Hi!
I was wondering exactly the same, but unlike @yb98 decoding the content of fusionauth.sso (Base64) does not match my refresh token (like, not at all).
Is there a trick (special encoding or something)?
Thanks 
Hi!
I was wondering exactly the same, but unlike @yb98 decoding the content of fusionauth.sso (Base64) does not match my refresh token (like, not at all).
Is there a trick (special encoding or something)?
Thanks 
Hello!
If refresh tokens have "One Time Use" enabled, and if a second usage attempt is detected on a refresh token:
Is the whole refresh tokens family invalidated so that all refresh token generated from a stolen one become useless?
Thank you!
Hello @dan,
Thanks a lot for your fast reaction!
I'm using FusionAuth 1.24.0, and yes there is a reverse proxy to reach it.
It was the same with several browsers.
Thank you, the solution was what you suggested 
We manually added the header "Access-Control-Allow-Origin": window.location.origin in our call to /oauth2/token, and it worked 
Hi!
I get the following error when trying to sign in:
Access to XMLHttpRequest at ... has been blocked by CORS policy: No ‘Access-Control-Allow-Origin’ header is present on the requested resource.
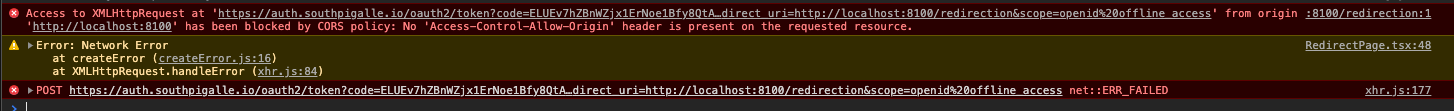
Here is a screenshot of the Network tab:
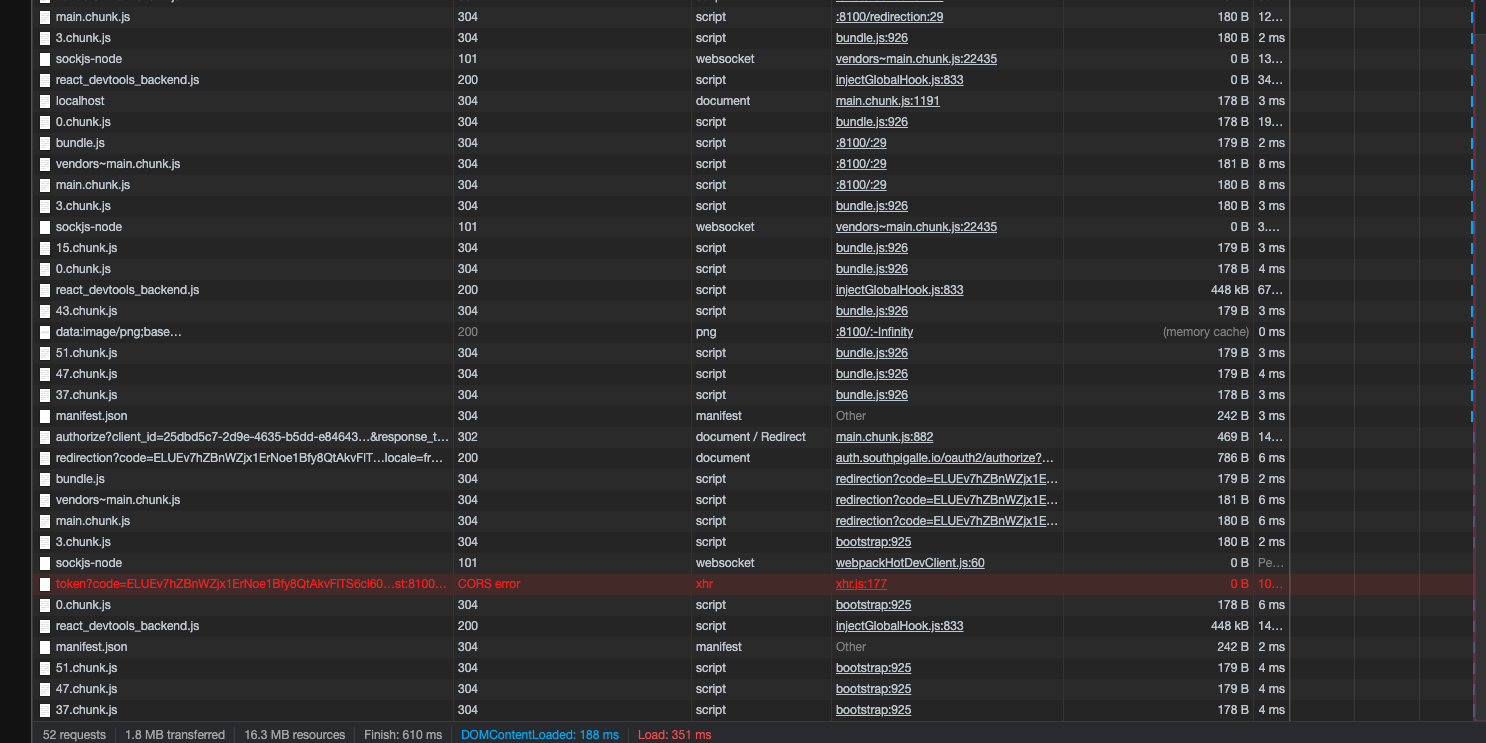
The problem is the same with different application URLs:
 When I use Postman, there is no CORS issue and this POST request to
When I use Postman, there is no CORS issue and this POST request to /oauth2/token works and I get valid Access and ID tokens.
