SAML SSO for Mattermost using FusionAuth
-
Hiya,
The
NameIdformat is determined by values in the SAML document, and at this time can't be specified in configuration. From the error you are seeing, it looks like they don't provide the header specifying their format, but the Okta instructions imply that it is theUnspecifiedformat:Name ID format: unspecified
Can you please provide:
- the version of mattermost you are working with
- the version of FusionAuth you are using as your IdP
- a copy of the SAML XML would be awesome
It looks like mattermost doesn't support OIDC at this time, which is a bummer.
-
This post is deleted! -
Hello @dan ,
Thanks so much for your insights. I am using :
FusionAuth: 1.18.4
Mattermost: 5.26.0
Below is the SAML request Payload, it's from https://docs.mattermost.com/deployment/sso-saml-technical.html<samlp:AuthnRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:samlsig="http://www.w3.org/2000/09/xmldsig#" ID="_u5mpjadp1fdozfih4cj8ap4brh" Version="2.0" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" AssertionConsumerServiceURL="http://localhost:8065/login/sso/saml" IssueInstant="2019-06-08T16:00:31Z"> <saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">http://www.okta.com/exkoxukx1D8OIfY03356</saml:Issuer> <samlsig:Signature Id="Signature1"> <samlsig:SignedInfo> <samlsig:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"></samlsig:CanonicalizationMethod> <samlsig:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1"></samlsig:SignatureMethod> <samlsig:Reference URI="#_u5mpjadp1fdozfih4cj8ap4brh"> <samlsig:Transforms> <samlsig:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"></samlsig:Transform> </samlsig:Transforms> <samlsig:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"></samlsig:DigestMethod> <samlsig:DigestValue></samlsig:DigestValue> </samlsig:Reference> </samlsig:SignedInfo> <samlsig:SignatureValue></samlsig:SignatureValue> <samlsig:KeyInfo> <samlsig:X509Data> <samlsig:X509Certificate>MIIFmzCCA4OgAwIBAgIJAIusvV3gZIwiMA0GCSqGSIb3DQEBCwUAMGIxCzAJBgNVBAYTAlVTMRIwEAYDVQQHDAlQYWxvIEFsdG8xEzARBgNVBAoMCk1hdHRlcm1vc3QxDzANBgNVBAsMBkRldk9wczEZMBcGA1UEAwwQYmFzZS5leGFtcGxlLmNvbTAeFw0xOTA2MDcxMjQ0MTdaFw0yOTA2MDQxMjQ0MTdaMGIxCzAJBgNVBAYTAlVTMRIwEAYDVQQHDAlQYWxvIEFsdG8xEzARBgNVBAoMCk1hdHRlcm1vc3QxDzANBgNVBAsMBkRldk9wczEZMBcGA1UEAwwQYmFzZS5leGFtcGxlLmNvbTCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBALAfDj+RyByszTOPRL4b+cilNF/3PB1I0CG3TNzgllgy5CwRGHLKn5/t8rPsJoWLKOUGenzVdXWuoVi3jyl5FZ1N60CBbXfmSWk20dSIkcYCcYEgs1BTBqKKYFw2dV4M0oppzNtlq7A0Glpg/gpaR/2TXEPAhOsUfORC2qAdJt9ev0AQjp5V0TkIKMZz8oo33Coi38TG5r/LG+ihRbpWzO7j9Rc2S5I6bczvG4wOg7nVKG+B5XBvuU9PjSqgxpd/F/fYf+ggAEru58E+VM4veCRV8vSPbBqDG4FMPV6DiA+tH/70n6zuPCS3soxX00kjKtP80QD6UgzvM2NN7PHiNlf0Zj6VCU3VdjEnypg7dzlHJuyyaAaTD5nSfkecamEoJpq7kaUB7uTmBHELRUhOOy24f54HnP72vnxicZL8cWsOkJwQAqIGzBxQ7J0uX4Os71WrV2YIur8QVk6KN6MBPxfiCh3xO/R+cycgx0aMrWZoyzOzP7NCTM5MNE41C48xeGviyCtUID4xiBow+xo6IDUaiCoUVJhz579ore8ic70a19DD0qHy4SpBvrUwCO54kvkgn6HjYlLC/k8nFM9F9W9wVAQD/QwIjd7EtLZLGgbU61Jv3q4kZxxq270hogCRY0lmI3RxkedGHhetF7kaizrikW5zJQEeido/ir37HhX5AgMBAAGjVDBSMBIGA1UdEwEB/wQIMAYBAf8CAQAwPAYDVR0RBDUwM4IQbG9ncy5leGFtcGxlLmNvbYITbWV0cmljcy5leGFtcGxlLmNvbYcEwKgAAYcEfwAAATANBgkqhkiG9w0BAQsFAAOCAgEAH1O91BABHXZjrU7v1OwG+GbU/4TYZqBXXNxax++OFSRCkEEoNKGg49R6J7lY4lrm12zBlw+oGSyjIOerzi39/dcxDkKpzyhGvEN4mExbDlybmdCVrHPeWgZl7uwqn4Bj1xiu97M6eMthgxJE7KVNDGDHthGL0/fTlONIh3qS7Far33hLHJJKy3+lC1MDB8cNltV3mf/ctHCx5Wa0bfZId0MJgd/seP0WU1HCf3kIxhnhsnOYs32xu7EGiM4/lgnquVd/q/f99ueSaDSHrep373/w2ce9iF3U0qcLd2iP8ayF/daGeW1dVPL9R10Oe4BpRjMkjlLwhZdjJeKSg9GBa2GXUEn1Ru9vpSw/C10no3Qx/6ZHweYbSmJ6hBg4T0nDBp6iVS1eQULNXxDuDWb26U0ESOO5jK8ATywuc45o0bqdvD1XOrGYGfGnofx7ofRWwKHWfltvxurnbsyo2vH6nM6K41K2DpVdyQOKAGvKe/oCWfdi+WyBQJGWcIp2OTC1XyWHv7JsY3lo04+islkHEcqJyd8Rf8GWmRHdXz0WzGiZbxWzAuvRRWnzM31VAws8kQBHTBwIJlJoGX4AXfEvPi+NTxkntf8cQdJucK9ZZbP4ycXHULO4LneyJoJ9Q7nxX11xWv7BDWxxclOXy6tyUkg9Fjb7pQ/HCVvGhRzilVU=</samlsig:X509Certificate> </samlsig:X509Data> </samlsig:KeyInfo> </samlsig:Signature> </samlp:AuthnRequest>Best Regards,
-
Hmm. SAML seems such an intricate protocol. Thanks for the XML file, it really helps.
