OpenID Connect with Azure AD
Configure OpenID Connect with Azure Active Directory/Microsoft Entra ID
Once you have completed this configuration you may enable an OpenID Connect Login with Azure AD button for one or more FusionAuth Applications. See Microsoft Entra ID - Register An App Quickstart Guide as an additional reference.
Here’s a diagram of the login flow between:
- the user
- your application
- FusionAuth and
- a remote identity provider
sequenceDiagram
participant User as User/Browser
participant App
participant FusionAuth
participant IdentityProvider as Provider
User ->> App : View Initial Page<br/>Click Login
App ->> User : Displays Login Page<br/>Including Link To 'Login With Provider'
User ->> App : Clicks On 'Login With Provider'
App ->> User : Redirect To Provider Authorization URL
User ->> IdentityProvider : Enters Credentials
IdentityProvider ->> IdentityProvider : Validate Credentials
IdentityProvider ->> User : Redirect to App With Authorization Code
User ->> App : Requests Page, Has Authorization Code
App ->> FusionAuth : Calls Complete Login<br/>With Code And Redirect URI
FusionAuth ->> IdentityProvider : Exchanges Code And<br/>Redirect URI For Provider Token
IdentityProvider ->> FusionAuth : Returns Provider Token
FusionAuth ->> FusionAuth : Stores Provivider Token, Calls Lambda, Creates User And Registrations (If Needed), Generates FusionAuth Tokens
FusionAuth ->> App : Return FusionAuth Tokens
App ->> App : Create Session Or<br/>Otherwise Log User In
Note over User, IdentityProvider: User Is Logged In And App Can Proceed<br/>Delivering Data And Functionality
Although this looks complex, the user only sees a few screens, such as the FusionAuth login screen, the provider login screen, and your application.
Azure AD is Microsoft Entra ID. But the usage of Azure AD is common. In this document, wherever you see Azure AD, rest assured we mean Microsoft Entra ID as well.
Register a New Azure Active Directory Application
You will first need to login to the Azure Portal.
Once logged in, navigate to Azure Active Directory -> App Registrations -> New Registration to create a new Azure Active Directory Application.
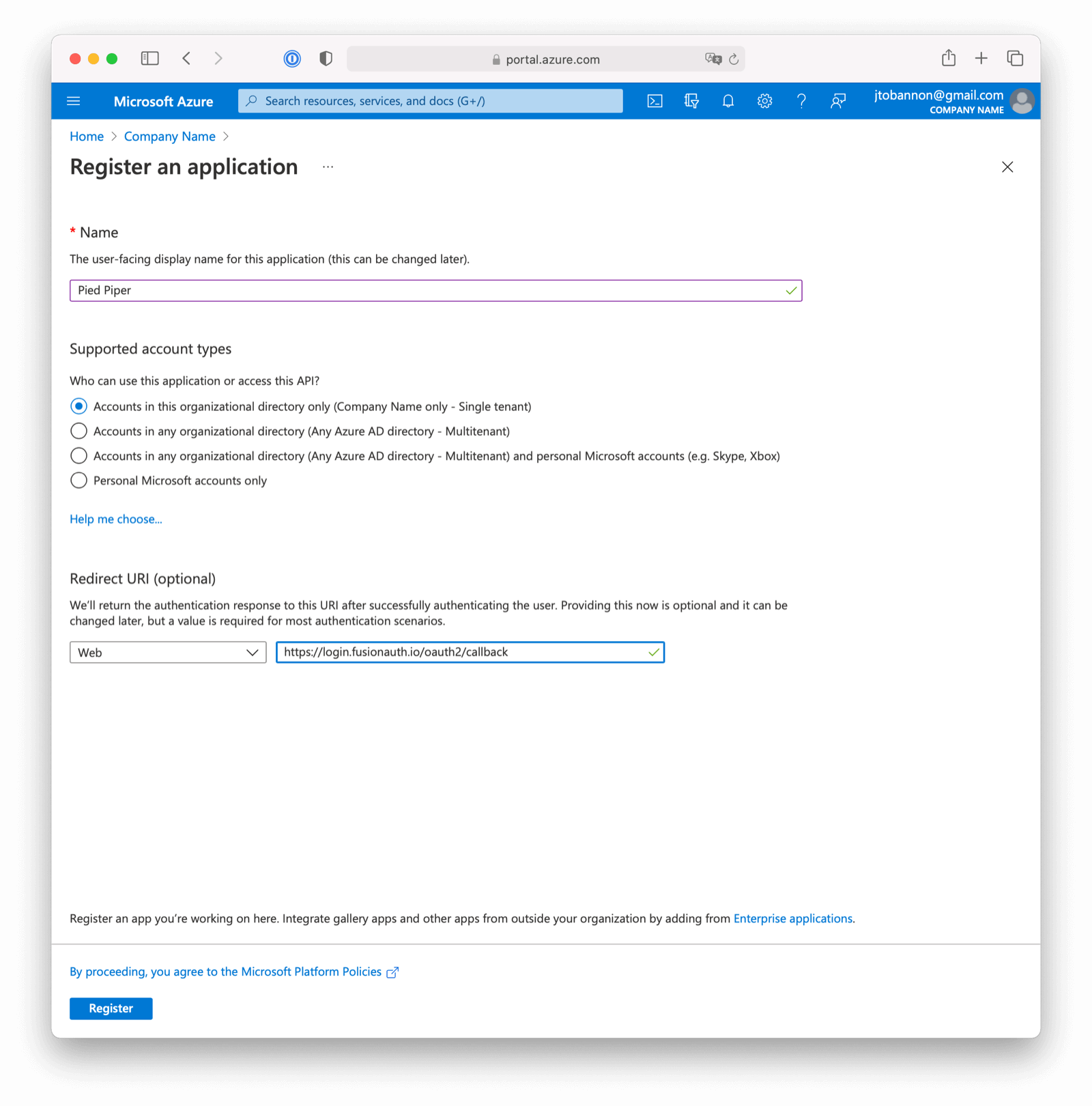
Here we have configured our application Redirect URI. If FusionAuth is running at https://login.fusionauth.io, this value should be https://login.fusionauth.io/oauth2/callback.
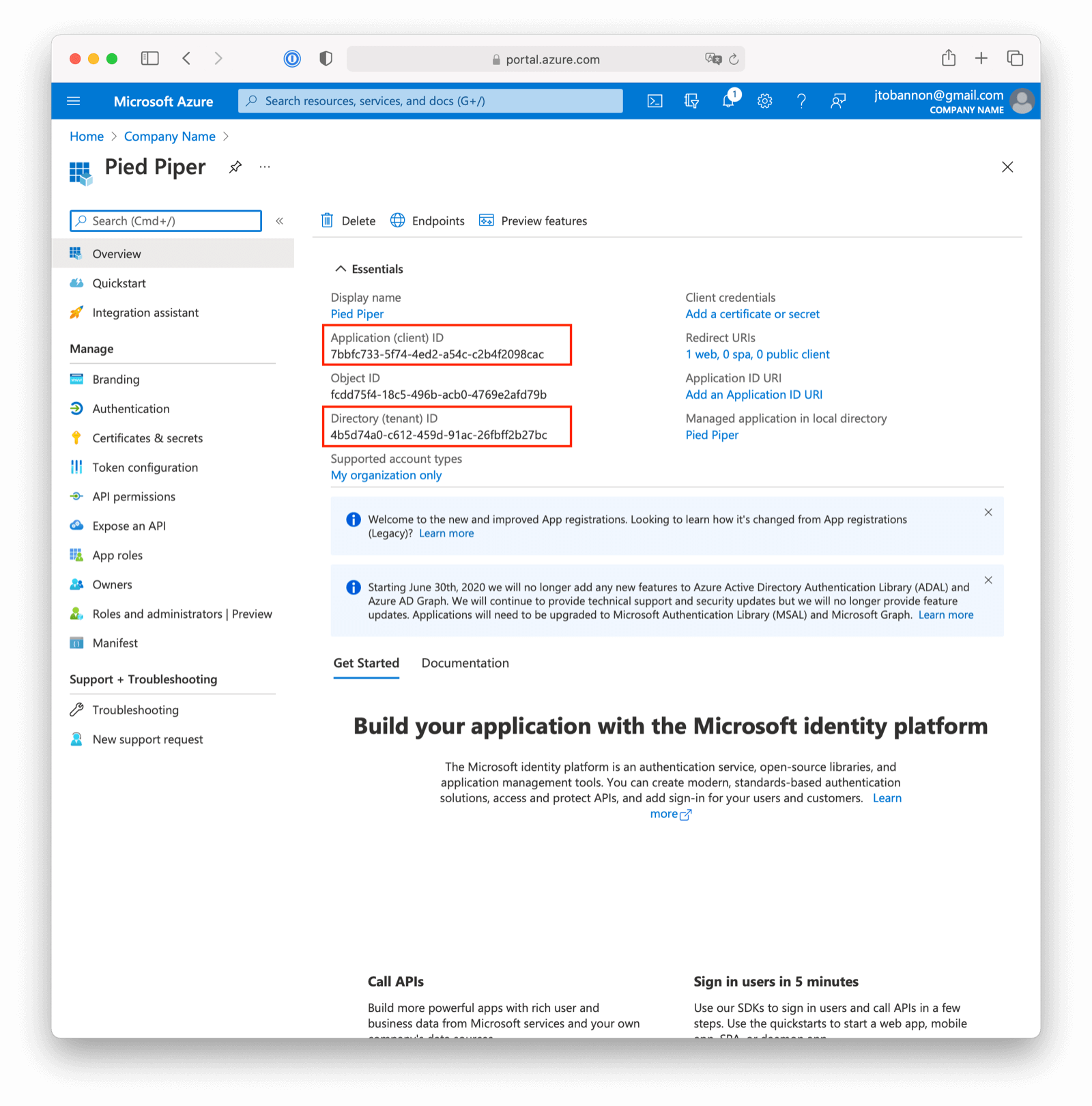
