SAML response does not contain role
-
I am using SAML2 with FusionAuth as Idp and my application as SP.
The authentication works fine. However, I need to get roles of the user for role-based authorization, but the SAML response does not contain roles:<?xml version="1.0" encoding="UTF-8" standalone="no"?><ns3:Response xmlns:ns3="urn:oasis:names:tc:SAML:2.0:protocol" xmlns="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:ns2="http://www.w3.org/2000/09/xmldsig#" xmlns:ns4="http://www.w3.org/2001/04/xmlenc#" Destination="http://localhost:8080/login/saml2/sso/fusion-auth" ID="_3c3607f8-4922-4c9f-a652-fae4108d15f7" InResponseTo="ARQ2d0164b-3a50-4272-99c4-460b376c829c" IssueInstant="2022-05-16T05:47:24.402Z" Version="2.0"><Issuer>http://localhost:9011/samlv2/d2274ffe-80d7-cc3b-c232-62804b62747e</Issuer><ns3:Status><ns3:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success"/></ns3:Status><Assertion ID="_9562fc02-26a8-4864-86a7-723dd4f08356" IssueInstant="2022-05-16T05:47:24.403Z" Version="2.0"><Issuer>http://localhost:9011/samlv2/d2274ffe-80d7-cc3b-c232-62804b62747e</Issuer><Signature xmlns="http://www.w3.org/2000/09/xmldsig#"><SignedInfo><CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#WithComments"/><SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256"/><Reference URI="#_9562fc02-26a8-4864-86a7-723dd4f08356"><Transforms><Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/><Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#WithComments"/></Transforms><DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"/><DigestValue>d4PjocF856yQrzYhMJKi+QRDT5/K3s3CdL8tZBRBh5g=</DigestValue></Reference></SignedInfo><SignatureValue>YBSWWZGIo1d4XdoBKppogn+lAFROJTp8zp8R0Wqpeybz7c3OOTlS6F714hA3UzvJbExYreXQBdoXD4/8TiJ2vJ9NjM6niaP6D2WOICsZdVZ9FuOAxEQ1QNmp2iGTuzQUDOnY2ZLS8/VpXTK4nzBwTI1uN7juD8Esmc6TBgAup5bSH+oek29MqZJzKfnDMds+VpyJKMRXY7iRiubcdPEW10zYxiyT5X3B4p43qYX4UGQH5HdhNEgLApDvgmlbGPB5lxKtZziz1TyO+GAsBNECA+TjD7Szow6nUZfLCAgQ+c/Odj5kq/G3MqvI5rpGcqiY1EwLEpYjE56cln3ANFL/2Q==</SignatureValue><KeyInfo><X509Data><X509Certificate>MIICyzCCAbOgAwIBAQIRAL1sztGuOEsWlXU8hmd4W3YwDQYJKoZIhvcNAQELBQAwITEfMB0GA1UEAxMWaHR0cDovL2xvY2FsaG9zdDo5MDExLzAeFw0yMjA1MTIwNjM0MzhaFw0zMjA1MTIwNjM0MzhaMCExHzAdBgNVBAMTFmh0dHA6Ly9sb2NhbGhvc3Q6OTAxMS8wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCsAYEw5OVaZ1H2M9wPWkIYnxqnWgYMJ7uyjc+LJo0fXyG8QTbg6LkqIWHm7dErsoXxK2lw1Wqbr7jYwHCFL1/XBaSo/30IKsu+rukwakaO3ZrMEaZA1n7ITlICom0RrVvOEkKoioa9YzpOELvR6bRR5FHFm2Fe3fWTbW7YQ1WynshZyvSUVLyMaxLAvEDpCTFyquhYi+zdxN8NbEWkam2iRcAicS5NGfoSBfjWstGpgwzlQTcajZ/X5muhsZQo2sfcA7MgkwhwgOdhzJT2/gDXm1NzJYKaRyD7o4Z5VqbiBjpWa1WKvncAxi98+GYmUMw4W2oqiWXlI+YqrWIB+EulAgMBAAEwDQYJKoZIhvcNAQELBQADggEBAKGF1AMQeY0HMmLy3