OpenID Connect with Okta
Configure OpenID Connect with Okta
Once you have completed this configuration, you may enable an OpenID Connect Login with Okta button for one or more FusionAuth applications. See Okta - Generic OpenID Connect as an additional reference.
Here's a diagram of the login flow between:
- the user
- your application
- FusionAuth and
- a remote identity provider such as Okta
Logging In Using Okta
Although this looks complex, the user only sees a few screens, such as the FusionAuth login screen, the Okta login screen, and your application.
Prerequisites
- A FusionAuth instance running on a publicly accessible URL. You can spin up a basic FusionAuth Cloud instance or install it on any server.
- An Okta Workforce Identity Cloud Account connected to a business email address. ** The Okta Verify app if your Okta account is not configured to send SMS messages for 2FA.
Okta Configuration
Log in to Okta and navigate to the Admin panel.

Navigate to Applications -> Applications and click the Create App Integration button.
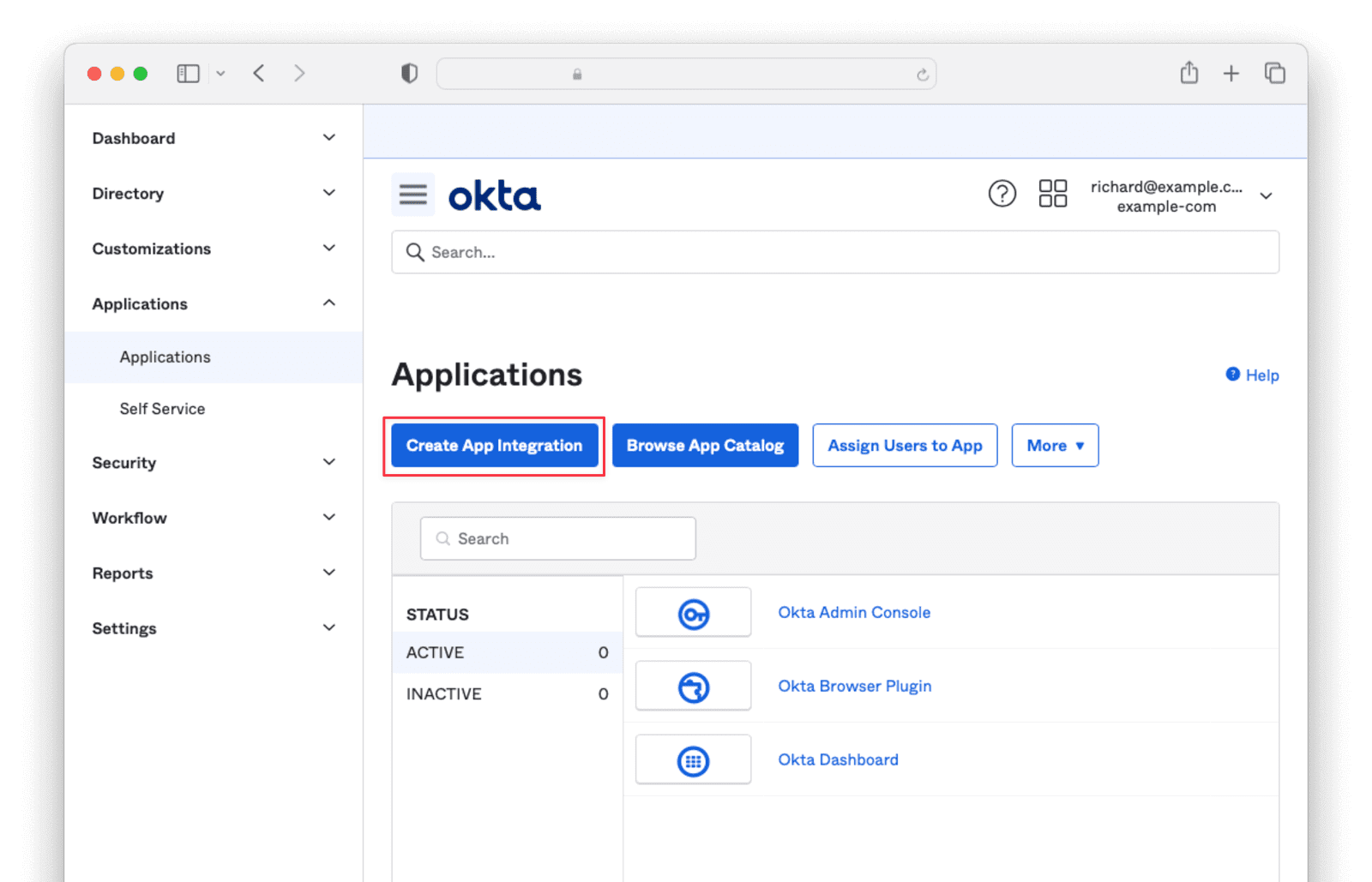
Select OIDC - OpenID Connect and Web Application then click Next.
