@dan It is like that. They use regular /oauth2/register flow to create spam accounts. Even though we deploy WAF, it usually can't catch them as they obey the rate-limits. 
Posts made by atakan
-
RE: How to deal with sign-up spam?posted in Q&A
-
RE: Startup fails after Postgresql db upgradeposted in General Discussion
After disabling the silent mode, the error has changed to table ownership issues. We granted FusionAuth users to table owners db-wide, and it fixed the problem. Why it appeared after the Azure DB upgrade, we don't know yet.
-
Startup fails after Postgresql db upgradeposted in General Discussion
Hi,
We have upgraded our Azure managed DB from 13.x to 16.8, and our Docker system started to give an error during the boot. It looks like FusionAuth is trying to install or migrate to a new version and writes logs as it is creating already existing tables with data in them. We also gave it a try to set the Docker version from 1.51.1 to 1.53.2 with the hope of getting rid of that error, but with no luck.
What would be the reason?
... ... -- Integrations INSERT INTO integrations(data) VALUES ('{}'); -- Initialize the version of the BreachPasswords data set INSERT INTO data_sets (name, last_update_instant) VALUES ('BreachPasswords', 1581476456155); -- FusionAuth Connector INSERT INTO connectors (id, insert_instant, last_update_instant, data, name, type) VALUES ('-intentionally deleted-', (EXTRACT(EPOCH FROM (SELECT NOW() AT TIME ZONE 'UTC'))) * 1000, (EXTRACT(EPOCH FROM (SELECT NOW() AT TIME ZONE 'UTC'))) * 1000, '{}', 'Default', 0); -- Create a FusionAuth connector policy INSERT INTO connectors_tenants (tenants_id, connectors_id, sequence, data) SELECT id, '-intentionally deleted-', 0, '{"domains":["*"]}' FROM tenants; -- Initialize migrations so they don't run on new installs INSERT INTO migrations (name, run_instant) VALUES ('io.fusionauth.api.migration.guice.Migration_1_8_0', 0), ('io.fusionauth.api.migration.guice.Migration_1_9_2', 0), ('io.fusionauth.api.migration.guice.Migration_1_10_0', 0), ('io.fusionauth.api.migration.guice.Migration_1_13_0', 0), ('io.fusionauth.api.migration.guice.Migration_1_15_3', 0), ('io.fusionauth.api.migration.guice.Migration_1_30_0', 0); . Cause: org.postgresql.util.PSQLException: ERROR: relation "email_templates" already exists 2025-06-09 05:43:23.499 PM INFO com.inversoft.maintenance.db.JDBCMaintenanceModeDatabaseService - [AUysOg] Attempting to unlock database to support multi-node configurations 2025-06-09 05:43:23.503 PM INFO com.inversoft.maintenance.db.JDBCMaintenanceModeDatabaseService - [AUysOg] Unlock completed 2025-06-09 05:43:23.887 PM INFO io.fusionauth.api.configuration.DefaultFusionAuthConfiguration - Loading FusionAuth configuration file [/usr/local/fusionauth/config/fusionauth.properties] 2025-06-09 05:43:23.888 PM INFO io.fusionauth.api.configuration.DefaultFusionAuthConfiguration - Set property [fusionauth-app.url] set to [https://login] using configured value. 2025-06-09 05:43:23.889 PM INFO com.inversoft.configuration.BasePropertiesFileInversoftConfiguration - - Overriding default value of property [database.mysql.enforce-utf8mb4] with value [true] - Overriding default value of property [FUSIONAUTH_APP_RUNTIME_MODE] with value [production] - Overriding default value of property [SEARCH_TYPE] with value [database]
-
Login with Twitter fails due to a backend error.posted in General Discussion
We're having a problem implementing Twitter as an alternate identity provider on FusionAuth 1.36.4 (docker)
Login with Twitter button appears on the login page as expected. However it immediately fails when we click on it, with displaying a white page.
