Restrict issuer when using "External JWT" identity provider
-
The "External JWT" identity provider, allows us to authenticate against an application using an external JWT. As far as I can see, the only way to allow/disallow external JWTs on this "External JWT" identity provider is whether or not the
kidis known in the Key Master configuration.I can't seem to find a way to restrict a certain external issuer to a certain "External JWT" identity provider which is problematic if we have multiple applications with different relying-parties.
For example:
"External JWT IdP A" is linked to "Application A"
"External JWT IdP B" is linked to "Application B"
on "Application A" we want to allow external JWTs of Issuer 1, withkidX.
on "Application B" we want to allow external JWTs of Issuer 2, withkidY.But since both
kids are known in Key Master, both External JWT IdPs will accept any JWT, doesn't matter if it'skidX or Y. Is there a way to restrict this (f.e. link specific signing key to specific external IdP or validate theissfield in the external JWT)? As currently this is a major security issue for us. -
Hmmm.
One option to explore would be using a custom lambda for each IdP, and setting an custom value (
iss_unexpected) on the user/registration if the issuer is not what you expect. Then you could pull the value from the user/registration and set it in the JWT issued by FusionAuth, and have your application check it.I don't see any way to accomplish this using the standard options.
-
@dan thanks for your answer.
I believe it should be possible to add this restriction in FusionAuth by configuration, as it presents a security issue for integrations using more than one External JWT. And as FusionAuth is multi-tenant, this could seriously go wrong.
What I would like to propose, is that the setting
Default verification keyis changed intoVerification key. If the token contains akid, it must match with what is configured there and the signature must be correct. If the token does not contain akid, the signature must be correct according to the key selected there. Is this the correct place to request such feature?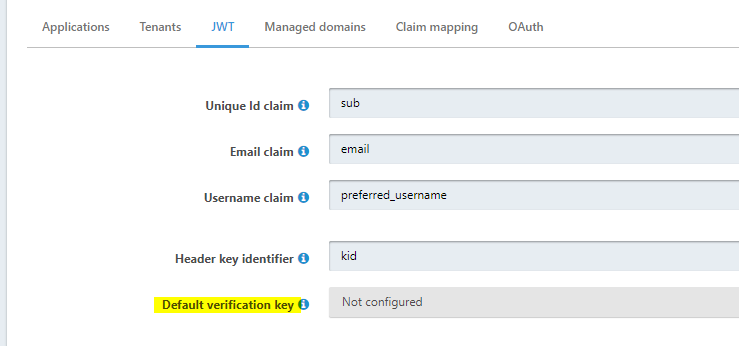
-
Sure, we welcome feature requests from the community! Members can upvote them and we review the upvotes when considering future development.
Here's the GitHub repo to file the issue in: https://github.com/FusionAuth/fusionauth-issues/issues/
Please feel free to reference this forum post and give as many details as you can. This helps us understand the use case.
More about our roadmap process: https://fusionauth.io/docs/operate/roadmap/roadmap