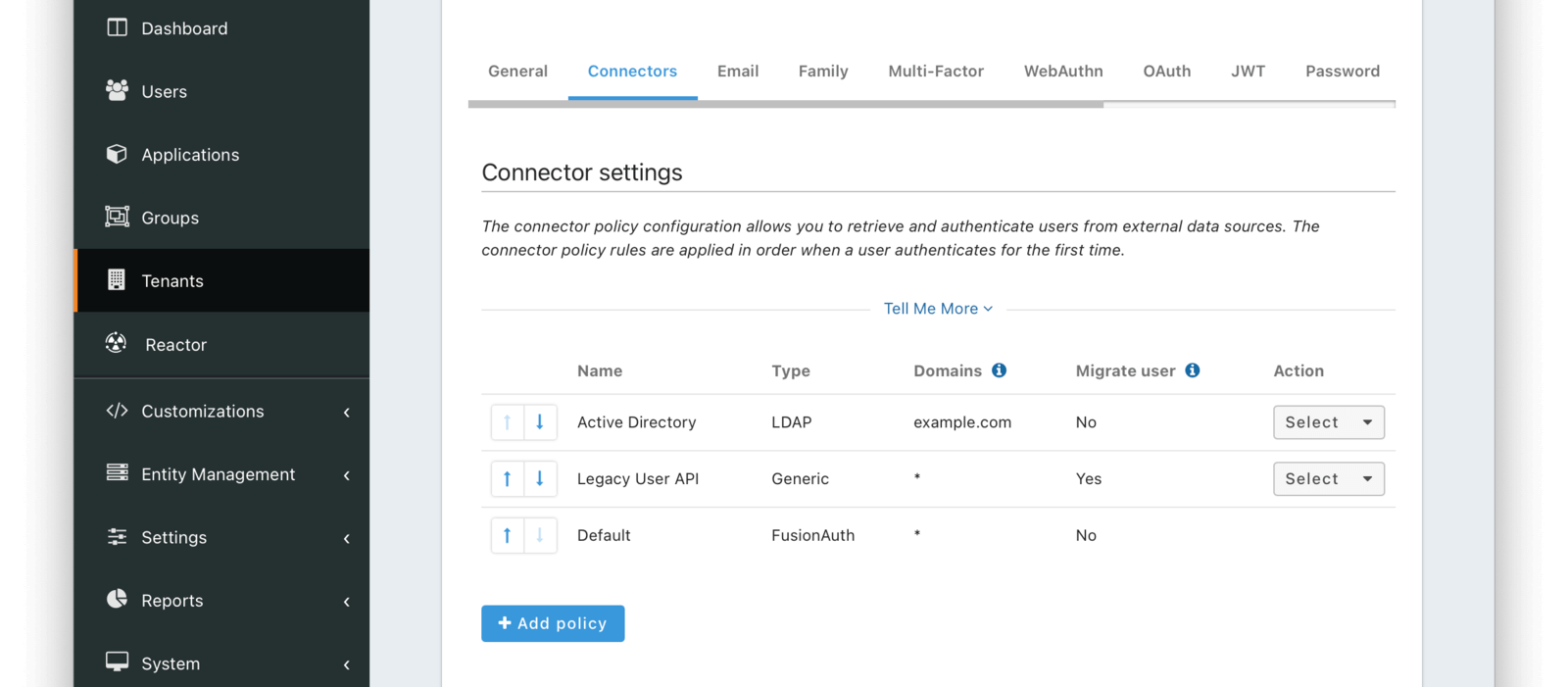
You can find details on adding a connector below. Full documentation on Connectors and Connector Policies can be found here.
Add Connector Policy Dialog
If you click on the Add policy button on this page you will be presented with the following dialog.
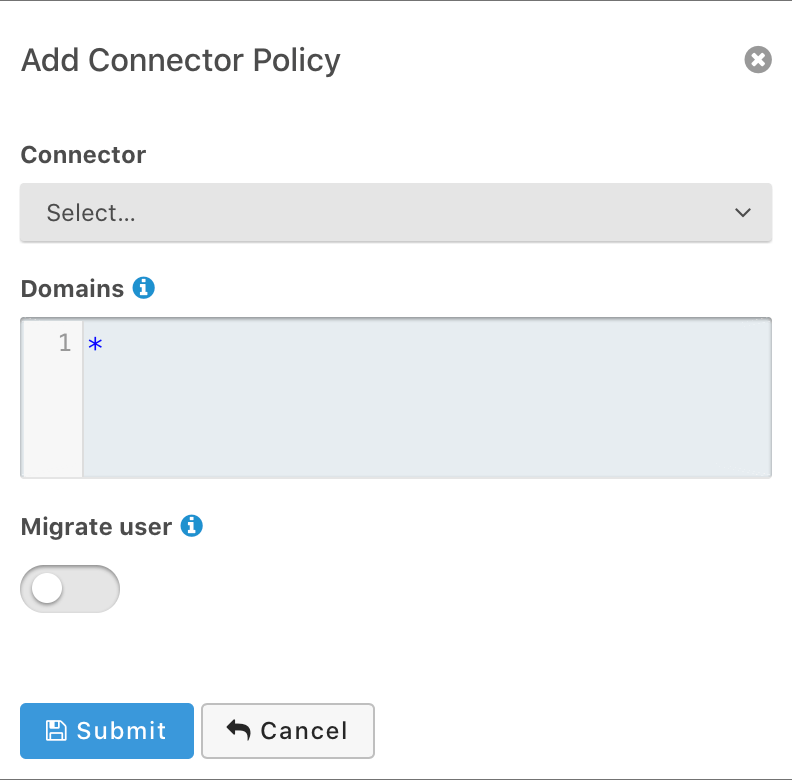
Form Fields
ConnectorrequiredThe Connector to be used for this policy.
DomainsDefaults to ["*"]One or more line separated domains to be used to filter incoming authentication requests. To match all incoming email addresses, a single entry using an asterisk * can be used.
Migrate userWhen selected, migrate the user from the Connector into FusionAuth so that future authentications will use FusionAuth and not the Connector.
Once you have configured your email settings, you may test your configuration with the Send test email button.
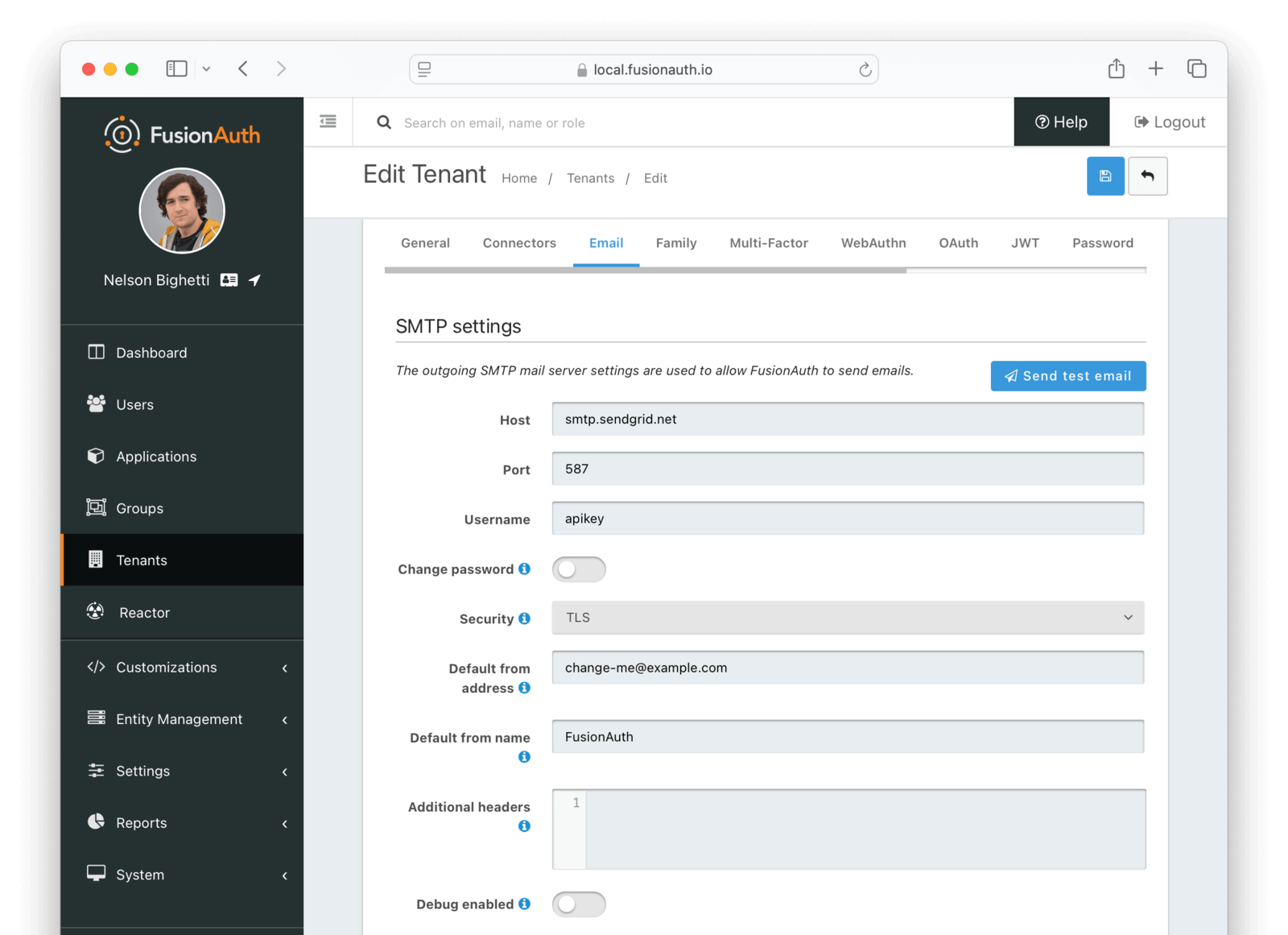
SMTP settings
HostDefaults to localhostThe hostname of the SMTP server. This will be provided by your SMTP provider.
PortDefaults to 25The port of the SMTP server. This will be provided by your SMTP provider. Ports 25, 465 and 587 are the well known ports used by SMTP, it is possible your provider will utilize a different port.
In most cases you will be using TLS to connect to your SMTP server, and the port will generally be 587 or 465.
UsernameThe username of the outgoing SMTP mail server authentication.
Change passwordWhen enabled, you may modify the SMTP password, when the Password field is not displayed the current password will not be modified.
PasswordrequiredThe new password to use for the outgoing SMTP mail server authentication. This field is only required when Change password is checked.
When using duplicating Tenants, the SMTP password is not copied. You will have to enter this manually before sending emails.
SecurityDefaults to NoneThe security type when using an SSL connection to the SMTP server. This value should be provided by your SMTP provider.
Generally speaking, if using port 25 you will select None, if using port of 465 you will select SSL and if using port 587 you will select TLS. It is possible your provider will be different, follow your providers instruction.
NoneSSLTLS
Default from addressThe default email address that emails will be sent from when a from address is not provided on an individual email template. This is the address part email address (i.e. Jared Dunn jared@piedpiper.com).
Default from nameThe default From Name used in sending emails when a from name is not provided on an individual email template. This is the display name part of the email address ( i.e. Jared Dunn jared@piedpiper.com).
Additional HeadersAvailable since 1.32.0One or more line separated SMTP headers to be added to each outgoing email. The header name and value should be separated by an equals sign. ( i.e. X-SES-CONFIGURATION-SET=Value).
Debug enabledAvailable since 1.37.0When enabled SMTP and JavaMail debug information will be output to the Event Log.
