Licensing
Overview
FusionAuth will always have a powerful, full featured free-to-use Community plan. This is the foundation of FusionAuth and the community surrounding it and as an organization FusionAuth is committed to improving the Community plan, with both features and bug fixes.
However, there are additional tiers of functionality which meet the needs of different types of organizations and offer premium features. For these plans, a license is required.
You can learn more about purchasing FusionAuth plans other than Community on the pricing page. The legal agreement you make when using FusionAuth, with or without a paid plan, is the FusionAuth license. Learn more about the license in the licensing FAQ.
You can see a list of features on the plans and features page.
Here’s a brief video documenting how to find and add your license to your instance if you have a paid plan.
The video covers the same content as the Adding Your License to Your Instance section.
Adding Your License to Your Instance
To access paid features, purchase a license via the pricing page or by contacting the sales team.
Once a license is purchased you must activate it. To do so, log into your Account. Navigate to the Plan tab.
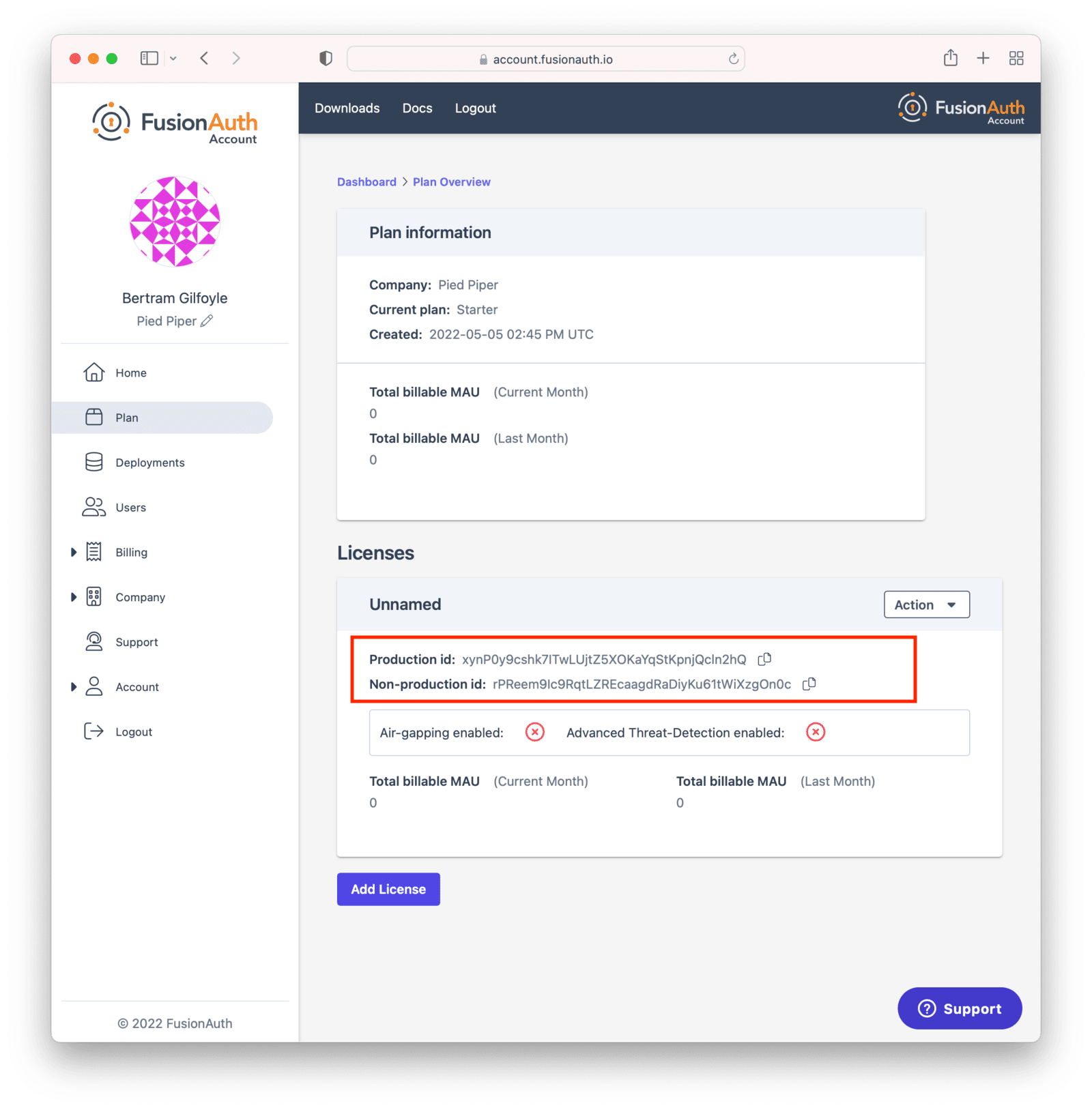
Copy the license Id appropriate for your needs.
