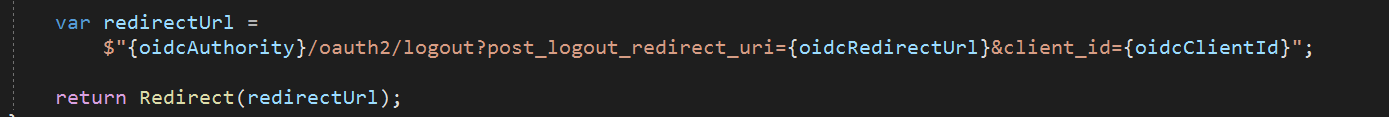
We recently upgraded our AKS instance of FusionAuth (FA) from Version 1.26 to 1.36.4 to use ElasticSearch user search.
This introduced errors with "response_type=id_token token" OIDC logins.
We did not update the receiving service provider or the FA application.
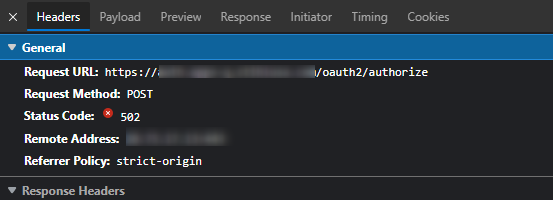
But now when we run the login to the service provider we get a 502 error when POST to https://zzz.com/oauth2/authorize after logging into FA:
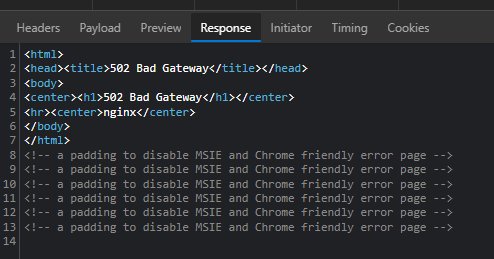
I have been playing around with the
- Access Token signing key
- Id Token signing key
sections under JWT section of the FA application.
But I still get an error if I leave either setting in RS256 or RS256 - 4096 length
If I update the application to HS256 - I do not get a 502 error on login to the service provider, but now the token will not decode and the service provider will not load
If I change the response_type from "id_token token" to just "id_token" I do not get a 502 error on login to the service provider, but now the token will not decode and the service provider will not load
Did something change in how FA handles response_type "id_token token" and RS256 signing keys from V 1.26 to 1.36.4?
As I said the only difference now is that we upgraded FA.
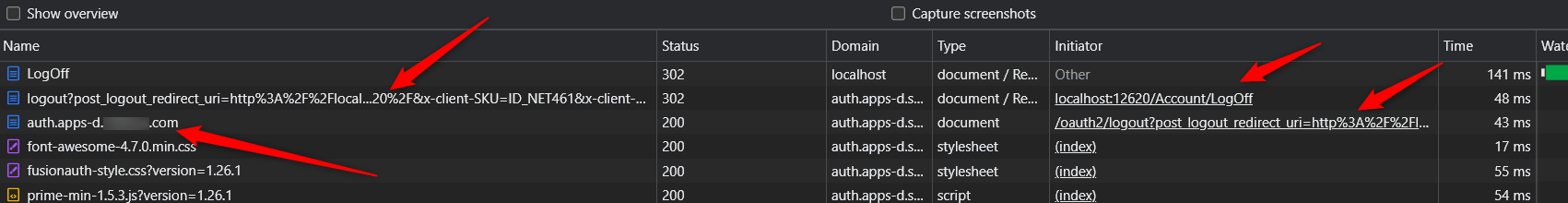
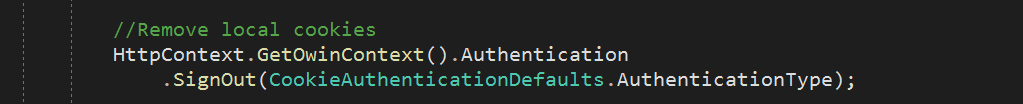
Also, like in the Docker instructions we pipe standard out to AKS logging, so I can do kubectl logs to see the logs, but FA does not output anything meaningful:
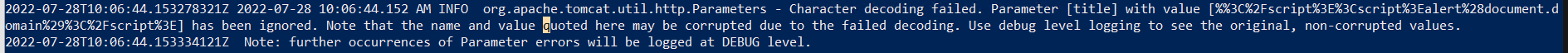
Is there anyway to debug what is going on with the new version?
By just seeing a 502 error page after logging in and no meaningful logs in either FA AKS logs or browser developer tools means I am just trying many different things to figure out why we cannot log into this service provider anymore.
Thanks