Once the application has been created, note the Application (client) ID and the Directory (tenant) ID. These will be used respectively as the Client Id value and to construct the Issuer value in your FusionAuth OpenID Connect Identity Provider configuration.
Create a New Azure Active Directory Application Secret
Navigate to Azure Active Directory -> App Registrations -> Your Application -> Certificates & secrets -> New client secret to create a new Azure Active Directory Application Client Secret.
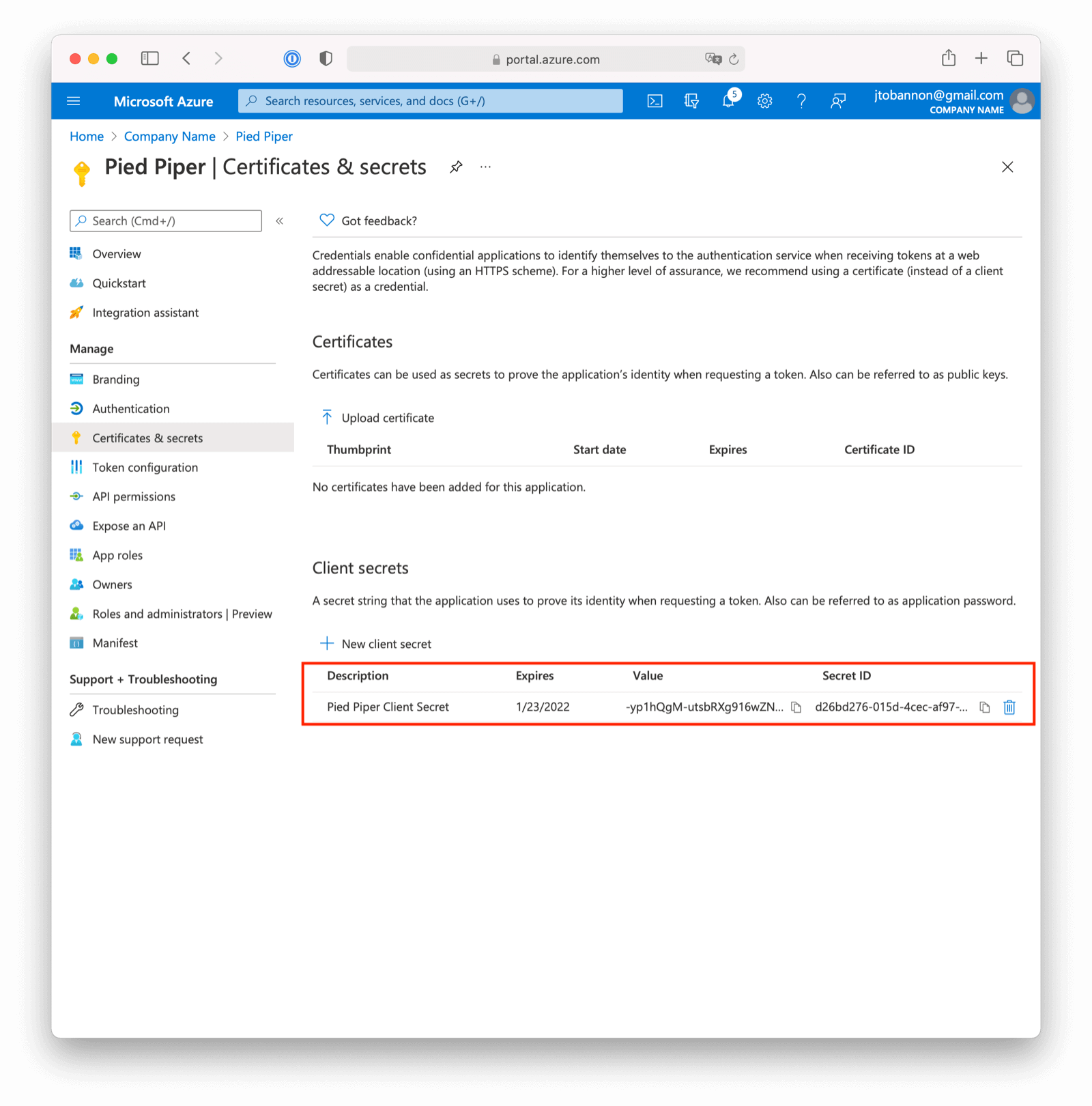
Note the VALUE of the created client secret. This will be used as the Client secret value in your FusionAuth OpenID Connect Identity Provider configuration.
Configure a New FusionAuth OpenID Connect Identity Provider
To create an Azure AD Identity Provider return to FusionAuth and navigate to Settings -> Identity Providers and click Add provider and select OpenID Connect from the dialog.
This will take you to the Add OpenID Connect panel, and you’ll fill out the required fields.
You will need to set the Client authentication method to HTTP Basic authentication (client_secret_basic).
Client Id and Client secret values reference the previously noted Azure AD Application’s Application (client) ID, client secret VALUE. The Redirect URL is read only and generated for you based upon the URL of FusionAuth, this value should match the one you configured in your Azure application.
Azure AD has implemented a well-known configuration endpoint, so FusionAuth will be able to discover the necessary endpoints using a discovery document by entering the Microsoft Authority URL in the Issuer field. To see the Issuer field, you may need to toggle Discover endpoints .
The Microsoft URL may differ across national clouds, so you will need to review the Microsoft documentation to ensure you have the correct URL for your region. For the Microsoft global Azure AD service, the URLs are as follows, where {tenantId} is the Directory (tenant) ID previously noted while creating our Azure AD Application.
- Azure AD v1
https://login.microsoftonline.com/{tenantId} - Azure AD v2
https://login.microsoftonline.com/{tenantId}/v2.0
You may set a Reconcile lambda to map attributes from the JWT provided by Azure AD to the FusionAuth user or registration. This is optional. Learn more about lambdas. You may also modify the Button text or Button logo if desired.
You will need to specify openid as a Scope .