OK, so it turns our our SAML processing code is open source, so you can check out the classes referenced in the stack trace here:
It looks to me like the
NameIDPolicyis optional (per https://docs.oasis-open.org/security/saml/v2.0/saml-core-2.0-os.pdf ) and I don't see it in the XML you provide. We handle that on line 468 in the service file, but for some reason this XML file is slipping through and we're getting a blank format, which the code doesn't know how to handle.Depending on your skill, desire and timeframe, you could submit a pull request to that repository fixing this issue. Another option is to create a bug report here: https://github.com/fusionauth/fusionauth-issues and reference this forum post.
Unfortunately we can't commit to a timeframe for a fix, but filing it there will put it on the engineers' radar. (More about our roadmap: https://fusionauth.io/community/forum/topic/172/the-fusionauth-roadmap )
-
If I understand correctly, you are using FusionAuth as the SAML v2 Identity Provider (IdP), and Mattermost is the SAML Service Provider (SP).
The example XML request doesn't seem to line up with the exception you received. The exception indicates that a
NameIDPolicyelement was found in the request but it did not have aformatassigned. But in the example XML request there is not aNameIDPolicyelement. If we encounter a request without theNameIDPolicywe default to email (urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress).When you set up your application in Mattermost, what did you set for the
Name ID formatconfiguration? And what are the available choices?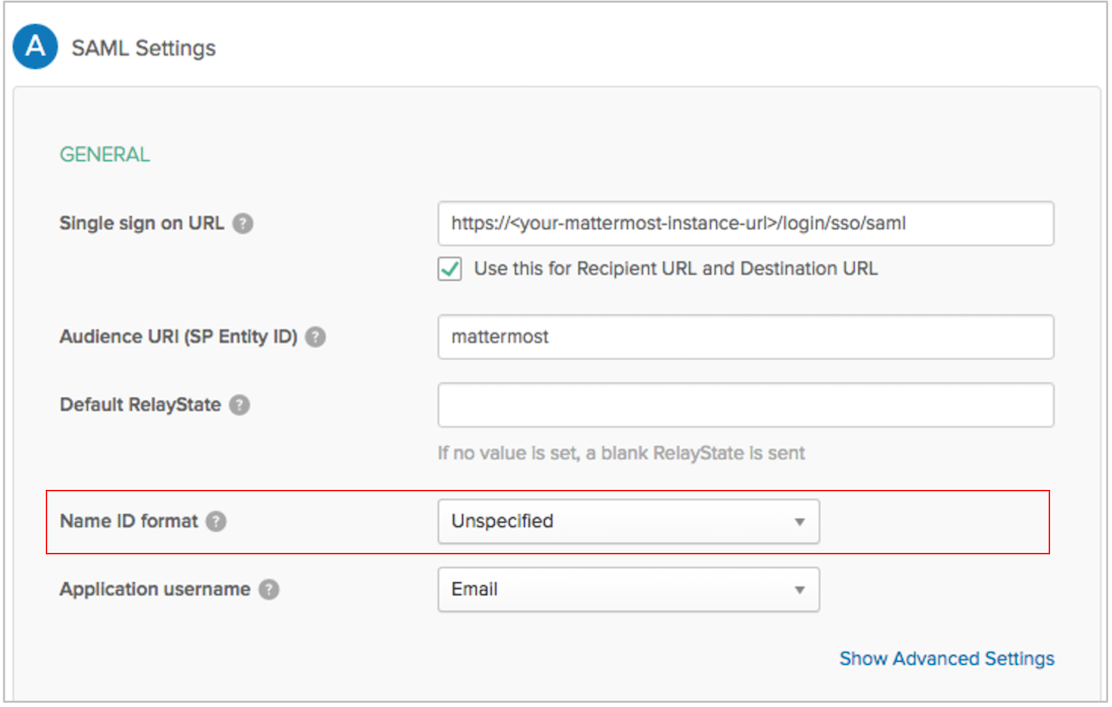
Additionally, if you want to enable debug logging in FusionAuth, we will print the XML request to the log and that will also help debug this issue.
