Overview#
Available since 1.23.0
Adding a Sign in with LinkedIn button to FusionAuth is simple, and this guide will walk you through the steps necessary to collect the credentials from LinkedIn in order to enable this Social login.
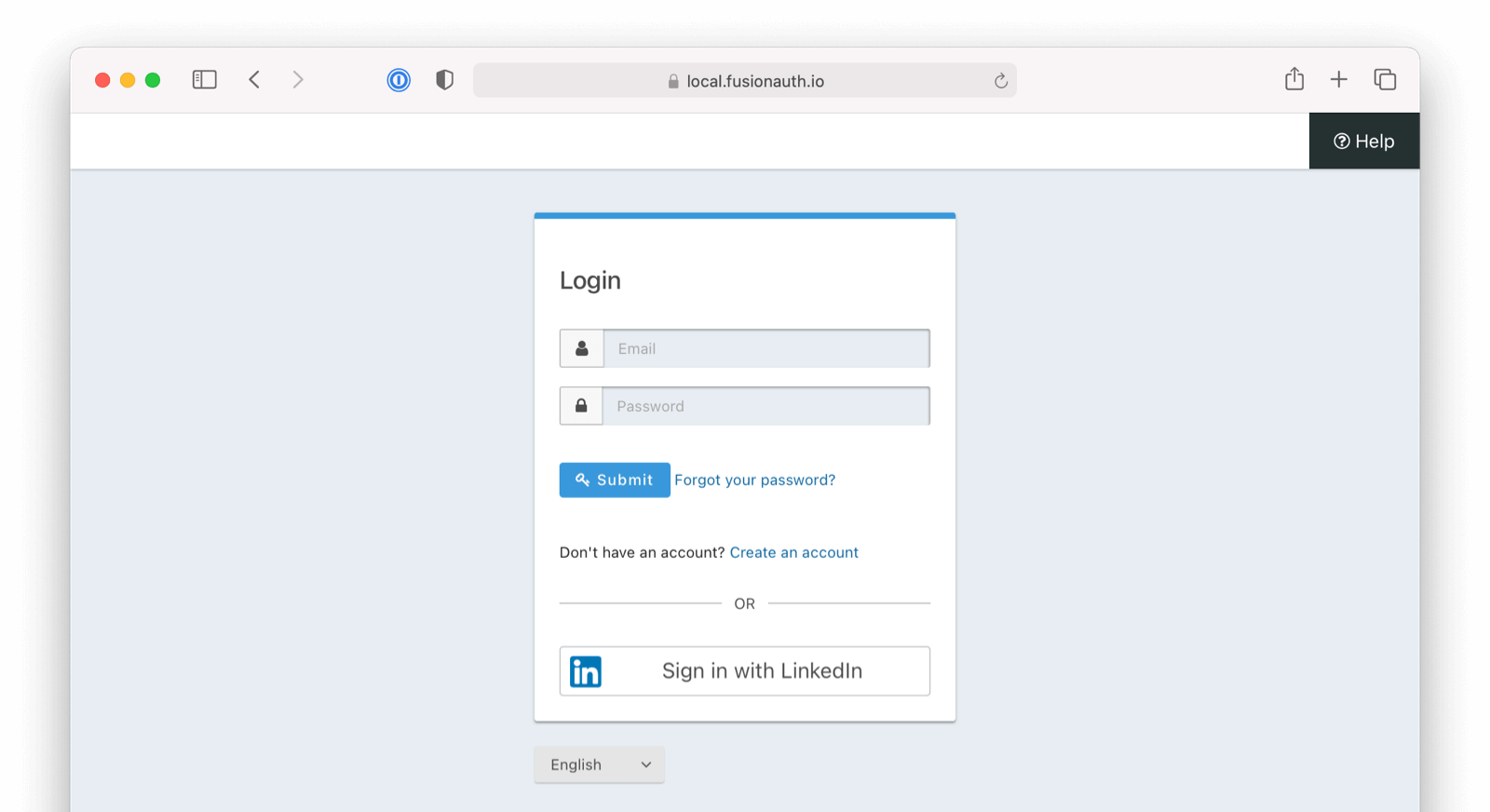
Once you have completed this configuration you will be able to enable the LinkedIn login button for one or more FusionAuth Applications. Below is an example login page with the LinkedIn Identity Provider enabled.