Use the “Production” license Id for your production server. This will be used to calculate your monthly active users (MAU), which may affect your monthly bill. Learn more about MAU here. The other license Id is suitable for non-production environments, such as user acceptance testing or development.
You can always find your license Id by logging in to your Account and then navigating to the Plan tab. If you do not have a license Id there, you are on the Community plan. In that case, no license is required.
After you have your license Id, log in to your FusionAuth instance.
The credentials you use to log into the instance have no connection to the credentials you used to log into your account portal. Navigate to the Reactor tab and enter your license Id in the License key field.
You will need either the admin or reactor_manager roles in the FusionAuth application to view the Reactor tab.
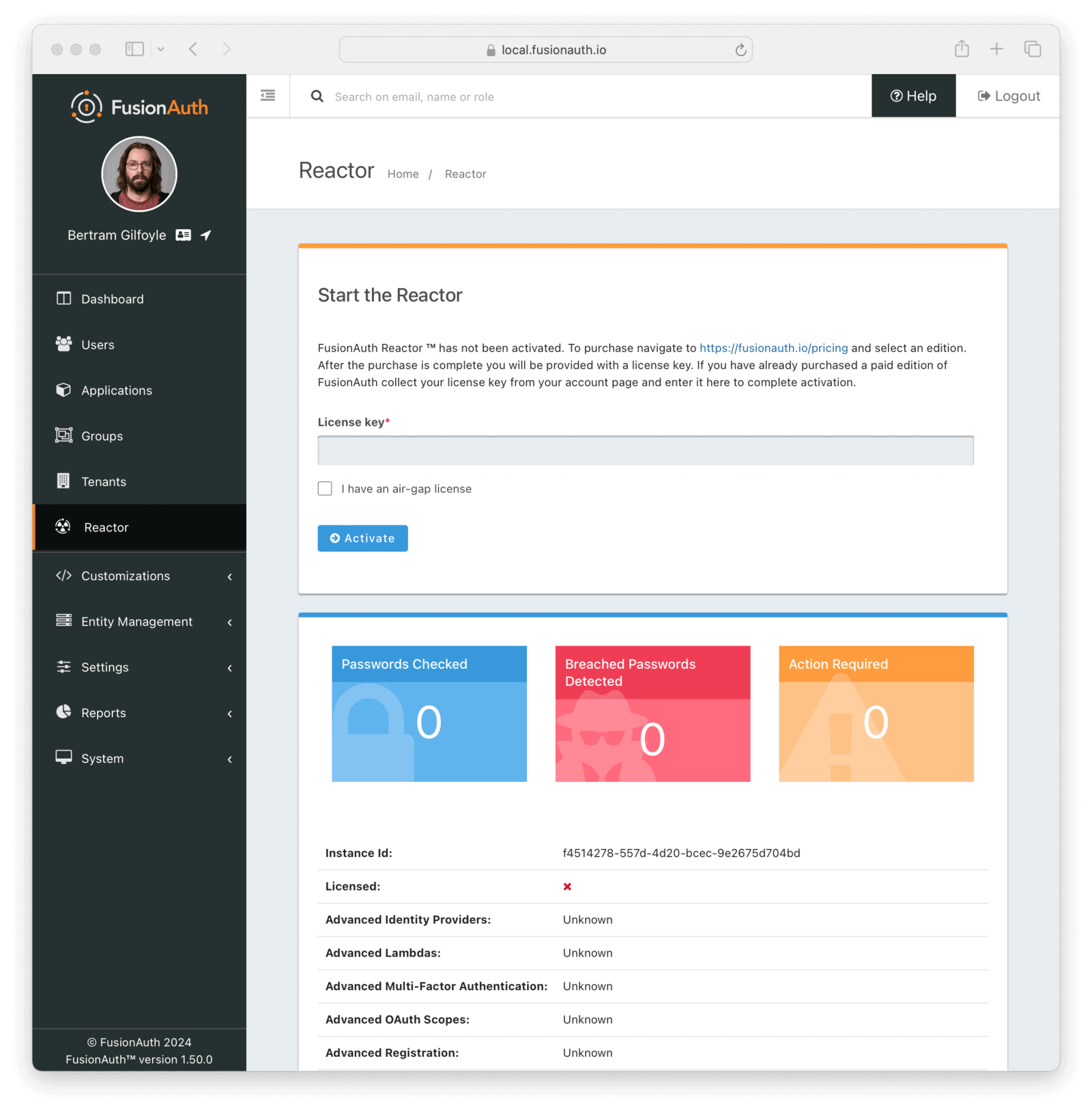
In an air-gapped configuration where outbound network access is not available, the license text will be available in your account. Check the I have an air-gapped license box and include this value in the License text field in addition to filling out the License key when activating. If you need an air-gapped license because your application will not have internet access or for any other reason, please contact sales for more information. See Advanced Scenarios for more information.