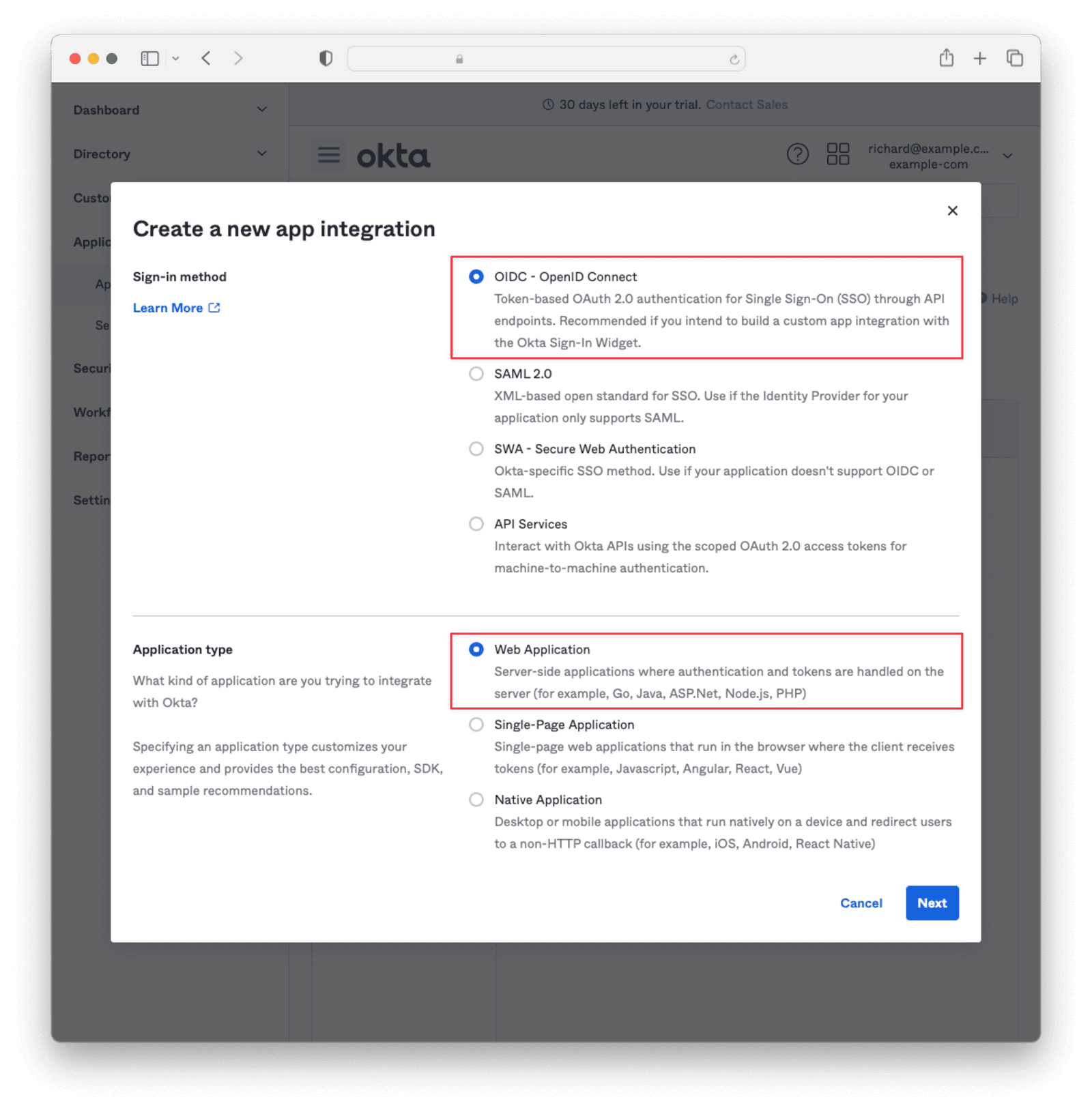
Enter an App integration name and ensure that Authorization Code is checked. Then, supply a Sign-in redirect URI of the form <YOUR_FUSIONAUTH_URL>/oauth2/callback, where YOUR_FUSIONAUTH_URL is the URL of your FusionAuth instance. For example, https://local.fusionauth.io.