Here’s a diagram of the login flow between:
- the user
- your application
- FusionAuth and
- a remote identity provider
sequenceDiagram
participant User as User/Browser
participant App
participant FusionAuth
participant IdentityProvider as Provider
User ->> App : View Initial Page<br/>Click Login
App ->> User : Displays Login Page<br/>Including Link To 'Login With Provider'
User ->> App : Clicks On 'Login With Provider'
App ->> User : Redirect To Provider Authorization URL
User ->> IdentityProvider : Enters Credentials
IdentityProvider ->> IdentityProvider : Validate Credentials
IdentityProvider ->> User : Redirect to App With Authorization Code
User ->> App : Requests Page, Has Authorization Code
App ->> FusionAuth : Calls Complete Login<br/>With Code And Redirect URI
FusionAuth ->> IdentityProvider : Exchanges Code And<br/>Redirect URI For Provider Token
IdentityProvider ->> FusionAuth : Returns Provider Token
FusionAuth ->> FusionAuth : Stores Provivider Token, Calls Lambda, Creates User And Registrations (If Needed), Generates FusionAuth Tokens
FusionAuth ->> App : Return FusionAuth Tokens
App ->> App : Create Session Or<br/>Otherwise Log User In
Note over User, IdentityProvider: User Is Logged In And App Can Proceed<br/>Delivering Data And Functionality
