Connector not persisting claim
-
When starting authentication from c# like this:
public IActionResult SignIn([FromRoute] string returnUrl) { var scheme = "FusionAuth"; var redirectUrl = Url.Content("~/"); var properties = new AuthenticationProperties { RedirectUri = redirectUrl, }; if(!string.IsNullOrEmpty(returnUrl) && returnUrl.ToLower() != "%2f") { properties.Items.Add("return_url", returnUrl); } return Challenge(properties, scheme); }It works great and we can migrate users using a connector. The only problem is that the return_url claim is not persisted when the fusionauth connector calls my endpoint. I setup a lambda for the application that is being used for the migration but the lambda never gets called as far as I can tell.
How do I persist a claim in the roundtrip during the use of a connector?
-
@helzgate What kind of lambda are you using? You should enable debugging for the lambda and then you can be sure to see if it is running or not.
-
@mark-robustelli I'm using GraalJS lambda and I already have debug turned on, that is how I know it isn't used.
-
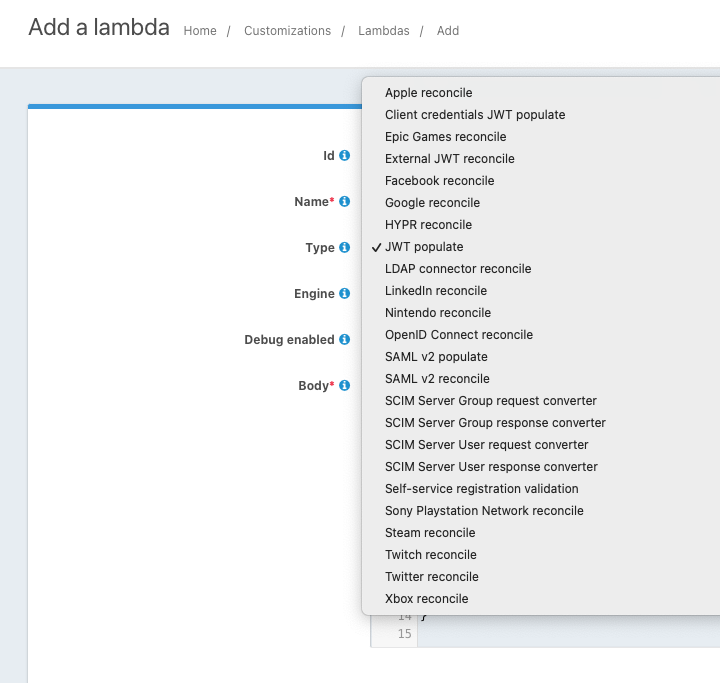
@helzgate Just to verify, is this a JWT Reconcile lambda (you may need to try External JWT Reconcile as well depending on what you are doing)? And you have it assigned to your applicaiton?
Beyond that, I think I need a little more detail on exactly how you have things set up. What are you trying to migrate from? That sort of thing.
-
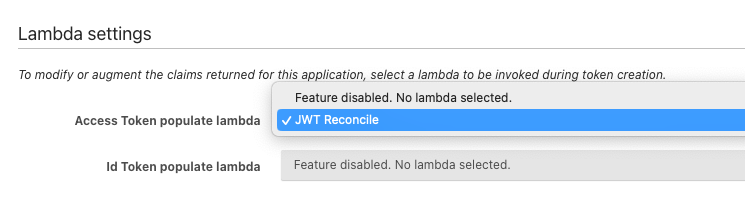
@mark-robustelli I'm using Jwt Populate. The other options are not relevant in my case.
Here is the call to authenticate I see in my browser
http://localhost:9011/oauth2/authorize?client_id=da2989a7-b0e5-4ad2-9ea5-2b1f01ebc880&redirect_uri=https%3A%2F%2Fdev1.somedomain.com%2Fsignin-oidc&response_type=code&scope=openid%20profile%20email&code_challenge=G_mxraEDekKv3A3OpmncS9VtEbbP8jK_9z92RWW9ePw&code_challenge_method=S256&response_mode=form_post&nonce=638470562867851627.MDAzN2NmYmMtMWQ0ZS00MjBmLThmMDEtNDVmOWI4NmYyYzE2NDIwMDMxYjItZDJiNi00YzA1LWI0NzctNzJkODY2ZGJiNTcx&return_url=%252Fpartner%252Flogin&state=CfDJ8F6ZIv_kW7lKoE8XeEvEDsloTq71-SuA19fiMi6eqxZiSr6MJWHyGmGHvWdEqUb-5O9mDNsvgTmm0tJJxOAxHJLAcbctP4UcyIND29yzNNM0TikTsX4QELJ2aHmPHdLCTlSBycIPdQZ1umw4GEsvrP-tKbYHT6f3YPvgqi2yoCc6W5Yxa0KBnfCDkb08zhlRDsoBjVc-nEcE7jM1K-CQhouZjoI6i4cPZZa0CX1hrGo2w166kH8l7Jn7FNU3V70BFejEpZehYKeNou-lfE38D1GRyjdeTLiSfssM9HvHD7RYn-8cZ5pEslleQLi6Hyj1m_STKKknETJNzTOxLRHrO-pI0yXwFsCJ08_IeGY33pAC2agsFK1JgQNVcd-c3z26Pp3dE8EroIRlrMJWLOwR7q6TPQui4U3WjjgbeY5N-FXv&x-client-SKU=ID_NET6_0&x-client-ver=6.35.0.0Notice this segment where I'm passing the return_url:
return_url=%252Fpartner%252FloginI need this return_url sent back to me in a claim when the user authenticates. How do I do that because in the jwt populate lambda there is no access to the request.
-
@helzgate I was focusing on your issue with the lambda not firing. You are correct in that you do not have access to the url in the lambda.
Let's take a step back here and take a look at the connector. Can you tell me how that is set up and what values are being returned from it? I'm thinking you may be able to add the return_url in the values returned from that.
-
H helzgate deleted this topic on
-
H helzgate restored this topic on
-
There is no way to get back information from FA when it calls your connector endpoint. What I ended up doing was creating separate applications for each portal in our app. WHen FA calls my connector, now I can look at the incoming applicationid and know which portal this user belongs too and that solved my issue.