Federated Authentication Scenario Possible?
-
I'm reviewing FusionAuth (paid edition) and the scenario I want to be able to accomplish is the following:
- Login using an Identity Provider (Federated Login) - using idp_hint works great to force this.
- After login reject some users from the provider if they aren't in certain groups (this works by using a lambda function and throwing an exception during it)
- After verifying the user is legit, require them to consent to one or more consents in the system, also possibly asking them for additional information before letting them in.
- After login, verify that the user has MFA setup in FusionAuth, if not force them to do this
So, the MFA piece appears to not be available yet without custom UI work - waiting on issue #960 to hopefully allow this to happen.
The consent piece, I thought I could use the advanced registration forms, but those require a (un/email, password) field set to be present. In the case of federated logins, I don't want that to happen since I don't want to own the user's password at all.
Is there a way to gather "additional data" for the user profile without requiring them to have a un/pw in the system like this with the hosted UI?
If not, is that something on the roadmap?
-
Hey @alan-woodm thanks for the question!
To your first two points, I'm glad you were able to find a solution that worked for you!
Regarding point three, here are some thoughts:
- I don't think this is currently possible in our hosted UI advanced registration flow. You could look into wiring it up yourself.
- To do so, you would have to address two challenges. The first is that our registrations forms will require a username/password (advanced or regular). One option would be to fill in "random" values for these required fields using on-page Javascript. You could also hide these fields on the page so that the user is unaware of their existence. You also have the option to log a feature request to add this "add random username and password and hide" functionality to the FusionAuth roadmap.
- The second challenge, what I could almost call "consent gating", could be addressed on an application level. Upon federation, the user can have custom claims added to their JWT. For instance, they could have data such as
{ consent_one: true, consent_two: true, consent_three: false }Your application could check the JWT for these claims, and then redirect the user to a page to complete any needed consents.
For point number four, you are correct, a forced MFA is not currently available within the admin UI but there are a few options explored below
https://fusionauth.io/community/forum/topic/1063/can-i-enforce-mfa-for-my-users
These options would all be very similar to the above "consent gating workflow" (except now with MFA). Essentially, you would check the JWT for a claim indicating that MFA was enabled for that user, and only once that claim was enabled would you allow the user access to your application.
I'll post back here if I hear anything else, I hope this helps!
Thanks,
Josh -
@alan-wood said in Federated Authentication Scenario Possible?:
After verifying the user is legit, require them to consent to one or more consents in the system, also possibly asking them for additional information before letting them in.
For the advanced registration piece, it would make more sense to me if that wasn't tied to a username/password at all. If we already have the un/pw in a federation situation, then forcing us to ask for it again to fill out the registration record seems incorrect.
I understand that for a B2C where someone is creating a un/pw on the site it makes sense. However, there are many instances where we don't want to have a user able to login via any means other than federation (AD login, social media login, etc). And even where it "may" make sense (multiple social media logins linked to the same record) - there might be a "username" but certainly no password would be required in those cases.
The custom claims makes sense, and I'm happy to do something like that.
If I wanted to inject my own screens into the middle of your hosted UX flow, how would we do that? [Basically add my own "advanced registration" flow into your UX flow]?
Does that require completely replacing the UX flow you have with my own hosted one?