To enable debug for the SAML parser, use the following
curlrequest and replace<YOUR API KEY>with your API key, andhttp://localhost:9011with the URL of your FusionAuth instance.curl -H"Authorization: <YOUR API KEY>" http://localhost:9011/logger\?name\=io.fusionauth.samlv2.service\&level\=debugOnce you do that, recreate the error, and then capture the XML request in the
fusionauth-app.logfile. -
@robotdan said in SAML SSO for Mattermost using FusionAuth:
usionauth-app.log
Hello @robotdan. Thanks for your insights. There is no place in mattermost for specifying a name id format and there is no place I have seen in FusionAuth to mark the name id format as unspecified like in the documentation for okta. But as @dan explains it's because it's in blank format. One option is to check from mattermost if the name id should be blank or null or blank.
I have also not been able to run the /logger command successfully. I have also looked into the API to see if there was a typo but, I didn't find it. Below is what it produces when I run the command:
curl -H "Authorization: 6YJsGGVP2BGOWni_y8sp0IgyhuCEekhH6070MP_k4gc" "http://localhost:9011/api/logger\?name\=io.fusionauth.samlv2.service\&level\=debug" ✔ 07:56:57 <!doctype html><html lang="en"><head><title>HTTP Status 400 – Bad Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400 – Bad Request</h1><hr class="line" /><p><b>Type</b> Exception Report</p><p><b>Message</b> Invalid character found in the request target. The valid characters are defined in RFC 7230 and RFC 3986</p><p><b>Description</b> The server cannot or will not process the request due to something that is perceived to be a client error (e.g., malformed request syntax, invalid request message framing, or deceptive request routing).</p><p><b>Exception</b></p><pre>java.lang.IllegalArgumentException: Invalid character found in the request target. The valid characters are defined in RFC 7230 and RFC 3986 org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:509) org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:502) org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:818) org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1623) org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1130) java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:630) org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) java.base/java.lang.Thread.run(Thread.java:832) </pre><p><b>Note</b> The full stack trace of the root cause is available in the server logs.</p><hr class="line" /><h3>Apache Tomcat/8.5.53</h3></body></html> -
hmmm I understand. It will adventurous for me to think I can send a pull request for a SAML project. I haven't dealt with SAML from a programming perspective before. Now for a pure java code perspective, I would have submitted this:
/** * Locates the NameIDFormat using the given SAML String. This is the value from the StatusCode element's value. * * @param samlFormat The SAML string. * @return The NameIDFormat enum instance. * @throws IllegalArgumentException If the samlFormat String is not a valid name ID format. */ public static NameIDFormat fromSAMLFormat(String samlFormat) { if (string.IsNullOrWhiteSpace(samlFormat)) { /// or add if((samlFormat?.Trim().length == 0) {return null;} after the original if (samlFormat == null) return null; } for (NameIDFormat nameID : NameIDFormat.values()) { if (nameID.toSAMLFormat().equals(samlFormat)) { return nameID; } } // SAML sucks, so just guess. // - It seems people are using urn:oasis:names:tc:SAML:2.0:nameid-format:emailAddress even though this is not valid. if (samlFormat.toLowerCase().contains("email")) { return EmailAddress; } throw new IllegalArgumentException("Invalid SAML v2.0 Name ID format [" + samlFormat + "]"); } -
