Missing Email address in JWT token claims
-
The email is missing in the token claims when I call the "/api/identity-provider/login" endpoint. The user successfully logs in, but when I parse the token, the email address is missing
-
S sandiprghane has marked this topic as solved on
-
I have the same problem (since my update from 1.51.X to 1.53.2 maybe?), but only for users created with the new version. This is strange...
The email claim is then missing in the token:
{
“aud": ‘fe6b5ed0-89a5-43f8-a7af-ec69c47a0c25’,
“exp": 1726866934,
“iat": 1726863334,
“iss": ‘xyz’,
“sub": ‘c1593867-dd98-4273-b965-8a15b101fbf8’,
“jti": ‘83b5bd18-2f3e-4c9e-91b6-2f5c8e49846b’,
“authenticationType": ‘PASSWORDLESS’,
“applicationId": ‘fe6b5ed0-89a5-43f8-a7af-ec69c47a0c25’,
“roles": [],
“sid": ‘e02e3a3a-12b3-4789-905f-4a4bd01d89ec’,
“auth_time": 1726863334,
“tid": ”fe6b5ed0-89a5-43f8-a7af-ec69c47a0c25”
}Old, existing users do have the email claim in the token.
What was the solution for you @sandiprghane ?
Can anyone help?
-
@dan , can you give me a quick hint?

-
@bubblez do you have the scope correctly set within your Identiy provider?
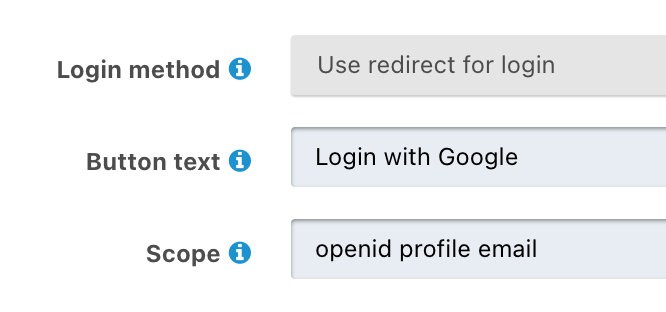
I am testing this now locally to see if there is a difference on the versions.
-
@bubblez there was also a change in 1.50 (so I am surprised if you were on 1.51 if this would happen) where we stopped sending email to the
app.idJWT and only provide this withinapp.idt.I would recommend updating the code accordingly if you are still using this method.
An alternative but not suggested is to change your scope handling policy to
Compatibilitywhich will send this again in yourapp.id.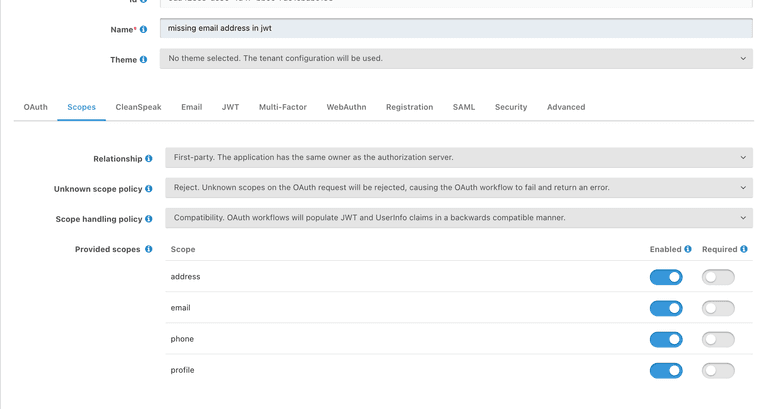
-
@Alex-Patterson
Indeed, you are right, it is because of the scope configuration, whose default values have changed. The advice in the release notes regarding this in version 1.50 also sounds appropriate in retrospect.What surprises me is that these settings are relevant when I perform the oldschool login via POST /api/login, I wasn't aware of that...
Thanks for the tip!
 I would probably have been looking for the difference for a while...
I would probably have been looking for the difference for a while...