Years ago, before the widespread adoption of cloud and SaaS-based offerings, IT security was arguably simpler. For a while, you could assume with a decent level of confidence that anyone inside your corporate network was meant to be there and could be trusted. Meanwhile, anyone outside the network was not to be trusted.
This is no longer the case.
With our increasing reliance on internet services, and the gradual shift toward the “work from anywhere” mindset, the edge of our trusted networks has been blurred into obscurity, and knowing who can be trusted is no longer a simple case of whether or not the user in question is inside our network.
In a successful IT security strategy, there are always many components in play. One of these components is the Identity Provider (IdP), a cornerstone of many modern systems, especially those in the enterprise space.
In this article, you will learn about the Zero Trust framework and how Identity Providers factor into it to protect your network and help keep your resources secure.
What is Zero Trust?
Originating at Forrester Research, Zero Trust is a strategic framework designed to mitigate data breaches by doing away with the concept of “trust” in enterprise networks. One of the core tenets of Zero Trust is to “never trust, always verify”, as opposed to the old-fashioned approach of assuming that any users inside the “trusted network” are meant to be there.
In order to verify a user for a given operation, a number of factors can be taken into account, including their identity, location, device details, attempted operation, and any other anomalies. This data serves to create a snapshot of who the user is and what they are trying to do, which can then be used to help inform whether or not to permit the operation.
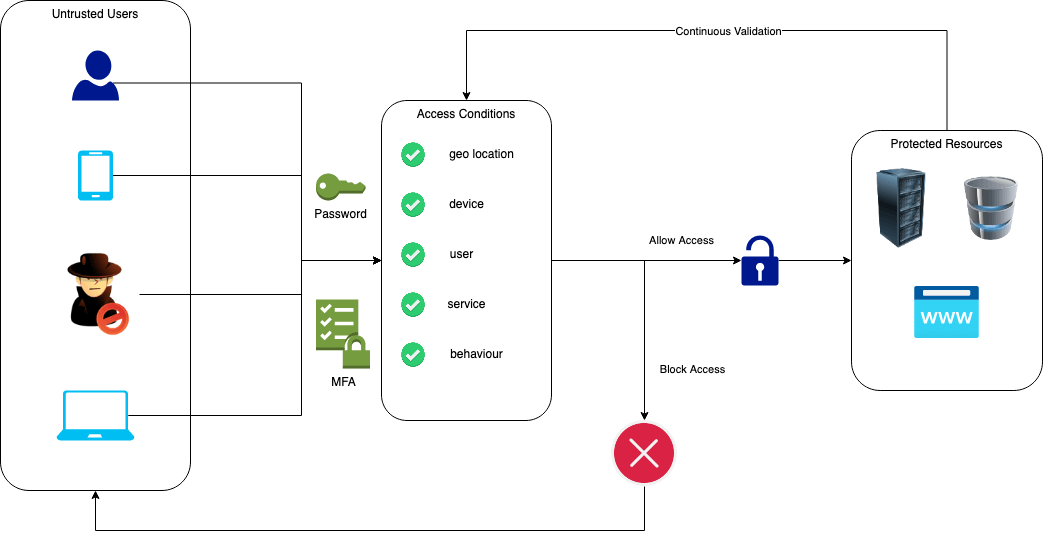
Zero Trust also factors in “preparing for the worst” by recognizing that some breaches are inevitable and preparing for them by minimizing the potential blast radius, implementing segmented access, and making use of the principle of “least privileged access” so that if a breach does occur, the impact is minimized as much as possible. Using physical security as an analogy, it’s kind of like having a lock on every door, rather than just the exterior ones. Even if someone gets into your building, there generally isn’t a lot they can do when confined to the hallways.
In recent years, the industry has seen a large-scale shift towards the Zero Trust approach. According to data from Statista, as of 2021 over 70 percent of surveyed respondents (n=357) reported that they were prioritizing the adoption of a Zero Trust model and had either started or were planning the implementation. This paradigm change is due to the disappearance of the old “secure perimeter” that businesses relied on for security before the rise of distributed cloud computing.