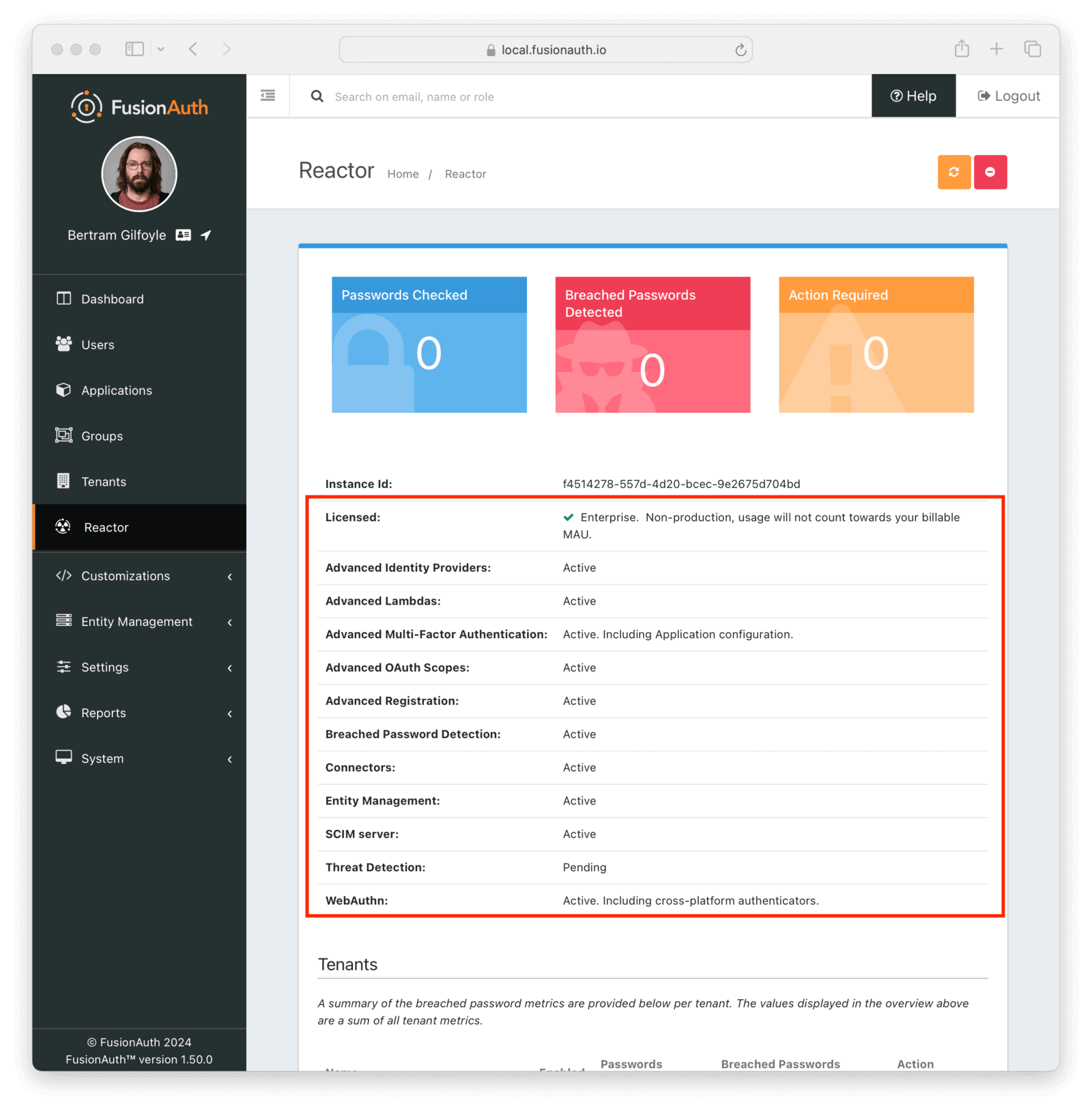
Immediately after activating, FusionAuth must obtain a secure connection to FusionAuth’s servers. It may take a minute or two to complete activation.