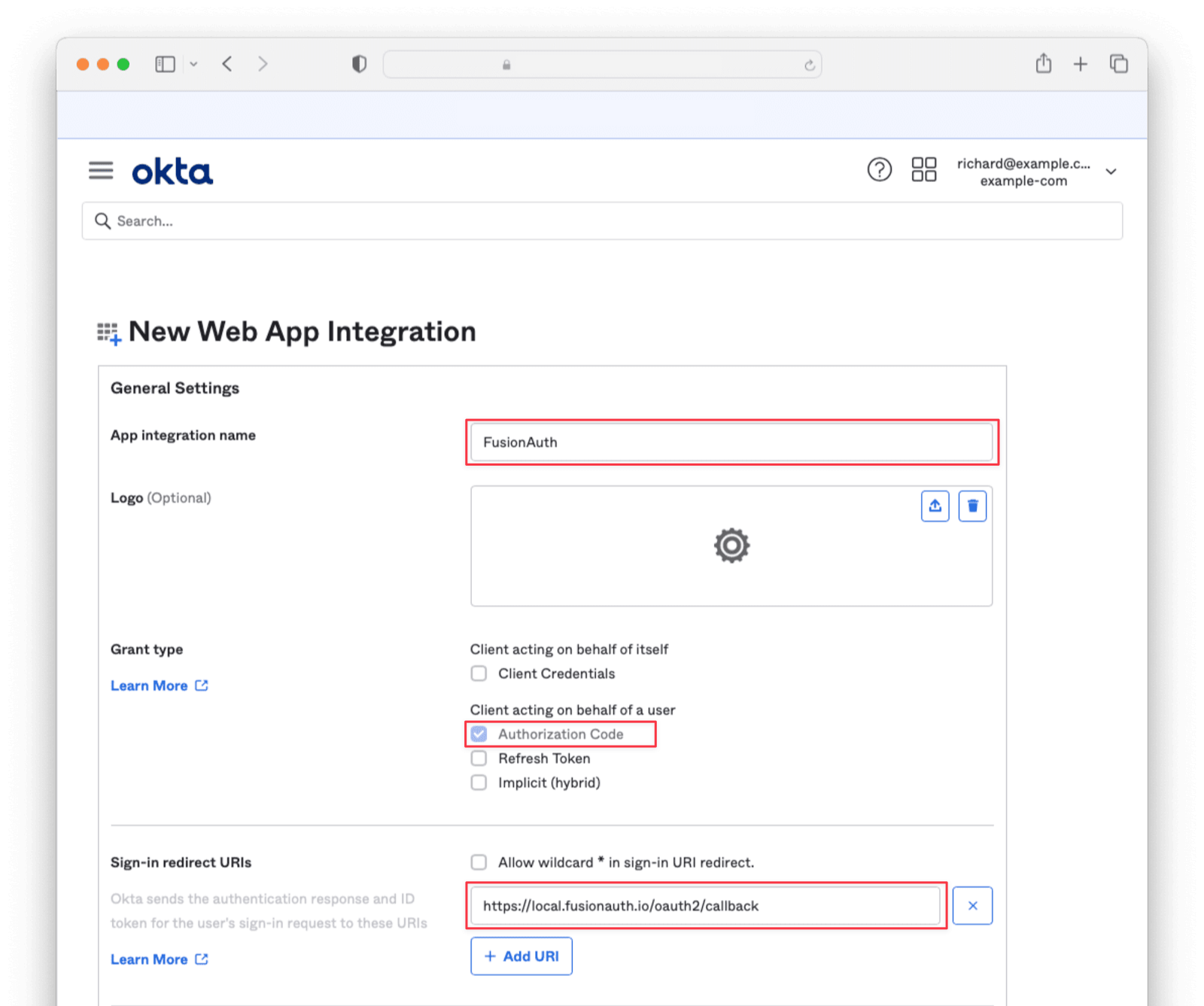
Under the Assignments section, select Skip group assignment for now . Hit Save.
