FusionAuth version: 1.47.1 (hosted version, Starter license).
I'm trying to get a SAML v2 identity provider set up against Google Workspace that allows both SP initiated and IdP initiated logins. [1] I'm struggling with how to configure this though.
Here's my basic setup:
-
I have a callback URL in my application where I do the code -> token exchange after authentication:
https://dashboard.stablebuild.com/callbacks/fusionauth?url=%2Forganizations%2Fstablebuild
FusionAuth then appends
&code=xxxxto this. -
When I do SP initiated login I redirect to (where idp_hint is the IdP ID):
I have two ACS callback URLs in the identity provider config in FusionAuth:
- Callback URL (ACS): https://stablebuild.fusionauth.io/samlv2/acs
- IdP Initiated Callback URL (ACS): https://stablebuild.fusionauth.io/samlv2/acs/5f06463b-97ae-4f93-b925-18d8ef9751a7/1c165b4b-ef9a-4fe7-bde9-89ea0498432e
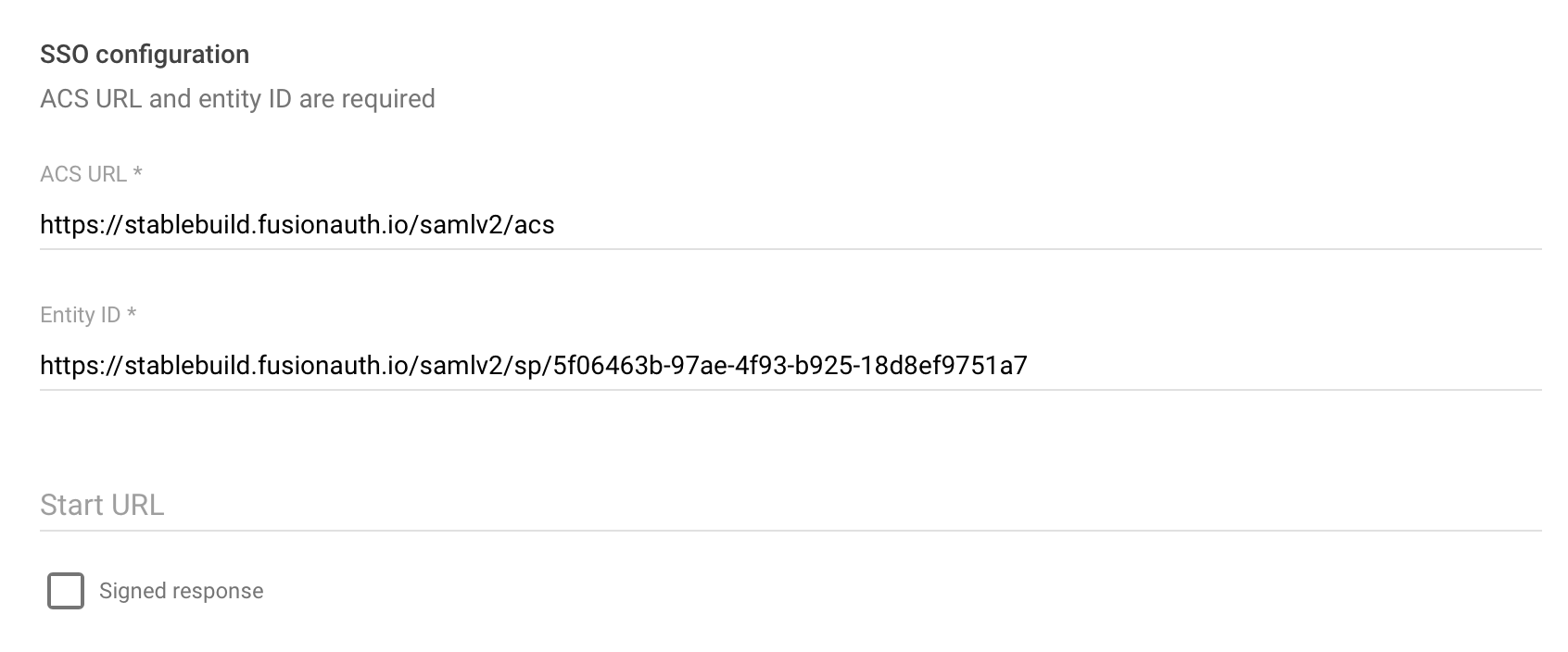
Try 1: Using the ACS callback URL
When I configure the first URL as the callback URL in Google Workspace:
Then:
-
SP initiated login works
-
IdP initiated login redirects to:
https://stablebuild.fusionauth.io/oauth2/authorize?tenantId=7c4f6470-a023-d2e5-728c-3e5137f089bb
And fails with 'The request is missing a required parameter: redirect_uri'
Try 2: Using the ACS callback URL w/ Start URL
Google describes the Start URL as "This is used to set the RelayState parameter in a SAML Request, which can be a URL to redirect to after authentication.". If I set the Start URL to my redirect URL:
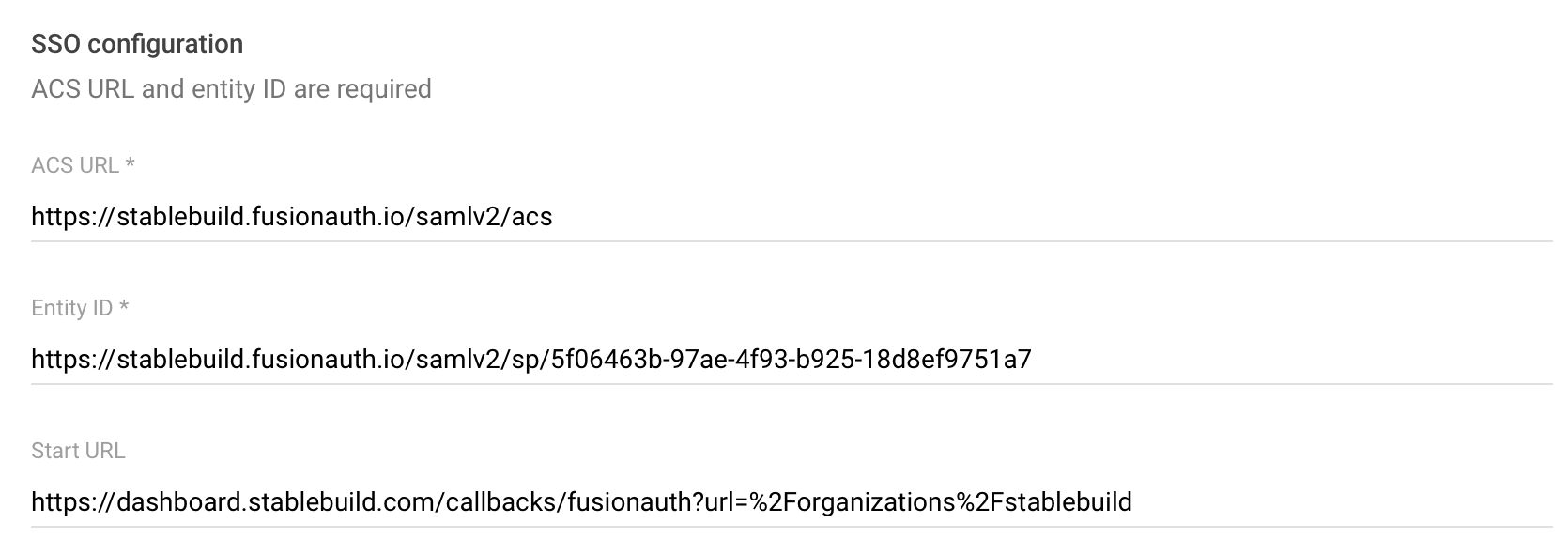
Then:
-
SP initiated login works
-
IdP initiated login redirects to:
and still fails with 'the request is missing a required parameter: redirect_uri' - makes sense, the URL is passed in the
statefield, not in theredirect_urifield.
