3rd Party Authentication
-
@it-contracts I apologize for misunderstanding your initial question. You and @kash are correct in that by using FusionAuth, it will appear to be one call from your perspective. However, in the background, FusionAuth will still need to make the same amount of calls to the the access token. And another nice thing about using FusionAuth is that you will be able to add other identity providers in the same way.
-
@kash said in 3rd Party Authentication:
You're definitely right. FusionAuth can handle all 3 steps and should take less calls.
You can add a google identity provider under 'Identity Providers' using a oauth client id and secret.
Thank kash and Mark for your replies. I really appreciate them as I feel a bit lost.

kash I did add the Google identity provider using Google Client Id and Secret, however, I'm seeing someone calling my callback program/servlet after step 1. Where Google return the code. The code is what one uses to obtain the Authorization Token. And then the Authorization Token is used to retrieve the User Info.
Where Google return the code. The code is what one uses to obtain the Authorization Token. And then the Authorization Token is used to retrieve the User Info.
So, it seems to me that I'm missing something. How do I invoke the flow so that FusionAuth handles all 3 calls and just returns to me the JSON with the User Info?I initiate the flow by using the URL for my application in my browser which takes me to the FusionAuth login screen with the button that says Login with Google. Once I proceed and login my callback routine is called with the code as I mentioned above and I'm left to try to complete the flow on my own.

TIA
Rudy -
Don't worry
 you almost got it.
you almost got it.The callback is the first step in the right direction. We need the code parameter from that callback to obtain the authorization token like you mentioned.
Do you mind posting a little more about what callback program/servlet you're using? It shouldn't be too many steps after that.
-
@kash Thank you kash for your reply once more. I'm not sure I understand what you are asking for.
 But would be happy to provide whatever details you need.
But would be happy to provide whatever details you need.Just to reiterate. I have initially completed a project that uses Google and other 3rd party authenticators directly. And it works perfectly. However, now my company wants to use FusionAuth. So I have to start from the beginning. Yay me!
The previous process as I mentioned called Google 3 times. First call was to get the code. Google called the "callback" servlet with the code which I used to obtain the Authorization Token. I then proceeded to call Google for the 3rd time with the Authorization Token to get the user info. This all works.
I thought that FusionAuth would perform all 3 steps for me. Meaning I would call it once and it would return to me the User Info. However, when I call FusionAuth, I see that my callback is called after step 1, which is where Google returns the code. And I have to call Google myself for calls 2 and 3. Which is very challenging since the callback (i.e. redirect_uri parameter must be identical between calls 1 and 2).
At the moment, my callback servlet simply calls Google to obtain the Authentication Token based on the code that was returned. Initially, I had code in my callback servlet to parse the User response that I was hoping to get back from FusionAuth. Alas, that code had to be commented out.
 As I'm still not sure how to call FusionAuth to get it to perform all 3 steps for me.
As I'm still not sure how to call FusionAuth to get it to perform all 3 steps for me.Meaning what URL should I be using to get FusionAuth to perform all 3 steps for me?
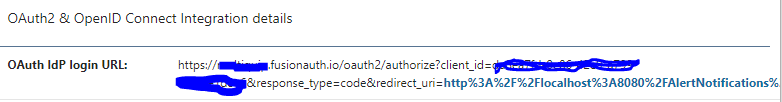
In my previous reply I posted the image of the URL I'm using now.
TIA
Rudy -
Alrighty let's try this. We'll maybe add a few more calls but we'll get it working
First, let's set up the scope for your google identity provider. It should be under the identity provider tab in the google section that you configured.
-
Also do you have fusionAuth running on port 9011?
-
@kash said in 3rd Party Authentication:
Also do you have fusionAuth running on port 9011?
Sorry, forgot to mention. We purchased the Cloud package. We are in the clouds.
 So nothing local.
So nothing local. -
@kash said in 3rd Party Authentication:
> Alrighty let's try this. We'll maybe add a few more calls but we'll get it workingI love your optimism.
 I'm onboard.
I'm onboard. 
> First, let's set up the scope for your google identity provider. It should be under the identity provider tab in the google section that you configured.
This is what I had the scope set to:
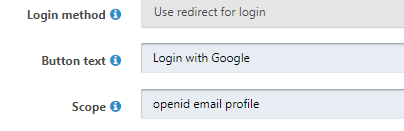
-
@it-contracts, which license did you purchase? If you selected the Essentials Plan you should have access to the Account Portal and may receive support directly through email if this is time sensitive.
-
@it-contracts Can you please share the OAuth settings you have for your application? In the Fusion Auth Admin UI select
Applications. Select Edit or view for your application. Share the OAuth and JWT settings. Be sure to remove any sensitive information before posting here. -
@mark-robustelli said in 3rd Party Authentication:
@it-contracts, which license did you purchase? If you selected the Essentials Plan you should have access to the Account Portal and may receive support directly through email if this is time sensitive.
In the Dashboard it says: Current plan Starter
Seems like we are paying $350 per monthThis is what it says in the Support tab:
*As a valued customer of FusionAuth Cloud hosting, you can open support tickets for the following items:Outages
Network issues
Assistance with upgrades
If you need other support including engineering support, you will need to purchase a paid Plan that includes support.*Am I the first person to attempt this? I find that a bit surprisisng.

-
@mark-robustelli said in 3rd Party Authentication:
@it-contracts Can you please share the OAuth settings you have for your application? In the Fusion Auth Admin UI select
Applications. Select Edit or view for your application. Share the OAuth and JWT settings. Be sure to remove any sensitive information before posting here.I did not make any settings in JWT, so there is nothig there.
In the OAUTH section here's what I have:
- Client Id - Id generated by fusionAuth.
- Client secret - Secret generated by FusionAuth.
- Client Authentication - Set to Required
- PKCE - Set to Not Required.
- Generate refresh tokens - Checked
- Debug enabled - Checked (No idea if this does anything in the Cloud configuration).
- URL validation - Set to Exact Match
- Authorized redirect URLs -http://localhost:8080/MyAppName/FusionAuthLogin
- Authorized request origin URLs - Not Set
- Logout URL - http://localhost:8080/MyAppName/FusionAuthLogout
- Logout behavior - Set To All applications
- Enabled grants - Checked "Authorization Code" and "Refresh Token"
- Require Registration - Checked
That's it.
Thank you Mark
Rudy