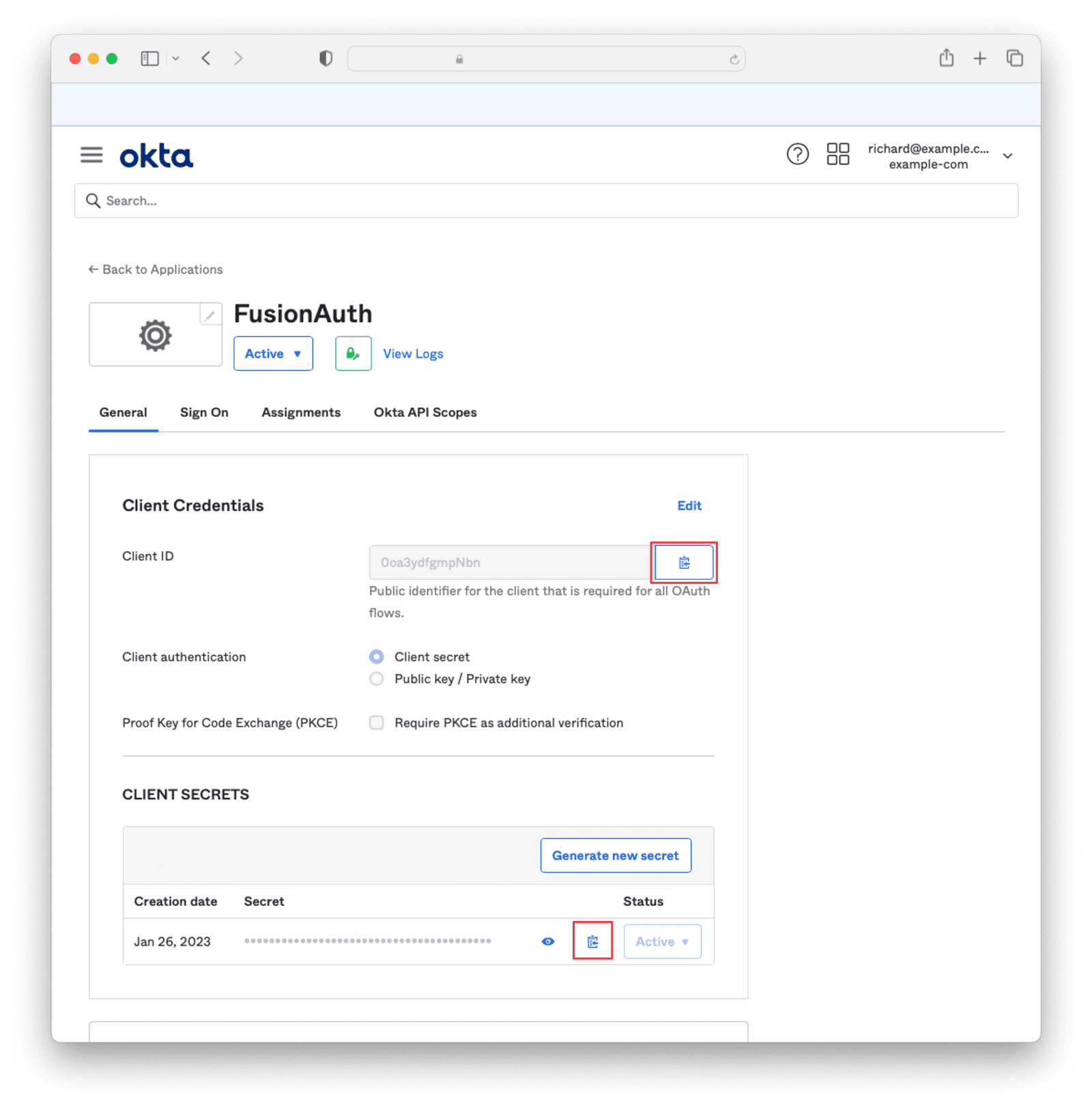
Copy the Client Id and Secret into a text file for later use.