Once that has happened, the Licensed field will change to a green checkmark. This may require a page refresh. You will also see a list of premium features. Depending on your particular plan, some may not be active. You can see a list of features on the premium features page.
Regenerating Your License
You may want to regenerate your license for any number of reasons.
- It may be part of a regular secrets rotation system.
- You may have inadvertently exposed your license key.
You can do so using the Reactor API.
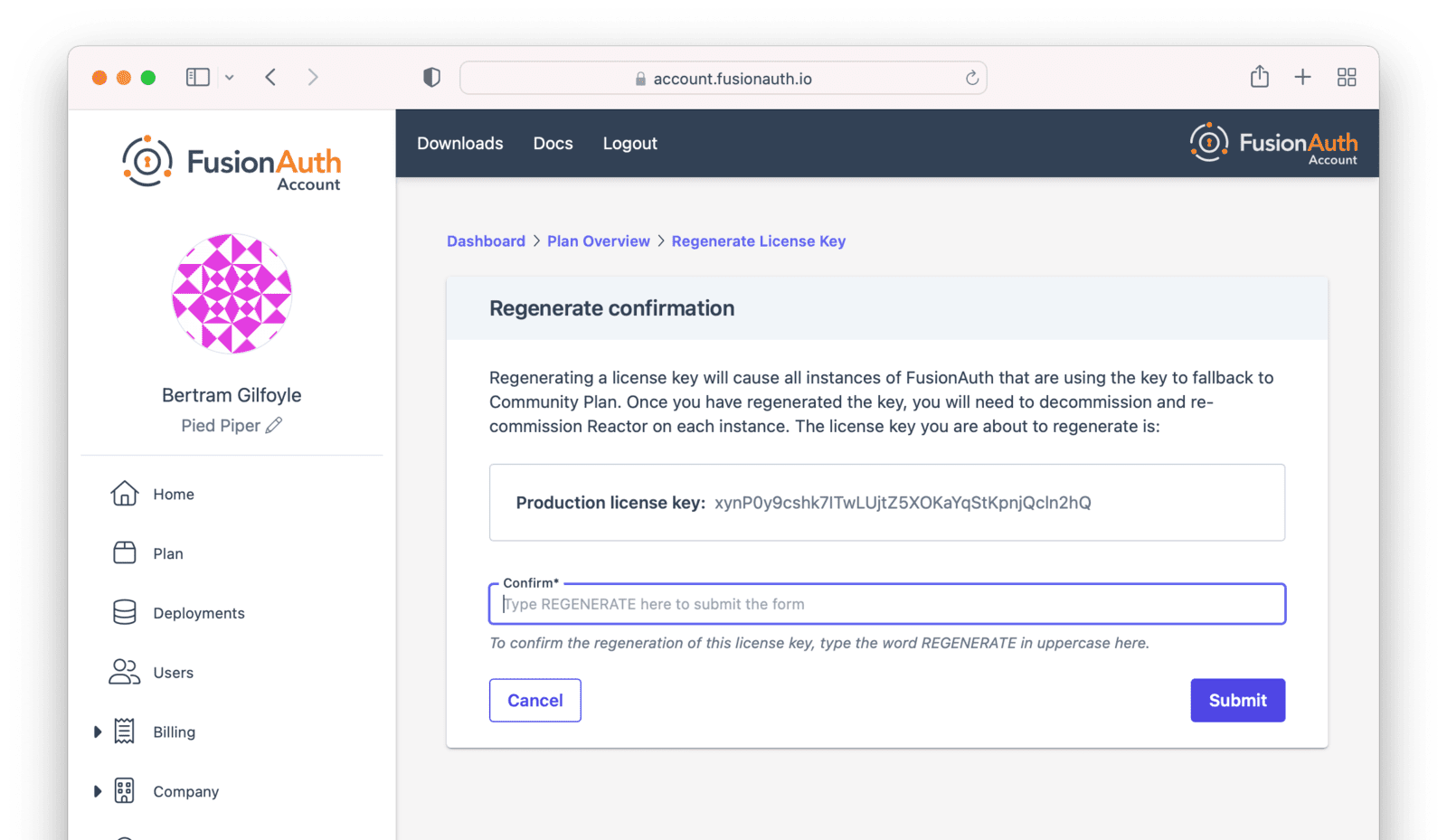
But you can also regenerate the license via the Plan tab. To do so, log into your Account. Then navigate to the Plan tab. Then click the Action button to display the dropdown.
