A Fast Path to FusionAuth in Kubernetes
The following set of guides are designed to help you get FusionAuth up and running in a Kubernetes cluster as quickly and easily as possible. Step-by-step instructions are provided on how to setup all of the required infrastructure for your local development machine or favorite cloud provider:
- minikube Setup
- Amazon Elastic Kubernetes Service (EKS)
- Google Kubernetes Engine (GKE)
- Microsoft Azure Kubernetes Service (AKS)
Each setup guide provides instructions on provisioning a Kubernetes cluster specific to the provider. Since FusionAuth requires a database, instructions on creating a managed PostgreSQL database are also included. For required version information, please review the general FusionAuth System requirements.
If you already have your Kubernetes platform setup, the Deploy FusionAuth to Kubernetes guide demonstrates how to configure and deploy FusionAuth to your cluster.
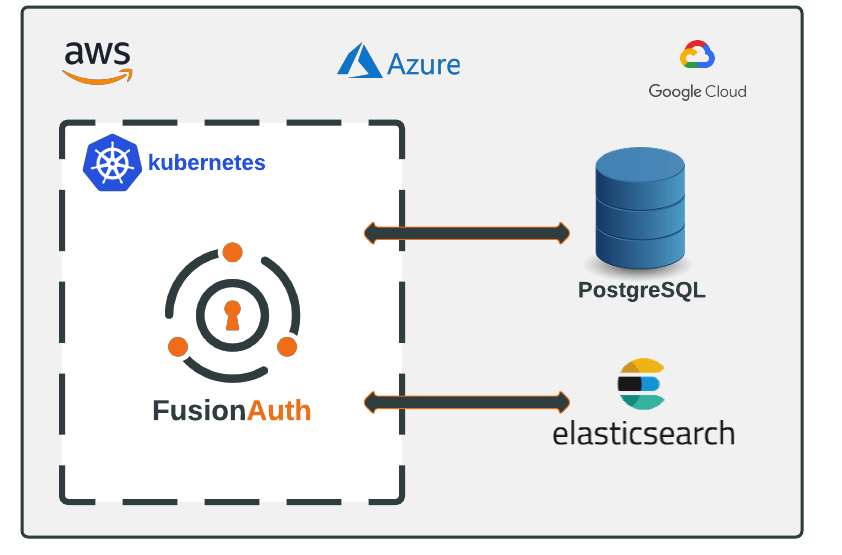
While databases can be deployed in Kubernetes using Stateful Sets, using managed services such as Amazon RDS or Google Cloud SQL are the preferred option as maintenance tasks like scaling, backups, and patching are handled for you.
Instructions are also provided in each guide on how to setup Elasticsearch. Using Elasticsearch is optional and can be configured accordingly prior to deploying FusionAuth.
Istio
Community provided Istio configurations can be found here.
Here’s a sample, community contributed, Istio configuration file.
---
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
name: auth-example-com-tls
namespace: istio-ingress
spec:
secretName: auth-example-com-tls
commonName: auth.example.com
dnsNames:
- auth.example.com
issuerRef:
group: cert-manager.io
kind: ClusterIssuer
name: letsencrypt-prod
---
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: gateway-auth
namespace: istio-ingress
spec:
selector:
istio: public-ingressgateway
servers:
- port:
number: 443
name: https
protocol: HTTPS
tls:
mode: SIMPLE
credentialName: auth-example-com-tls
hosts:
- auth.example.com
---
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: fusionauth
namespace: auth
spec:
hosts:
- auth.example.com
gateways:
- istio-ingress/gateway-auth
http:
- headers:
request:
set:
X-Forwarded-Port: "443"
X-Forwarded-Proto: "https"
route:
- destination:
host: fusionauth
port:
number: 9011