phOJIBs2qugtOohSq4brV1cIXAF3hwG2wqC7XFM5SldSQOY7VSrrtkuTW18ynpdwZIxbKi9Jv2qB7bs9h2bOfOPyrBRhgu5hMlGbZ19wg0YUVZ1kxDmWlqdo3kQC5h8fpzvNRCjoYekcOmCF2LoHcyMcUt/8nXFXTie8uD+4wiOn0RAc9m+fSf5SFPnuBlY/mzgUcaSHanauAc0d9KzfDUhIjp6pU8Rt4ATYzF+olSGIrs7YP8BtROkCoNgFGeJjGoCBEZxHueL7WUFdSQZFZEcLB/MruQ6vn1NMFgN2gyIvx70OufV66q1OoNomKbTn796f8E=</X509Certificate></X509Data></KeyInfo></Signature><Subject><NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">bvbao@gmail.com</NameID><SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"><SubjectConfirmationData InResponseTo="ARQ2d0164b-3a50-4272-99c4-460b376c829c" NotOnOrAfter="2022-05-16T06:47:24.402Z" Recipient="http://localhost:8080/login/saml2/sso/fusion-auth"/></SubjectConfirmation></Subject><Conditions NotBefore="2022-05-16T05:44:24.402Z" NotOnOrAfter="2022-05-16T06:17:24.402Z"><AudienceRestriction><Audience>http://localhost:8080/saml2/service-provider-metadata/fusion-auth</Audience></AudienceRestriction></Conditions><AttributeStatement><Attribute Name="last_name"><AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">Bui</AttributeValue></Attribute><Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname"><AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">Bao</AttributeValue></Attribute><Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname"><AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">Bui</AttributeValue></Attribute><Attribute Name="id"><AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">b7791499-1b49-4b6f-be3a-1799a07fb532</AttributeValue></Attribute><Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"><AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">bvbao@gmail.com</AttributeValue></Attribute><Attribute Name="first_name"><AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">Bao</AttributeValue></Attribute><Attribute Name="email"><AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">bvbao@gmail.com</AttributeValue></Attribute></AttributeStatement><AuthnStatement AuthnInstant="2022-05-16T05:47:24.403Z" SessionIndex="b8d0466a-ef80-4e7d-8fc1-e7b9c848d2bc"><AuthnContext><AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:Password</AuthnContextClassRef></AuthnContext></AuthnStatement></Assertion></ns3:Response>Here is the role assigned to the user
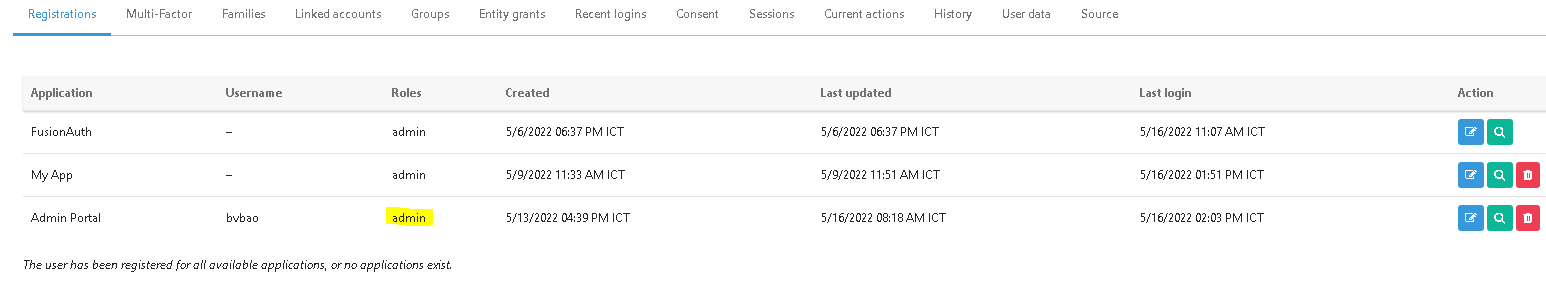
Note: when I use oauth2, I can retrieve the same role
-
I figured out that we can use lambda to set extra parameters into the SAML response:
https://fusionauth.io/docs/v1/tech/lambdas/samlv2-response-populatebut the lambda feature is disabled
Note: I'm using community edition
-
@bvb1992bvb You should be able to assign a lambda to a SAML Identity Provider. This is a community edition feature.