Try 3: Using the ACS callback URL by appending ?redirect_uri
According to https://github.com/FusionAuth/fusionauth-issues/issues/1785 the RelayState parameter is indeed not supported, but we should be able to append ?redirect_uri to the callback URL. Here I append the callback URL (previously in Start URL to the ACS URL):
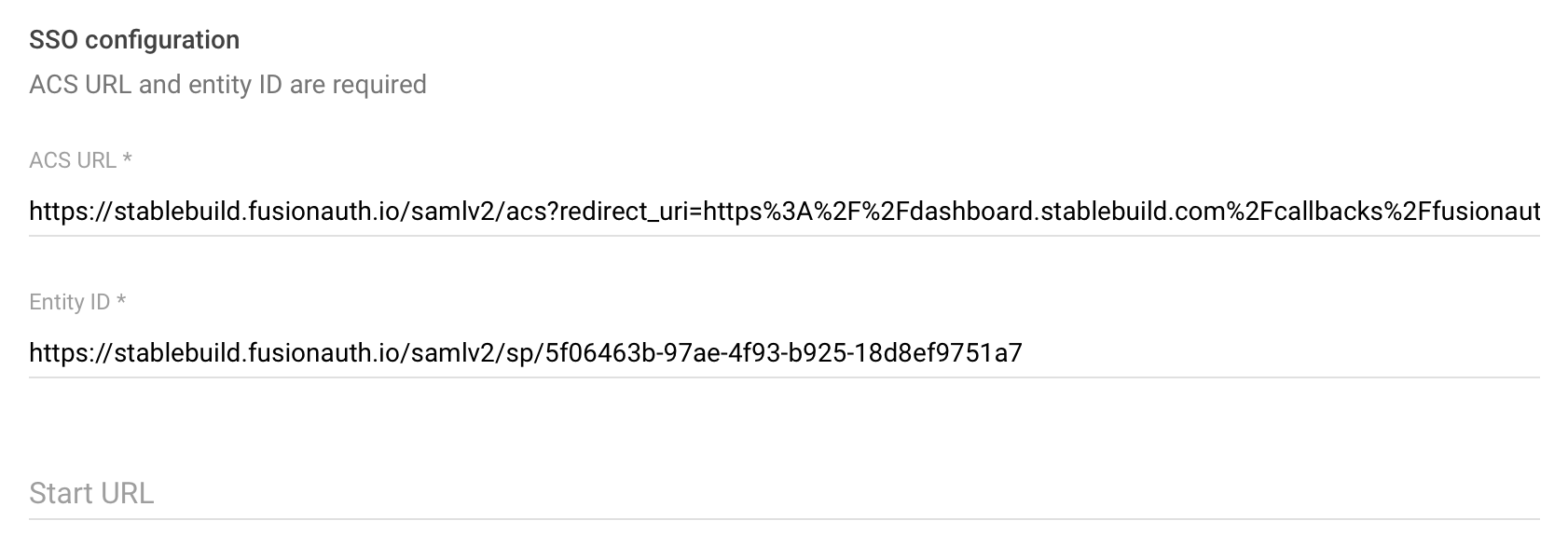
Then:
-
SP initiated login fails with:
"The SAML AuthnResponse status indicated the request has failed. Unable to complete this login request."
And in the logs I see:
<saml2p:StatusMessage>Invalid request, ACS Url in request https://stablebuild.fusionauth.io/samlv2/acs doesn't match configured ACS Url https://stablebuild.fusionauth.io/samlv2/acs/?redirect_uri=https%3A%2F%2Fdashboard.stablebuild.com%2Fcallbacks%2Ffusionauth%3Furl%3D%252Forganizations%252Fstablebuild.</saml2p:StatusMessage>So that won't work.
-
IdP initiated login redirects to:
and fails with 'The request is missing a required parameter: client_id'. So it picks up the redirect_uri at least.
So, it seems that we can append the right parameters to the URL maybe - but SP initiated login breaks whenever we do that.