Fusion Docker container logs an error during this time:
fusionauth_1 | 2022-05-18 9:51:56.359 PM ERROR org.primeframework.mvc.servlet.PrimeFilter - Error encountered fusionauth_1 | org.primeframework.mvc.PrimeException: Missing result for action class [class io.fusionauth.app.action.oauth1.RequestTokenAction] URI [/oauth1/request-token] and result code [unauthenticated] fusionauth_1 | at org.primeframework.mvc.action.result.AbstractForwardResult.locateDefault(AbstractForwardResult.java:161) fusionauth_1 | at org.primeframework.mvc.action.result.AbstractForwardResult.buildFullyQualifiedPath(AbstractForwardResult.java:122) fusionauth_1 | at org.primeframework.mvc.action.result.AbstractForwardResult.execute(AbstractForwardResult.java:92) fusionauth_1 | at org.primeframework.mvc.action.result.DefaultResultInvocationWorkflow.perform(DefaultResultInvocationWorkflow.java:108) fusionauth_1 | at org.primeframework.mvc.workflow.SubWorkflowChain.continueWorkflow(SubWorkflowChain.java:51) fusionauth_1 | at org.primeframework.mvc.message.DefaultMessageWorkflow.perform(DefaultMessageWorkflow.java:44) fusionauth_1 | at org.primeframework.mvc.workflow.SubWorkflowChain.continueWorkflow(SubWorkflowChain.java:51) fusionauth_1 | at org.primeframework.mvc.scope.DefaultScopeStorageWorkflow.perform(DefaultScopeStorageWorkflow.java:62) fusionauth_1 | at org.primeframework.mvc.workflow.SubWorkflowChain.continueWorkflow(SubWorkflowChain.java:51) fusionauth_1 | at org.primeframework.mvc.workflow.DefaultErrorWorkflow.perform(DefaultErrorWorkflow.java:46) fusionauth_1 | at org.primeframework.mvc.workflow.SubWorkflowChain.continueWorkflow(SubWorkflowChain.java:51) fusionauth_1 | at io.fusionauth.app.primeframework.FusionAuthMVCWorkflow.perform(FusionAuthMVCWorkflow.java:91) fusionauth_1 | at org.primeframework.mvc.workflow.DefaultWorkflowChain.continueWorkflow(DefaultWorkflowChain.java:44) fusionauth_1 | at org.primeframework.mvc.servlet.FilterWorkflowChain.continueWorkflow(FilterWorkflowChain.java:50) fusionauth_1 | at org.primeframework.mvc.servlet.PrimeFilter.doFilter(PrimeFilter.java:78) fusionauth_1 | at com.inversoft.maintenance.servlet.MaintenanceModePrimeFilter.doFilter(MaintenanceModePrimeFilter.java:63) fusionauth_1 | at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) fusionauth_1 | at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) fusionauth_1 | at com.inversoft.servlet.UTF8Filter.doFilter(UTF8Filter.java:27) fusionauth_1 | at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) fusionauth_1 | at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) fusionauth_1 | at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:197) fusionauth_1 | at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:97) fusionauth_1 | at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:543) fusionauth_1 | at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:135) fusionauth_1 | at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:81) fusionauth_1 | at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:78) fusionauth_1 | at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:367) fusionauth_1 | at org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:639) fusionauth_1 | at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) fusionauth_1 | at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:881) fusionauth_1 | at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1647) fusionauth_1 | at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) fusionauth_1 | at org.apache.tomcat.util.threads.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1191) fusionauth_1 | at org.apache.tomcat.util.threads.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:659) fusionauth_1 | at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) fusionauth_1 | at java.base/java.lang.Thread.run(Thread.java:833)The URL is missing a
state.client_id, but I'm not sure if it is relevant./oauth1/request-token?state.client_id=null&state.state=Y2.........What would be the reason?
Thank you
A. -
How to use FusionAuth JWT token and claims with Hasura GraphQL to authenticate GraphQL requestsposted in Q&A
Re: Gatsby + Hasura + FusionAuth + KintoHub (My Dream Stack)
There are several aspects you need to think about this topic. The first thing requires us to make our setup correct and authenticate GraphQL requests. The second part requires figuring out how to use refresh JWT tokens to continue operation without breaking something.