Although this looks complex, the user only sees a few screens, such as the FusionAuth login screen, the provider login screen, and your application.
Create A LinkedIn Account#
Ensure you have a LinkedIn login, and then navigate to the Linked In developer portal.
Optionally Create a LinkedIn App#
If you have an existing LinkedIn app which you are going to use, skip this step.
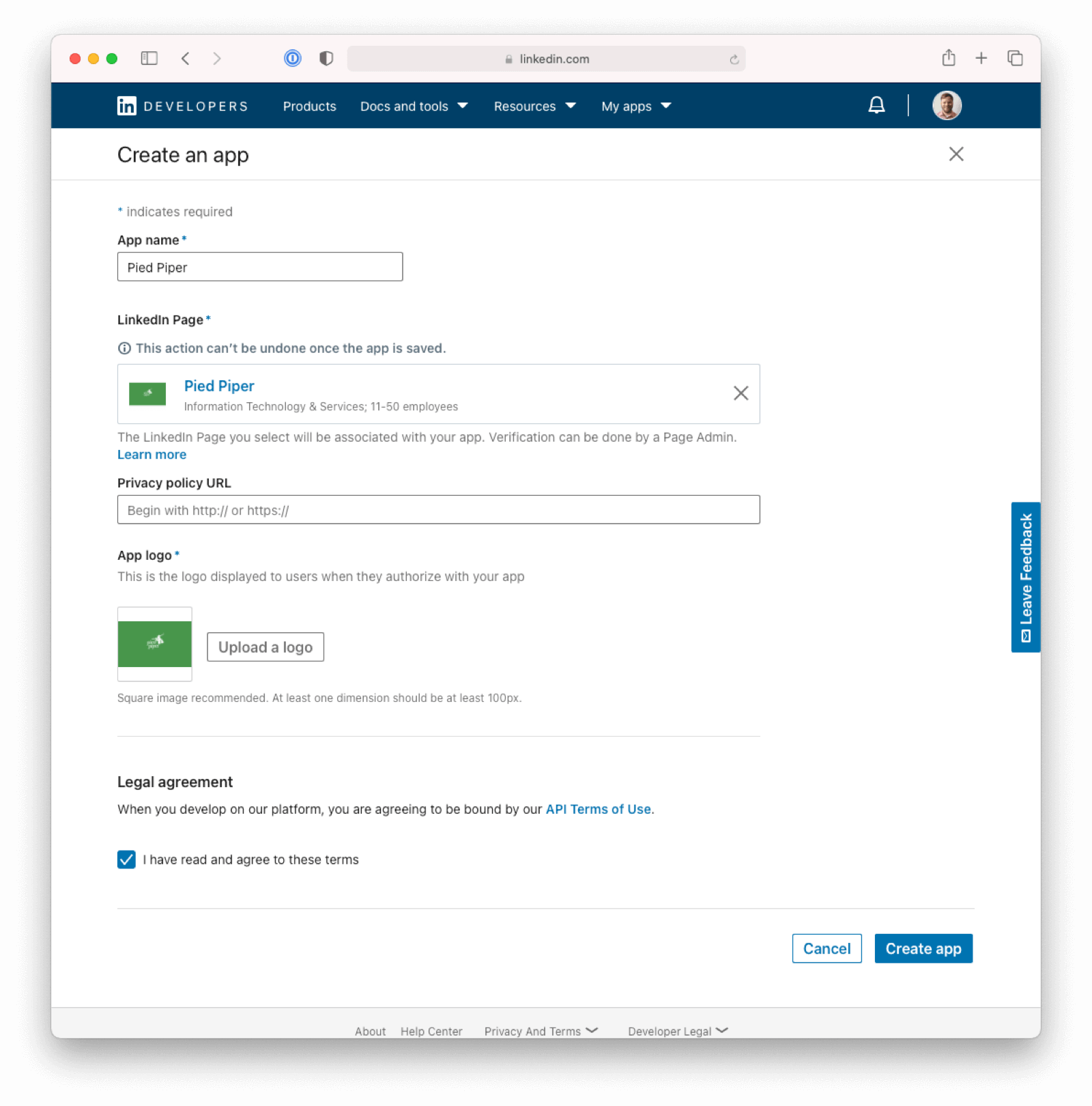
If you don’t have an existing LinkedIn app, navigate to the new application form and fill it out. In the following example I will create my first application before I can create credentials. I will call the application Pied Piper.
Grant Your App Required Permissions#
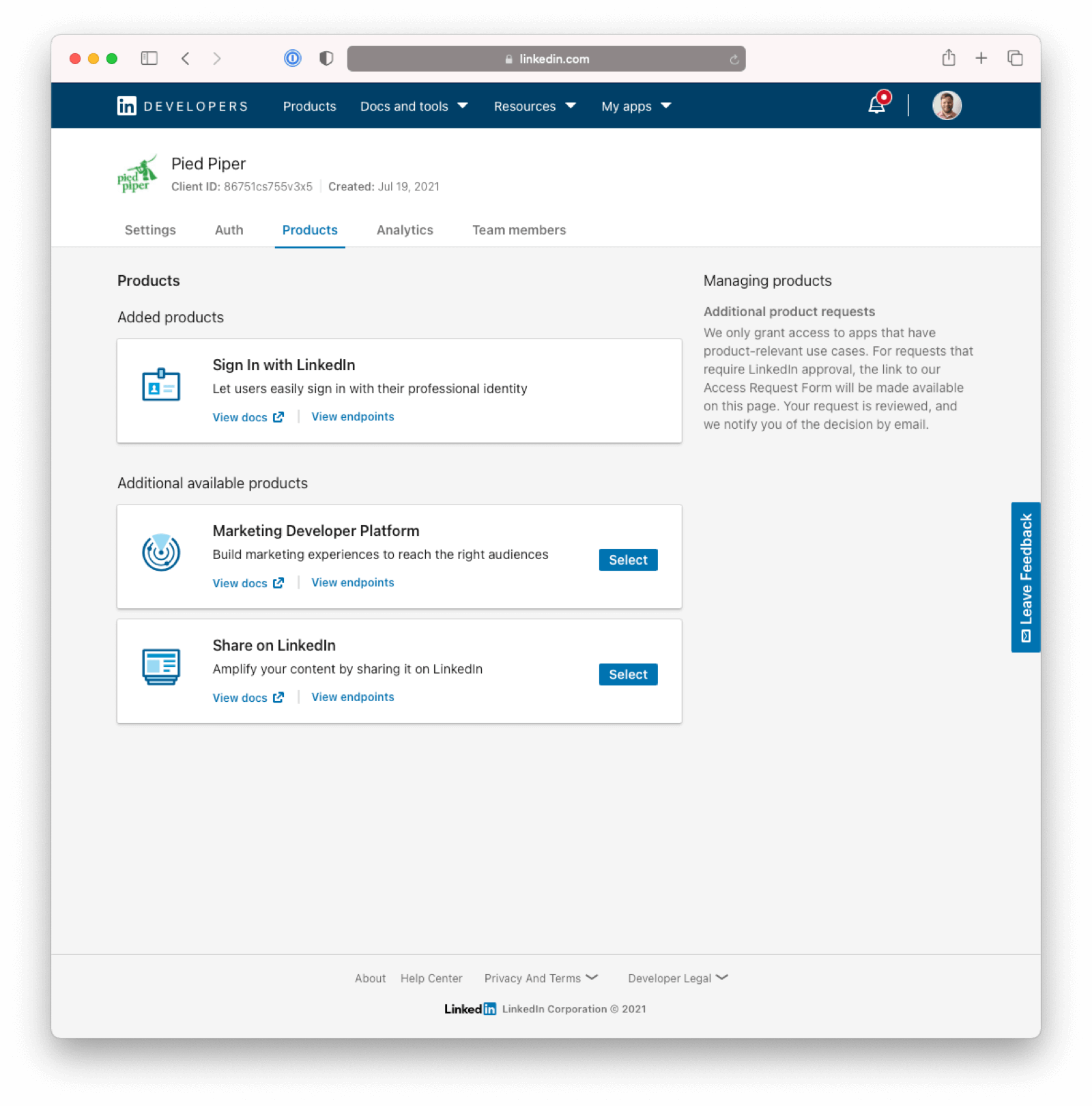
In the LinkedIn developer portal, ensure you are viewing the correct LinkedIn application by navigating to My apps -> Your Application .
If you don’t see the Products tab for your application, navigate to Products in the top level menu. This may occur if this is your first LinkedIn application.
Navigate to My apps -> Your Application -> Products . Select Sign In With LinkedIn and accept the terms.
Your application may not be immediately available. It may be reviewed for a time by the LinkedIn platform team.