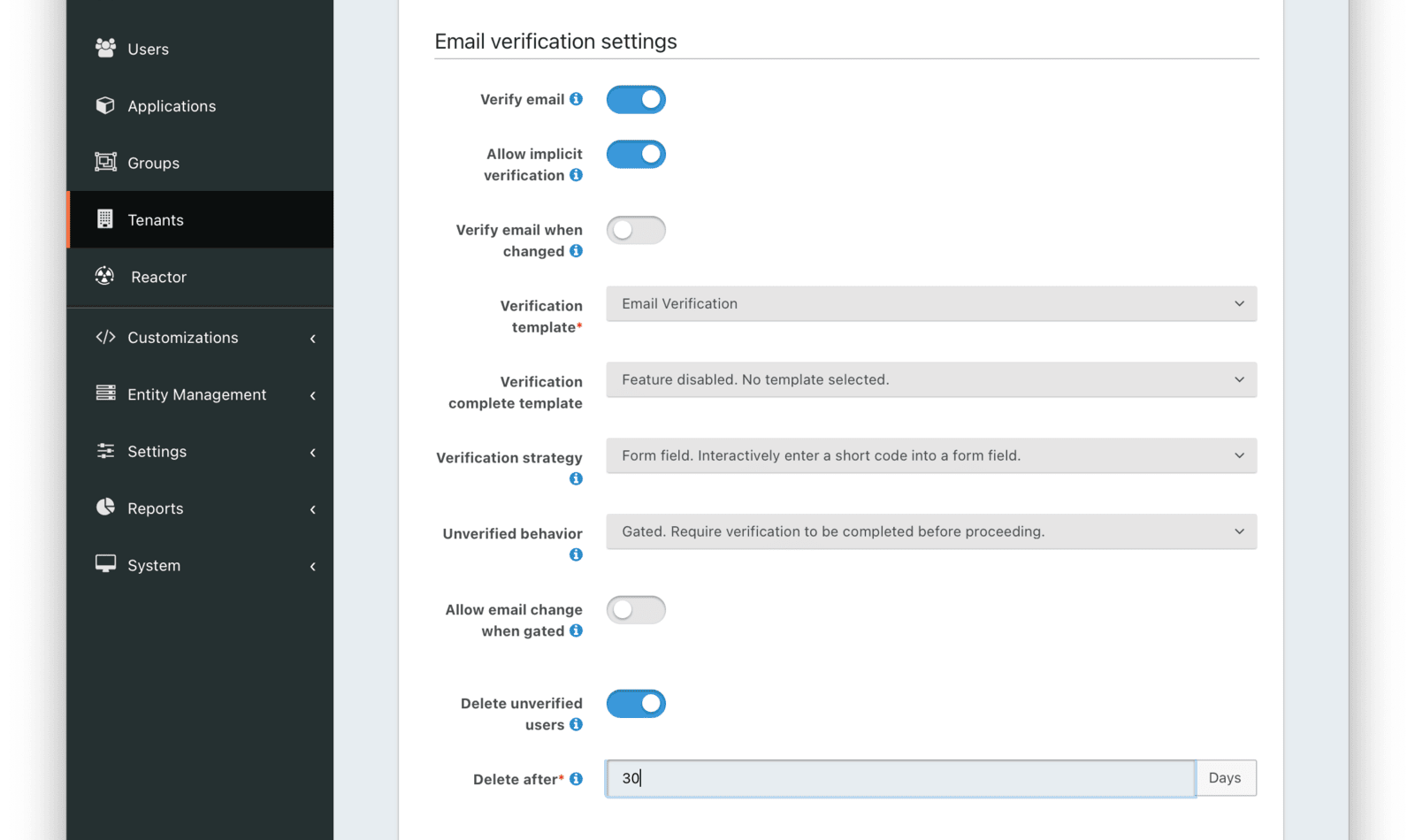
Email verification settings
Verify emailWhen enabled, users will be required to verify their email address.
Allow implicit verificationWhen enabled, this allows a user’s email address to be verified as a result of completing a similar based email workflow such as change password.
Verify email when changedWhen enabled, users will be required to verify their email address upon update.
Verification templaterequiredThe email template to use when accounts are created to verify the User’s email address.
Required when the Verify email toggle is enabled.
Verification complete templateAvailable since 1.30.0The email template to use when notifying a user that email address has been verified.
Verification strategyAvailable since 1.27.0The process by which the user will verify their email address. Using the “Form Field” method works only when the Unverified behavior is Gated.
Unverified behaviorAvailable since 1.27.0The way a user is handled during the login process when they do not have a verified email address.
Allow email change when gatedAvailable since 1.27.0When enabled, the user is allowed to change their email address when they are gated because they haven’t verified their email address.
Delete unverified usersWhen enabled, users who have not verified their email address after a configurable duration since being created will be permanently deleted.
Delete afterrequiredThe duration since creation that a user must exist before being deleted for having an unverified email address.
Required when the Delete unverified users toggle is enabled.
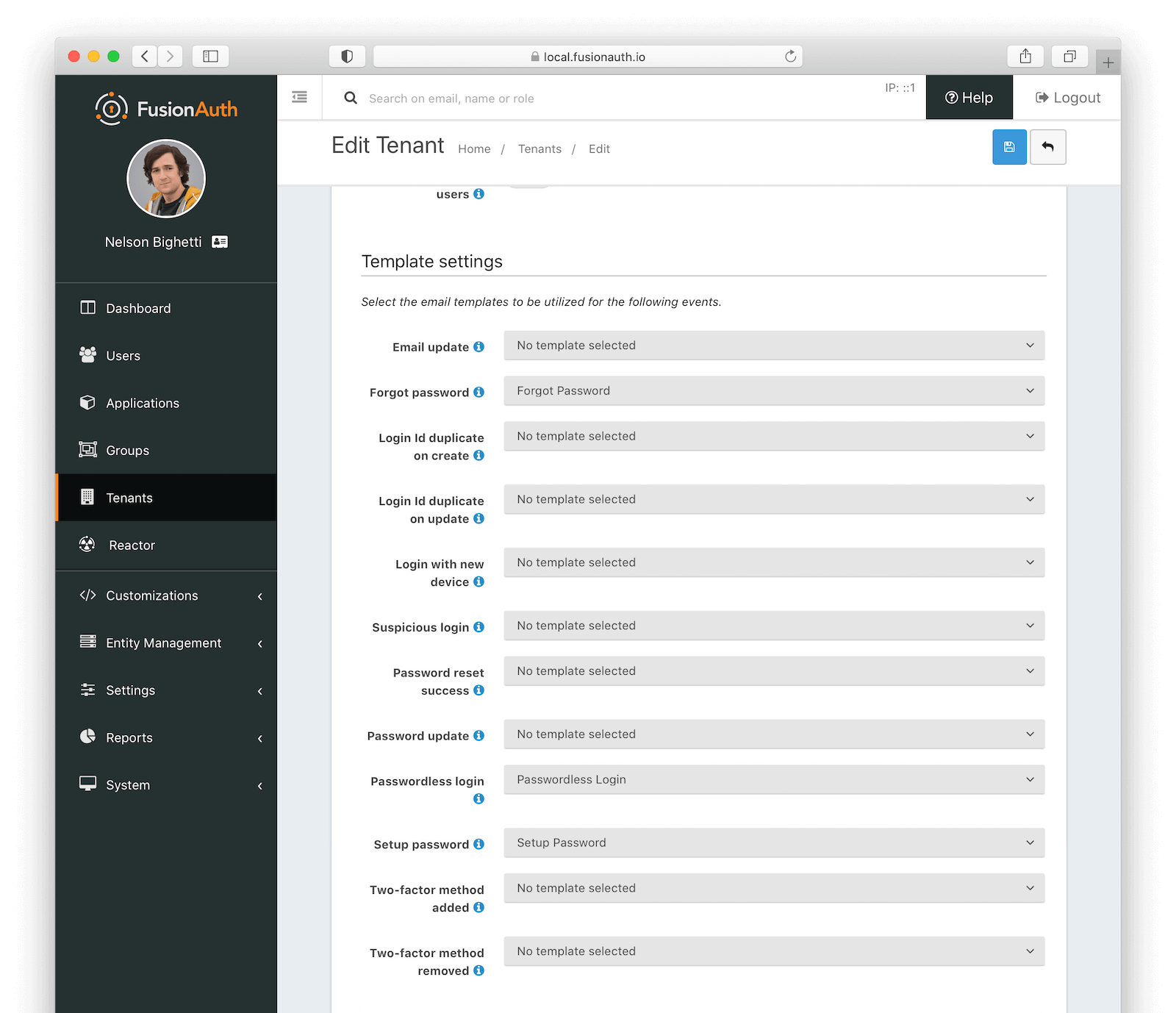
Template settings
Email updateAvailable since 1.30.0The email template to use when notifying a user that their email address has been updated.
Note: An Enterprise plan is required to utilize this feature.
Email verifiedAvailable since 1.30.0The email template to use when notifying a user that email address has been verified.
Note: An Enterprise plan is required to utilize this feature.
Forgot passwordThe email template to use for the forgot password workflow.
Login Id duplicate on createAvailable since 1.30.0The email template to use when notifying a user that another user has attempted to register an account with the same username or email address as they have. If user Richard has an email richard@piedpiper.com and a new user tries to register with the email address richard@piedpiper.com, then user Richard will be notified.
Note: An Enterprise plan is required to utilize this feature.
Login Id duplicate on updateAvailable since 1.30.0The email template to use when notifying a user that another user has attempted to change their own email or username to a value in-use by the user.
Note: An Enterprise plan is required to utilize Login Id duplicate on update.
Login with new deviceAvailable since 1.30.0The email template to use when notifying a user that a new device was used to login.
Note: An Enterprise plan is required to utilize Login with new device.
Suspicious loginAvailable since 1.30.0The email template to use when notifying a user that a login occurred and it was determined to be of interest or suspect due to the location, IP address or other factors.
Note: An Enterprise plan is required to utilize Suspicious login.
Password reset successAvailable since 1.30.0The email template to use when notifying a user that their password has been successfully updated using the reset workflow.
Note: An Enterprise plan is required to utilize Password reset success.
Password updateAvailable since 1.30.0The email template to use when notifying a user that their password has been successfully updated. This is different from Password reset success in that this event occurs outside of the reset workflow.
Note: An Enterprise plan is required to utilize Password update.
Passwordless loginThe template to use to send the link for passwordless login requests.
Setup passwordThe email template to use when accounts are created and the user needs to setup their password.
Two-factor method addedAvailable since 1.30.0The email template to use when notifying a user that a new two-factor method has been successfully added.
Note: An Enterprise plan is required to utilize Two-factor method added.
Two-factor method removedAvailable since 1.30.0The email template to use when notifying a user that a previously configured two-factor method has been successfully removed.
Note: An Enterprise plan is required to utilize Two-factor method removed.
Family
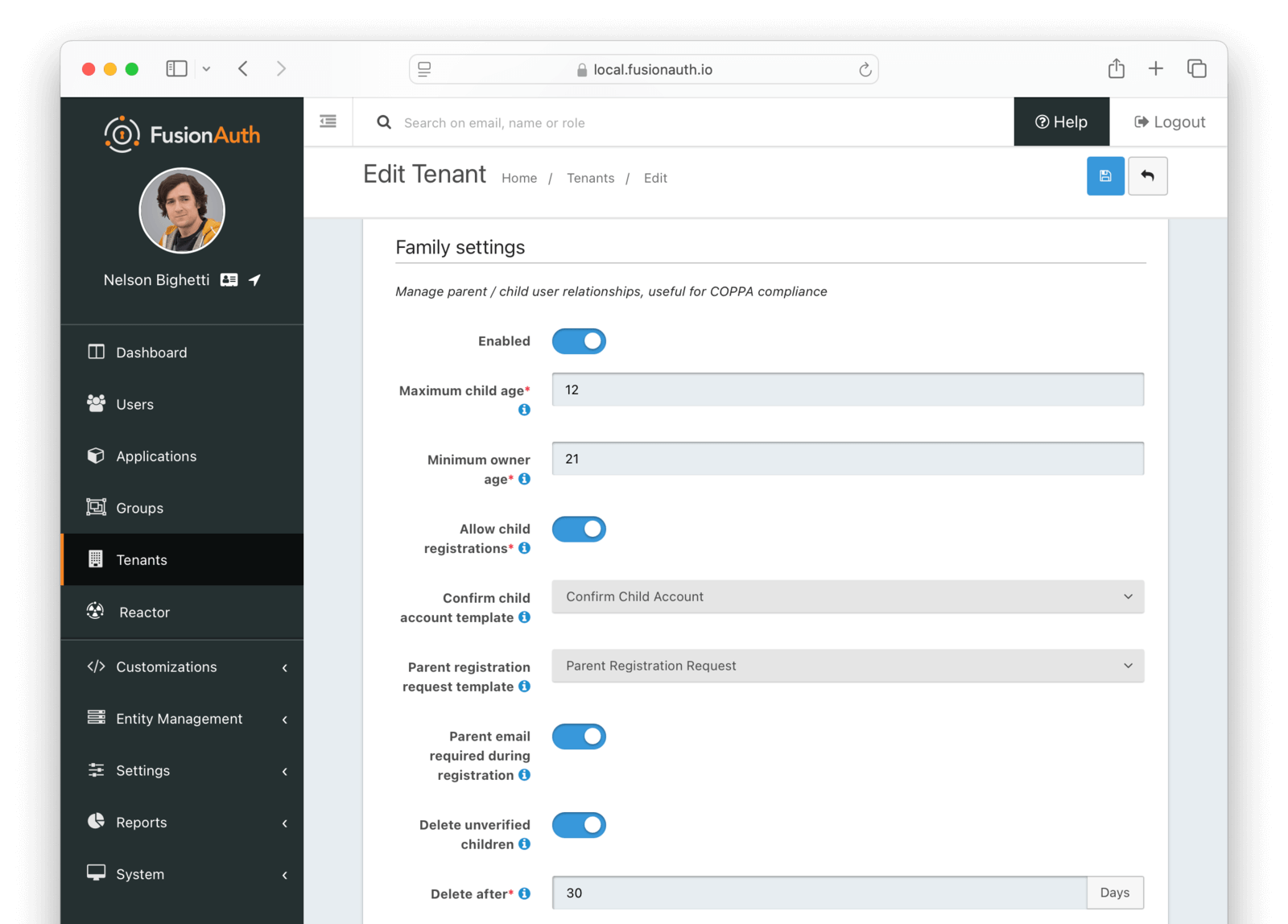
Form Fields
EnabledWhen enabled, you may model parent-child user relationships, and observe parental approval and age validation on user creation.