This post covers the first part: The Setup and authenticating the requests
1 - Add Hasura custom claims in the JWT
- Create a Lambda function on FusionAuth to add Hasura claims to the tokens you issued. It's pretty much covered on this GitHub issue
- To do that, go to https://fusionauth:9011/admin/lambda/
- Add a new Lambda function with a name you can easily recognize later like "Populate - Hasura GraphQL Custom JWT Claims"
- Leave ID empty, as you should always do

- Select JWT Populate as the type
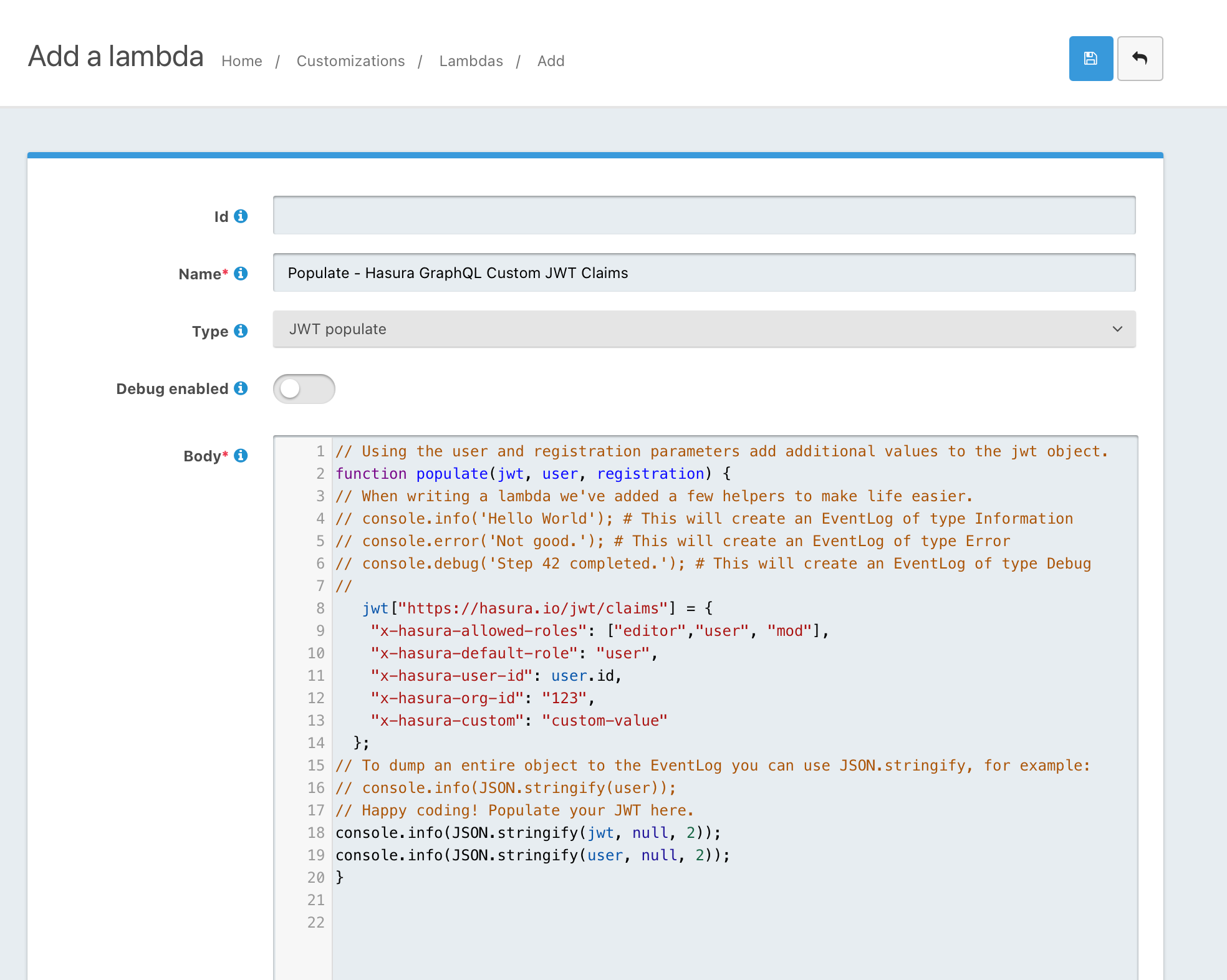
- Add @robotdan's code in the code area
// Using the user and registration parameters add additional values to the jwt object. function populate(jwt, user, registration) { // When writing a lambda we've added a few helpers to make life easier. // console.info('Hello World'); # This will create an EventLog of type Information // console.error('Not good.'); # This will create an EventLog of type Error // console.debug('Step 42 completed.'); # This will create an EventLog of type Debug // jwt["https://hasura.io/jwt/claims"] = { "x-hasura-allowed-roles": ["editor","user", "some-other-role"], "x-hasura-default-role": "user", "x-hasura-user-id": user.id, "x-hasura-org-id": "123", "x-hasura-custom": "custom-value" }; // To dump an entire object to the EventLog you can use JSON.stringify, for example: // console.info(JSON.stringify(user)); // Happy coding! Populate your JWT here. console.info(JSON.stringify(jwt, null, 2)); console.info(JSON.stringify(user, null, 2)); }- Roles are used in Step #5 below. You'll have to figure it out later by yourself depending on your needs
- Save your function
2- Tell your FusionAuth app to use the lambda
- Find your FusionAuth app here https://fusionauth:9011/admin/application/ and click edit.