Try 4: Using the IdP Initiated Callback URL w/ ?redirect_uri param
When I set the IdP initiated callback URL, with the ?redirect_uri parameter set:
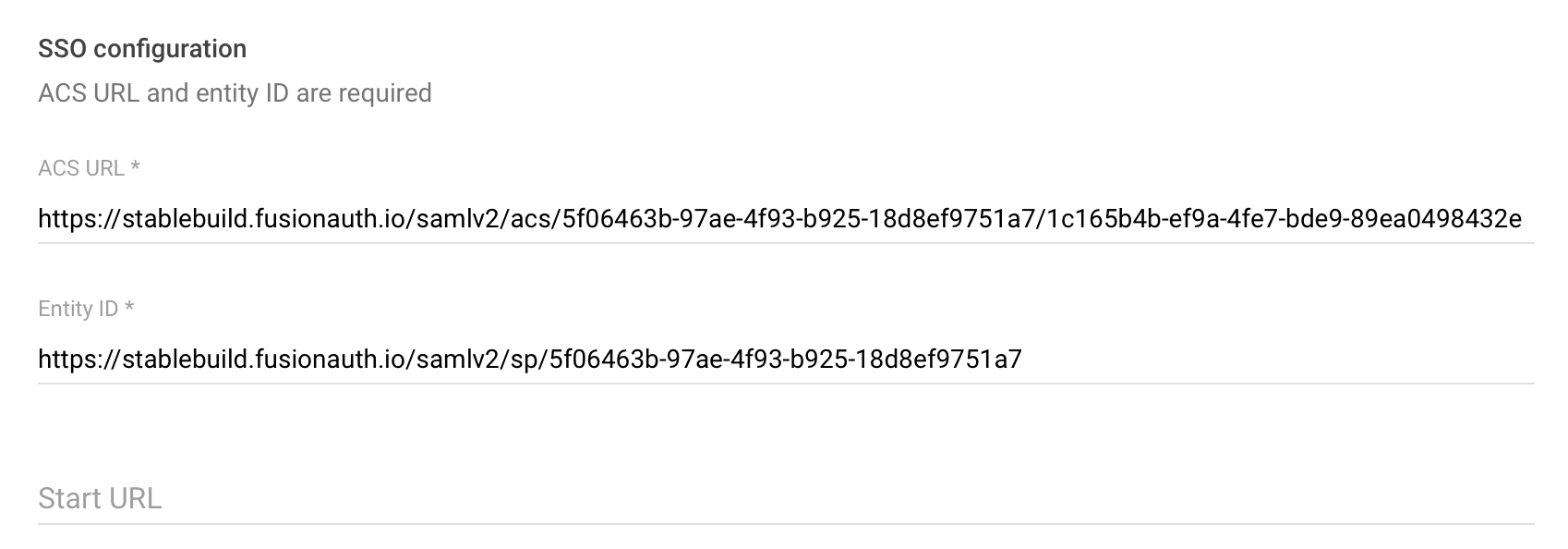
Then:
-
SP initiated login fails with:
Invalid redirect_uri Y2xpZW50X2lkPTFjMTY1YjRiLWVmOWEtNGZlNy1iZGU5LTg5ZWEwNDk4NDMyZSZyZWRpcmVjdF91cmk9aHR0cHMlM0ElMkYlMkZkYXNoYm9hcmQuc3RhYmxlYnVpbGQuY29tJTJGY2FsbGJhY2tzJTJGZnVzaW9uYXV0aCUzRnVybCUzRCUyNTJGb3JnYW5pemF0aW9ucyUyNTJGc3RhYmxlYnVpbGQmcmVzcG9uc2VfdHlwZT1jb2RlJnRlbmFudElkPTdjNGY2NDcwLWEwMjMtZDJlNS03MjhjLTNlNTEzN2YwODliYiZpZGVudGl0eVByb3ZpZGVySWQ9NWYwNjQ2M2ItOTdhZS00ZjkzLWI5MjUtMThkOGVmOTc1MWE3JmNzcmY9b1gzLVQxTzVEcVJ4NVpKVgWhich is base64 encoded:
client_id=1c165b4b-ef9a-4fe7-bde9-89ea0498432e&redirect_uri=https%3A%2F%2Fdashboard.stablebuild.com%2Fcallbacks%2Ffusionauth%3Furl%3D%252Forganizations%252Fstablebuild&response_type=code&tenantId=7c4f6470-a023-d2e5-728c-3e5137f089bb&identityProviderId=5f06463b-97ae-4f93-b925-18d8ef9751a7&csrf=oX3-T1O5DqRx5ZJVWhich looks like valid query params; but for some reason they are base64 encoded, and interpreted as just the redirect_uri.
-
IdP initiated login works.
So... ?
I'm unsure how to proceed. I think that:
- If using the RelayState parameter as the redirect URI would be supported then I guess all of this would just work out of the box (filed on GH here: I've filed https://github.com/FusionAuth/fusionauth-issues/issues/2545 as a feature request to support using the RelayState as the redirect URL.).
- Appending ?redirect_uri, as suggested in https://github.com/FusionAuth/fusionauth-issues/issues/1785 does not work for SP initiated logins (bug? feature?).
- Something gets interpreted as base64 that shouldn't when using the IdP Initiated Callback URL with an SP-initiated flow (or I'm just abusing the endpoint, and this should never be possible - but maybe this should error out with a better message).
Any suggestions?
[1]I'd assume this is a relatively common usecase, as I want to trigger an auth flow from my application (SP initiated), as well as have a button in the Google Workspace app drawer to go to the application (IdP initiated) - if I have this wrong then I'd be happy to hear that too.