I don't think your
curlrequest is correct.You do not need to escape anything if you double quote it. If you are going to quote the URL, then it would look like this:curl -H "Authorization: 6YJsGGVP2BGOWni_y8sp0IgyhuCEekhH6070MP_k4gc" "http://localhost:9011/api/logger?name=io.fusionauth.samlv2.service&level=debug"Or in my example, I did not quote the URL, so I had to escape it.
curl -H "Authorization: 6YJsGGVP2BGOWni_y8sp0IgyhuCEekhH6070MP_k4gc" http://localhost:9011/api/logger\?name\=io.fusionauth.samlv2.service\&level\=debugBeing able to review the SAML XML request will be our best chance to understand how to fix it.
-
@misterjoj Thanks!
I think before we move forward with a code change, it'd be good to take a look at the XML which is being sent.
-
Thanks to @robotdan I have been able to switch on the debug level. Below is the XML being sent
fusionauth_1 | Aug 24, 2020 6:09:52.024 PM DEBUG io.fusionauth.samlv2.service.DefaultSAMLv2Service - SAMLRequest XML is fusionauth_1 | <samlp:AuthnRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" AssertionConsumerServiceURL="http://localhost:8000/login/sso/saml" Destination="http://localhost:9011/samlv2/login/7dc5ea85-3495-3e94-62db-fc50e759d978" ID="_07e838e3-6d4a-45fd-9f97-307ea33802b6" IssueInstant="2020-08-24T18:09:51Z" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Version="2.0"><saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">http://localhost:8000/login/sso/saml</saml:Issuer><ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:SignedInfo><ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/><ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1"/><ds:Reference URI="#_07e838e3-6d4a-45fd-9f97-307ea33802b6"><ds:Transforms><ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/><ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/></ds:Transforms><ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/><ds:DigestValue>7j2BZ5Gtd7D9QwgV5lrjjduK+uY=</ds:DigestValue></ds:Reference></ds:SignedInfo><ds:SignatureValue>OY96Y439syU7Zfz5esljLalM3/4SsVsm7xY/f61vrC2AM50EA1nUk4zQ6IbhEfy99npPxtbStqZ8KSWymq4dZbb0Q5xpi211y/hEOPVh+fcoSIPcL8EopaJ/HxJRNSYGv29oALwnMggET/0ORDawSBep8c2VEjDJozIL9RPwW70fD/HMi92dhOLi+uiofdr7w552igwxsMOLDj6swOs9tdNZrSQ2VcOcA9N6RvJSi4qWm9nMnaXQqzZcZewmL/nQ80Wz8XzTIngIqUSOL4Ulj88PvFsIb+fWsCnTZVFmSTq9WqRSYKv5ldIkckU5Hm1MY20607RPx82Dl91AEzWQLCCGnQvED3STg8AmFOe9aIlN/kMyd4Q4eutdRqH0Vzy8hPAPs2DPzNzesLhMBkIEu5iDdu0JFrWoc+Ysj0rAinCSvGQhPdPievLHaelzF2Yzyr4KSfjSLJhxs0Uqb30c1tqcAtAAH3+u7NLHpEbc0/+Bx8ao9AJpWKiFfVGPLw9KNLbTUVTs61zwNTnGp24d7rq84IcHWGd5UZMX9WFu66LmvnxansuC5xR4TUAvmAIoryuAPEiR6EK1Vt4A9MMjRGmx+cLjd1V+z+Pe6iWgcMv8iAB912MytKMms2u7XUKXng2GthkH8UE/HjXg89gjENajpoJCmhqecdeOjTNSU3s=</ds:SignatureValue><ds:KeyInfo><ds:X509Data><ds:X509Certificate>MIIFjDCCA3SgAwIBAgIUCeAwhCwAOr8GKURZEYhJskUIjTEwDQYJKoZIhvcNAQELBQAwZjELMAkGA1UEBhMCVVMxEjAQBgNVBAcMCVBhbG8gQWx0bzETMBEGA1UECgwKTWF0dGVybW9zdDEPMA0GA1UECwwGRGV2T3BzMR0wGwYDVQQDDBRtYXR0ZXJtb3N0LmxvY2FsaG9zdDAeFw0yMDA4MTkxNDE0MjVaFw0zMDA4MTcxNDE0MjVaMGYxCzAJBgNVBAYTAlVTMRIwEAYDVQQHDAlQYWxvIEFsdG8xEzARBgNVBAoMCk1hdHRlcm1vc3QxDzANBgNVBAsMBkRldk9wczEdMBsGA1UEAwwUbWF0dGVybW9zdC5sb2NhbGhvc3QwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQDRqCWOJFGO5pZE6DPk068roQ/FDUSAx5aTQ1YAgysV/5zRuRXtOh/abPjonFRzvv8FzYDQbfi88jP9JlxjIY6C8D1v4DGscknKkoYkR6XXD3G2QWD0wlz+JZ8ODC+cKvMeEj4fwQ6CHu7EaGGRb7bgQyQxhcjnmg7NcYb0xwVbneju4ErFx4hLL69KZHdwMLDUcQ8hvPzN38KqOUs2gxcPg6PagVDYT2VvcthyOk1pyesoh8m+pvp23zwg5F1KPdza4OU8gf4YH9IPoBmdS2UZVAgughvvrlQnPvoHqCx6ILy+tNwcFesVJGgRI2fWyMwbXOSGVAaxetkt32Qkv96RG+w29yMDZM+bBE475z45GPmzQuNzUm/uY78MdgZ5CNTnUiifflD1Hvtc89KpJbPxJ6d1vwUedgVrRgiPVNTErYAyrX94HEL5J2/82SRhK19twYYtwGxps8fknN5Hit7n8nBU+iIF2JxShwyGhdPuT3T9hOGilxleTBJSOA6UkYJ0jSAk/cEupx1FrM0UjK6tljIuJqAZdzwiCOTlwgwyiOZq2Sbh21moitJNjsrQolopNX8hvPna2Z+mjlD8FKbs1ByqCLrxsQwFoIUaK5mIrGec3TWnSeyNnmyBwtb5y3qgNDgJMgmf69QDVdz8bOZLP9IK2Z66UvnFLhGnMs/QBQIDAQABozIwMDASBgNVHRMBAf8ECDAGAQH/AgEAMBoGA1UdEQQTMBGCCWxvY2FsaG9zdIcEfwAAATANBgkqhkiG9w0BAQsFAAOCAgEAiWlqVfSO093GUBOCEzlP7d5HRh3coZtMl/HPf0/evMfnzrqoDpPmMmdWb24tlVhVsE8l1ojr4b3WeHICkOyVGx5/SW1mDpbcZVbza3xwuwVQFvIAx49smZv4KdUM5lAGKTqVYxDogl7eZX+g9jwKMwxTXAOI3DJEjtg0inTk765crqkpPm6vGPKZy00Y5ydYXIePh+LjDLkPYk++1/KEJGGMBMcwywjhMQr3GAd9+uLXq6gO7Qf04HU0lkvHOSXIPfHkBc9+jbsPx8//WvLrYyK5w2UMawkWNYjWFy5XECljBsoFGPXsB6iSRzV/4X3AMIQyZozVpCgIh0YL+RSEjpx8HvDZXb6lCOSJigu5uUViRuExYc5a2RHqH3Vic4up98272B/5peqY/zilpL3bbBZHdJkEVxlzNPExkdwAhE6e/f4uMP3VI86XRysTP/FBb+0MCyeu2d6nikh/RFk/zRiXfyMWWVbUivnkc9jGkgbOshc1UE/G3xscBU0Wr36EJh42G95Vu15OicGOB2ULgy9hSapt3svYEYenVFG7ZEINePGtVwETGEDz6rCuXiteomfO1SE3Pa8oF6okEb/U3oENxRsPo1rfZoKtB1ZokMPYR5D2JnqUZgp0YFuKWj2estGf/D45RgV6himhOxejNJstcl4SdI7yPOQFbnHtMrU=</ds:X509Certificate></ds:X509Data></ds:KeyInfo></ds:Signature><samlp:NameIDPolicy AllowCreate="true" Format=""/></samlp:AuthnRequest>when formatted using an online tool we have the following
<?xml version="1.0" encoding="UTF-8"?> <samlp:AuthnRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" AssertionConsumerServiceURL="http://localhost:8000/login/sso/saml" Destination="http://localhost:9011/samlv2/login/7dc5ea85-3495-3e94-62db-fc50e759d978" ID="_07e838e3-6d4a-45fd-9f97-307ea33802b6" IssueInstant="2020-08-24T18:09:51Z" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Version="2.0"> <saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">http://localhost:8000/login/sso/saml</saml:Issuer> <ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#"> <ds:SignedInfo> <ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" /> <ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1" /> <ds:Reference URI="#_07e838e3-6d4a-45fd-9f97-307ea33802b6"> <ds:Transforms> <ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" /> <ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" /> </ds:Transforms> <ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1" /> <ds:DigestValue>7j2BZ5Gtd7D9QwgV5lrjjduK+uY=</ds:DigestValue> </ds:Reference> </ds:SignedInfo> <ds:SignatureValue>OY96Y439syU7Zfz5esljLalM3/4SsVsm7xY/f61vrC2AM50EA1nUk4zQ6IbhEfy99npPxtbStqZ8KSWymq4dZbb0Q5xpi211y/hEOPVh+fcoSIPcL8EopaJ/HxJRNSYGv29oALwnMggET/0ORDawSBep8c2VEjDJozIL9RPwW70fD/HMi92dhOLi+uiofdr7w552igwxsMOLDj6swOs9tdNZrSQ2VcOcA9N6RvJSi4qWm9nMnaXQqzZcZewmL/nQ80Wz8XzTIngIqUSOL4Ulj88PvFsIb+fWsCnTZVFmSTq9WqRSYKv5ldIkckU5Hm1MY20607RPx82Dl91AEzWQLCCGnQvED3STg8AmFOe9aIlN/kMyd4Q4eutdRqH0Vzy8hPAPs2DPzNzesLhMBkIEu5iDdu0JFrWoc+Ysj0rAinCSvGQhPdPievLHaelzF2Yzyr4KSfjSLJhxs0Uqb30c1tqcAtAAH3+u7NLHpEbc0/+Bx8ao9AJpWKiFfVGPLw9KNLbTUVTs61zwNTnGp24d7rq84IcHWGd5UZMX9WFu66LmvnxansuC5xR4TUAvmAIoryuAPEiR6EK1Vt4A9MMjRGmx+cLjd1V+z+Pe6iWgcMv8iAB912MytKMms2u7XUKXng2GthkH8UE/HjXg89gjENajpoJCmhqecdeOjTNSU3s=</ds:SignatureValue> <ds:KeyInfo> <ds:X509Data> <ds:X509Certificate>MIIFjDCCA3SgAwIBAgIUCeAwhCwAOr8GKURZEYhJskUIjTEwDQYJKoZIhvcNAQELBQAwZjELMAkGA1UEBhMCVVMxEjAQBgNVBAcMCVBhbG8gQWx0bzETMBEGA1UECgwKTWF0dGVybW9zdDEPMA0GA1UECwwGRGV2T3BzMR0wGwYDVQQDDBRtYXR0ZXJtb3N0LmxvY2FsaG9zdDAeFw0yMDA4MTkxNDE0MjVaFw0zMDA4MTcxNDE0MjVaMGYxCzAJBgNVBAYTAlVTMRIwEAYDVQQHDAlQYWxvIEFsdG8xEzARBgNVBAoMCk1hdHRlcm1vc3QxDzANBgNVBAsMBkRldk9wczEdMBsGA1UEAwwUbWF0dGVybW9zdC5sb2NhbGhvc3QwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQDRqCWOJFGO5pZE6DPk068roQ/FDUSAx5aTQ1YAgysV/5zRuRXtOh/abPjonFRzvv8FzYDQbfi88jP9JlxjIY6C8D1v4DGscknKkoYkR6XXD3G2QWD0wlz+JZ8ODC+cKvMeEj4fwQ6CHu7EaGGRb7bgQyQxhcjnmg7NcYb0xwVbneju4ErFx4hLL69KZHdwMLDUcQ8hvPzN38KqOUs2gxcPg6PagVDYT2VvcthyOk1pyesoh8m+pvp23zwg5F1KPdza4OU8gf4YH9IPoBmdS2UZVAgughvvrlQnPvoHqCx6ILy+tNwcFesVJGgRI2fWyMwbXOSGVAaxetkt32Qkv96RG+w29yMDZM+bBE475z45GPmzQuNzUm/uY78MdgZ5CNTnUiifflD1Hvtc89KpJbPxJ6d1vwUedgVrRgiPVNTErYAyrX94HEL5J2/82SRhK19twYYtwGxps8fknN5Hit7n8nBU+iIF2JxShwyGhdPuT3T9hOGilxleTBJSOA6UkYJ0jSAk/cEupx1FrM0UjK6tljIuJqAZdzwiCOTlwgwyiOZq2Sbh21moitJNjsrQolopNX8hvPna2Z+mjlD8FKbs1ByqCLrxsQwFoIUaK5mIrGec3TWnSeyNnmyBwtb5y3qgNDgJMgmf69QDVdz8bOZLP9IK2Z66UvnFLhGnMs/QBQIDAQABozIwMDASBgNVHRMBAf8ECDAGAQH/AgEAMBoGA1UdEQQTMBGCCWxvY2FsaG9zdIcEfwAAATANBgkqhkiG9w0BAQsFAAOCAgEAiWlqVfSO093GUBOCEzlP7d5HRh3coZtMl/HPf0/evMfnzrqoDpPmMmdWb24tlVhVsE8l1ojr4b3WeHICkOyVGx5/SW1mDpbcZVbza3xwuwVQFvIAx49smZv4KdUM5lAGKTqVYxDogl7eZX+g9jwKMwxTXAOI3DJEjtg0inTk765crqkpPm6vGPKZy00Y5ydYXIePh+LjDLkPYk++1/KEJGGMBMcwywjhMQr3GAd9+uLXq6gO7Qf04HU0lkvHOSXIPfHkBc9+jbsPx8//WvLrYyK5w2UMawkWNYjWFy5XECljBsoFGPXsB6iSRzV/4X3AMIQyZozVpCgIh0YL+RSEjpx8HvDZXb6lCOSJigu5uUViRuExYc5a2RHqH3Vic4up98272B/5peqY/zilpL3bbBZHdJkEVxlzNPExkdwAhE6e/f4uMP3VI86XRysTP/FBb+0MCyeu2d6nikh/RFk/zRiXfyMWWVbUivnkc9jGkgbOshc1UE/G3xscBU0Wr36EJh42G95Vu15OicGOB2ULgy9hSapt3svYEYenVFG7ZEINePGtVwETGEDz6rCuXiteomfO1SE3Pa8oF6okEb/U3oENxRsPo1rfZoKtB1ZokMPYR5D2JnqUZgp0YFuKWj2estGf/D45RgV6himhOxejNJstcl4SdI7yPOQFbnHtMrU=</ds:X509Certificate> </ds:X509Data> </ds:KeyInfo> </ds:Signature> <samlp:NameIDPolicy AllowCreate="true" Format="" /> </samlp:AuthnRequest>I am also sharing the metadata from my mattermost install got using the following
curl http://localhost:8000/api/v4/saml/metadata -o metadata.xml<?xml version='1.0' encoding='UTF-8'?> <EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" validUntil="2020-08-31T18:08:27.516331114Z" entityID="http://localhost:8000/login/sso/saml"> <SPSSODescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" AuthnRequestsSigned="true" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"> <KeyDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" use="signing"> <KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#"> <X509Data xmlns="http://www.w3.org/2000/09/xmldsig#"> <X509Certificate xmlns="http://www.w3.org/2000/09/xmldsig#">MIIFjDCCA3SgAwIBAgIUCeAwhCwAOr8GKURZEYhJskUIjTEwDQYJKoZIhvcNAQELBQAwZjELMAkGA1UEBhMCVVMxEjAQBgNVBAcMCVBhbG8gQWx0bzETMBEGA1UECgwKTWF0dGVybW9zdDEPMA0GA1UECwwGRGV2T3BzMR0wGwYDVQQDDBRtYXR0ZXJtb3N0LmxvY2FsaG9zdDAeFw0yMDA4MTkxNDE0MjVaFw0zMDA4MTcxNDE0MjVaMGYxCzAJBgNVBAYTAlVTMRIwEAYDVQQHDAlQYWxvIEFsdG8xEzARBgNVBAoMCk1hdHRlcm1vc3QxDzANBgNVBAsMBkRldk9wczEdMBsGA1UEAwwUbWF0dGVybW9zdC5sb2NhbGhvc3QwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQDRqCWOJFGO5pZE6DPk068roQ/FDUSAx5aTQ1YAgysV/5zRuRXtOh/abPjonFRzvv8FzYDQbfi88jP9JlxjIY6C8D1v4DGscknKkoYkR6XXD3G2QWD0wlz+JZ8ODC+cKvMeEj4fwQ6CHu7EaGGRb7bgQyQxhcjnmg7NcYb0xwVbneju4ErFx4hLL69KZHdwMLDUcQ8hvPzN38KqOUs2gxcPg6PagVDYT2VvcthyOk1pyesoh8m+pvp23zwg5F1KPdza4OU8gf4YH9IPoBmdS2UZVAgughvvrlQnPvoHqCx6ILy+tNwcFesVJGgRI2fWyMwbXOSGVAaxetkt32Qkv96RG+w29yMDZM+bBE475z45GPmzQuNzUm/uY78MdgZ5CNTnUiifflD1Hvtc89KpJbPxJ6d1vwUedgVrRgiPVNTErYAyrX94HEL5J2/82SRhK19twYYtwGxps8fknN5Hit7n8nBU+iIF2JxShwyGhdPuT3T9hOGilxleTBJSOA6UkYJ0jSAk/cEupx1FrM0UjK6tljIuJqAZdzwiCOTlwgwyiOZq2Sbh21moitJNjsrQolopNX8hvPna2Z+mjlD8FKbs1ByqCLrxsQwFoIUaK5mIrGec3TWnSeyNnmyBwtb5y3qgNDgJMgmf69QDVdz8bOZLP9IK2Z66UvnFLhGnMs/QBQIDAQABozIwMDASBgNVHRMBAf8ECDAGAQH/AgEAMBoGA1UdEQQTMBGCCWxvY2FsaG9zdIcEfwAAATANBgkqhkiG9w0BAQsFAAOCAgEAiWlqVfSO093GUBOCEzlP7d5HRh3coZtMl/HPf0/evMfnzrqoDpPmMmdWb24tlVhVsE8l1ojr4b3WeHICkOyVGx5/SW1mDpbcZVbza3xwuwVQFvIAx49smZv4KdUM5lAGKTqVYxDogl7eZX+g9jwKMwxTXAOI3DJEjtg0inTk765crqkpPm6vGPKZy00Y5ydYXIePh+LjDLkPYk++1/KEJGGMBMcwywjhMQr3GAd9+uLXq6gO7Qf04HU0lkvHOSXIPfHkBc9+jbsPx8//WvLrYyK5w2UMawkWNYjWFy5XECljBsoFGPXsB6iSRzV/4X3AMIQyZozVpCgIh0YL+RSEjpx8HvDZXb6lCOSJigu5uUViRuExYc5a2RHqH3Vic4up98272B/5peqY/zilpL3bbBZHdJkEVxlzNPExkdwAhE6e/f4uMP3VI86XRysTP/FBb+0MCyeu2d6nikh/RFk/zRiXfyMWWVbUivnkc9jGkgbOshc1UE/G3xscBU0Wr36EJh42G95Vu15OicGOB2ULgy9hSapt3svYEYenVFG7ZEINePGtVwETGEDz6rCuXiteomfO1SE3Pa8oF6okEb/U3oENxRsPo1rfZoKtB1ZokMPYR5D2JnqUZgp0YFuKWj2estGf/D45RgV6himhOxejNJstcl4SdI7yPOQFbnHtMrU=</X509Certificate> </X509Data> </KeyInfo> </KeyDescriptor> <KeyDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" use="encryption"> <KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#"> <X509Data xmlns="http://www.w3.org/2000/09/xmldsig#"> <X509Certificate xmlns="http://www.w3.org/2000/09/xmldsig#">MIIFjDCCA3SgAwIBAgIUCeAwhCwAOr8GKURZEYhJskUIjTEwDQYJKoZIhvcNAQELBQAwZjELMAkGA1UEBhMCVVMxEjAQBgNVBAcMCVBhbG8gQWx0bzETMBEGA1UECgwKTWF0dGVybW9zdDEPMA0GA1UECwwGRGV2T3BzMR0wGwYDVQQDDBRtYXR0ZXJtb3N0LmxvY2FsaG9zdDAeFw0yMDA4MTkxNDE0MjVaFw0zMDA4MTcxNDE0MjVaMGYxCzAJBgNVBAYTAlVTMRIwEAYDVQQHDAlQYWxvIEFsdG8xEzARBgNVBAoMCk1hdHRlcm1vc3QxDzANBgNVBAsMBkRldk9wczEdMBsGA1UEAwwUbWF0dGVybW9zdC5sb2NhbGhvc3QwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQDRqCWOJFGO5pZE6DPk068roQ/FDUSAx5aTQ1YAgysV/5zRuRXtOh/abPjonFRzvv8FzYDQbfi88jP9JlxjIY6C8D1v4DGscknKkoYkR6XXD3G2QWD0wlz+JZ8ODC+cKvMeEj4fwQ6CHu7EaGGRb7bgQyQxhcjnmg7NcYb0xwVbneju4ErFx4hLL69KZHdwMLDUcQ8hvPzN38KqOUs2gxcPg6PagVDYT2VvcthyOk1pyesoh8m+pvp23zwg5F1KPdza4OU8gf4YH9IPoBmdS2UZVAgughvvrlQnPvoHqCx6ILy+tNwcFesVJGgRI2fWyMwbXOSGVAaxetkt32Qkv96RG+w29yMDZM+bBE475z45GPmzQuNzUm/uY78MdgZ5CNTnUiifflD1Hvtc89KpJbPxJ6d1vwUedgVrRgiPVNTErYAyrX94HEL5J2/82SRhK19twYYtwGxps8fknN5Hit7n8nBU+iIF2JxShwyGhdPuT3T9hOGilxleTBJSOA6UkYJ0jSAk/cEupx1FrM0UjK6tljIuJqAZdzwiCOTlwgwyiOZq2Sbh21moitJNjsrQolopNX8hvPna2Z+mjlD8FKbs1ByqCLrxsQwFoIUaK5mIrGec3TWnSeyNnmyBwtb5y3qgNDgJMgmf69QDVdz8bOZLP9IK2Z66UvnFLhGnMs/QBQIDAQABozIwMDASBgNVHRMBAf8ECDAGAQH/AgEAMBoGA1UdEQQTMBGCCWxvY2FsaG9zdIcEfwAAATANBgkqhkiG9w0BAQsFAAOCAgEAiWlqVfSO093GUBOCEzlP7d5HRh3coZtMl/HPf0/evMfnzrqoDpPmMmdWb24tlVhVsE8l1ojr4b3WeHICkOyVGx5/SW1mDpbcZVbza3xwuwVQFvIAx49smZv4KdUM5lAGKTqVYxDogl7eZX+g9jwKMwxTXAOI3DJEjtg0inTk765crqkpPm6vGPKZy00Y5ydYXIePh+LjDLkPYk++1/KEJGGMBMcwywjhMQr3GAd9+uLXq6gO7Qf04HU0lkvHOSXIPfHkBc9+jbsPx8//WvLrYyK5w2UMawkWNYjWFy5XECljBsoFGPXsB6iSRzV/4X3AMIQyZozVpCgIh0YL+RSEjpx8HvDZXb6lCOSJigu5uUViRuExYc5a2RHqH3Vic4up98272B/5peqY/zilpL3bbBZHdJkEVxlzNPExkdwAhE6e/f4uMP3VI86XRysTP/FBb+0MCyeu2d6nikh/RFk/zRiXfyMWWVbUivnkc9jGkgbOshc1UE/G3xscBU0Wr36EJh42G95Vu15OicGOB2ULgy9hSapt3svYEYenVFG7ZEINePGtVwETGEDz6rCuXiteomfO1SE3Pa8oF6okEb/U3oENxRsPo1rfZoKtB1ZokMPYR5D2JnqUZgp0YFuKWj2estGf/D45RgV6himhOxejNJstcl4SdI7yPOQFbnHtMrU=</X509Certificate> </X509Data> </KeyInfo> <EncryptionMethod Algorithm="http://www.w3.org/2009/xmlenc11#aes128-gcm"> <DigestMethod></DigestMethod> </EncryptionMethod> <EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc"> <DigestMethod></DigestMethod> </EncryptionMethod> <EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc"> <DigestMethod></DigestMethod> </EncryptionMethod> </KeyDescriptor> <AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="http://localhost:8000/login/sso/saml" index="1"></AssertionConsumerService> </SPSSODescriptor> </EntityDescriptor>As suspected @dan the Format is an empty string
<samlp:NameIDPolicy AllowCreate="true" Format="" />I would want to check with mattermost if there is a way of setting the format in a way. Thanks a lot -
Ok, this is helpful.