Set Up Your LinkedIn App Client Credentials#
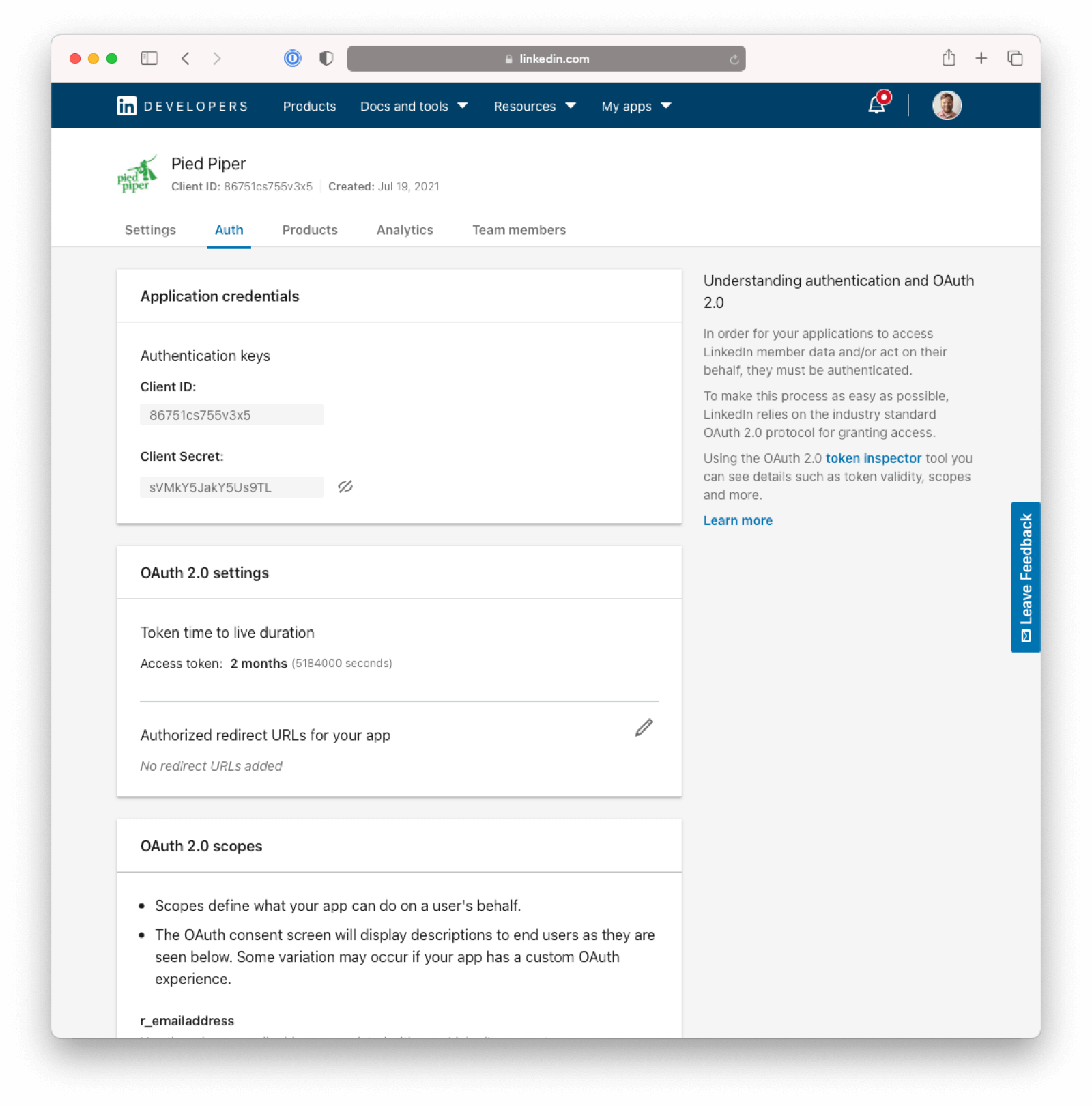
In the LinkedIn developer portal, ensure you are viewing the correct LinkedIn app by navigating to My apps -> Your Application .
View the application credentials by going to Auth -> Application credentials . Record both the Client ID and the Client Secret values.
Add your redirect URL. This value will be your FusionAuth installation hostname with the string /oauth2/callback appended. For example, if you are going to access FusionAuth at https://login.piedpiper.com then you will add https://login.piedpiper.com/oauth2/callback to the Authorized redirect URLs for your app list.
Save the setting.
You should see the following scopes in the OAuth 2.0 Scopes section:
openidprofileemail
If these scopes are not visible in the UI you may need to add them to the configuration in FusionAuth and attempt a login using the integration. The initial login should trigger LinkedIn to update the configuration visible in their UI. See Create a LinkedIn Identity Provider.
Now you have completed creating a LinkedIn App with the appropriate permissions.
LinkedIn Identity Provider Scopes#
LinkedIn has changed their API programs over time.
Depending on when you created your application in LinkedIn you may have a different set of scopes available to you. LinkedIn has an older Compliance program with different scopes that no longer registers new apps, and a newer program based on OpenID Connect.
The legacy scopes you may need to use instead are r_emailaddress for email address info and r_liteprofile or r_basicprofile for the rest of the user info. These scopes were used to call LinkedIn’s Profile API
Prior to 1.49.0 FusionAuth only supported using the legacy scopes. The new scopes openid, profile, and email are used with the UserInfo API.
If you are using these scopes you will need to upgrade to FusionAuth 1.49.0 or later.
If you do not see these scopes, you may not have added the LinkedIn product to your LinkedIn app correctly. You may also need to reload the app page or log out of LinkedIn and log in again to make sure your application has the proper permissions.
Create a LinkedIn Identity Provider#
The last step will be to create a LinkedIn Identity Provider in FusionAuth. Log in to the FusionAuth administrative user interface. Create an Identity Provider by navigating to Settings -> Identity Providers and click on the menu on the upper right and select Add LinkedIn.