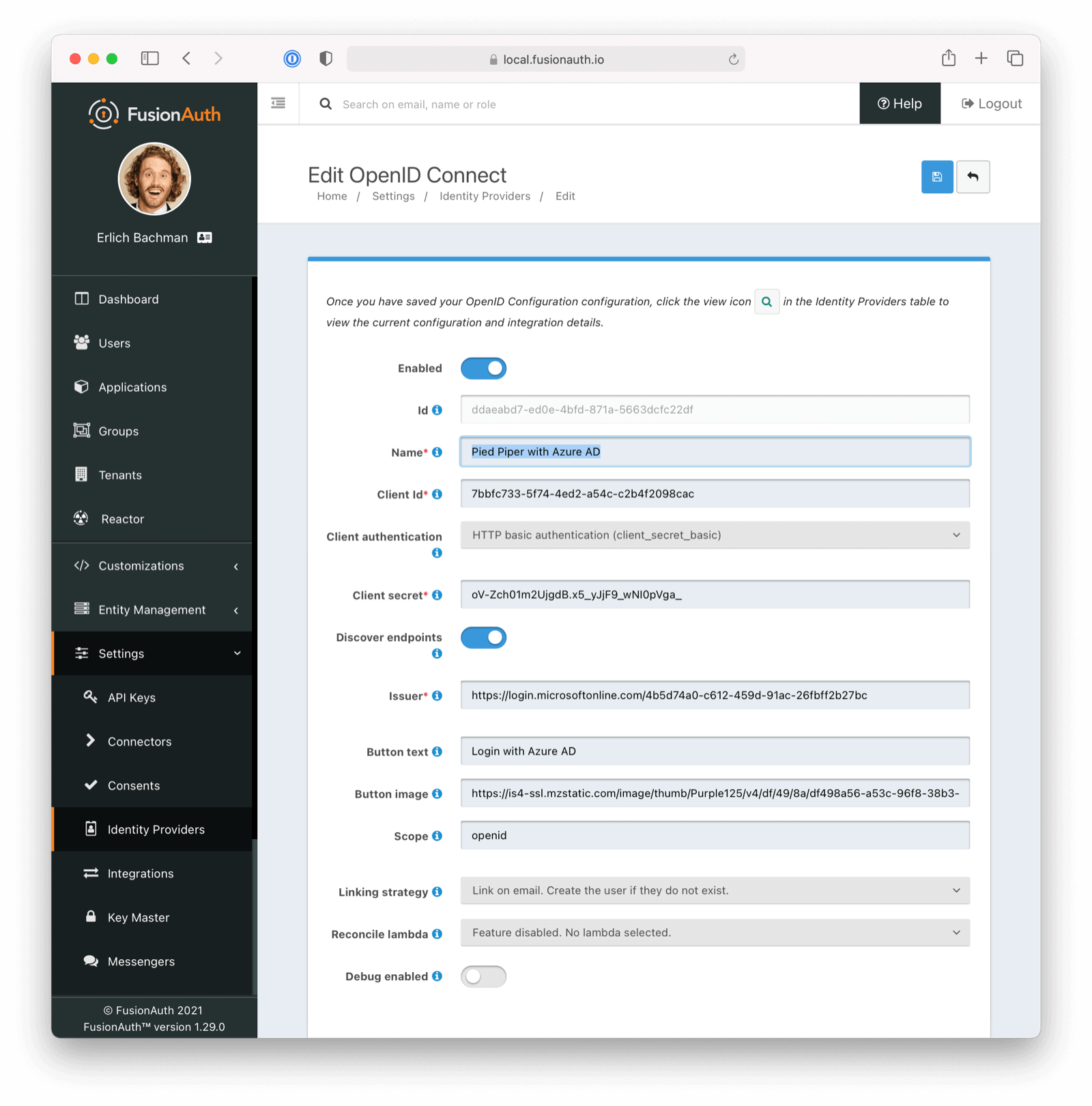
Scroll down and make sure you enable this Identity Provider for your application. In the following screenshot you will see that we have enabled this login provider for the Pied Piper application and enabled Create registration.