Maximum child agerequiredThe maximum age a user can be to be considered a child.
Required when the Enabled toggle is enabled.
Minimum owner agerequiredThe minimum age a user must be to create a family.
Required when the Enabled toggle is enabled.
Allow child registrationsrequiredWhen enabled, allow children to register themselves without requiring a parent to create their account for them.
Family request templateThe email template used when children are not able to register themselves and they are asking their parent to create them an account.
Confirm child account templateThe email template used when a parent needs to confirm a child account before it is activated as part of their family.
Parent registration request templateThe email template used when a child is requesting that their parent create an account (because it is not created automatically).
Parent email required during registrationWhen enabled, child users must provide their parent’s email address during the registration process.
Delete unverified childrenWhen enabled, child user accounts that have not been verified by a parent after a configured period will be automatically deleted.
Delete afterrequiredThe number of days before a child account that has not yet been verified by a parent is automatically deleted.
Required when the Delete unverified children toggle is enabled.
Multi-Factor

This feature is only available in paid plans. Please visit our pricing page to learn more.
Note: The Authenticator/TOTP implementation is not a premium feature, and is included in the Community version. Email and SMS require the Advanced Multi-Factor feature available when purchasing a paid plan.
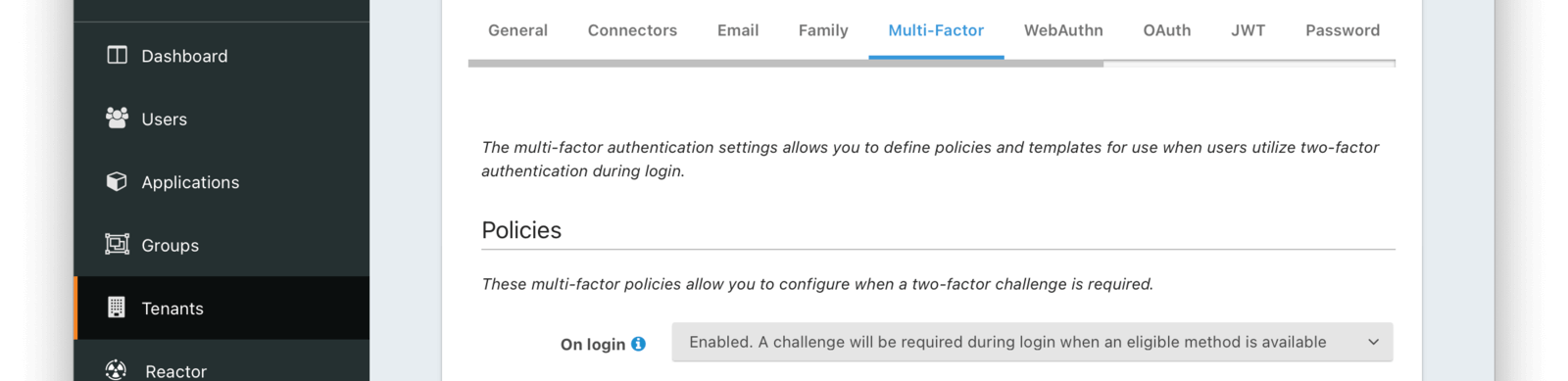
Policies
On loginWhen set to Enabled, a two-factor challenge will be required during login when a user has configured one or more two-factor methods. When set to Disabled, even when a user has one or more two-factor methods configured, a two-factor challenge will not be required during login. When set to Required, a two-factor challenge will be required during login. If a user does not have configured two-factor methods, they will not be able to log in.
Supported values include:
- Enabled. A challenge will be required during login when an eligible method is available.
- Disabled. A challenge will not be required during login.
- Required. A challenge will be required during login. Available since 1.42.0
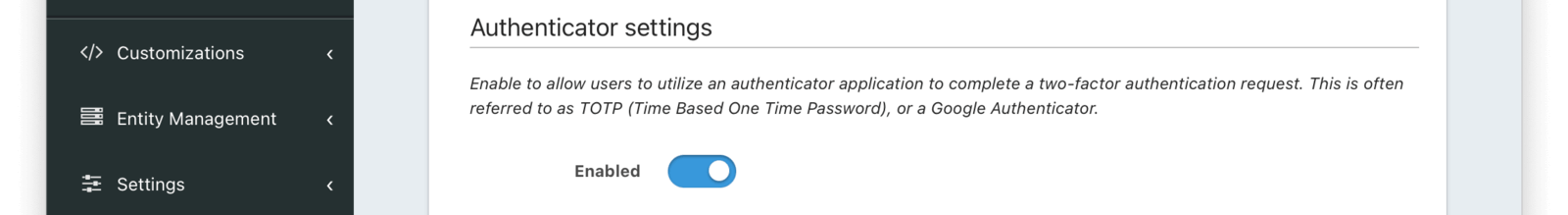
Authenticator settings
EnabledWhen enabled, users may use an authenticator application to complete a multi-factor authentication request.
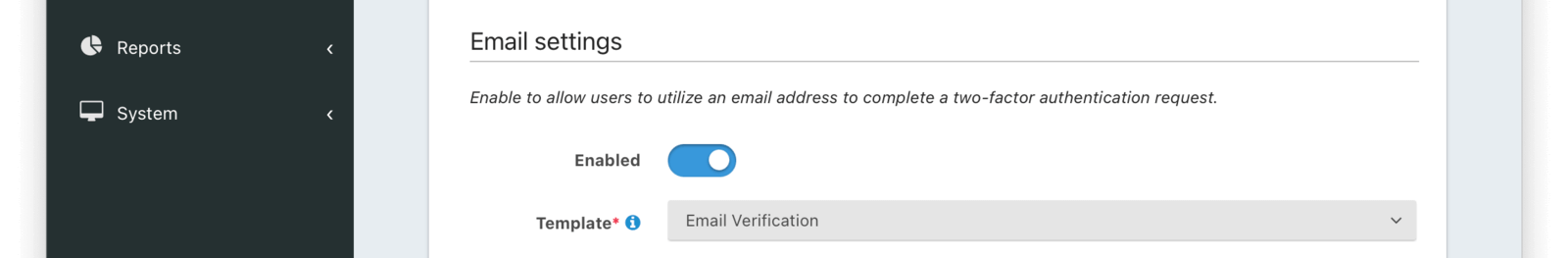
Email settings
EnabledWhen enabled, users may use an email address to complete a multi-factor authentication request.
TemplaterequiredThe email template to use when a multi-factor authentication request is sent to the User’s email address.
Required when the Enabled toggle is enabled.
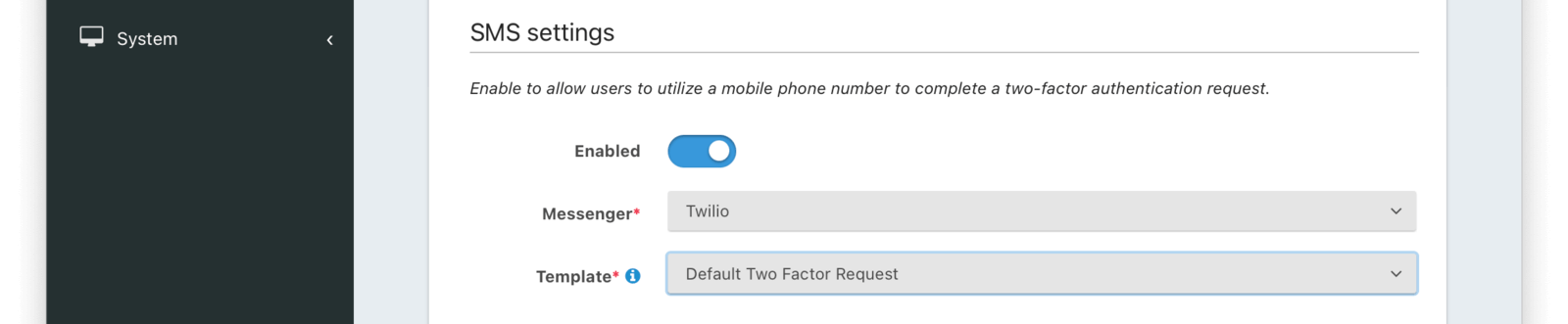
SMS settings
EnabledWhen enabled, users may use a mobile phone number to complete a multi-factor authentication request.
MessengerrequiredThe Messenger used to deliver the template.
Required when the Enabled toggle is enabled.
TemplaterequiredThe SMS template to use when a multi-factor authentication request is sent to the User’s mobile phone number.
Required when the Enabled toggle is enabled.
WebAuthn

This feature is available to licensed FusionAuth instances as of version 1.52.0. A free license is available in the Plan tab for any user who registers in the account portal.
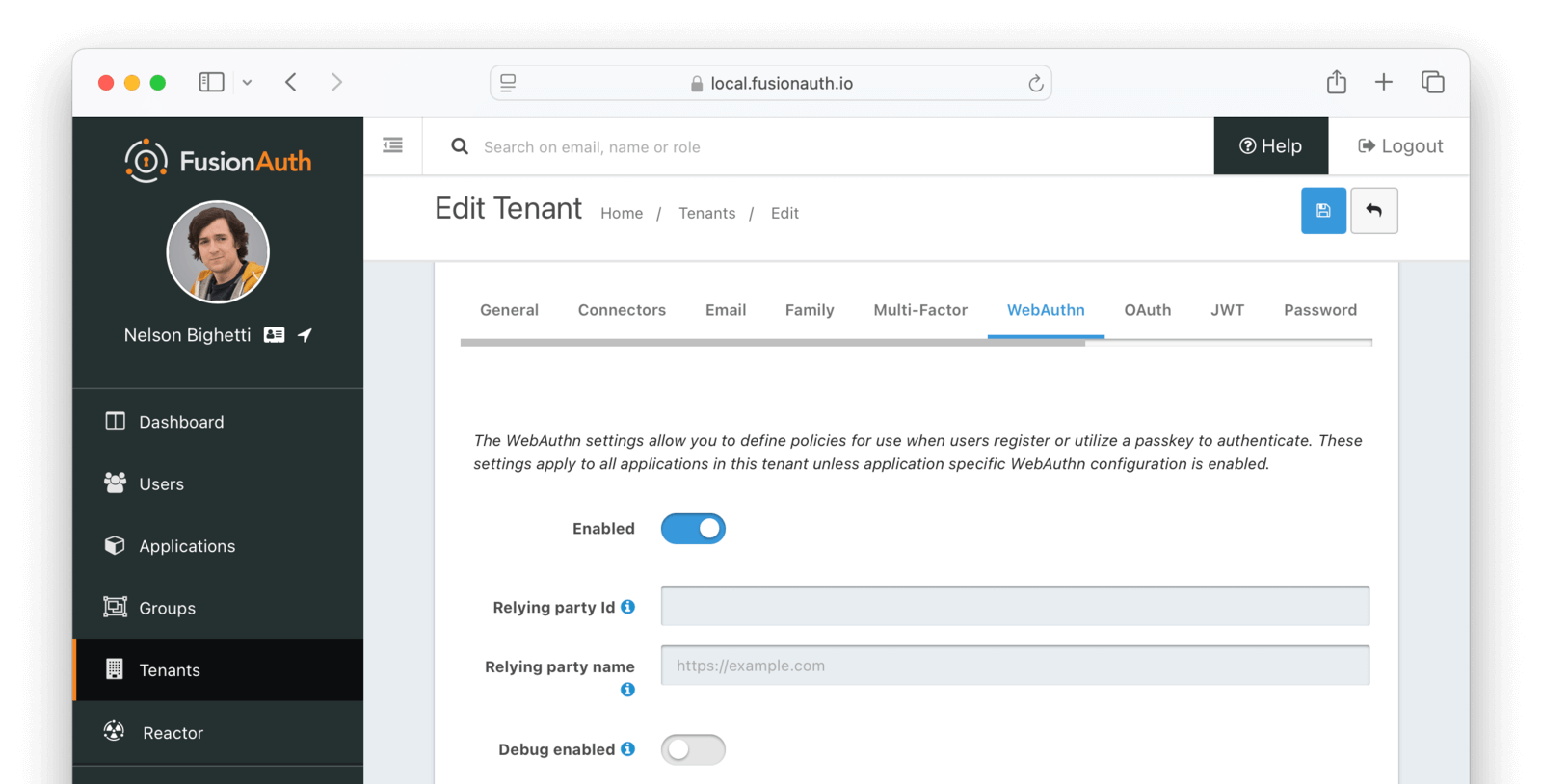
Form Fields
EnabledWhen enabled, WebAuthn is available for the tenant, and additional configuration options will be available.
Relying party IdThe Relying Party Id is used to scope WebAuthn passkeys to the site where they were registered. As part of WebAuthn’s security requirements, this value must be either:
- The browser request origin’s effective domain
- A registrable domain suffix of the effective domain
For example, if the login page is at auth.piedpiper.com, then the following are valid Relying Party Ids:
auth.piedpiper.com- matches the effective domainpiedpiper.com- a registrable suffix of the effective domain
But the following values are not valid:
m.auth.piedpiper.com- a subdomain of the effective domaincom- this is a suffix of the effective domain but not registrable
It is important that this is configured according to the URL that a user would see in their browser while on the FusionAuth login page. See the WebAuthn Admin Guide for more details on how to select the appropriate value.