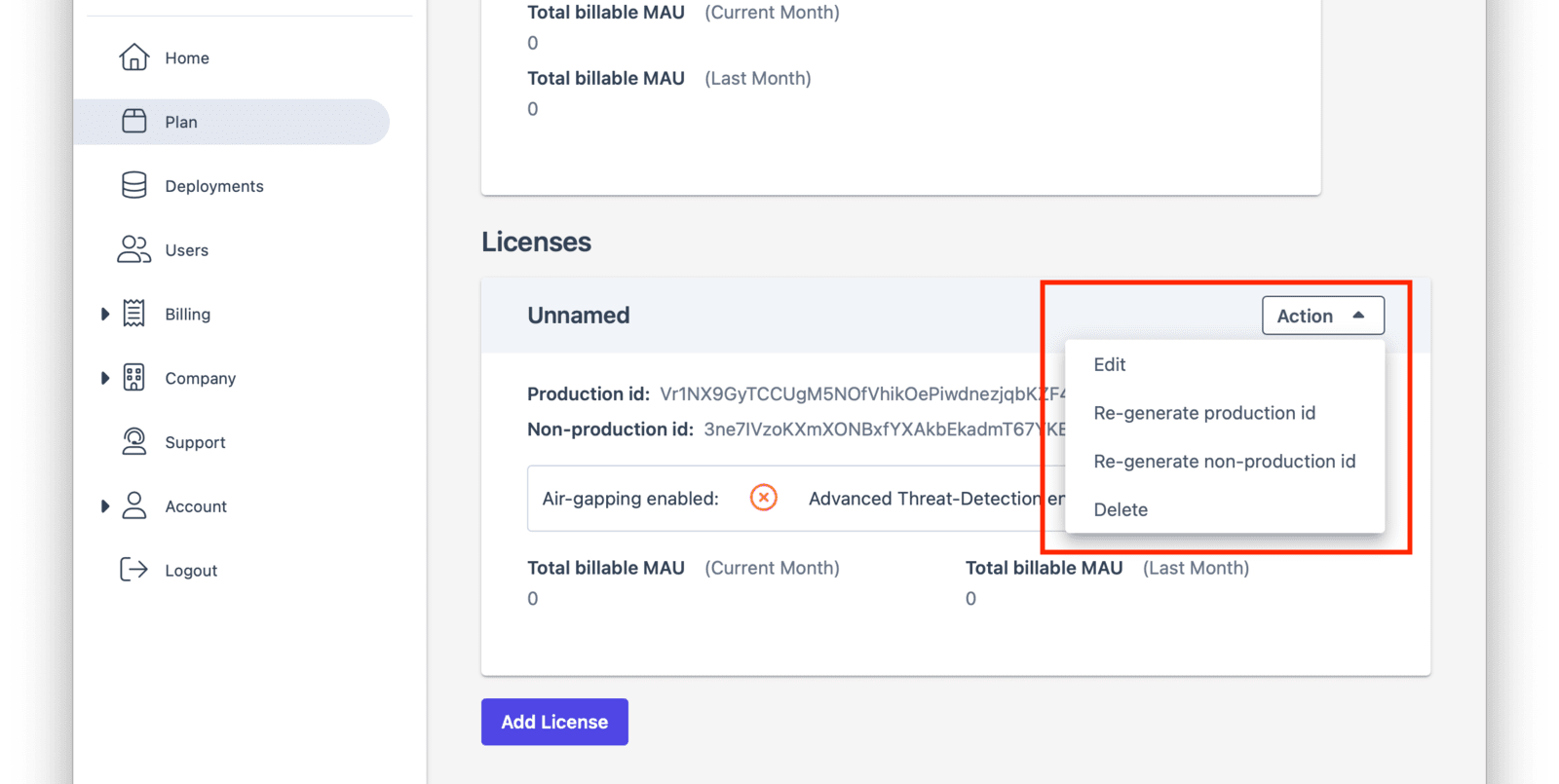
After you choose which license to regenerate, you’ll be prompted to confirm your choice.