Now, because employees can work from anywhere, on any device, this perimeter is gone, and security practices have needed to adjust accordingly. This can impact organizations regardless of their IT setup. Full cloud and hybrid cloud approaches are obviously affected, but even the more traditional on-prem setups can be affected. The advent of Software-as-a-Service and the recent surge in remote work have caused the erosion of many traditional secure perimeters.
While Zero Trust offers a lot of advantages when it comes to securing networks, it is inherently more complex than the simpler models which preceded it. As such, properly configuring a Zero Trust environment calls for knowledge, expertise, and experience in mitigating potential security hazards. There are a number of supporting technologies that go into making a Zero Trust system work. These include:
- Multi-factor Authentication (MFA) requires the user to provide multiple points of authentication, such as a temporary code in addition to a password.
- Segmentation divides the network into smaller zones with dedicated access to only what they need, making it difficult for attackers to move laterally through a network.
- Privilege access management (PAM) allows you to restrict a user’s access to implement “least-access privilege” for each user.
Your Identity Provider (IdP), such as FusionAuth, is the key to all of this, as it provides a single source of truth for your core user identity management.
What are Identity Providers?
Identity Providers are services which store and manage digital identities. Companies often use them to manage access rights and privileges, enabling employees to get access to the assets they need to do their jobs. In essence, an IdP provides a list of identities for services (like SSO providers) to validate against. IdPs are necessary because they play a crucial role in the operation of modern IT systems. In many cases, they can be thought of as the central nervous system of your IT infrastructure, providing the information necessary for other systems to know who is allowed to access what. Naturally, this makes them an integral part of a successful Zero Trust implementation. Without an IdP, there would be no efficient way to verify a user’s identity claims and determine whether or not they should be allowed to access a given resource.
While there are different levels of IdP, something that they all have in common is the ability to enumerate all of the potential authorized users of a system. This alone might allow a system to get off the ground, but generally speaking, it won’t be enough for a successful Zero Trust approach. As mentioned above, an essential aspect of Zero Trust is the principle of Least Privileged Access. For this to happen, the IdP, or a system related to it, needs to grant users granular permissions to specific segments of the network so that a user never has more access than what they need to do their job. Some IdPs will allow the configuration of Identity and Access Management (IAM) rules, restricting certain accounts to particular parts of the broader system.
Which IdP you use will depend a lot on what your organization does. There are many options out there, but some are more suited to particular workloads. For example, one of the more traditional systems, Microsoft Active Directory, works not just in the cloud thanks to more recent offerings by Azure, but also in the more traditional way, authenticating users in a Windows domain. This is an example of a specialized trait which other IdPs may not have, so if you want a seamless identity management experience across all of your infrastructure, it is important to take a high-level look at all the systems you need to consider, to determine which IdP is best for you.
How do they work together?
To fully realize the benefits of Zero Trust and have a reliable implementation that will suit your business needs, it is necessary to have a good IdP as the foundation on which you build your infrastructure. Some IdP solutions focus on essentially just the basics, identity management and passwords. If this is the sort of IdP you are using, you will likely need additional solutions to bridge the gaps. Other IdP solutions may offer more profound control that will get you closer to a Zero Trust implementation. FusionAuth, for example, offers advanced threat detection which helps give visibility into what is going on with your users, event webhooks, and multifactor authentication, all of which are essential aspects of Zero Trust.
In most cases, you will still need to go beyond the controls offered by your IdP. Things like intrusion detection, prevention systems, and firewalls still have their place in your enterprise security, but seeing as they traditionally operate “at the edge”, there is only so much they can do to mitigate threats as the traditional perimeter continues to become increasingly obscure.
The explosion of cloud services doesn’t look like it will be slowing down anytime soon, and the security threats that come with it are here to stay for the time being. For businesses to survive the ever-changing landscape of cybersecurity threats, they need to adapt.
Experience shows that Zero Trust is one of the best ways to adapt to these changes right now, but it simply isn’t possible to implement an effective Zero Trust system without the right tools. In the fight to remain secure, your IdP is a critical component of your system. It is what allows you to do Zero Trust properly. Don’t cut corners with your IdP; lay a foundation that will help you, not hinder you.