Leaving this value empty will cause the WebAuthn JavaScript API to use the browser’s current request origin.
Relying party nameThe Relying Party name for WebAuthn ceremonies. This value may be displayed to the user by the browser or OS during WebAuthn registration and authentication ceremonies.
If this value is left blank, the Issuer value will be used.
Debug enabledEnable debug to create an event log to assist you in debugging integration errors.
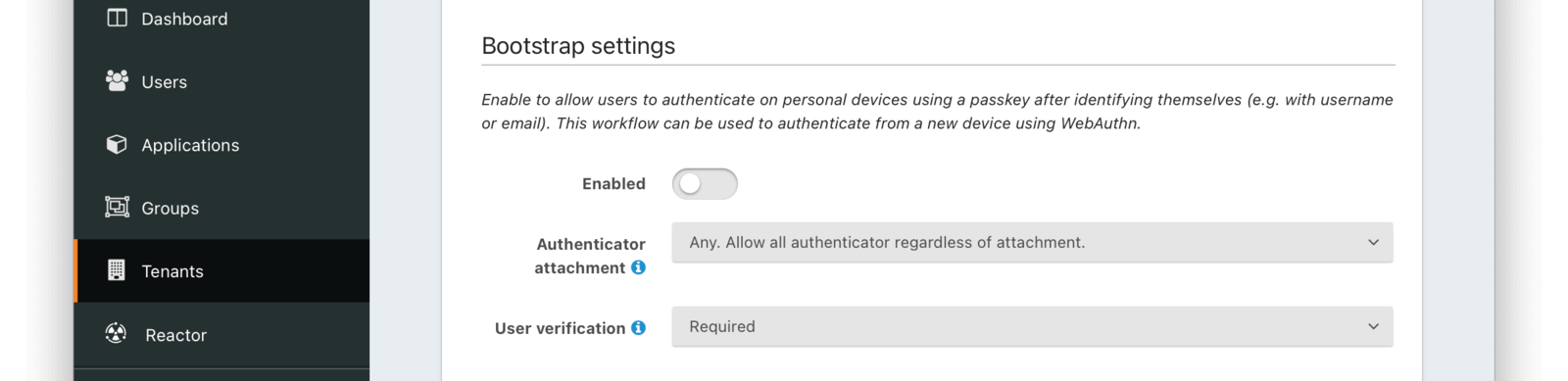
Bootstrap settings
The settings in this section affect the availability and behavior of the WebAuthn bootstrap workflow. The bootstrap workflow is used when the user must “bootstrap” the authentication process by identifying themselves prior to the WebAuthn ceremony and can be used to authenticate from a new device using WebAuthn.
EnabledWhen enabled, the WebAuthn bootstrap workflow can be used to authenticate users via WebAuthn from new or repeat devices.
The availability of the bootstrap workflow can be overridden at the application level on the WebAuthn Tab of the Application settings.
Authenticator attachmentThe authenticator attachment preference for the bootstrap workflow on this tenant. This value controls the attachment requirement for authenticators during the bootstrap workflow registration ceremony. Authenticators that do not meet the requirement are not considered during passkey registration. The possible values are:
Any- any authenticator attachment is allowedPlatform only- only authenticators integrated with the client device are allowedCross-platform only- only authenticators that are usable across multiple client devices are allowed
The recommended value for the bootstrap workflow is Any when the option is available.
Note: An Enterprise plan is required to utilize WebAuthn cross-platform authenticators.
User verificationThe user verification requirement for the bootstrap workflow on this tenant. This value controls whether user verification is required for registration and authentication ceremonies during the bootstrap workflow. Authenticators that do not meet the requirement are not considered during passkey registration or authentication. The possible values are:
Required- user verification is required to complete the WebAuthn ceremonyPreferred- the Relying Party prefers user verification is provided but will not fail the WebAuthn ceremony without itDiscouraged- the Relying Party does not want user verification for the WebAuthn ceremony
Because the bootstrap workflow is used to authenticate a user, it is highly recommended to set this value to Required.
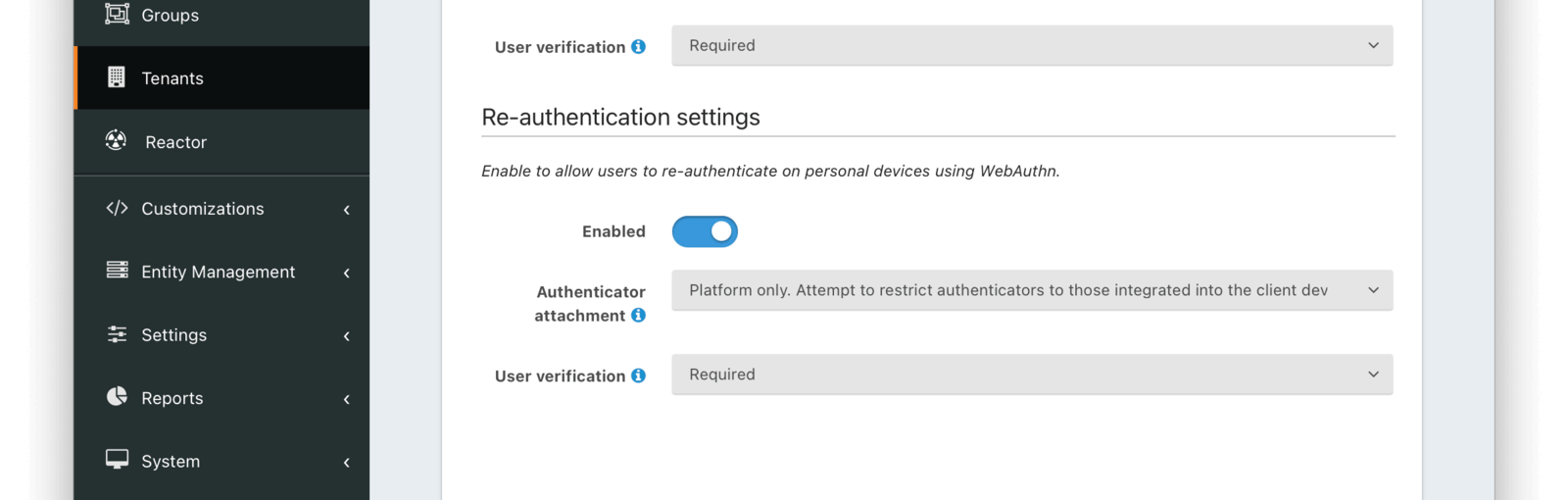
Re-authentication settings
The settings in this section affect the availability and behavior of the WebAuthn re-authentication workflow. The re-authentication workflow is meant to provide a streamlined user experience when logging in from a frequently used device.
EnabledWhen enabled, the WebAuthn re-authentication workflow can be used to streamline the login experience when authenticating from a previously used device.
The availability of the re-authentication workflow can be overridden at the application level on the WebAuthn Tab of the Application settings.
Authenticator attachmentThe authenticator attachment preference for the re-authentication workflow on this tenant. This value controls the attachment requirement for authenticators during the re-authentication workflow registration ceremony. Authenticators that do not meet the requirement are not considered during passkey registration. The possible values are:
Any- any authenticator attachment is allowedPlatform only- only authenticators integrated with the client device are allowedCross-platform only- only authenticators that are usable across multiple client devices are allowed
The recommended value for the re-authentication workflow is Platform only to ensure the user has access to that authenticator when logging from the device in the future.
Note: An Enterprise plan is required to utilize WebAuthn cross-platform authenticators.
User verificationThe user verification requirement for the re-authentication workflow on this tenant. This value controls whether user verification is required for registration and authentication ceremonies during the re-authentication workflow. Authenticators that do not meet the requirement are not considered during passkey registration or authentication. The possible values are:
Required- user verification is required to complete the WebAuthn ceremonyPreferred- the Relying Party prefers user verification is provided but will not fail the WebAuthn ceremony without itDiscouraged- the Relying Party does not want user verification for the WebAuthn ceremony
Because the re-authentication workflow is used to authenticate a user, it is highly recommended to set this value to Required.
OAuth
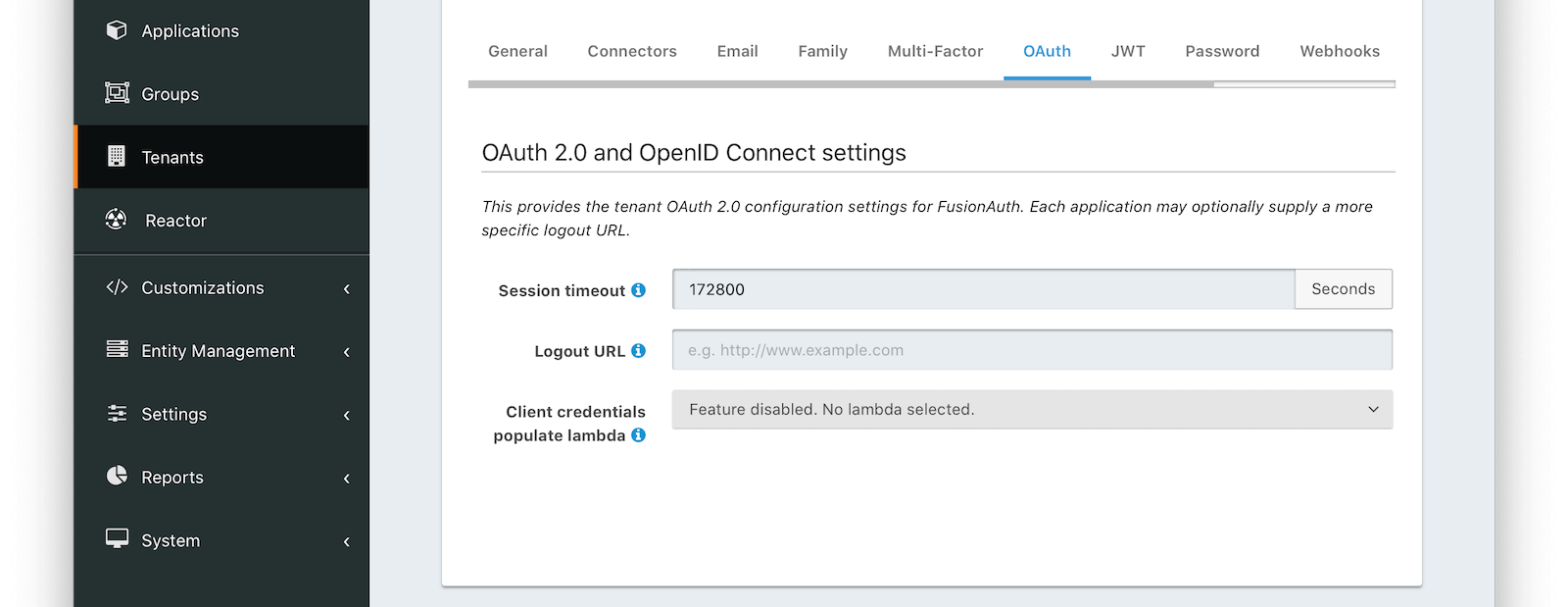
Form Fields
Session timeoutThe length of time an SSO session can be inactive before it is closed.
Logout URLThe URL the user is redirected to upon logout.
Client credentials populate lambdaAvailable since 1.28.0The lambda that will be called to populate the JWT during a client credentials grant.
Allow access token bootstrapAvailable since 1.56.0When enabled, an SSO session can be created after login by providing an access token as a bearer token in a request to the OAuth2 Authorize endpoint.