<samlp:NameIDPolicy AllowCreate="true" Format="" />Next step is to identify if this is a valid value according to SAML, if so we need to handle it. Or if it is not, you'll have to see what you can do in your Mattermost config to ensure a value is sent, or omitted.
We can do a little investigation on our end to see if the SAML spec says that
Format=""is an acceptable value. My previous understanding was thatNameIDPolicyis optional, and if there is not a requested format, the element should be omitted from the document. -
Here's part of section 3.4.1.1 of the SAML 2.0 Core spec:
Format [Optional]
Specifies the URI reference corresponding to a name identifier format defined in this or another specification (see Section 8.3 for examples). The additional value ofurn:oasis:names:tc:SAML:2.0:nameid-format:encryptedis defined specifically for use within this attribute to indicate a request that the resulting identifier be encryptedSection 8.3 doesn't show any examples of blank identifiers, and just before section 3.4.1.2, the type of format is specified:
<attribute name="Format" type="anyURI" use="optional"/>I don't believe an empty string is a valid URI.
I'd probably file an issue with Mattermark and see what they think, if you haven't yet, @misterjoj .
-
I have opened a ticket on Mattermost and provided them with the URL to this post. They are looking into it. Thanks for the insights. Will update if there is a way around this.
Best Regards,
-
Great! Let us know what you find out.
-
@misterjoj do you mind dropping a link (if you filed an issue in a public issue list)? I'd like to follow along if possible.
-
Hello Guys,
Finally here is the feedback from Mattermost:
So one issue that we found is that this incorrect format of the NameIDPolicy is actually part of the go-saml library we're using to create the assertions.
There's been a PR opened in the repository of this library that is supposed to fix this, however we do not necessarily know when this will get merged.
For that reason we'll merge the fix into a fork we maintain until the PR is merged upstream.Now I have used the old saml implementation with dependency on xmlsec. I hit a blocker there as well and I figure out that there is a step that I can't seem to get around to. If you follow the documentation for okta https://docs.mattermost.com/deployment/sso-saml-okta.html the step 8: Set Assertion Encryption as Encrypted and upload the Service Provider Public Certificate you generated in step 2 to the Encryption Certificate
Same for oneLogin https://docs.mattermost.com/deployment/sso-saml-onelogin.html section 2. b. Paste the Public key that you generated earlier into the SAML Encryption field.I haven't seem a way to do SAML assertion encryption with fusionauth. Is there a way to do that? With that I am sure I can complete the setup. Thanks in advance
-
Hiya,
I'm glad you figured this out.
Here's a SAML example where a signing key was created: https://fusionauth.io/docs/v1/tech/samlv2/zendesk
You can either generate one in the "SAML" tab of your application when you are setting it up, or you can go to "Key Master" and create or import one. You can see the private and public key by going to "Settings" and then "Key Master".
Then, in the "SAML" tab of your application you can set the "Signing key" to the value of the key you created.
Hope that helps.
-
Hey @dan ,
Thanks for your reply. At first, I also thought the certificate being referred to is the same as the one generated but I believe the scenarios are different.
It looks to me that 2 certificates are being used.
1- Service Provider generates a certificate that is imported into the Identity provider for Assertion Encryption. (Step 8 of the okta example )
2 The Identity provider generated certificate that is imported in the service provider (Step 12 of the otka example)So in FusionAuth SAML section I only know or see Identity provider public certificate being configured. Nothing pops out to me on where to put the service provider certificate along side with its own Identity provided generated one.
I don't know if you get my point.
Thanks
-
Ah, thanks. I didn't catch that it was happening both ways.
Looks like you can turn off the assertion encryption, though it is not recommended for production: https://docs.mattermost.com/administration/config-settings.html . I'd probably try turning it off just to see if you can get it to work end to end. Then you can make the call if that is a security setting you're willing to live with.
The bad news is that FusionAuth doesn't support "Service Provider Public Certificates" for assertion encryption at this time. Please feel free to file an issue: https://github.com/fusionauth/fusionauth-issues/issues requesting such support (I didn't see anything previously filed).
Here's guidance regarding our roadmap: https://fusionauth.io/community/forum/topic/172/the-fusionauth-roadmap
-
thanks , I will do just that
Best Regards,