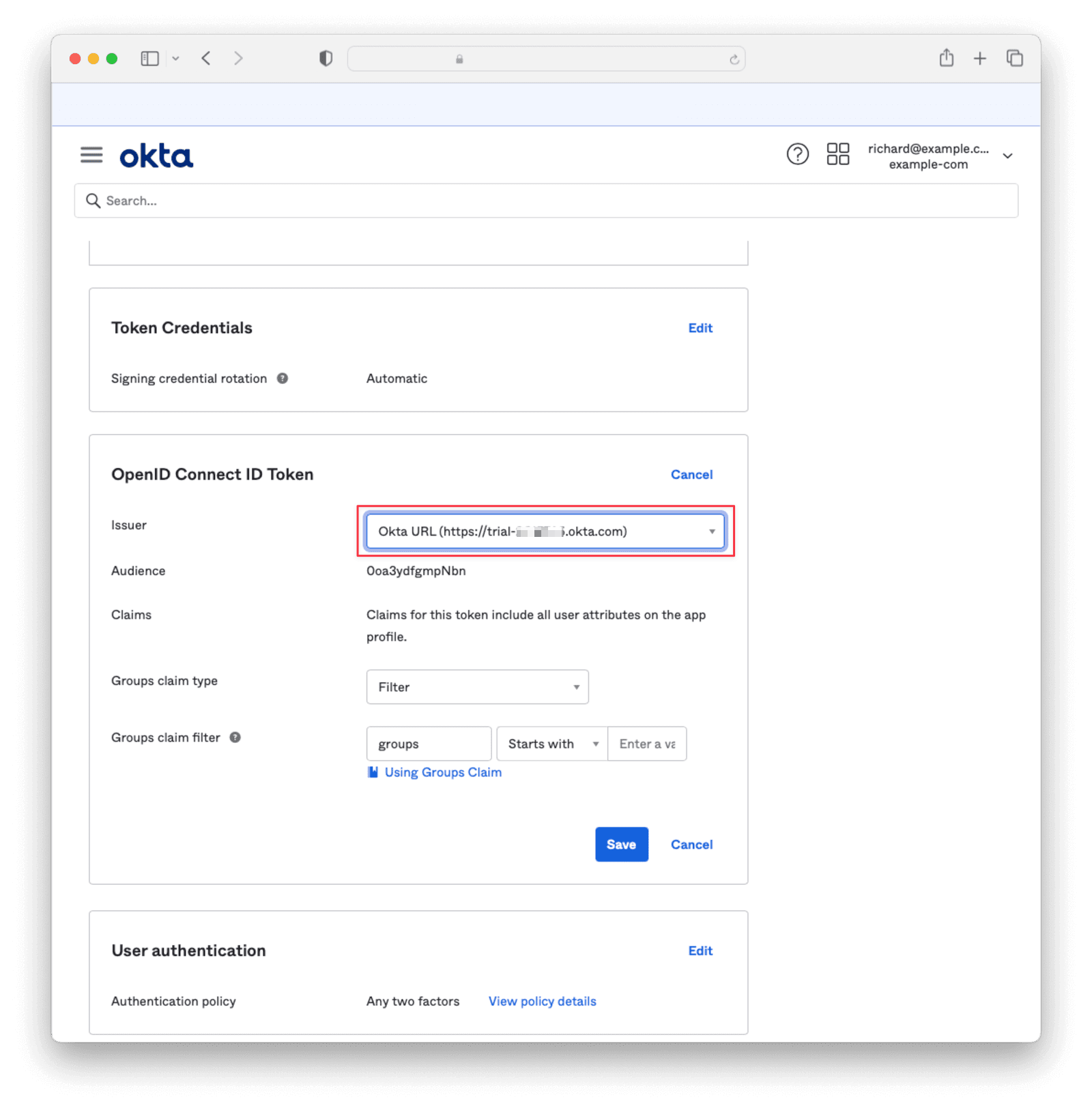
Under Sign On, navigate to the section OpenID Connect ID Token and change the Issuer to use the Okta URL. Hit Save and copy this URL into a text file.
Navigate to Directory -> People and click on the username of the user that you’d like to authenticate. Then click Assign Applications and hit the Assign button next to the one you created. Then click Save and Go Back and Done.
Configure a new FusionAuth OpenID Connect Identity Provider
There is no pre-configured Identity Provider for Okta in FusionAuth. The generic “OpenID” Identity Provider can be used though, as Okta supports the standard OpenId Connect protocols.
Navigate to your FusionAuth instance. Select Settings from the sidebar and then navigate to the section Identity Providers.