JWT
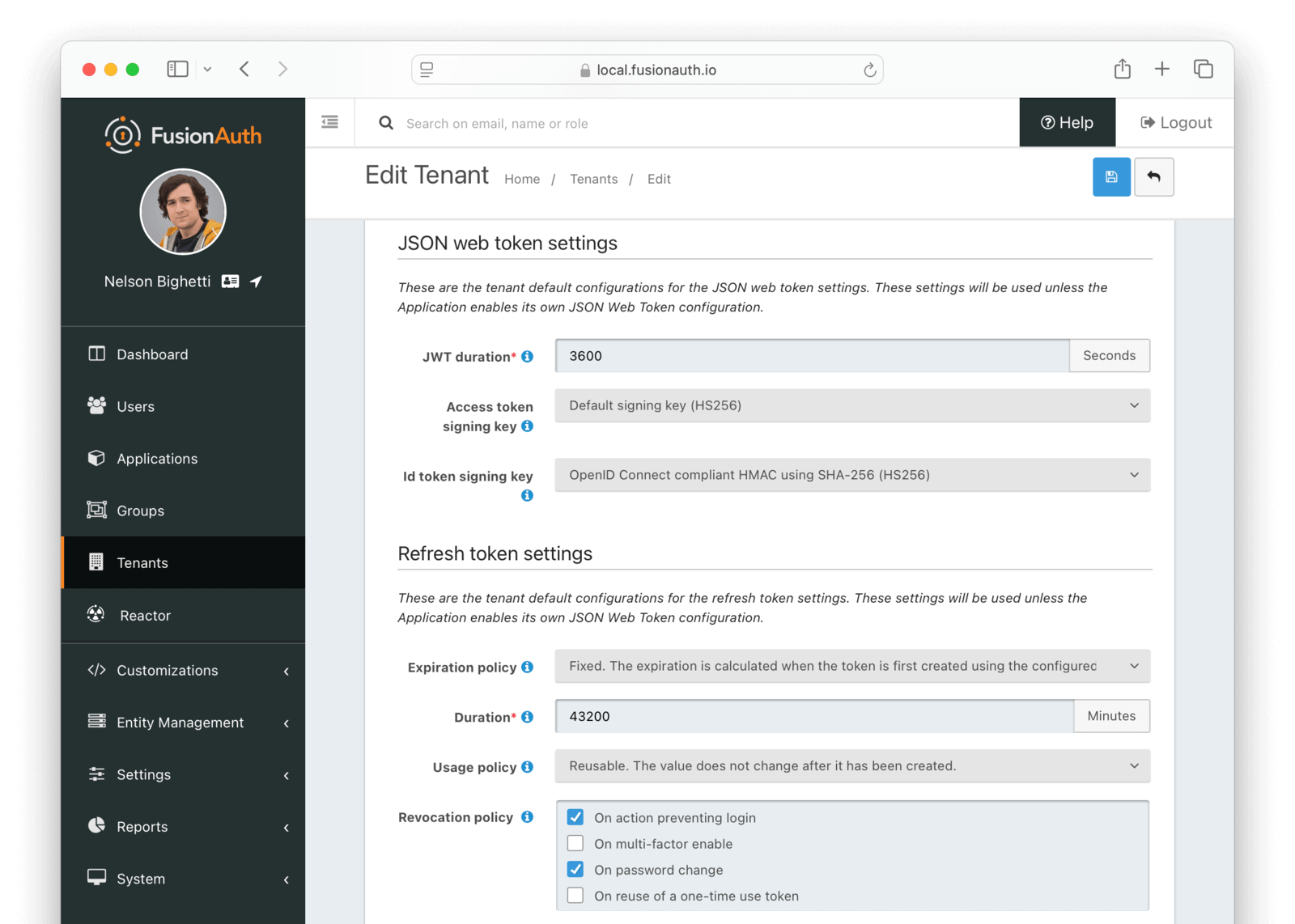
JSON Web Token settings
JWT durationrequiredThe length of time the issued token (access token and Id token) is valid. JWT tokens are typically short lived.
Access token signing keyThe key used to sign the access token JWT.
Id token signing keyThe key used to sign the Id token JWT.
Refresh Token settings
Refresh token durationrequiredDefaults to 43,200The length of time the refresh token is valid. Refresh tokens are typically long lived.
Refresh token expirationDefaults to FixedThe Refresh token expiration may be either a fixed window, sliding window, or sliding window with a maximum lifetime. By default, the expiration of a refresh token is a fixed length of time from when it was originally issued. With a sliding window expiration, the expiration is calculated from the last time the refresh token was used. However with a sliding window with a maximum lifetime, the expiration is calculated from the last time the refresh token was used until a maximum lifetime value is reached.
For instance, consider the following scenarios given the above configuration. If a refresh token is issued at 1:00pm and has a duration of 60 minutes, if the expiration is fixed, the token will expire at 2:00pm. If, instead, the expiration is a sliding window, then if the refresh token is used at 1:55pm, it would then expire at 2:55pm. If it were then used at 2:50pm, it would expire at 3:50 pm. Lastly if the expiration is a sliding window with a maximum lifetime of 24 hours, then the token could be refreshed every hour (in the same sliding manner as outlined above) up to 23 times. For instance, if a token was issued at 1:55pm on Monday and refreshed every hour, the 23th refresh it would be the last valid refresh request (12:55pm Tuesday would be the last valid refresh event).
Refresh token usageDefaults to ReusableThe Refresh token usage may be reusable or one time use. By default, a token is reusable and the token does not change after it was issued. With a one time use token, the token value will be changed each time the token is used to refresh a JWT. This means the client must store the new value after each use.
One-time use grace periodDefaults to 0When Refresh token usage is set to One-time use, you may optionally set the grace period to something greater than 0 seconds.
The grace period is the length of time specified in seconds that a one time use token can be reused.
This value must be greater than 0 and less than 86400 which is equal to 24 hours. Setting this value to 0 effectively disables the grace period which means a one-time token may not be reused. For security reasons, you should keep this value as small as possible, and only increase past 0 to improve reliability for an asynchronous or clustered integration that may require a brief grace period.
Note that one-time use tokens refreshed within a grace period are not considered for revocation when the Tenant Refresh Token Revocation Policy is configured to revoke a one-time use refresh token on reuse. When a token is reused within the grace period the current token will be returned on the API response and the token will not be rotated.
Refresh token revocationThe events that will cause refresh tokens to be revoked.
Password
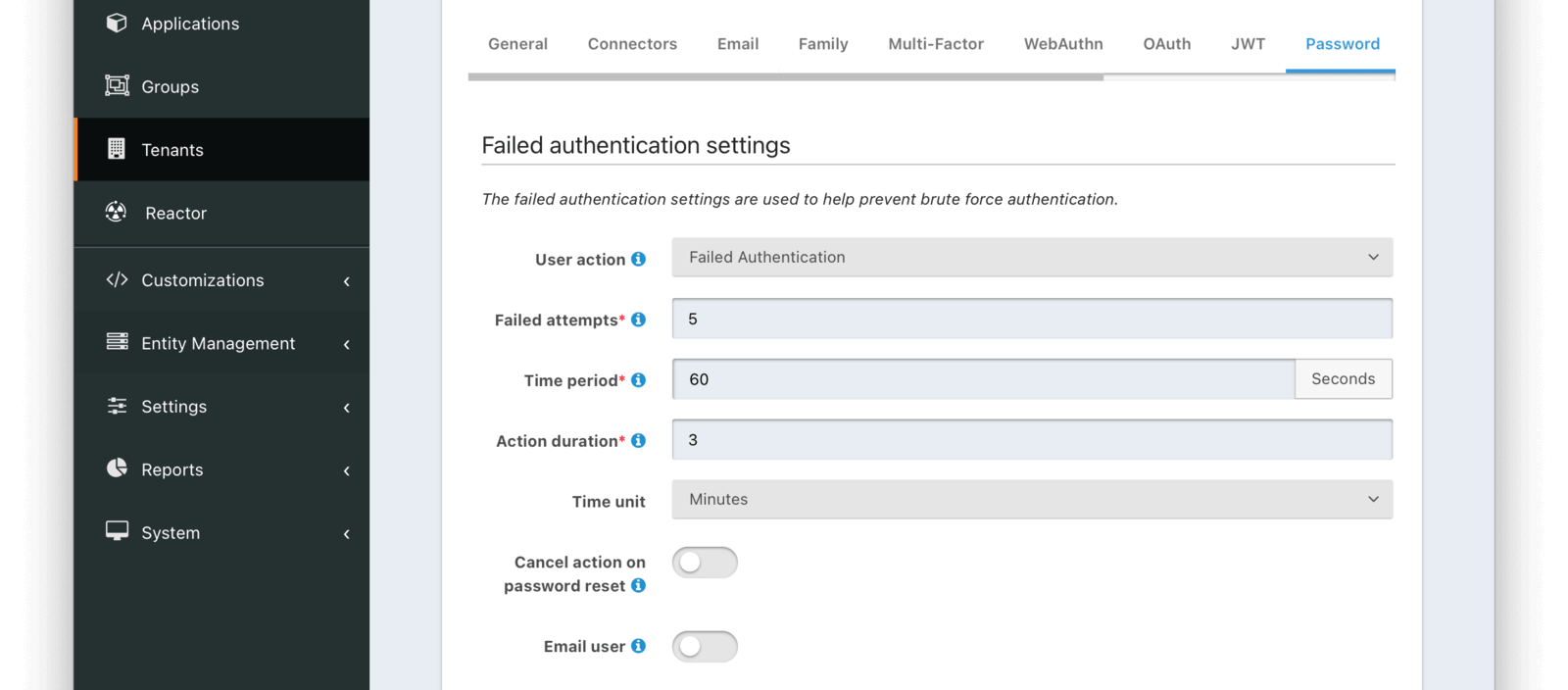
Failed authentication settings
User actionThe user action must be ‘time-based’ and must have ‘prevent login’ enabled. This actions is applied after multiple failed login attempts.
Failed attemptsrequiredThe number of failed attempts allowed during the specified time period before the selected action is applied.
Time periodrequiredThe window of time in seconds for which the failed authentication attempts are counted. If no further failed attempts occur the failure count will be reset after this time period starting at the time of the last failed login.
Action durationrequiredThe length of time the selected action is applied to the user before the action expires at which point the user will be allowed to attempt log in again.
Time unitThe time unit the Action duration is measured in.
Cancel action on password resetAvailable since 1.42.0Indicates whether you want the user to be able to self-service unlock their account prior to the action duration by completing a password reset workflow.
Email userAvailable since 1.42.0Indicates you would like to email the user when the user’s account is locked due to this action being taken. This requires the User Action specified by the User action to also be configured for email. If the User Action is not configured to be able to email the user, this configuration will be ignored.
The email template configuration will be in the User Action.
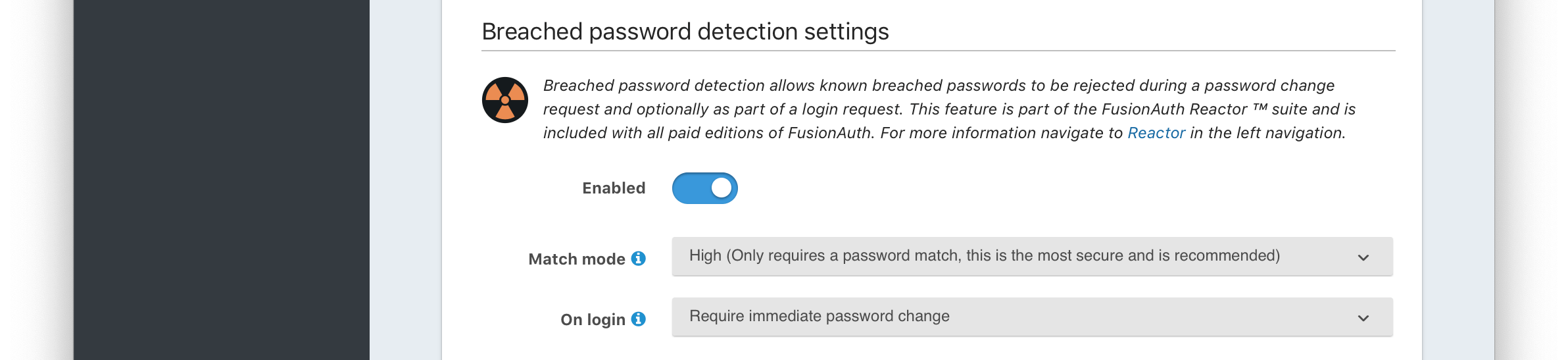
Breach detection settings
EnabledWhen enabled, users’ login Id and password will be checked against public breached password databases on user creation, password change, and (optionally) on login. Purchase of a FusionAuth plan is required to enable this feature.
Match modeThe login Id and password match constraints to qualify as a breach match.
On loginThe action to perform during login for breach detection. Performing breach detection during login may increase the time it takes to complete authentication.