This will take you to the Add LinkedIn screen, and you’ll fill out the Client Id and Client secret required fields with the values previously recorded. The button text is also required, but it will be defaulted to Sign in with LinkedIn. You may optionally modify this value.
To enable this identity provider for an application, find your application name in the Applications configuration section at the bottom of this panel. You will always see the FusionAuth application, this application represents the FusionAuth administrative user interface. If you wish to be able to log into FusionAuth with this provider, you may enable this application.
In the following screenshot you will see that we have enabled this login provider for the Pied Piper application and enabled Create registration. Enabling create registration means that a user does not need to be manually registered for the application prior to using this login provider.
For example, when a new user attempts to log into Pied Piper using LinkedIn, if their user does not exist in FusionAuth it will be created dynamically, and if the Create registration toggle has been enabled, the user will also be registered for Pied Piper and assigned any default roles assigned by the application.
If you do not wish to automatically provision a user for this application when logging in with LinkedIn, leave Create registration off. You will need to manually register a user for this application before they may Sign in with LinkedIn.
That's it, now the Sign in with LinkedIn button will show up on the login page for the Pied Piper application.
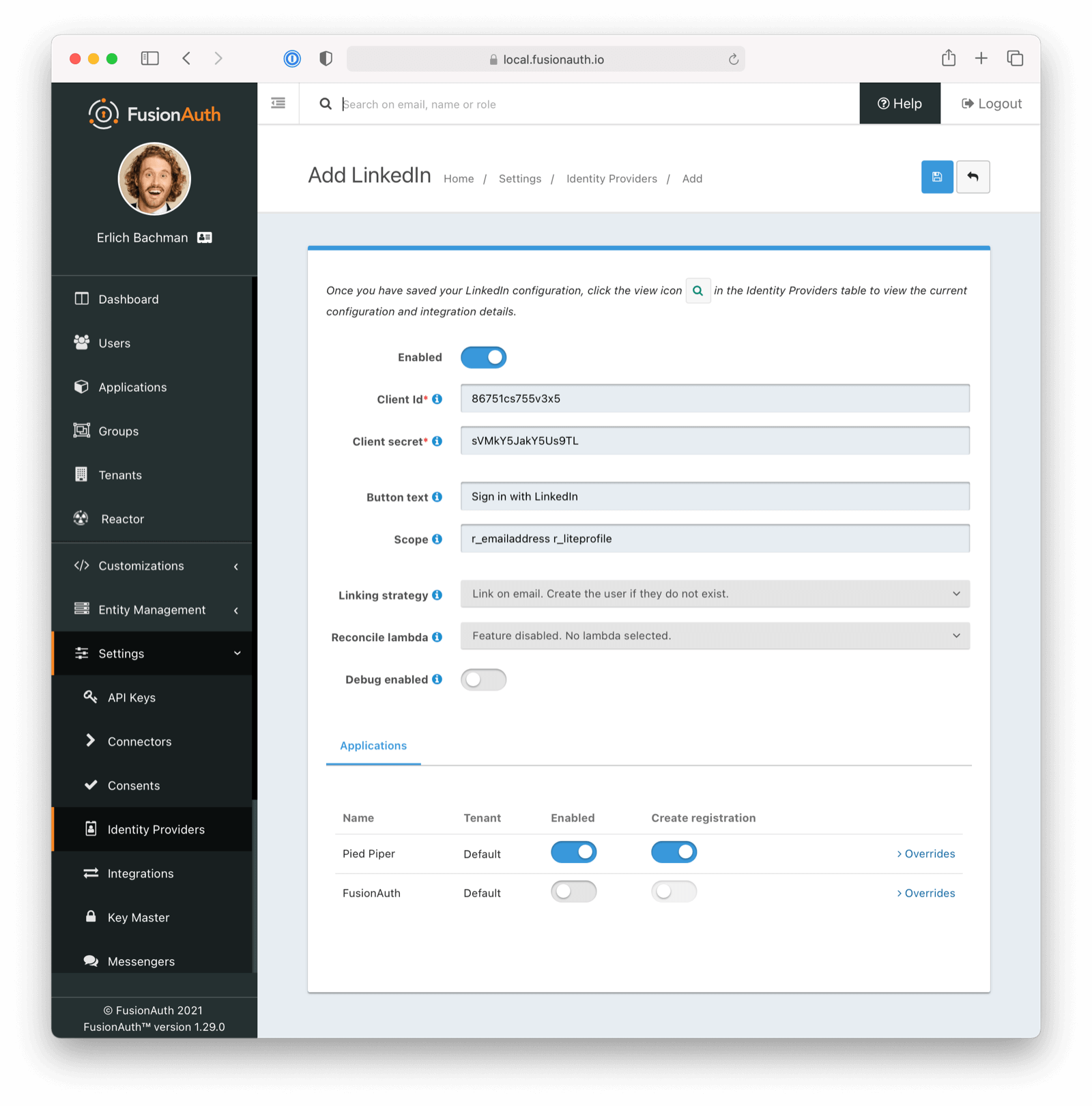
Form Fields#
IdAvailable since 1.61.0An optional UUID. When this value is omitted a unique Id will be generated automatically.
