Found the correct env var here: https://fusionauth.io/docs/reference/configuration#configuration-file
Best posts made by stephan
-
RE: http-proxy not picked up by fusionauthposted in Q&A
Latest posts made by stephan
-
RE: http-proxy not picked up by fusionauthposted in Q&A
Found the correct env var here: https://fusionauth.io/docs/reference/configuration#configuration-file
-
http-proxy not picked up by fusionauthposted in Q&A
Hi,
FusionAuth sits behind a http-proxy, and must use it to connect to the internet (for activating the licence)
We've tried to set the following variables in the helm chart, but no luck (see attached image)
... values: environment: - name: FUSIONAUTH_APP_ADDITIONAL_JAVA_ARGS value: -Dhttp.proxyHost=serverproxy.intern.REDACTED.de -Dhttps.proxyPort=8080 -Dhttp.nonProxyHosts="10.236.0.1|.cluster.local|.svc" - name: FUSIONAUTH_ADDITIONAL_JAVA_ARGS value: -Dhttp.proxyHost=serverproxy.intern.REDACTED.de -Dhttp.proxyPort=8080 -Dhttp.nonProxyHosts="10.236.0.1|.cluster.local|.svc" ...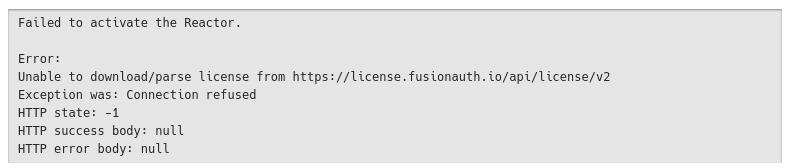
I can, however, do the following, and connect to the licence server from within the pod:
export HTTPS_PROXY=http://serverproxy.intern.REDACTED.de:8080 curl -k -vvv https://license.fusionauth.io/api/license/v2This returns a http response.
Java stacktrace in the logs:
| fusionauth 2024-04-25 11:03:43.267 AM ERROR io.fusionauth.http.server.HTTPWorker - HTTP worker threw an exception while processing a request │ │ fusionauth io.fusionauth.http.ConnectionClosedException: java.lang.InterruptedException │ │ fusionauth at io.fusionauth.http.io.BlockingByteBufferOutputStream.addBuffer(BlockingByteBufferOutputStream.java:163) │ │ fusionauth at io.fusionauth.http.io.BlockingByteBufferOutputStream.close(BlockingByteBufferOutputStream.java:69) │ │ fusionauth at io.fusionauth.http.io.DelegatingOutputStream.close(DelegatingOutputStream.java:56) │ │ fusionauth at java.base/sun.nio.cs.StreamEncoder.implClose(StreamEncoder.java:347) │ │ fusionauth at java.base/sun.nio.cs.StreamEncoder.close(StreamEncoder.java:169) │ │ fusionauth at java.base/java.io.OutputStreamWriter.close(OutputStreamWriter.java:252) │ │ fusionauth at io.fusionauth.http.server.HTTPResponse.close(HTTPResponse.java:107) │ │ fusionauth at io.fusionauth.http.server.HTTPWorker.run(HTTPWorker.java:53) │ │ fusionauth at java.base/java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:539) │ │ fusionauth at java.base/java.util.concurrent.FutureTask.run(FutureTask.java:264) │ │ fusionauth at java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1136) │ │ fusionauth at java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:635) │ │ fusionauth at java.base/java.lang.Thread.run(Thread.java:833) │ │ fusionauth Caused by: java.lang.InterruptedException: null │ │ fusionauth at java.base/java.util.concurrent.locks.ReentrantLock$Sync.lockInterruptibly(ReentrantLock.java:159) │ │ fusionauth at java.base/java.util.concurrent.locks.ReentrantLock.lockInterruptibly(ReentrantLock.java:372) │ │ fusionauth at java.base/java.util.concurrent.LinkedBlockingQueue.put(LinkedBlockingQueue.java:332) │ │ fusionauth at io.fusionauth.http.io.BlockingByteBufferOutputStream.addBuffer(BlockingByteBufferOutputStream.java:159) │ │ fusionauth ... 12 common frames omittedAlso posted the question in slack: https://fusionauth.slack.com/archives/C02DN10M95E/p1713183966365859
-
RE: Can I add the user's IP to the JWT token?posted in Q&A
@mark-robustelli We are on "Starter" unfortunately. There no other way of doing it?
-
Can I add the user's IP to the JWT token?posted in Q&A
We have a requirement to validate on our API that the JWT token comes from the IP that it was issued to, otherwise reject it. Is this possible to do? How do I access the user's current IP in a JWT populate lambda?
Thanks
-
RE: Group & Role Design in a nearly multitenant Applicatinoposted in General Discussion
Hi
You'd create a company entity type with permissions like 'admin' or 'editor', add each company as an entity, and then individually manage the grants to the use
This seems to be exactly what we need, but I'm unsure of how to get the entity grant permissions into the jwt token so that our API can do permission checks. Any tips?
Thanks