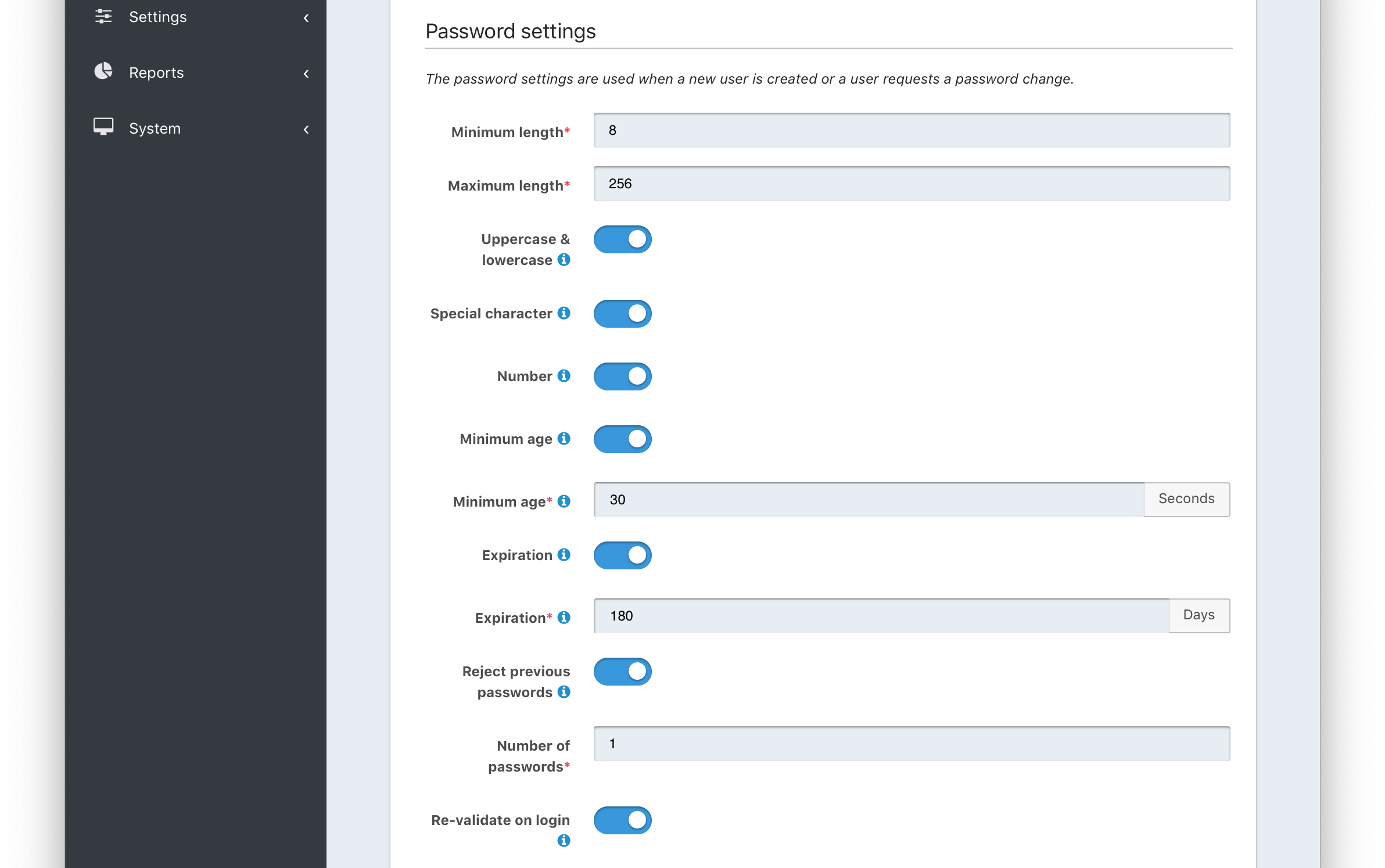
Password settings
Minimum lengthrequiredThe minimum length a password may be to qualify as a valid password.
Maximum lengthrequiredThe maximum length a password may be to qualify as a valid password.
Uppercase & lowercaseWhen enabled, force the user to use at least one uppercase and one lowercase character.
Special characterWhen enabled, force the user to use at least one non-alphanumeric character.
NumberWhen enabled, force the user to use at least one number.
Minimum age (toggle)When enabled, users must wait a configurable duration before changing their password after the previous change.
Minimum age (value)requiredThe minimum age (in seconds) users must wait before changing their password after the previous change.
Required when the Minimum age toggle is enabled.
Expiration (toggle)When enabled, user passwords will expire after a configurable duration, at which point the user will be forced to change their password on login.
Expiration (value)requiredThe duration (in days) the password expire after since the previous change.
Required when the Expiration toggle is enabled.
Reject previous passwordsWhen enabled, prevent users from using a configurable number of their previous passwords.
Number of passwordsrequiredThe number of previous password to retain, to prevent users from password reuse.
Required when the Reject previous passwords toggle is enabled.
Re-validate on loginWhen enabled the user’s password will be validated during login. If the password does not meet the currently configured validation rules the user will be required to change their password.
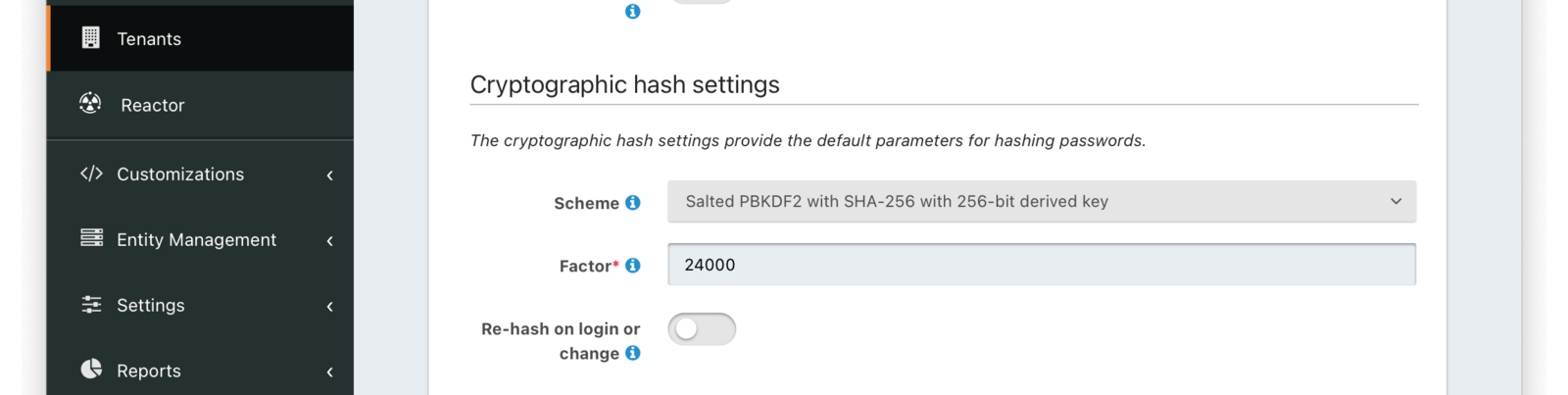
Cryptographic hash settings
SchemeThe password hashing scheme used when creating new users and when changing a password. View hashing algorithms that ship with FusionAuth or learn how to create your own hashing algorithm.
FactorrequiredA non-zero number that provides an iteration count to the hashing scheme. A higher number will make the password hash more difficult to reverse engineer but will take more CPU time during login. Be careful as a high factor may cause logins to become very slow.
Re-hash on loginWhen enabled the user’s password hash will be modified if it does not match the configured values during next login.
Webhooks
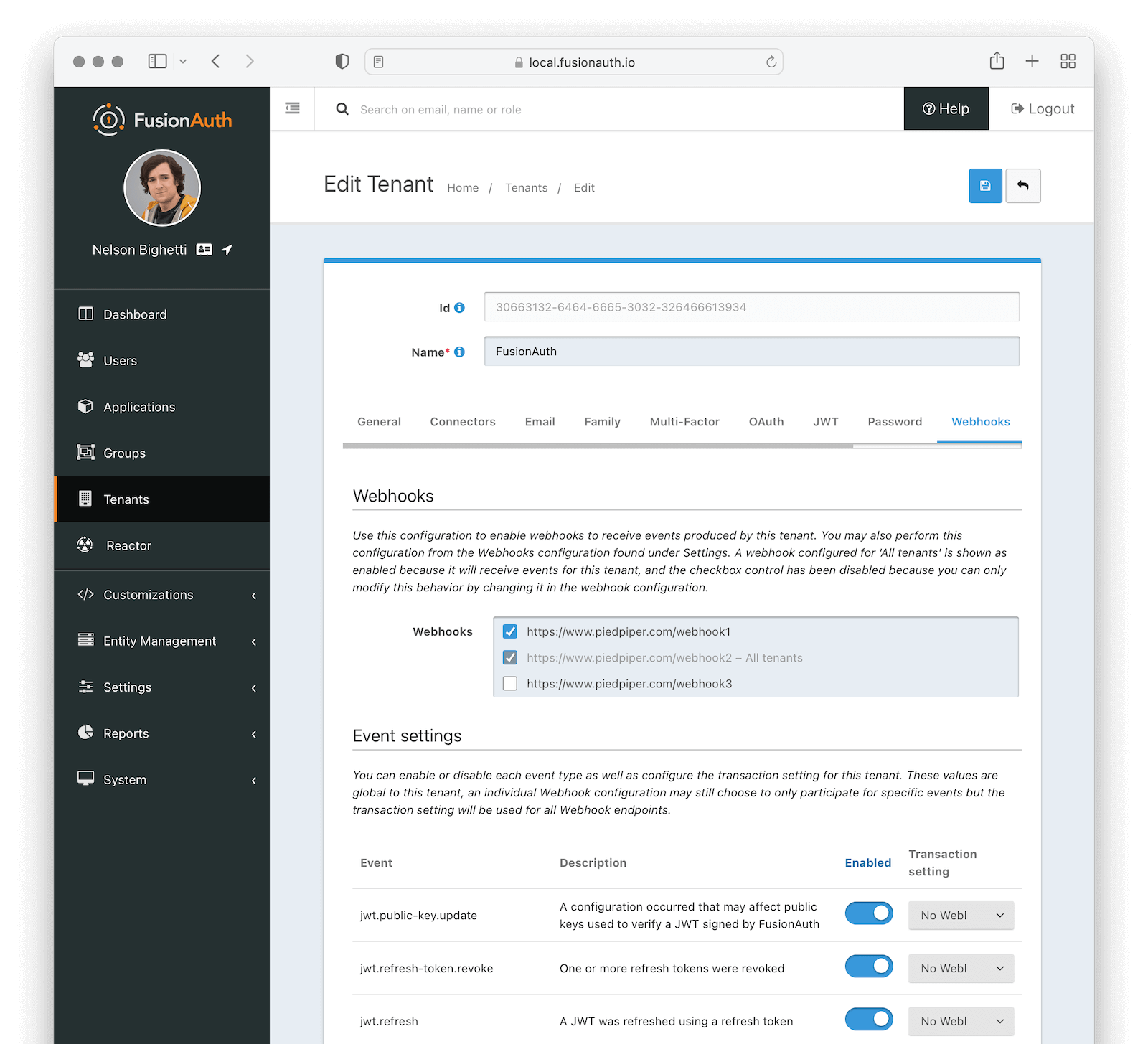
Webhooks
Enable the webhooks you wish to receive events from this tenant. All webhooks will be shown, but if the webhook is a global webhook then you will not be able to unselect it here. That must be done in the Tenants Tab of the Webhook Settings.
Event Settings
EventThe event type, this value will be present in the JSON request to identify the message.
DescriptionThe description of the event.
EnabledWhen enabled this event can be sent by one or more webhook. You will also need to enable the event for a specific webhook to receive the event.
This toggle allows you to optionally disable an event for all webhooks all at once.
Transaction settingThe transaction setting for this event. This setting will apply to all webhooks consuming this event type.
No Webhooks are required to succeed: The event will succeed regardless of the webhook response status code. Use this setting when it is not important for a webhook to succeed or provide confirmation that the event has been received and processed successfully.
Any single Webhook must succeed:
The event will succeed as long as one or more of the webhooks respond with a status code between 200 and 299 (inclusive).
A simple majority of Webhooks must succeed:
The event will succeed if at least half of the webhooks respond with a status code between 200 and 299 (inclusive). This means 50% or more of the webhooks must respond successfully.
A two-thirds majority of Webhooks must succeed:
The event will succeed if a super majority of the webhooks respond with a status code between 200 and 299 (inclusive). A super majority is two-thirds (66.7%) or more of the configured webhooks.
All of the Webhooks must succeed:
The event will succeed if every configured webhook responds with a status code between 200 and 299 (inclusive). Use this setting when it is critical for every configured webhook to receive and process the event before considering it complete.
SCIM

This feature is only available in the Enterprise plan. Please visit our pricing page to learn more.
Read more about setting up and using SCIM in the full SCIM documentation.
The SCIM server configuration to enable incoming SCIM client provisioning requests.