Deactivating Your License
Should you need to deactivate your license Id, either because you are changing your plans or rotating your license Id, you can do so by using the Deactivate link, in the upper right hand corner of the Reactor page.
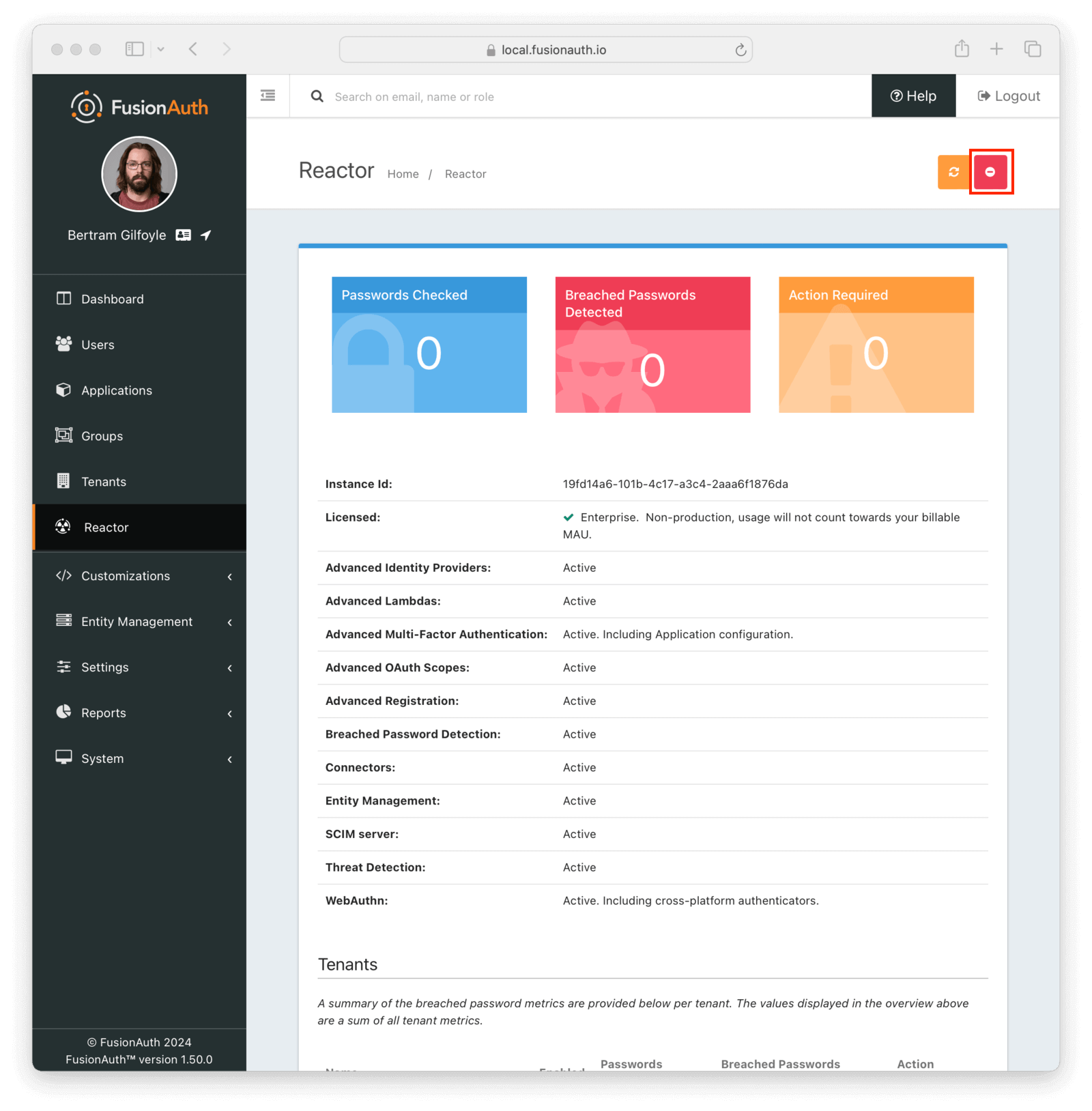
Deactivating your license will disable any premium functionality.