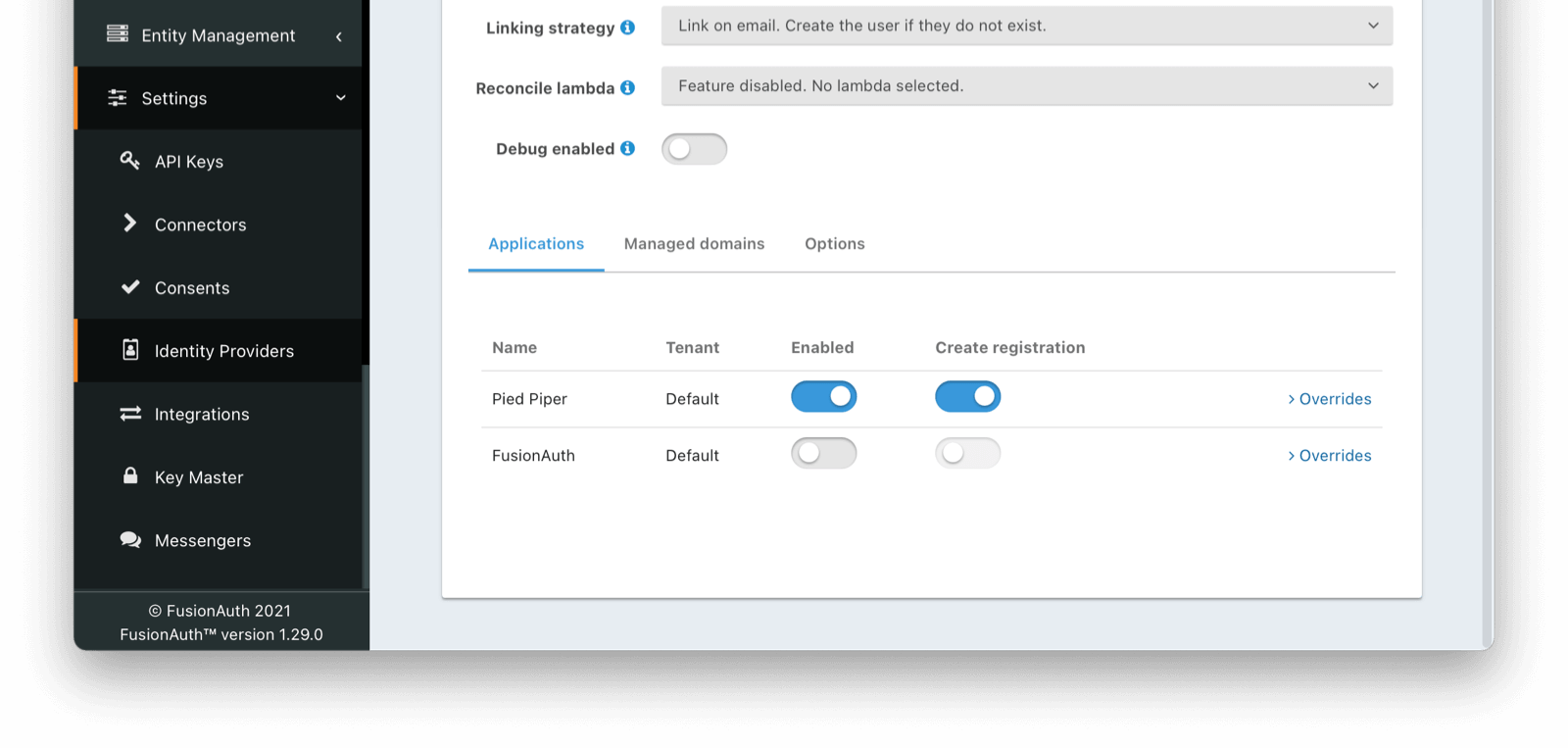
That’s it, now the Login with Azure AD button will show up on the login page of our Pied Piper application.
Form Fields
TenantAvailable since 1.62.0Global identity provider is selected on the previous page, this field does not display.Client IdrequiredClient secretrequiredButton textLogin with Azure but it may be modified to your preference.
Linking strategyDefaults to Link on email. Create the user if they do not existReconcile lambdaDebug enabledDefaults to false