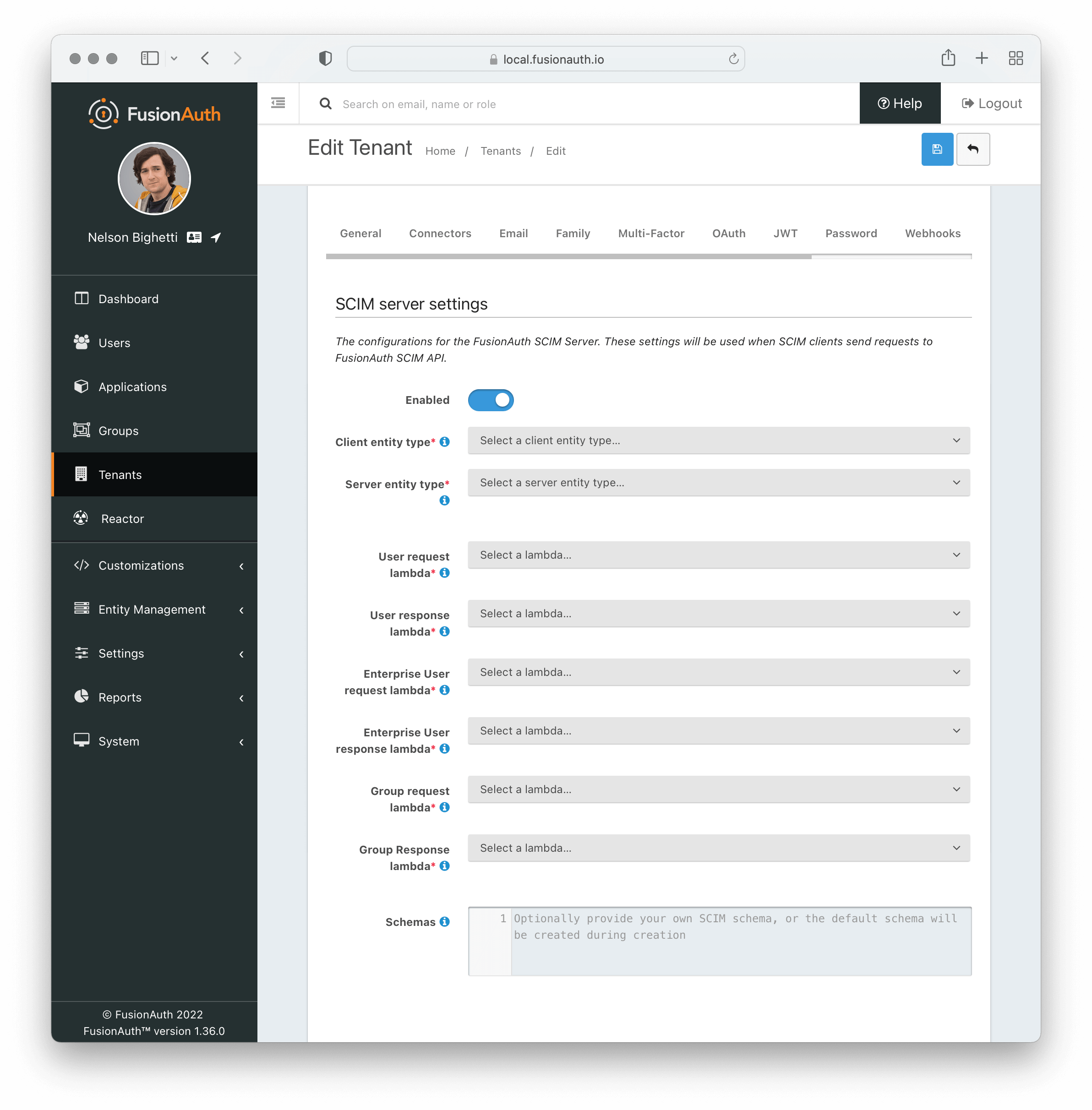
SCIM server settings
EnabledWhen enabled, FusionAuth will act as a SCIM server and the SCIM API endpoints will be functional.
Client entity typerequiredThe Entity Type defined for the SCIM client. If there are no Entity Types available in the list then navigate to Entity > Types and create a new one using the template button for SCIM client.
Server entity typerequiredThe Entity Type defined for the SCIM server. If there are no Entity Types available in the list then navigate to Entity > Types and create a new one using the template button for SCIM server.
User request lambdarequiredThe lambda that will be invoked on every incoming request to the SCIM User API endpoints. This maps the incoming SCIM User JSON to the User object.
User response lambdarequiredThe lambda that will be invoked on every outgoing response from the SCIM User API endpoints. This maps the outgoing User object to the JSON for a SCIM User.
Enterprise User request lambdarequiredThe lambda that will be invoked on every incoming request to the SCIM Enterprise User API endpoints. This maps the incoming SCIM Enterprise User JSON to the User object.
Enterprise User response lambdarequiredThe lambda that will be invoked on every outgoing response from the SCIM Enterprise User API endpoints. This maps the outgoing User object to the JSON for a SCIM Enterprise User.
Group request lambdarequiredThe lambda that will be invoked on every incoming request to the SCIM Group API endpoints. This maps the incoming SCIM Group JSON to the Group object.
Group response lambdarequiredThe lambda that will be invoked on every outgoing response from the SCIM Group API endpoints. This maps the outgoing Group object to the JSON for a SCIM Group.
SchemasThe JSON response sent from the Schemas endpoint. This can be customized however you like, but by default the response body will contain the JSON for the core SCIM schemas for SCIM Group, SCIM User, and SCIM EnterpriseUser.
Security
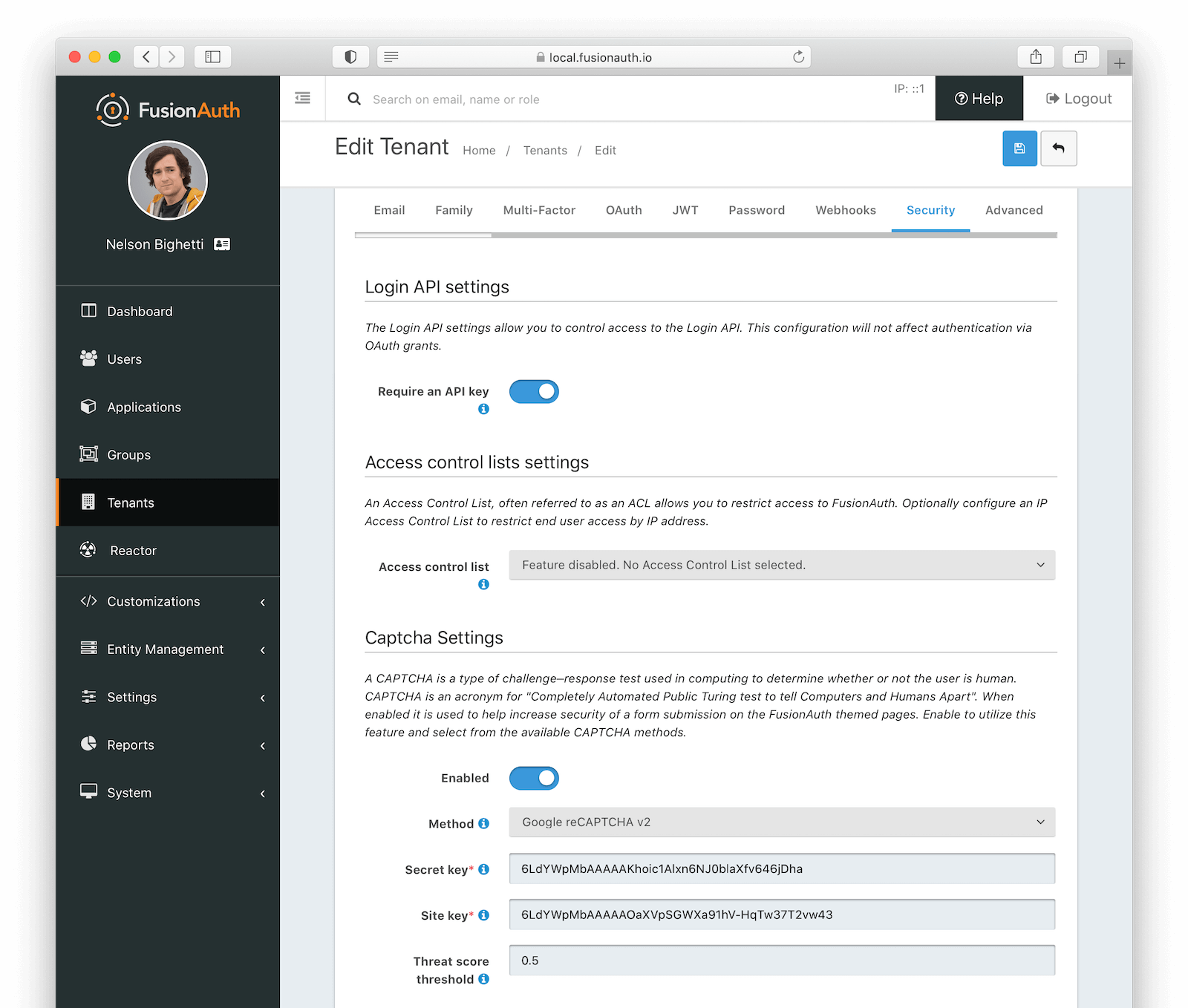
Login API settings
Require an API keyThis indicates how to authenticate the Login API when an applicationId is not provided.
When an applicationId is provided, the application configuration will take precedence. In almost all cases you will want to leave this enabled to require the use of an API key.
Login validation lambdaAvailable since 1.53.0The lambda assigned to perform extended validation during login requests.
Access control lists settings

This feature is only available in the Enterprise plan. Please visit our pricing page to learn more.
Access control listThe IP access control list that will be used to restrict or allow access to hosted login pages in FusionAuth. For example, it may be configured to only allow specific IP addresses to access authentication pages (login, forgot password, etc) for all applications on that tenant.
When Access control list is configured on an application within the tenant, the application value will override the tenant value for that application.
CAPTCHA settings

This feature is only available in the Enterprise plan. Please visit our pricing page to learn more.
CAPTCHA is supported on multiple theme templates, when enabled. You can further control display on a template by template basis with the specific theme template variables.
See invisible reCAPTCHA for information on enabling an invisible reCAPTCHA badge on the page.
EnabledWhen enabled, CAPTCHA is used to help increase security of a form submission on the FusionAuth themed pages.
MethodrequiredThe type of CAPTCHA to use. FusionAuth supports Google reCAPTCHA v2, Google reCAPTCHA v3, hCaptcha, and hCaptcha Enterprise.
Required when enabled is set to true.
Secret keyrequiredThe secret key for this CAPTCHA service.
Required when enabled is set to true.
Site keyrequiredThe site key for this CAPTCHA service.
Required when enabled is set to true.
Threat score thresholdThe threat score threshold for this CAPTCHA service if required. If it is not used by this CAPTCHA service then the value will be ignored.
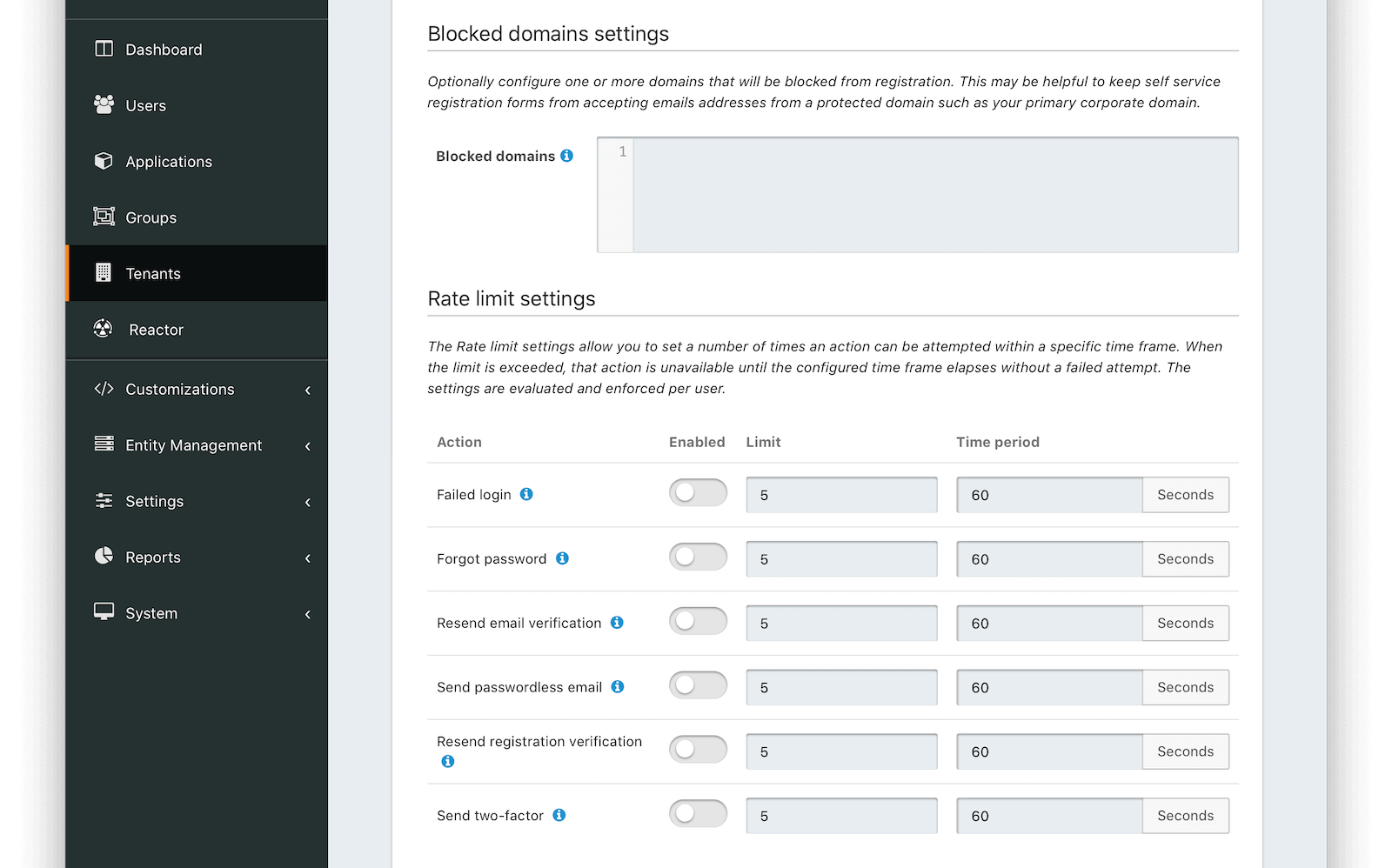
Blocked domain settings

This feature is only available in the Enterprise plan. Please visit our pricing page to learn more.