-
In reviewing with the team, looks like there is another path forward regarding original bullet #3
- Add an Idp (you could use
googlefor instance) - Add a consent from
settings > consents - Add a form field referencing this consent
- Make an advanced registration form
- Add previously created form field/consent to this form
- Create a new theme (or extend your existing non-default/shipped theme)
- Modify the theme to remove the display of the username and password in FreeMarker
- Navigate to
customizations > themes > all affected templates(in my case, this was theOAuth registertemplate)
Here is the simple Freemarker that I used to modify (disclaiming now that you may want to rework this code a bit -- example only)
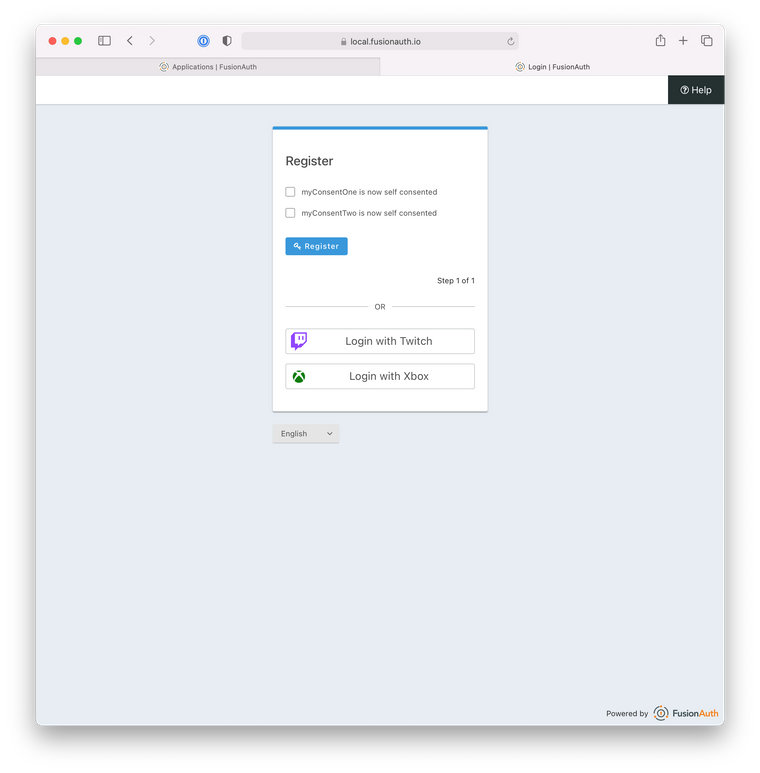
[#-- Begin Self Service Custom Registration Form Steps --] [#if fields?has_content] <fieldset> [#list fields as field] [#if field.key == "user.username"] [#elseif field.key == "user.password"] [#else] [@helpers.customField field field.key field?is_first?then(true, false) field.key /] [#if field.confirm] [@helpers.customField field "confirm.${field.key}" false "[confirm]${field.key}" /] [/#if] [/#if] [/#list] </fieldset> <div class="form-row"> [#if step == totalSteps] [@helpers.button icon="key" text=theme.message('register')/] [#else] [@helpers.button icon="arrow-right" text="Next"/] [/#if] </div> [#-- End Custom Self Service Registration Form Steps --]- Now when I see my register page, I get view like this. The Idp that you select will use the hidden username/email and password fields.
You are going to want to also customize the label for the consent. More information can be found below.
https://fusionauth.io/docs/v1/tech/guides/advanced-registration-forms/#consents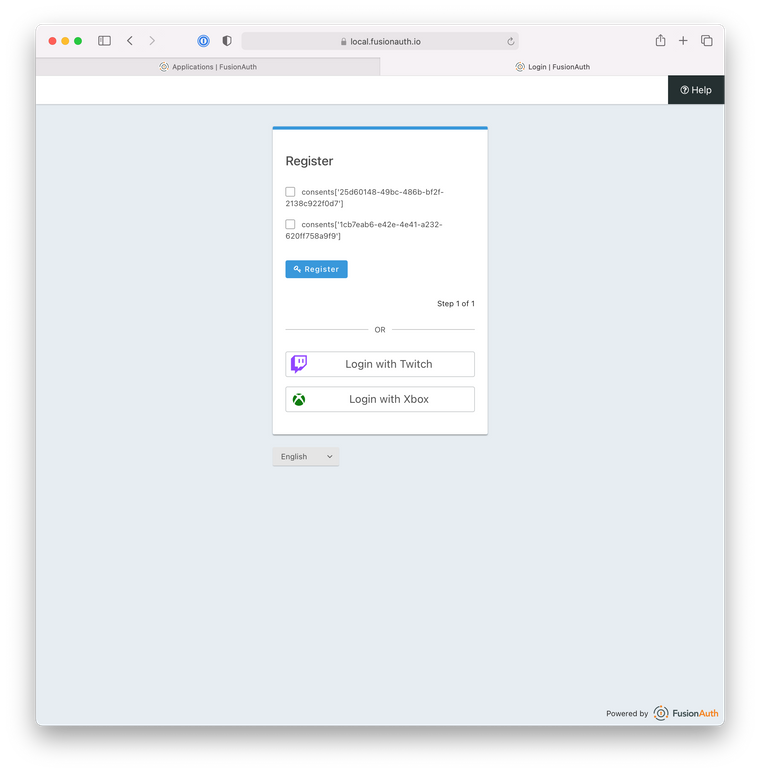



Does that require completely replacing the UX flow you have with my own hosted one?
Yes, I believe that you would have to do this to add your own pages.
- Add an Idp (you could use