Identity Provider with no email?
-
I am using
name emailas it shows in the documentation and I can log in. You can enabledebugon the Apple Identity Provider which may provide you some additional details if it is not working. -
Checked again. Here's the screenshot:
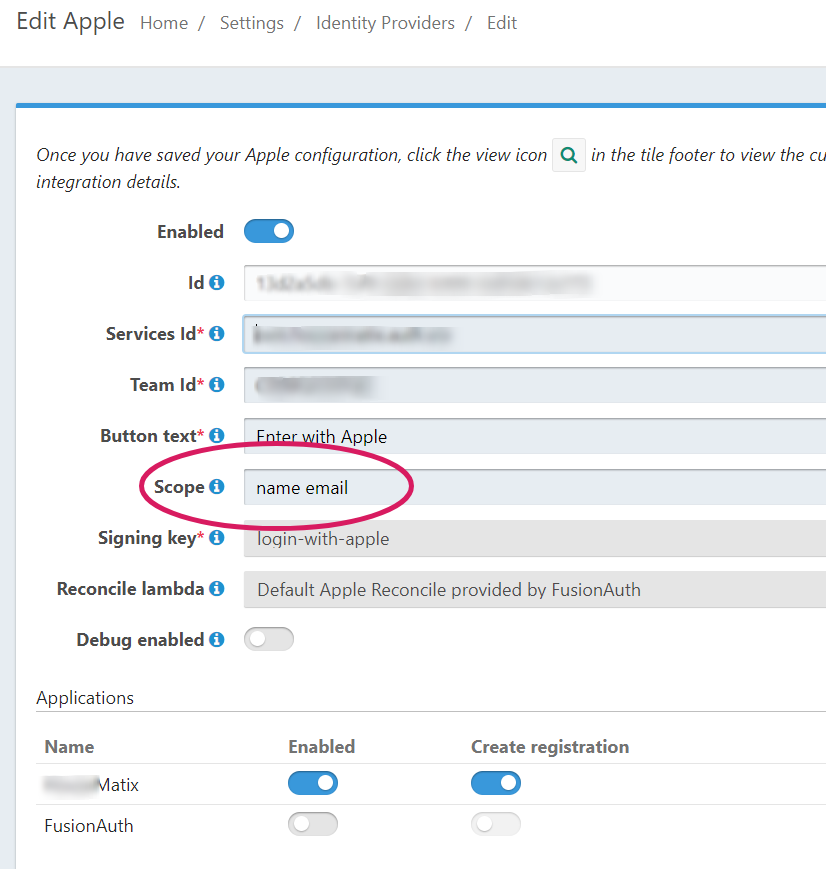
Apple authentication is done, back to FusionAuth, and still
An email address was not provided for the user. This account cannot be used to login, unable to complete this login request.I can't really debug inside Docker - the Portainer->log only shows an irrelevant error that happened ages ago:
`
26-Sep-2020 13:55:07.670 INFO [http-nio-9011-exec-2] org.apache.tomcat.util.http.Parameters.processParameters Invalid chunk starting at byte [172] and ending at byte [173] with a value of [=] ignoredNote: further occurrences of Parameter errors will be logged at DEBUG level.
WARNING: An illegal reflective access operation has occurred
WARNING: Illegal reflective access by org.apache.ibatis.reflection.Reflector (file:/usr/local/fusionauth/fusionauth-app/web/WEB-INF/lib/mybatis-3.4.6.jar) to field java.util.UUID.serialVersionUID
WARNING: Please consider reporting this to the maintainers of org.apache.ibatis.reflection.Reflector
WARNING: Use --illegal-access=warn to enable warnings of further illegal reflective access operations
WARNING: All illegal access operations will be denied in a future release`
-
Hiya,
Can you please check the
debugsetting (below 'reconcile lambda') and run through the login sequence again? It'd be great to see if that provides more details. -
@dan here's the message:
An email address was not provided for the user. This account cannot be used to log in, unable to complete this login request.debugis enabled, but I have no idea where to look for logs - under docker the log that is seen in e.g. Portanier is only showing some older warnings:WARNING: Please consider reporting this to the maintainers of org.apache.ibatis.reflection.Reflector WARNING: Use --illegal-access=warn to enable warnings of further illegal reflective access operations WARNING: All illegal access operations will be denied in a future releaseAnother interesting thing: of two of my friends who tried it, one was able to log in, and Apple even asked him if he wanted to hide his real email address. The other one got the same message that I'm getting.
-
Hiya,
Hmmm. That's not super helpful, eh? The ibatis errors shouldn't be related (see https://github.com/FusionAuth/fusionauth-issues/issues/721 for more about that particular warning).