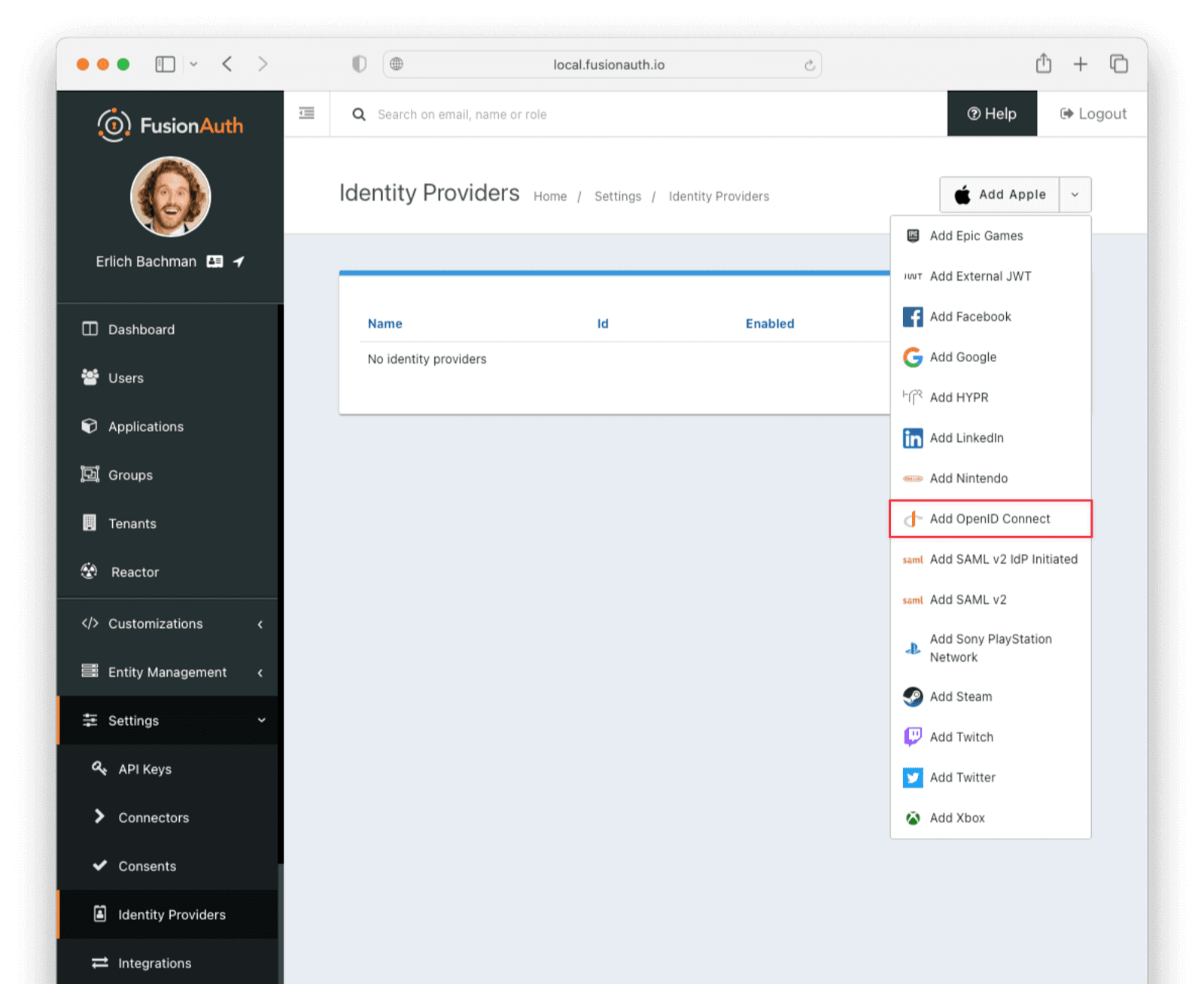
Select Add OpenID Connect from the Add dropdown at the top right of the page.
