@johnathon like you see on the capture i am using the login screen.
Posts made by llorach.pablo
-
RE: User not registered still logged inposted in General Discussion
-
RE: User not registered still logged inposted in General Discussion
i do not want to see that image, I want the user to crash on the login screen if he is not registered to the application and receive a generic error (if I can write the error message is fine for me, but if it says the password is wrong is ok for me).
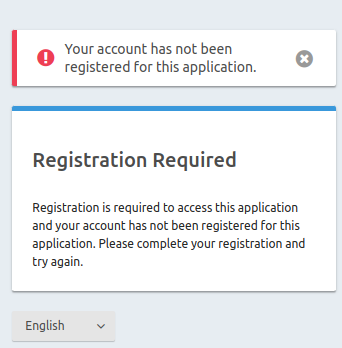 file:///home/garsiv/Pictures/Screenshots/Screenshot%20from%202023-02-03%2010-52-11.png
file:///home/garsiv/Pictures/Screenshots/Screenshot%20from%202023-02-03%2010-52-11.png -
RE: Registration Required persistentposted in Q&A
@dan And how do you add a button? Do you have an example? if I want to delete the token and make a forward redirect the user to another page (the login, for example).
-
User not registered still logged inposted in General Discussion
i have a structure of applications and tenants based on registrations, so users must be registered on the application, if he is not registered he will be logged in, but won't be granted access to the Application, but i dont want that, i want that fusionauth reject the user in the login screen like when the password is wrong?
Is that possible? -
.NET Core 5 is giving a 401 errorposted in General Discussion
i have an API in net core 5 and a front app in next. Front app is configured with nextauth library and is working fine. The problem is with the API, that is not recognizing the JWT and is giving and unauthorized error to the front.
this is mi Startup ConfigureServices method:
services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme) .AddJwtBearer(options => { if (_environment.IsDevelopment()) { var opts = _configuration.GetSection("FusionAuth"); options.Authority = opts["Authority"]; options.Audience = opts["ClientId"]; }else if (_environment.IsProduction()) { string authority = Environment.GetEnvironmentVariable("FUSIONAUTH_AUTHORITY"); string clientId = Environment.GetEnvironmentVariable("FUSIONAUTH_CLIENT_ID"); options.Authority = authority; options.Audience = clientId; } options.RequireHttpsMetadata = false; options.Events = new JwtBearerEvents { OnMessageReceived = context => { context.Token = context.HttpContext.Session.GetString(SessionKeys.Token); return Task.CompletedTask; }, }; }) .AddOpenIdConnect("oidc", options => { if (_environment.IsDevelopment()) { var opts = _configuration.GetSection("FusionAuth"); options.Authority = opts["Authority"]; options.ClientId = opts["ClientId"]; options.ClientSecret = opts["ClientSecret"]; }else if (_environment.IsProduction()) { string authority = Environment.GetEnvironmentVariable("FUSIONAUTH_AUTHORITY"); string clientId = Environment.GetEnvironmentVariable("FUSIONAUTH_CLIENT_ID"); string clientSecret = Environment.GetEnvironmentVariable("FUSIONAUTH_CLIENT_SECRET"); options.Authority = authority; options.ClientId = clientId; options.ClientSecret = clientSecret; } options.UsePkce = true; options.ResponseType = "code"; options.RequireHttpsMetadata = false; options.Events = new OpenIdConnectEvents { OnMessageReceived = context => { context.Token = context.HttpContext.Session.GetString(SessionKeys.Token); return Task.CompletedTask; }, }; }); services.AddAuthorization(); services.AddDistributedMemoryCache(); services.AddSession(options => { options.IdleTimeout = TimeSpan.FromMinutes(60 * 24); }); services.AddHttpClient();