Just to check, the screenshot you shared had
debugdisabled, but you definitely enabled it?Are you seeing anything in the event log (in the admin UI) that might shed more light on the situation?
Does the email address you are using to try to login with have any special characteristics?
-
I played with it more and found this:
-
Login with Apple sometimes works, sometimes doesn't. It looks like users with emails that are not known to my FusionAuth are fine. But existing emails are not.
-
When a new user is successfully registered via Google or Twitter (didn't try other providers) all there fields are returned by /oauth2/userinfo: 'given_name', 'family_name', and 'name'. And consequently the FusionAuth database has all three: 'firstName', 'lastName', and 'fullName'.
However, when a new user is onboarded via the Apple plugin, the user is missing 'name' as returned by /oauth2/userinfo, and 'FullName' is also missing from the database.
-
-
The results of the
Userinfoendpoint will reflect what is in the JWT and what additional details FusionAuth knows about the user.So with Twitter, Facebook, Google and Apple, this will all depend upon what is returned from those providers, and then subsequently what you do with that information during login.
Each of these IdPs can be assigned a Reconcile Lambda, a default lambda is provided with FusionAuth that you can use and modify.
https://fusionauth.io/docs/v1/tech/lambdas/apple-reconcile/
https://fusionauth.io/docs/v1/tech/lambdas/facebook-reconcile/
https://fusionauth.io/docs/v1/tech/lambdas/google-reconcile/
https://fusionauth.io/docs/v1/tech/lambdas/twitter-reconcile/In your example, are you using an Apple Reconcile Lambda, and if so, can you post your lambda function?
Apple will only return the user's first and last name on the very first authentication event. Subsequent events will not contain this information, so if you were to log a user in using the Apple provider, and then subsequently assign a reconcile Lambda that would otherwise attempt to capture this information, you will not have that User's first and last name in FusionAuth.
Similarly with Twitter, we would need to see your reconcile Lambda function body that you have assigned to this IdP configuration to understand what is being obtained from Twitter and stored in FusionAuth.
Hope that helps!
-
Can we just skip the login part and just return the
userInfo? -
@robotdan said in Identity Provider with no email?:
Each of these IdPs can be assigned a Reconcile Lambda, a default lambda is provided with FusionAuth that you can use and modify.
I'm using the default lambda. And it does NOT return "name/fullname" as I mentioned earlier. Google and Twitter do return "name/fullname".
Here's how Apple Identity provider is set up:
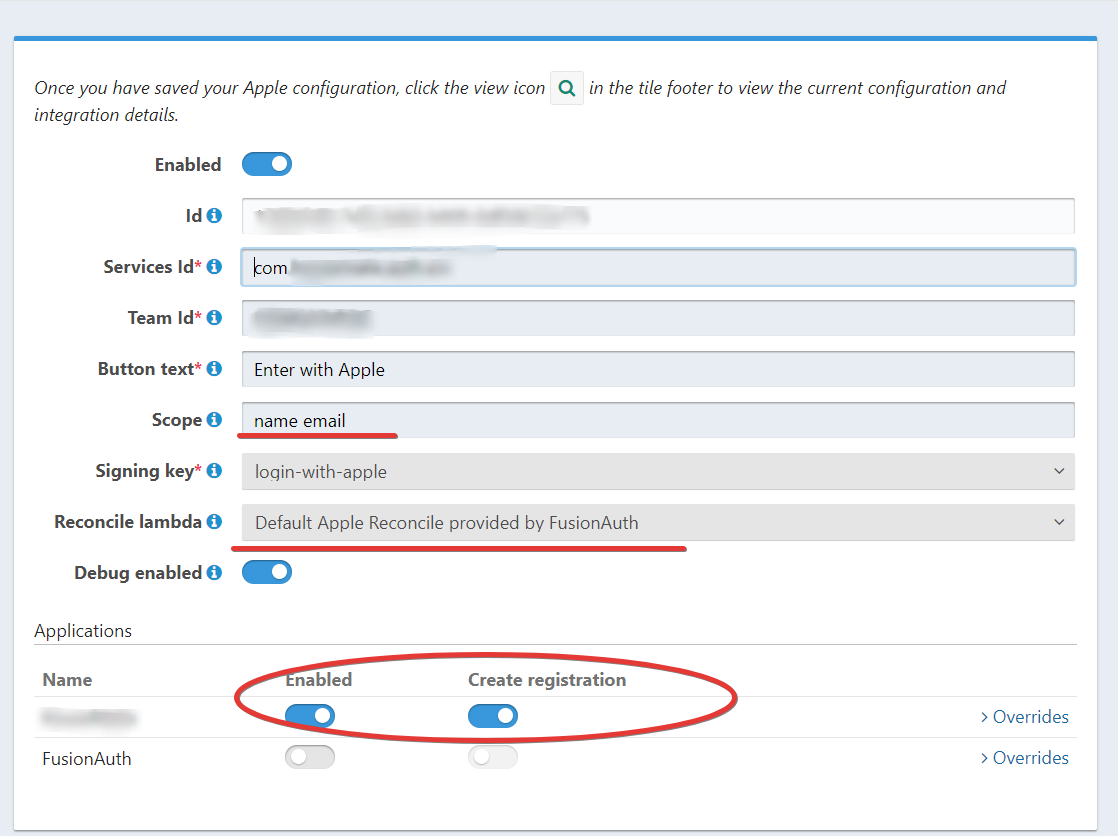
-
What is the lambda seeing? Can you have the entire JSON object printed to the log and share that?