- Edit your app
- Click on the JWT tab
- Enable the JWT if you haven't before
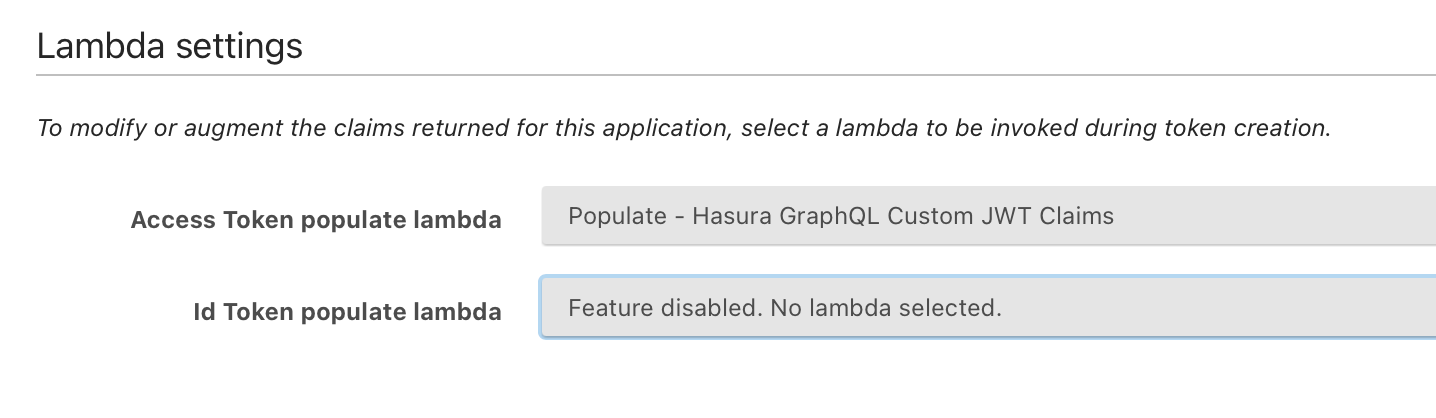
- Set Access Token populate lambda to your newly created lambda
3 - Create a Signing key on FusionAuth
- Go to https://fusioauth:9011/admin/key/
- Create a new key based on your choice of algorithm. I'd go with RSA256 or RSA512 since you don't need to share your private key with Hasura or anybody else
4- Tell your Fusion App to use the key
- You've created a key. Now you need to have your tokens be signed with it. Find your FusionAuth app here https://fusionauth:9011/admin/application/ and click edit.
- Click on the JWT tab
- Select your Key created before for Access Token signing key
- Select your Key created before for Id Token signing key
- Save your app
5- Tell Hasura where to get the signing public keys
- Hasura has a config parameter named HASURA_GRAPHQL_JWT_SECRET, which it uses to grab public keys to verify your Auth header tokens. Put it in your docker-compose file. (or into the file you set your Hasura config)
HASURA_GRAPHQL_JWT_SECRET='{"type": "RS512", "jwk_url": "https://fusionauth/.well-known/jwks"}'6- Restart your Hasura instance
- If you're using Docker, you'd do
docker restart hasura_docker_image_name7- Tell your Hasura how to use row or column level permissions for the tables you track
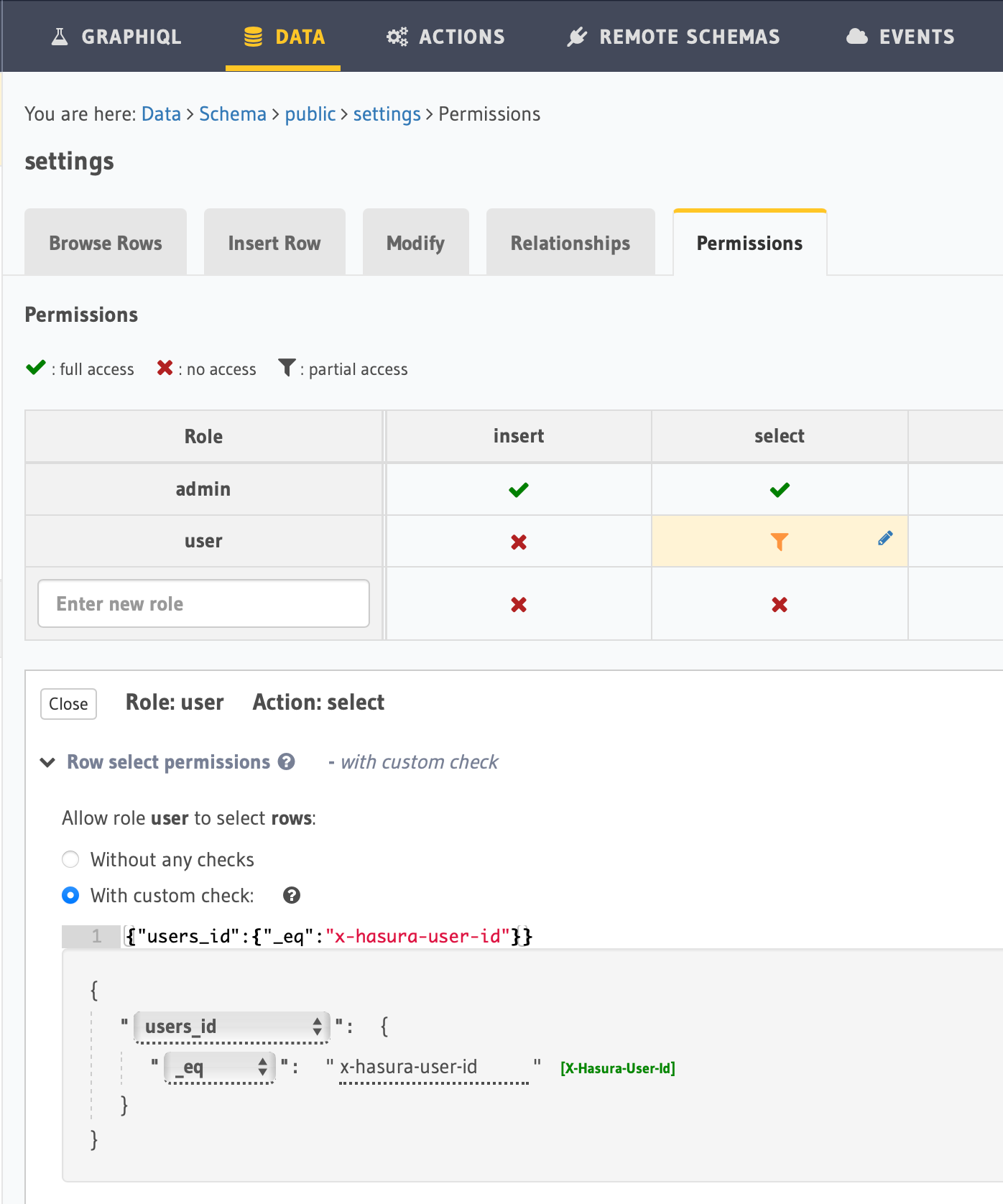
- Hasura helps you to set row or column level permissions on the DATA page of its dashboard. Find your table and set select permission as it described in this tutorial
- Basically, add your user group, and set your permission to check the user-id set in the request's header.
{"users_id":{"_eq":"x-hasura-user-id"}}- Here, I set "user" role permission on my app's user "Settings" table we store user-specific settings so only the user in auth header could get the data that strictly belongs to him/her
8- You're pretty much ready to make a request now with your token