This includes both the ability of users to access such functionality and the ability of admins to configure it.
For example, consider the scenario where you:
- Activate your license.
- Enable email MFA on your tenant.
- Have users set up email MFA on their accounts.
Then, after some time, you deactivate your license. While your license is deactivated, the following functionality will be affected:
- Users will not be able to configure email MFA.
- Users with configured email MFA will not be prompted for the additional factor at login, but will still be able to log in.
- Administrators will not be able to configure additional MFA methods.
However, deactivating your license does not remove configuration previously saved while the license was active. In the scenario above, if you were to activate a license, users and admins would immediately be able to access previously disabled functionality and the previous configuration would be active.
The License API
You can use the Reactor API to activate or deactivate your license.
You can also retrieve data on the license status of your instance, including whether specific features are enabled or disabled.
Licensing and Kickstart
You can set your license Id using Kickstart as well. Doing so allows you to use features requiring a license in your development environment and continuous integration systems. You should use the non-production license Id in your Kickstart files.
If you would like to set this value during Kickstart, set the value in a top level field called licenseId.
In this example there is a license Id of eb7244dc-5d8e-40cd-a005-70b116fbda31.
{
"licenseId": "eb7244dc-5d8e-40cd-a005-70b116fbda31"
}Learn more about setting up Kickstart.
Advanced Scenarios
You may configure FusionAuth to use an HTTP proxy for any outbound connections. This is done using the proxy.* configuration settings, documented here. When a proxy is configured, FusionAuth will use it for all outbound HTTP connections, including the data downloads for premium features mentioned above. Using a proxy in this manner allows FusionAuth to access external data through a connection of your choosing.
Air-Gapping
If you are running FusionAuth with limited or no network access, you can do so using an air-gapped configuration. The license text will be available in your account. Include this text in addition to the license Id when adding your license to your instance.
Running air-gapped limits certain features in FusionAuth, including breached password detection and advanced threat detection, which depend on downloading external data.
An air-gapped license is designed to work in an air-gapped environment, but you must implement network controls blocking outbound requests from FusionAuth. Here’s the list of hostnames FusionAuth to block:
https://reactor.fusionauth.iohttps://metrics.fusionauth.iohttps://license.fusionauth.io
You should also disable usage data collection.
If you need an air-gapped license, please contact sales for more information.
Deleting Your Account
To delete your account, take the following steps, in this order:
- Log into your account.
- Delete all deployments.
- Switch your account to the Community plan.
- Delete your company.
FusionAuth requires that customers delete their own deployments using the account portal.
FusionAuth is not able to cancel accounts with deployments that could potentially contain critical user data.
To remove your deployments, please log into your account and navigate to the Hosting tab. Once you see your deployment, you can click the Action button and select Delete. After a deployment is destroyed, you won’t be charged for this instance going forward. Any previous usage outside of a free trial will be billed.
Then, switch your plan type to the Community plan. After the current billing cycle is done, you won’t be charged; plans are billed monthly.
After deleting your deployments and changing your plan, your account will not be charged after the current billing cycle, unless you start up another instance or change your plan to something else. It is inactive and can be deleted if you desire.
It is perfectly acceptable to leave your account in this condition, especially in the case where you may be doing future work with FusionAuth. However, if data practices or company policies mandate, you may also remove your account from FusionAuth Cloud. Removing a company and its data is not reversible. To delete the company, navigate to Company -> Danger Zone and follow the instructions there.