-
Important
Apple only returns the user object the first time the user authorizes the app. Persist this information from your app; subsequent authorization requests won’t contain the user object.
(https://developer.apple.com/documentation/sign_in_with_apple/sign_in_with_apple_js/configuring_your_webpage_for_sign_in_with_apple)So you should go to Settings->ID Apple ->Password&Security and remove the app from apps that use your Apple ID
Now you can register again and apple will send the userInfo.
-
@robotdan Is the workaround for no email Identity Providers available in SAML as well?
-
@joseantonio Nope, only for OIDC. Feel free to file an issue explaining your use case or open a support ticket if you have a support plan.
-
I was incorrect. I've learned that you should be able to do this with a SAML Lambda. Here's the documentation for the SAML lambda you should customize: https://fusionauth.io/docs/v1/tech/lambdas/samlv2-response-populate/ Sorry about that.
Please let us know how this goes.
-
This post is deleted! -
@dan Thank you for the help. Indeed it is not possible to assign a generated email in SAML reconcile lambdas. However, I found a solution for my problem.
Using SAML reconcile lambda, I create a new metadata field for the registration called "generated_email". Then, I assign it to the JWT response for the specific application using a JWT populate lambda. Example:
Edit: adding code for SAML reconcile lambda as well.SAML reconcile:
function reconcile(user, registration, samlResponse) { var userid=samlResponse.assertion.subject.nameID.id; //registration.email = userid + '@subdomain.mydomain.com'; This can't be done yet registration.data.generated_email=userid + '@subdomain.mydomain.com'; }JWT populate:
function populate(jwt, user, registration) { if(registration.data&®istration.data.generated_email){ var new_email= registration.data.generated_email; jwt.email= new_email; }else{ console.debug('No generated email set'); } }(after checking that it exists for the registration).
New problem: I need to make an API call inside the SAML reconcile. Is this possible?
-
@joseantonio said in Identity Provider with no email?:
I need to make an API call inside the SAML reconcile. Is this possible?
Nope, this is currently not possible, unfortunately.
Upgrading lambda functionality to support network requests is an open issue. Please vote it up if it is important to you.
If this is very important to you, you can engage our professional services.
More on the FusionAuth roadmap.
-
In the next release we plan to add additional options for IdPs for account linking. In this up-coming release you should be able to do things such as:
- Use an IdP that only uses usernames (at your own risk)
- Modify or build an email address using a Lambda for any IdP (at your own risk)
- Modify or build a username using a Lambda for any IdP (at your own risk)
- Use an IdP that does not have a username or email address
-
It looks like setting the email address in a lambda works for Facebook now (as of at least 1.41.2):
if (!facebookUser.email) { user.email = facebookUser.id + '@no-email.facebook.com'; }1/10/2023 10:10:33 PM Z Linking strategy [LinkByEmail] 1/10/2023 10:10:33 PM Z Resolved email to [] 1/10/2023 10:10:33 PM Z Resolved username to [null] 1/10/2023 10:10:33 PM Z Resolved unique Id to [115587478085870] 1/10/2023 10:10:33 PM Z Identity provider returned a unique Id [115587478085870]. 1/10/2023 10:10:33 PM Z A link has not yet been established for this external user. 1/10/2023 10:10:33 PM Z The user with the email address [] does not exist. 1/10/2023 10:10:33 PM Z Invoke configured lambda with Id [787cd34e-1618-4cd9-8156-936734cfe368] 1/10/2023 10:10:33 PM Z The lambda set or modified the initially resolved email. Email is now [115587478085870@no-email.facebook.com] 1/10/2023 10:10:33 PM Z Creating user: 1/10/2023 10:10:33 PM Z User is not registered for application with Id [e0da3f10-7efa-4a6b-95f8-fbf4894884b5] 1/10/2023 10:10:33 PM Z User has successfully been reconciled and logged into FusionAuth. 1/10/2023 10:10:33 PM Z Authentication type: FACEBOOK 1/10/2023 10:10:33 PM Z Authentication state: Authenticated