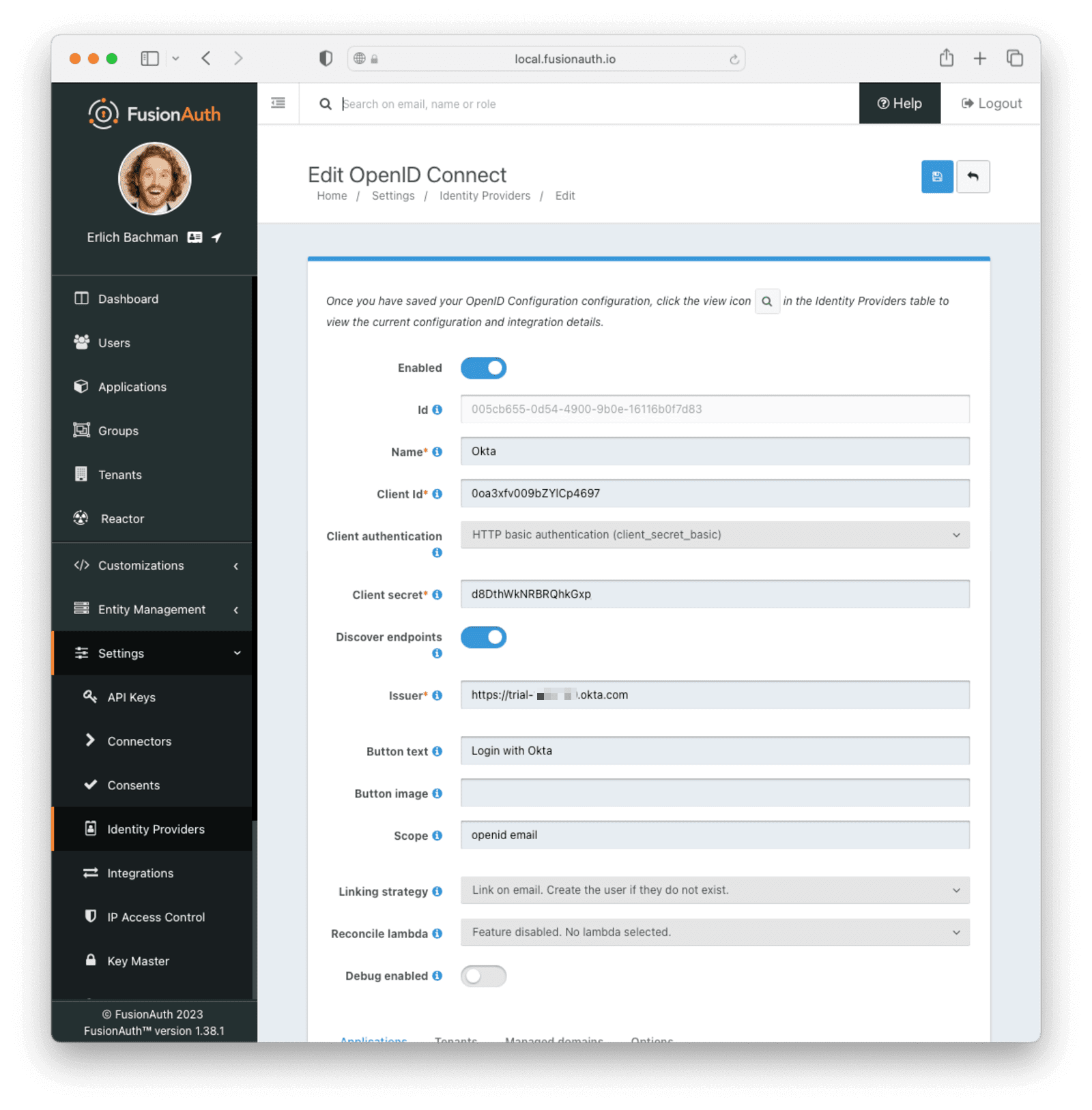
- Provide a Name , like
Okta. - Set Client Id to the
Client IDrecorded when creating the app integration on Okta. - Select
HTTP Basic Authenticationfor the Client Authentication field. - Set the Client secret to the client secret recorded when creating the app integration on Okta.
- Enable Discover endpoints .
- Use the Okta URL that you recorded as the Issuer URL.
- For the Scope , type in
openid email. - Optionally, change the Button Text field to
Login with Okta.
- Navigate to the Applications section and ensure that the application you are adding Okta authentication to has the Enabled and Create Registration switches toggled. Hit Save.