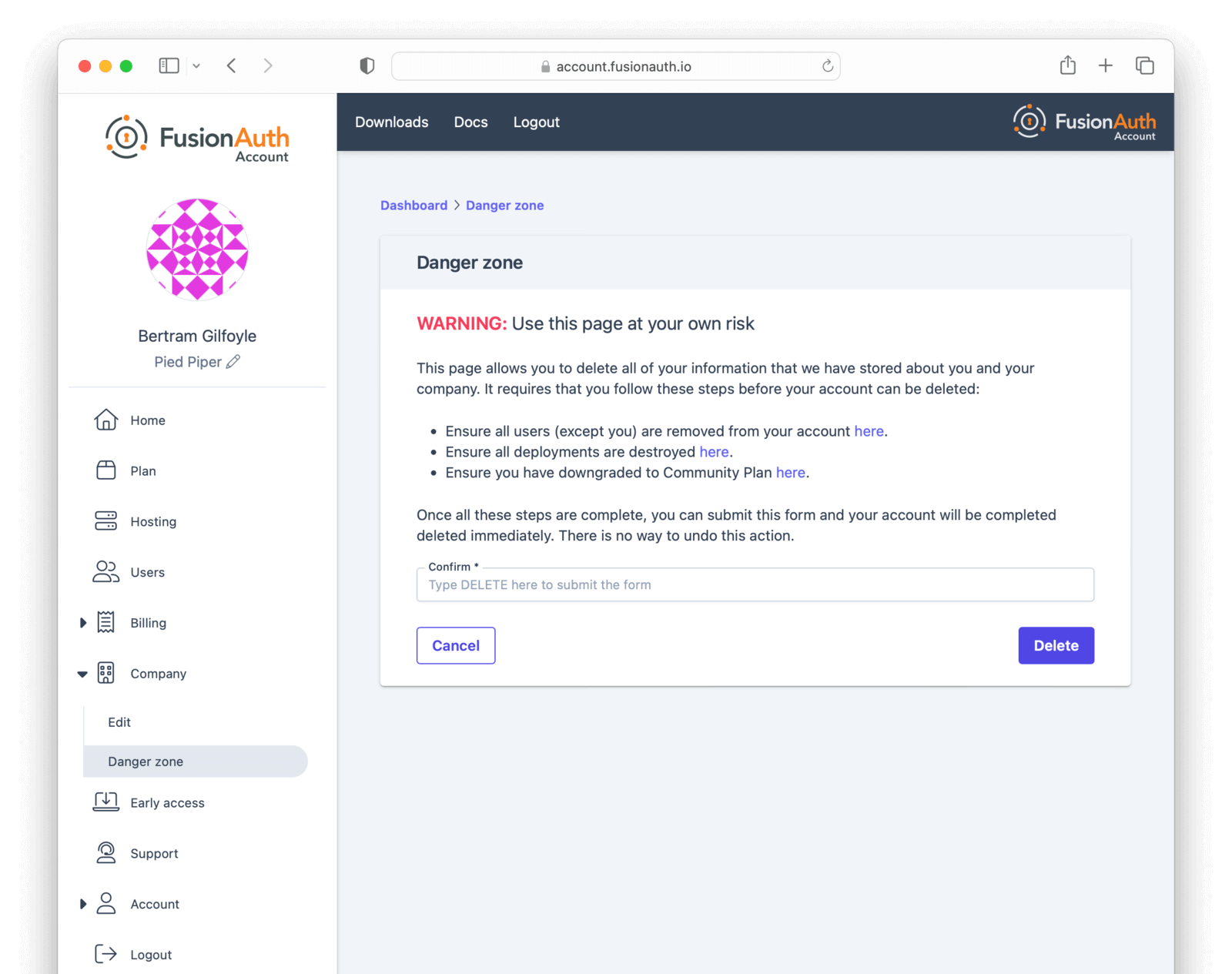
If you cannot delete the company following these instructions, you may have an account which requires FusionAuth team assistance. This occurs if your FusionAuth plan is invoiced, for example.
In this case, please contact your account team for further instructions. A support ticket may also be required to remove your company.
Common Questions
Which license do I use?
There are two licenses, a production license and a non-production one. Use the production license on any system where real live users login. This will be tracked for purposes of MAU calculations, and will affect your monthly bill.
Non-production licenses are used for any other purpose: development, UAT, testing, CI/CD, etc. Any logins which occur on an instance with such a license will not be part of the MAU count.
What counts as an active user?
Any user who logs in during the time period. It doesn’t matter if they log in once or one thousand times. Learn more about what counts as a login here.
Other questions about licensing, MAU overages and certifications can be found in the License FAQ.