TenantAvailable since 1.62.0The tenant to which this identity provider belongs. This field only displays when the user selects a specific tenant on the previous page. When Global identity provider is selected on the previous page, this field does not display.
NamerequiredAvailable since 1.61.0A unique name to identify the identity provider. This name is for display purposes only and it can be modified later if desired.
Client IdrequiredThe LinkedIn Client Id found in your LinkedIn credentials settings in the Client ID field.
Client secretrequiredThe LinkedIn Client Secret found in your LinkedIn credentials settings in the Client secret field.
Button textrequiredThe text to be displayed in the button on the login form. This value defaults to Sign in with LinkedIn but it may be modified to your preference.
ScopeThis optional field defines the scope you’re requesting from the user during login The default scopes are the suggested values. See the LinkedIn documentation for further information.
Linking strategyDefaults to Link on email. Create the user if they do not exist.The linking strategy for LinkedIn. See Linking Strategies for more.
When the Linking strategy is equal to Link on email. Create the user if they do not exist. or Link on email. Do not create the user if they do not exist. and the email_verified claim is present on the response from LinkedIn and the value is false a link will not be established and an error will be returned indicating a link cannot be established using an unverified email address.
Reconcile lambdaA lambda may be utilized to map custom claims returned from LinkedIn. See the LinkedIn Reconcile lambda documentation for more details.
To configure a lambda, navigate to Customizations -> Lambdas .
Debug enabledDefaults to falseEnable debug to create an event log to assist you in debugging integration errors.
Building Your Own Integration#
If you are building your own login experience, you’ll want to start the identity provider flow yourself and then complete the login.
You might do this if you are using the Login API rather than using the hosted FusionAuth login pages. Here’s a diagram illustrating this login flow:
sequenceDiagram
participant User as User/Browser
participant App
participant FusionAuth
participant IdentityProvider as Provider
User ->> App : View Initial Page<br/>Click Login
App ->> User : Displays Login Page<br/>Including Link To 'Login With Provider'
User ->> App : Clicks On 'Login With Provider'
App ->> User : Redirect To Provider Authorization URL
User ->> IdentityProvider : Enters Credentials
IdentityProvider ->> IdentityProvider : Validate Credentials
IdentityProvider ->> User : Redirect to App With Authorization Code
User ->> App : Requests Page, Has Authorization Code
App ->> FusionAuth : Calls Complete Login<br/>With Code And Redirect URI
FusionAuth ->> IdentityProvider : Exchanges Code And<br/>Redirect URI For Provider Token
IdentityProvider ->> FusionAuth : Returns Provider Token
FusionAuth ->> FusionAuth : Stores Provider Token, Calls Lambda, Creates User And Registrations (If Needed), Generates FusionAuth Tokens
FusionAuth ->> App : Return FusionAuth Tokens
App ->> App : Create Session Or<br/>Otherwise Log User In
Note over User, IdentityProvider: User Is Logged In And App Can Proceed<br/>Delivering Data And Functionality
If you require a refresh token after completing the login, ensure Enable JWT Refresh is true in the application configuration. This is found in the administrative user interface by navigating to Applications -> Your Application -> Security -> Login API settings .

