Proxy Warning with NLB before Ingress
-
Hi there,
We've installed FA on a kubernetes cluster. Ingress resource is setup to get connection over http. We know that by default, TLS is terminated in the ingress controller. But we've configured it to terminate TLS in the Load Balancer. Load balancer is an AWS NLB used from https://kubernetes.github.io/ingress-nginx/deploy/#awsWe are getting the following warning, that makes total sense.
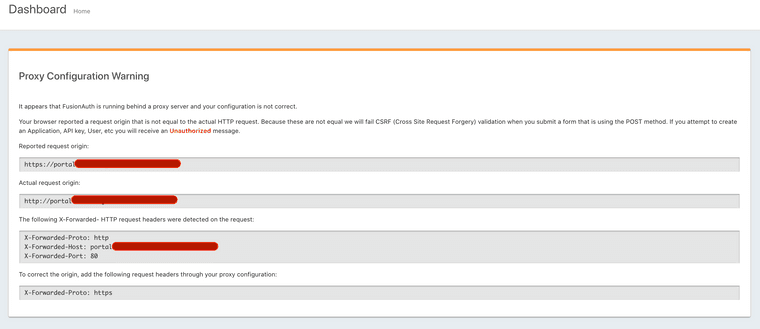
The question is how to get around this warning, and add a X-forwarded-proto header to our Ingress controller but talk over http. Please Note: We do not want to terminate TLS on Ingress controller because then we cannot get AWS Certificate Manager to renew certificates automatically.
Any help or hints to move forward would be highly appreciated.
Best Regards,
Faisal. -
What happens if you add the header, but continue to terminate TLS at the load balancer?
-
@dan
I do not know how to modify X-Forwarded-Proto to https, without terminating at the Ingress controller.
Currently the LB is setting the right headers i.e. X-Forwarded-Proto: http. And the intention is to connect to FA over http.
But because browser shows https, and doesn't matches with the origin, CSRF doesn't gets satisfied
-
FusionAuth, as you can see, doesn't like to be run without being assured TLS is involved. That is what the warnings are about. It relies on the
X-Forwarded-Prototo be assured that TLS is involved.It looks like you have this:
User -> (TLS) -> Internet -> (TLS) -> NLB -> (HTTP) -> Ingress -> (HTTP) -> FusionAuth
Which seems like a fine architecture (because from the NLB to FusionAuth is presumably a private, secure network, so TLS is not needed). The question is, how do you tell FusionAuth that things are okay? That's why I suggested trying to set the header.
I do not know how to modify X-Forwarded-Proto to https, without terminating at the Ingress controller.
I also do not know how to do this. I suggest reviewing the AWS documentation and/or contacting AWS support.
If you have a FusionAuth edition including support, you can also file a support ticket and the engineering team will take a look. (If you do that, please reference this forum post.)