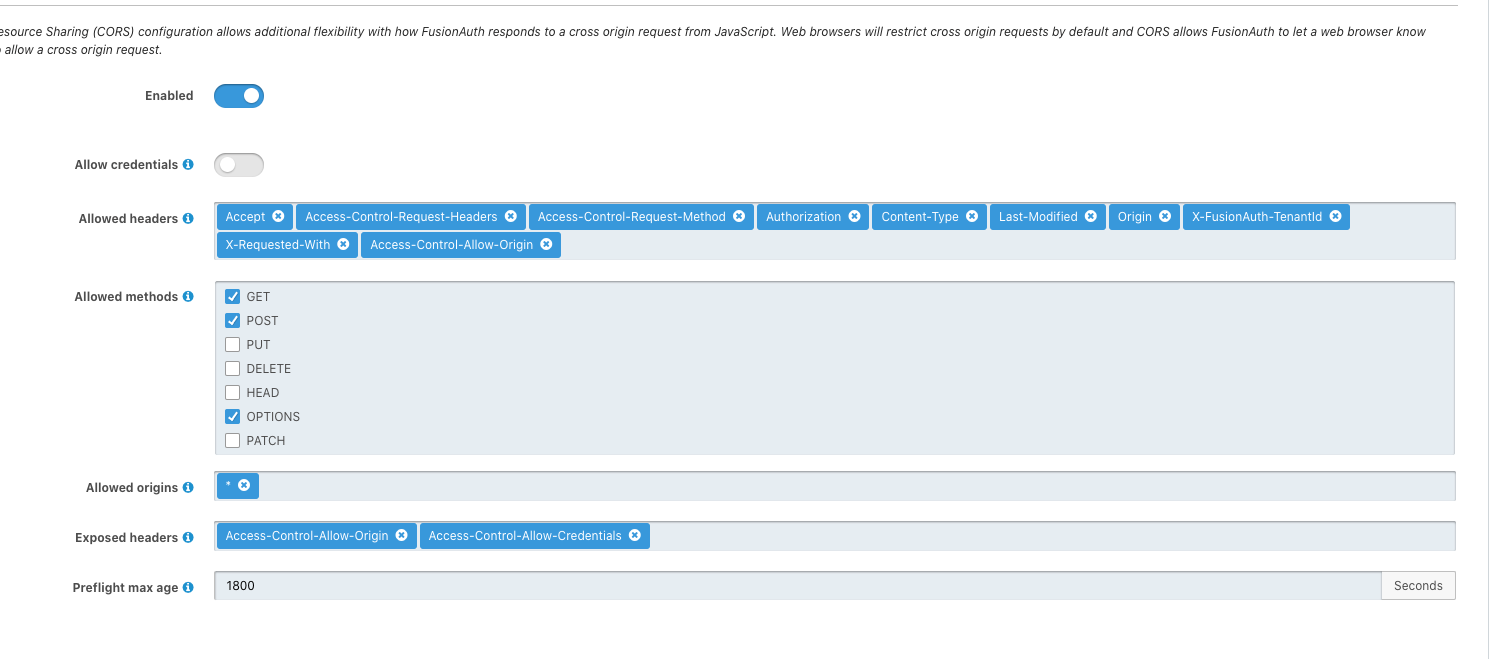
Thanks a lot  !
!
We are unable to start a SAML v2 Login Request (as explained here).
Our version of FusionAuth is 1.20.0.
The exception bellow is throw:
2020-11-02T09:12:47.670831893Z 2020-11-02 9:12:47.670 AM ERROR io.fusionauth.app.primeframework.error.ExceptionExceptionHandler - An unhandled exception was thrown
2020-11-02T09:12:47.670862293Z java.lang.NullPointerException: null
2020-11-02T09:12:47.670866593Z at io.fusionauth.api.service.authentication.SAMLv2IdentityProviderAuthenticationService.start(SAMLv2IdentityProviderAuthenticationService.java:176)
2020-11-02T09:12:47.670870593Z at io.fusionauth.app.action.api.identityProvider.StartAction.post(StartAction.java:61)
Note: The configuration of our Application and Identity provider in FusionAuth looks good as we are able to sign in graphically (with the SSO button).
Thank you!