- I Assume you've used one of the workflows to get your auth bearer token from FusionAuth. They cover pretty much every scenario on their blog you can find here, a must-read!.
- Make a Curl request or use a tool like Postman.
- Authentication header
- Make your request for the logged-in user by sending his/her token
curl -X POST https://publish.graph.circleboom.com/v1/graphql -H 'Authorization: Bearer eyJhb..............' -H 'Content-Type: application/json' -d '{"query": "{ settings { job_start_time } }" }'- Get your user-specific answer back for the token owner
{"data":{"settings":[{"job_start_time":"22:30:00"}]}}Next: Refresh JWT token by following The Ultimate Guide to handling JWTs on frontend clients (GraphQL) *
-
RE: What is the best practice for differentiating free-tier users from the paid subscribersposted in Q&A
Thank you for the answer @mgetka. The subscriptions are already managed on a billing platform. What I'm trying to figure out is to find an efficient way to give the logged-in user a decent screen based on his/her subscription type (free/paid) without checking it via the billing systems API every time.
I checked user actions they seem promising as you said. FusionAuth says it's roughly used for user reward mechanisms, I'm still trying to align that to my purpose.
-
What is the best practice for differentiating free-tier users from the paid subscribersposted in Q&A
I'm trying to figure out whether to use FusionAuth groups and roles to keep users' subscription status or not.
From one perspective, it is a correct way to differentiate logged in users by using built-in roles/groups for a SaaS authentication setup. On the other hand, I'm not sure if FusionAuth's roles/groups are meant to be used like that.
What would be the best practice to understand a user's subscription status for the given app (under a tenant) during or after the login to enable disable features?
Thank you