See the
Reconcile Lambdafield on this page: https://fusionauth.io/docs/v1/tech/identity-providers/samlv2/ -
@dan , thanks for your reply, but I think you misunderstood me, I'm using FusionAuth as an identity provider for my application, not for itself.
The one you mentioned is used to add a third-party identity provider.Anyway, Reconcile lambda is used to copy claims from the third-party identity provider, but the identity provider does not return roles, so how can we get it in Reconcile lambda?
The lambda I mentioned is the one in SAML tab in Application Setting:
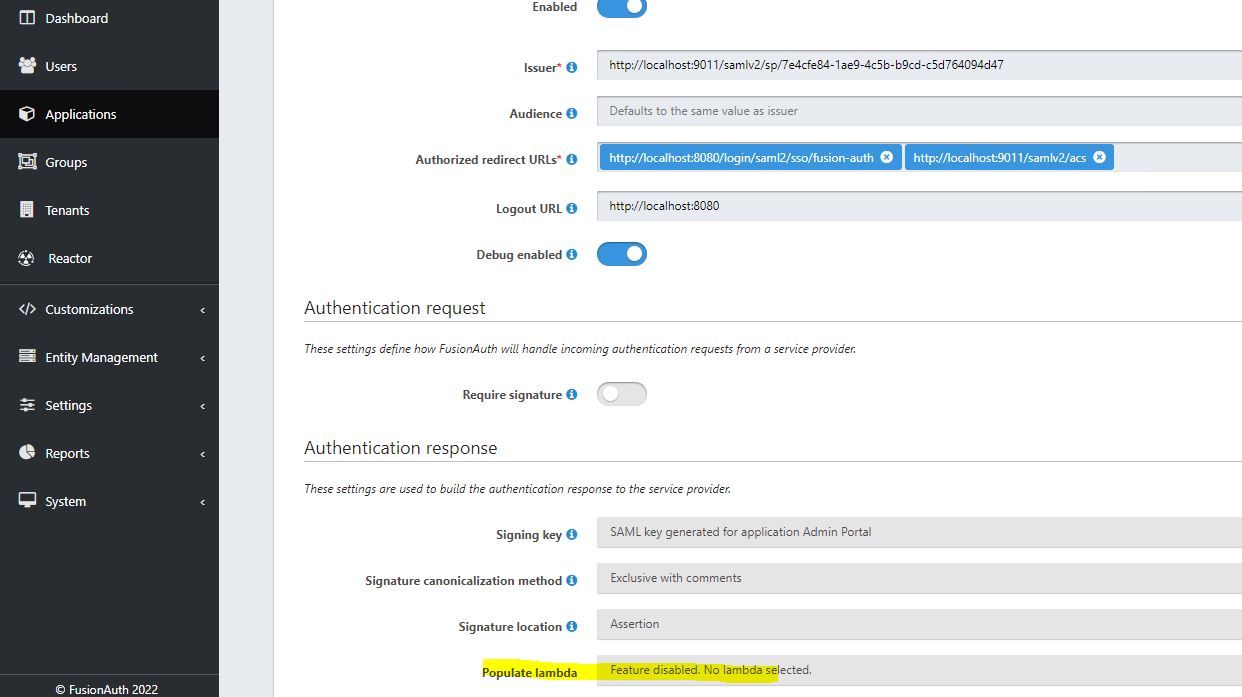
-
@bvb1992bvb Ah, makes sense.
This should still be available. However, you need to create a lambda of the proper type (SAML Populate), which is documented here: https://fusionauth.io/docs/v1/tech/lambdas/samlv2-response-populate
In order to handle complex integrations with SAML service providers, you can specify a lambda to be used by the FusionAuth SAML identity provider. This lambda will be invoked prior to the SAML response being sent back to the service provider.
Does this help?
-
@dan thanks a lot, it works.