JWT token with roles
-
Re: Implementing a Role-Based Access System for Authorization
Hey everyone.
We have a question about JWTs and roles;
Our application is an admin panel which uses FusionAuth's Login API for authentication, and every other request will hit our own back-end;
We need to protect endpoints by using the roles that are decoded from the token, and there is none;
So I ask you guys:
-
Is it wrong to put it like that?
-
If not, how should we include the roles inside the token, knowing that on the docs, the claim "roles" is reserved? (https://fusionauth.io/docs/v1/tech/lambdas/jwt-populate)
Thank you!
-
-
Is it wrong to put it like that?
I think you're on the right track.
If not, how should we include the roles inside the token, knowing that on the docs, the claim "roles" is reserved? (https://fusionauth.io/docs/v1/tech/lambdas/jwt-populate)
Have you added any roles to your FusionAuth application? Those roles should be put into the JWT automatically.
-
Hey Dan!
Have you added any roles to your FusionAuth application? Those roles should be put into the JWT automatically.
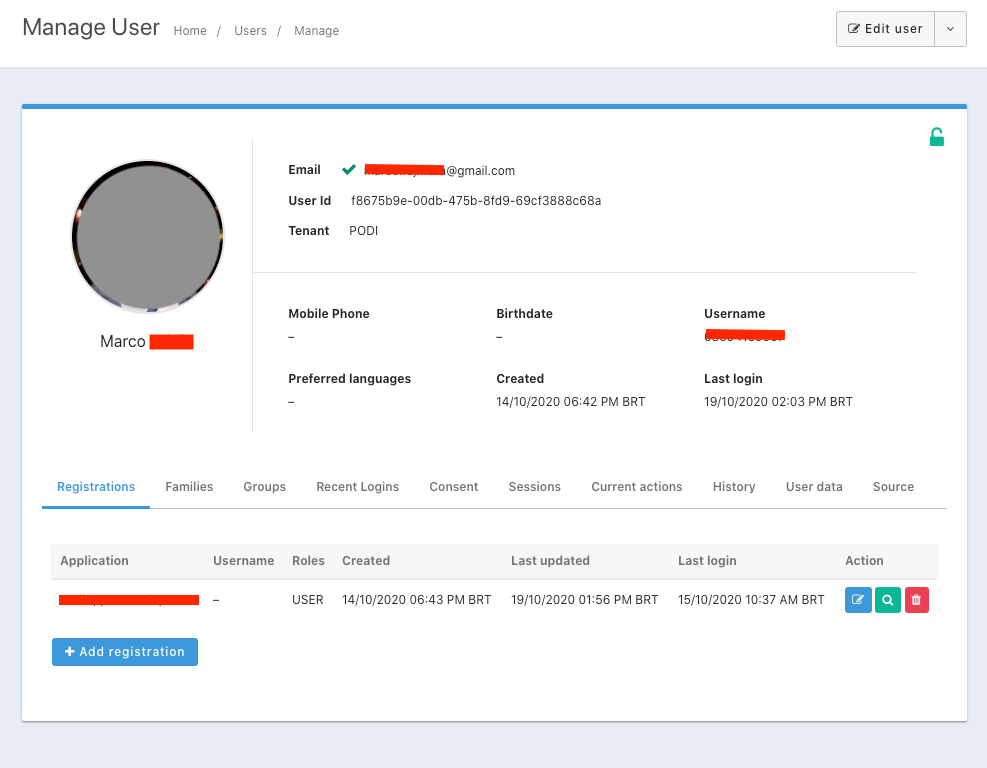
Yes, we added one role on the application (USER), but still, there is no "roles" claim inside the token.
Any advice on where to look Dan?
Thanks again.
-
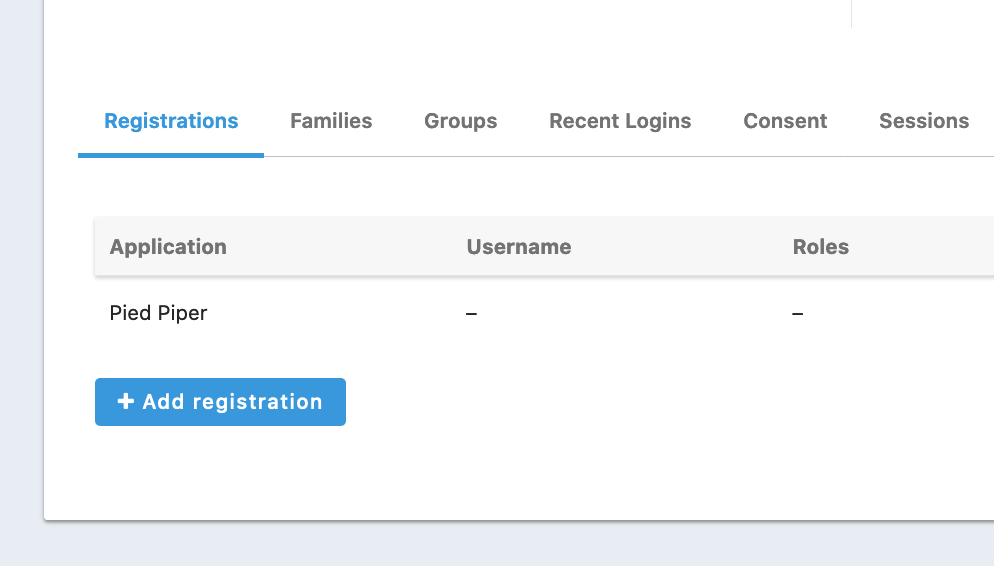
Is the user registered to the application within FusionAuth?
Go to the user details page and look at the 'registrations' tab.
-
-
Hmmm. A few more questions.
And you are logging into that application (with a client_id)? Are you logging the user in with OAuth and the hosted login pages (that is within FusionAuth's ui you manage with themes) or with the login API? What version of FusionAuth are you using?
-
Hey Dan!
So let me answer one by one:
- I am logging the user using Facebook, Google and Apple with FusionAuth's UI;
- The version we are using is 1.19.8;
-
Hi Marco,
I'm unable to replicate using Google's login with google button (this is with 1.19.8).
Here's what my JWT looks like:
{ "aud": "ffbbef97-a2c0-49eb-990d-bd6e96acf2f9", "exp": 1603227230, "iat": 1603223630, "iss": "acme.com", "sub": "8c5a7890-3deb-4fc7-a5d9-29cf396847c5", "jti": "f091312c-47ce-4125-a9a0-a2d2e7279ce3", "authenticationType": "GOOGLE", "email": "<email address>", "email_verified": true, "applicationId": "ffbbef97-a2c0-49eb-990d-bd6e96acf2f9", "roles": [ "USER" ] }I'm not quite understanding what is going on, because my JWT doesn't look like yours. Typically if a user is registered for an application you'll receive an
audclaim with the application id in it (more here on that).I also note that the JWT you provide shows you are logging in with the
PASSWORDmethod, not google, facebook or apple.Maybe it makes sense for you to lay out, step by step, the auth process a user goes through where they don't get the roles claim? Because I'm not sure what's going on.
-
@dan said in JWT token with roles:
"applicationId": "ffbbef97-a2c0-49eb-990d-bd6e96acf2f9",
"roles": [
"USER"
]Hey Dan!
Now we got it working.
For reference, we were not passing applicationId inside the request body, that's why the roles were not included in the token.
Thanks again for the time Dan!