Testing the Login
To test, navigate to the applications page in FusionAuth. Click on the View icon (magnifying glass) next to the application you enabled Okta login on and copy the OAuth IdP login URL address. Navigate to this address. You should see a Login with Okta button on your app’s sign-in page:
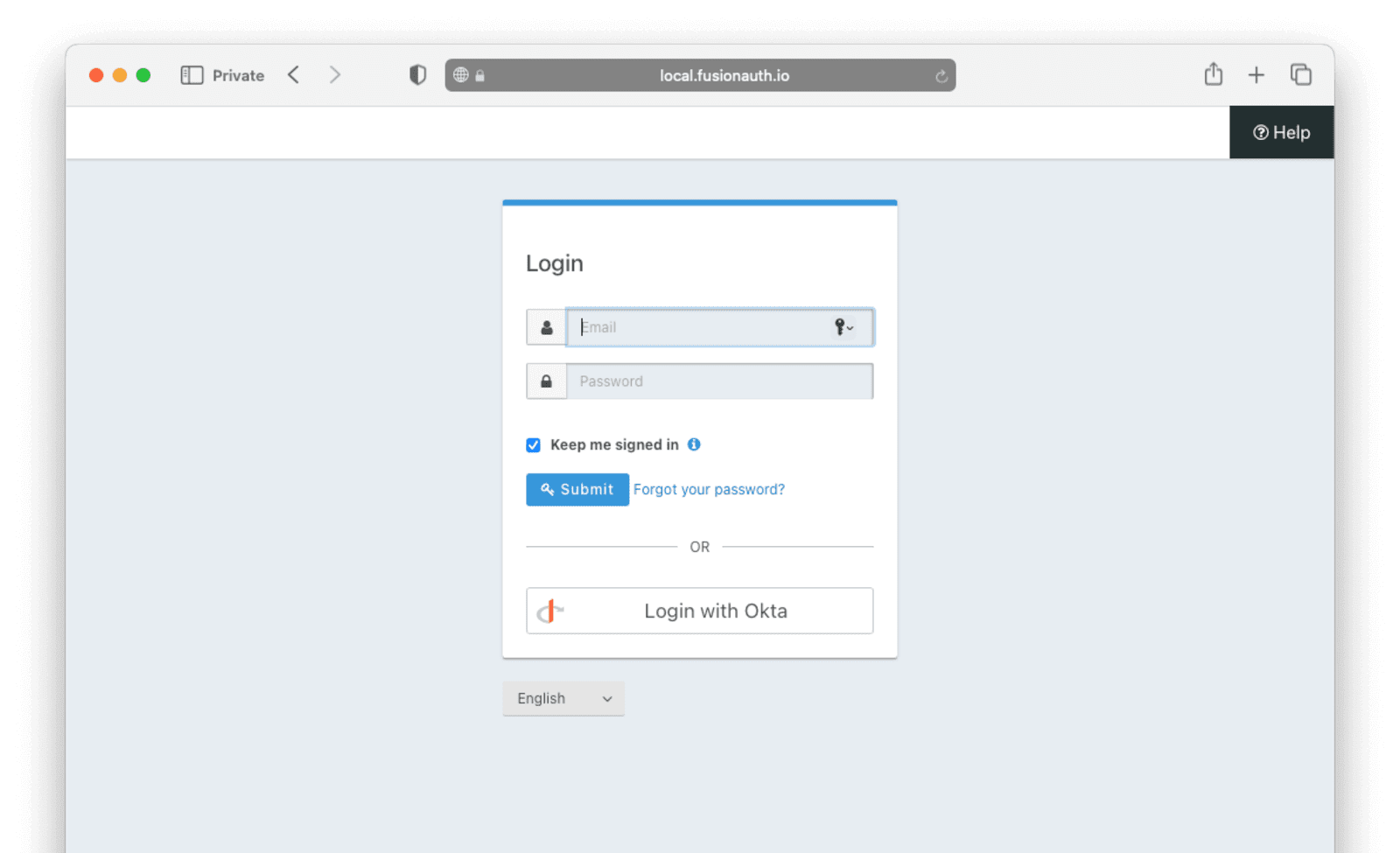
Click the Login with Okta button. Test logging in with the username and password, as well as the 2FA method selected when configuring your account on Okta.
If it is all set up correctly, you should be redirected back to your app, successfully logged in. The user will be added to FusionAuth, and you can examine the Linked accounts section of the user details screen to see that the Okta OIDC link was created.