Blocked domainsOne or more newline separated email domains for which self service registration will be prohibited. For example, enter your company email domain (piedpiper.com) to prevent employees from using the self-service registration form, or to prevent end users from attempting to create an account using a company email address.
This configuration is applied to all registration API requests and self-service registration pages for all applications in this tenant.
Rate limit settings

This feature is only available in the Enterprise plan. Please visit our pricing page to learn more.
The Rate limit settings allow you to set a number of times an action can be attempted within a specific time frame. When the limit is exceeded, that action is unavailable until the configured time frame elapses without a failed attempt. The settings are evaluated and enforced per user.
ActionThe action to be rate limited.
Note: For the Failed login action, rate limiting can be used in combination with Failed authentication settings. When enabled, and rate limiting conditions have been exceeded, login requests will be denied and bypass the login flow until conditions are no longer exceeded. Failed attempts will only be incremented when requests are not being rate limited.
EnabledWhen enabled, the corresponding action will be rate limited when the limit value has been exceeded within the specified time period .
LimitThe number of allowed attempts within the time period before an action will be rate limited. When an action is rate limited, it will not succeed.
Time periodThe window of time that the limit is evaluated against when determining if an action should be rate limited.
Advanced
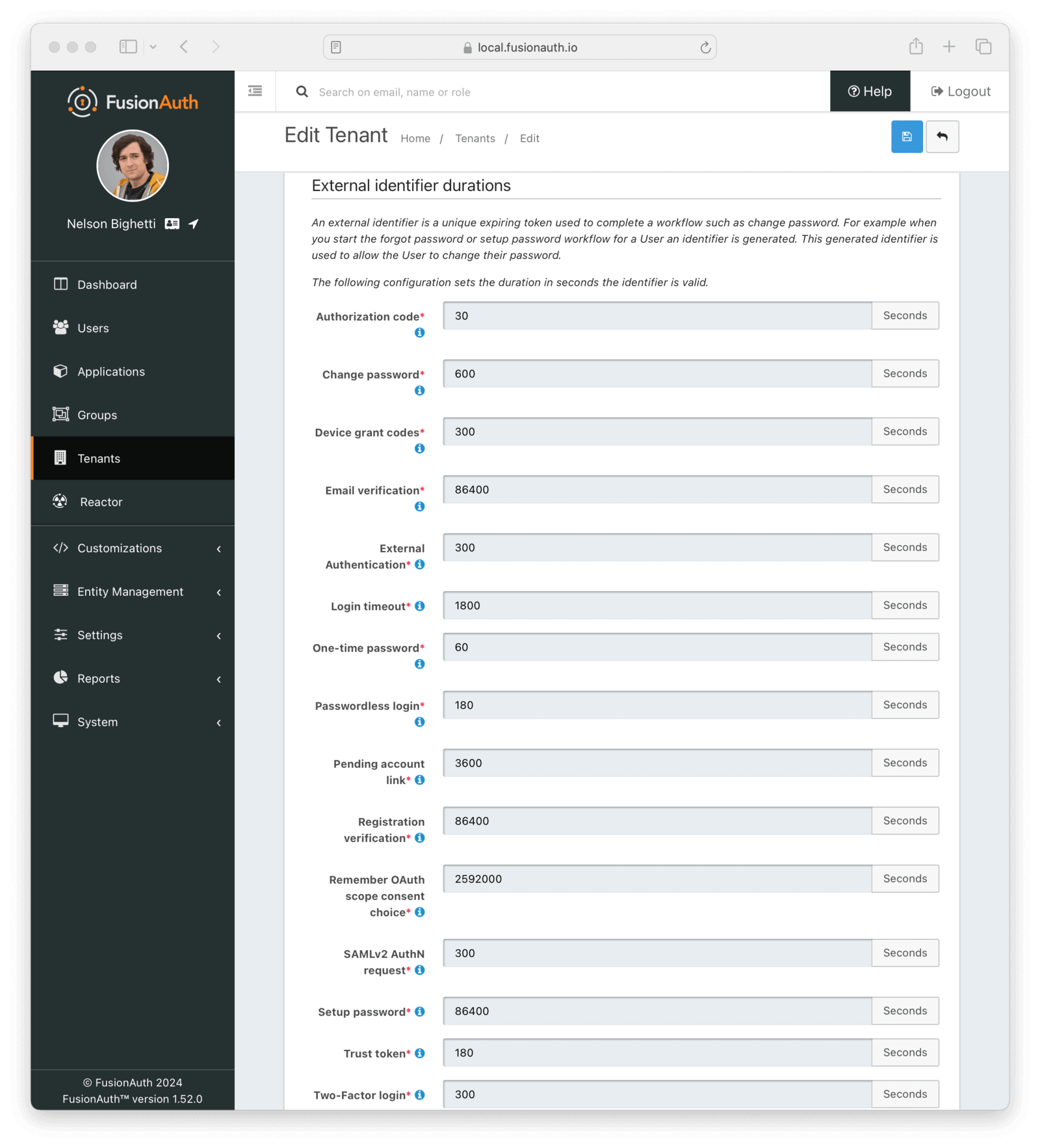
External identifier durations Form Fields
Authorization CoderequiredThe number of seconds before the OAuth2 Authorization Code is no longer valid to be used to complete a Token request.
Change PasswordrequiredThe number of seconds before the Change Password identifier is no longer valid to complete the Change Password request.
Device Grant CodesrequiredThe number of seconds before the device_code and user_code are no longer valid to be used to complete the Device Code grant.
Email VerificationrequiredThe number of seconds before the Email Verification identifier is no longer valid to complete the Email Verification request.
External AuthenticationrequiredThe number of seconds before the External Authentication identifier is no longer valid to complete the Authentication request.
Login timeoutrequiredThe number of seconds before the Login Timeout identifier is no longer valid to complete post-authentication steps in the OAuth workflow.
One Time PasswordrequiredThe number of seconds before the One Time Password identifier is no longer valid to complete a Login request.
Passwordless LoginrequiredThe number of seconds before the Passwordless Login identifier is no longer valid to complete a Login request.
Pending account linkrequiredThe number of seconds before the Pending account link is no longer valid to complete an account link request.
Registration VerificationrequiredThe number of seconds before the Registration Verification identifier is no longer valid to complete the Registration Verification request.
Remember scope consent choicerequiredThe number of seconds before a remembered consent choice, used to bypass the OAuth scope consent prompt, expires.
SAMLv2 AuthN requestrequiredThe number of seconds before the SAMLv2 AuthN request is no longer valid to complete the SAMLv2 login request.
Setup PasswordrequiredThe number of seconds before the Setup Password identifier is no longer valid to complete the Change Password request.
Two Factor LoginrequiredThe number of seconds before the Two Factor identifier is no longer valid to complete a Two Factor login request.
Two Factor one-time coderequiredThe number of seconds before the Two Factor one-time code used to enable or disable a two-factor method is no longer valid.
Two Factor TrustrequiredThe number of seconds before the Two Factor Trust is no longer valid and the user will be prompted for Two Factor during login.
WebAuthn authenticationrequiredThe number of seconds before the WebAuthn authentication challenge is no longer valid and the user will need to restart the authentication workflow.
WebAuthn registrationrequiredThe number of seconds before the WebAuthn registration challenge is no longer valid and the user will need to restart the credential registration workflow.
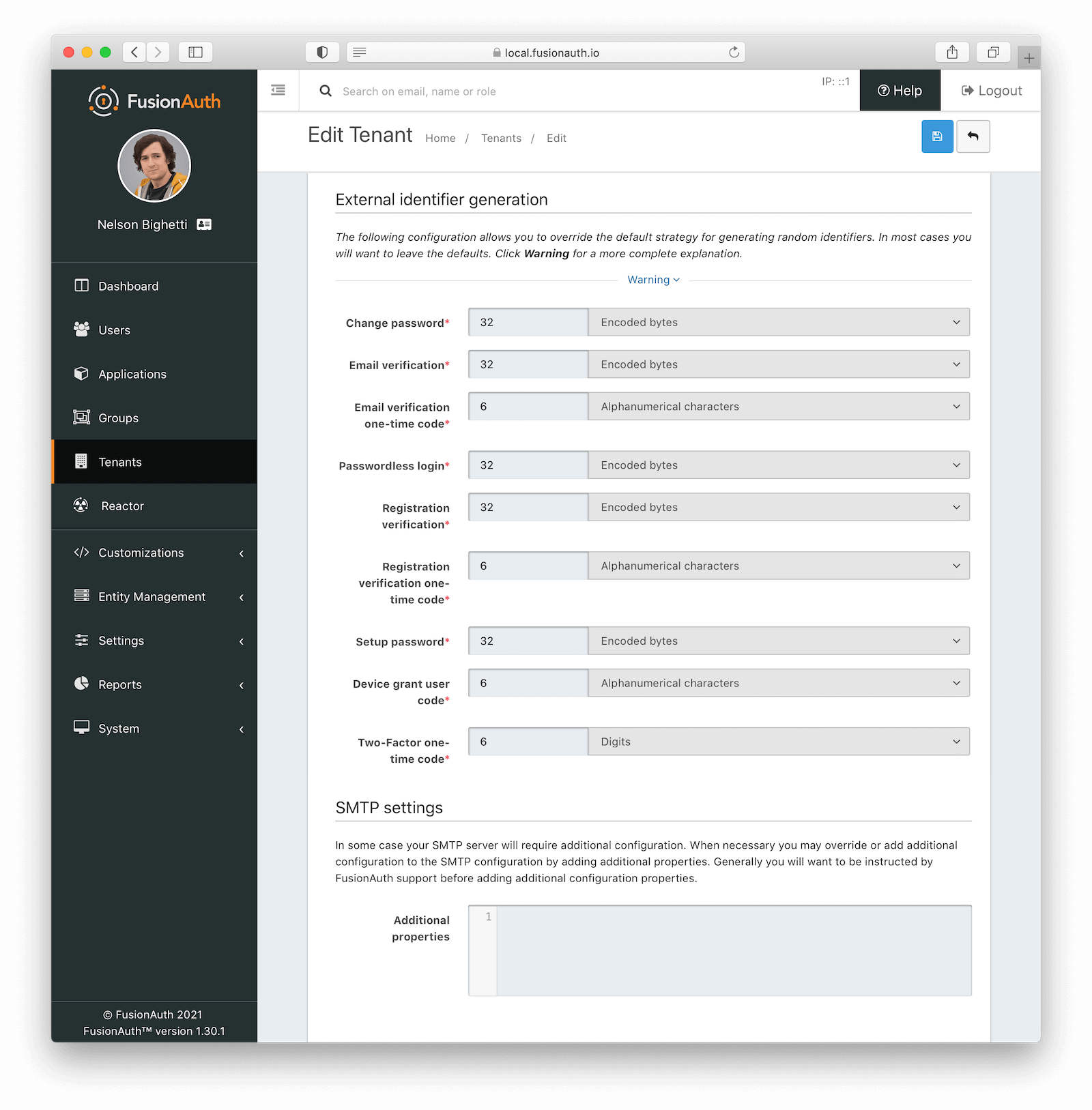
External identifier generation Form Fields
Change PasswordrequiredThe length and type of characters of the generated code used in the Change Password flow.
Email VerificationrequiredThe length and type of characters of the generated code used in the Email Verification flow.
Email Verification one-time coderequiredThe length and type of characters of the generated code used for Email Verification one-time codes.
The one-time code for email verification is only used with email verification gating and when using a form field configuration instead of the clickable link.
Passwordless LoginrequiredThe length and type of characters of the generated code used in the Passwordless Login flow.
Registration VerificationrequiredThe length and type of characters of the generated code used in the Registration Verification flow.
Registration Verification one-time coderequiredThe length and type of characters of the generated code used for Registration Verification one-time codes.
The one-time code for registration verification is only used with registration verification gating and when using a form field configuration instead of the clickable link.
Setup PasswordrequiredThe length and type of characters of the generated code used in the Setup Password flow.
Device grant user coderequiredThe length and type of characters of the generated user code used in the Device Authorization Grant flow.
Two-Factor one-time coderequiredThe length and type of characters of the generated code used for Two-Factor one-time codes.
SMTP Settings Form Fields
Additional propertiesCustom SMTP configuration properties. This field can contain any Java mail property. Any value here will override the default values FusionAuth sets.
The following property has a default value:
mail.smtp.ssl.protocolshas a default value ofTLSv1 TLSv1.1 TLSv1.2.
Since version 1.44.0, the following two properties have default values:
mail.smtp.timeouthas a default value of2000.mail.smtp.connectiontimeouthas a default value of2000.
Here’s example syntax for overriding these properties, in this case setting both timeout defaults to 5 seconds.
mail.smtp.timeout=5000
mail.smtp.connectiontimeout=5000
