Self Service Account Management Overview

This feature is only available in paid plans. Please visit our pricing page to learn more.
Available since 1.26.0
Overview
FusionAuth self-service account management allows users to manage their accounts, including the ability to add Multi-factor Authentication (MFA). This documentation section covers:
- Update User Data & Password
- Add Two Factor Method - Authenticator
- Add Two Factor Method - Email
- Add Two Factor Method- SMS
- Add WebAuthn Passkey
- Customizing Account Management
- Troubleshooting
Here’s a brief video showing account management functionality.
A Note About User Images in this Documentation
Throughout this self service account management section we will use:
Richard Hendricks for any user facing actions. Imagine Richard is a user on your site, trying to enable MFA for his account, or update his profile data.

Erlich Bachman for any admin facing actions. Imagine Erlich is you or a customer service rep at your company.

Finding the Self Service Page
To view the account and self service pages, login as an admin and navigate to Applications and click on the icon to view the application details.
From here copy and paste the account URL into a browser. Use a different browser than the one you are using to access the FusionAuth administrative user interface, or use your browser in incognito mode.
In a real world application this link would be part of the navigation for your application.
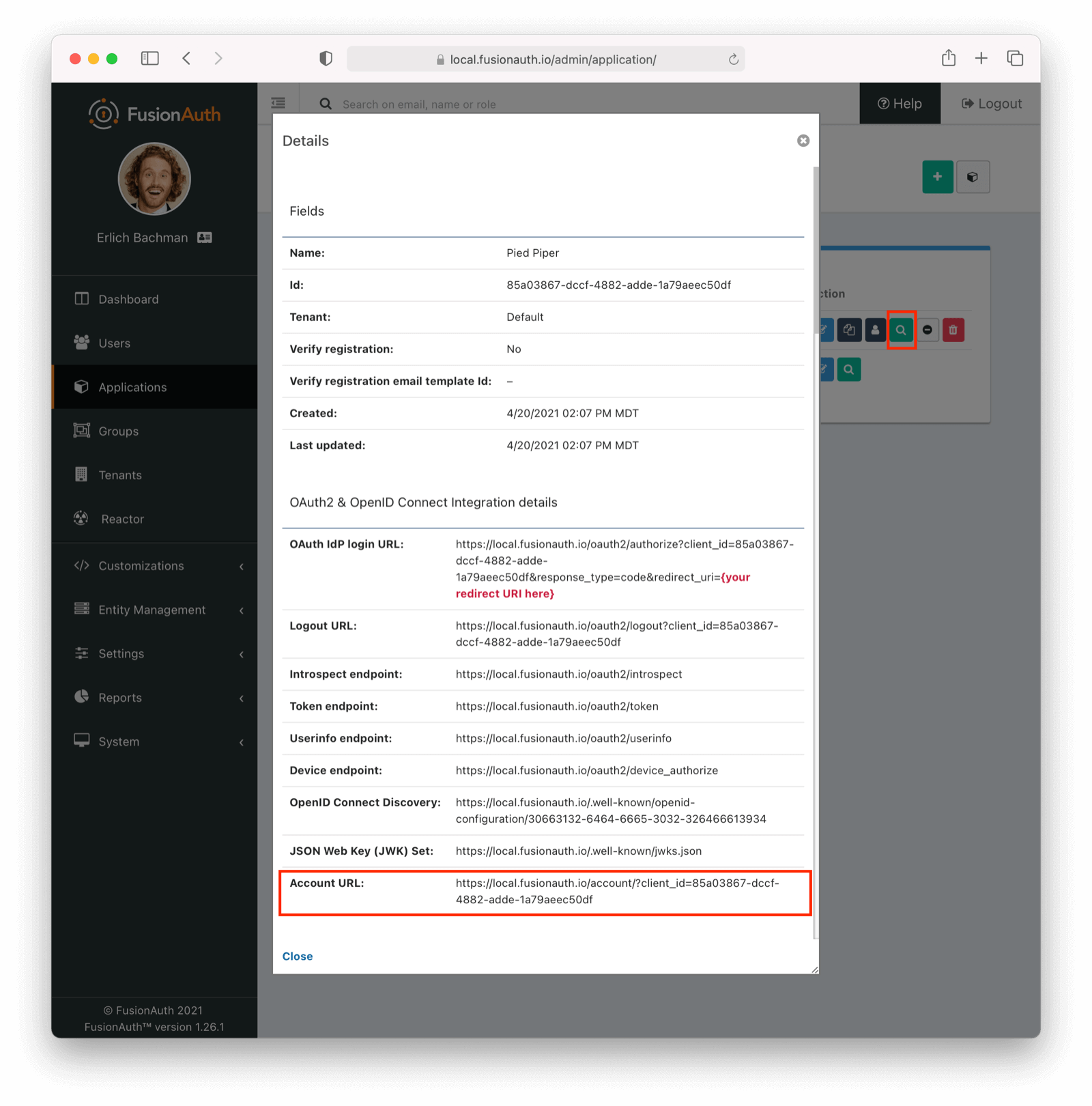
Account Home
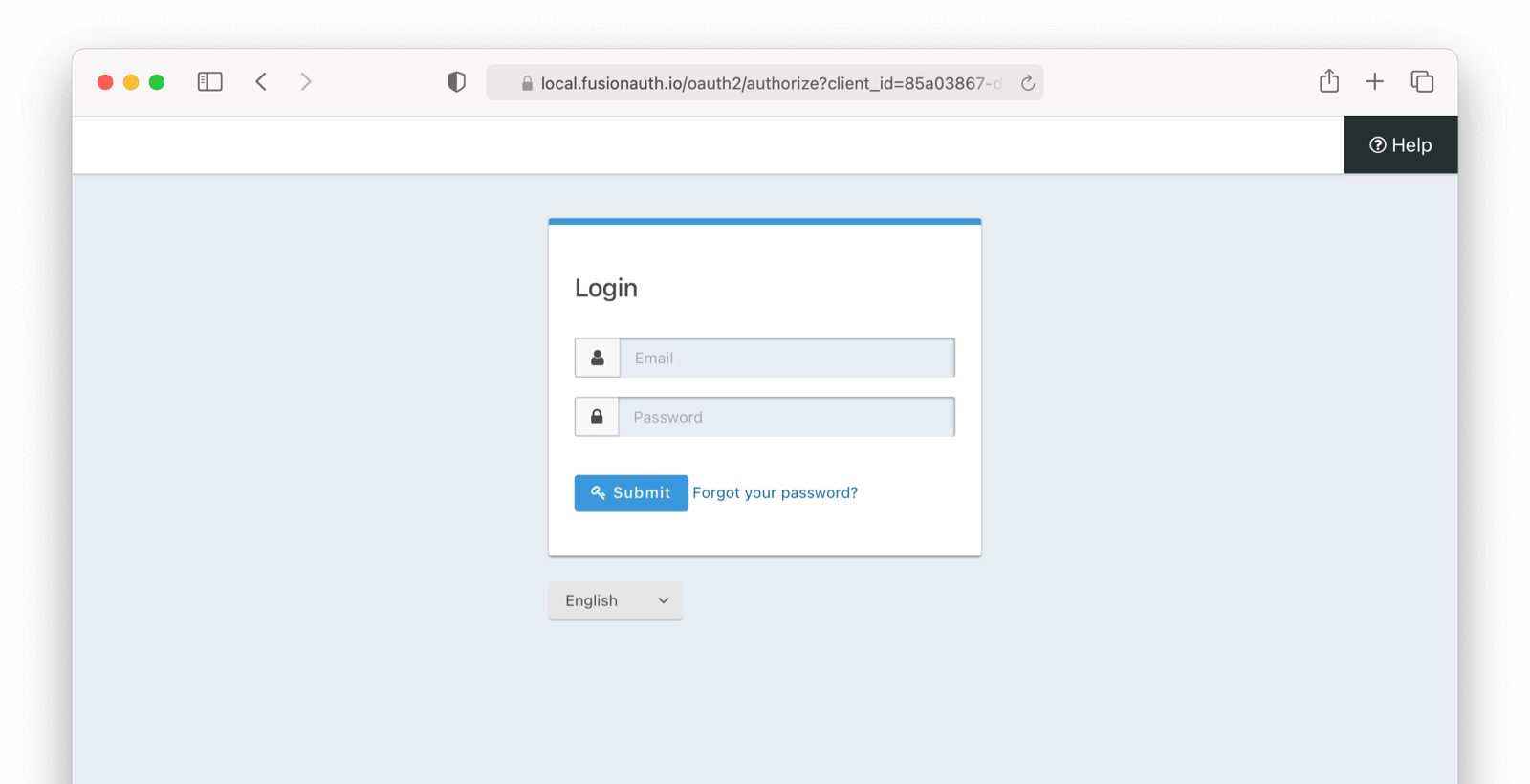
Before accessing the account you will be asked to log in. Make sure the user you log in with is registered for this application.
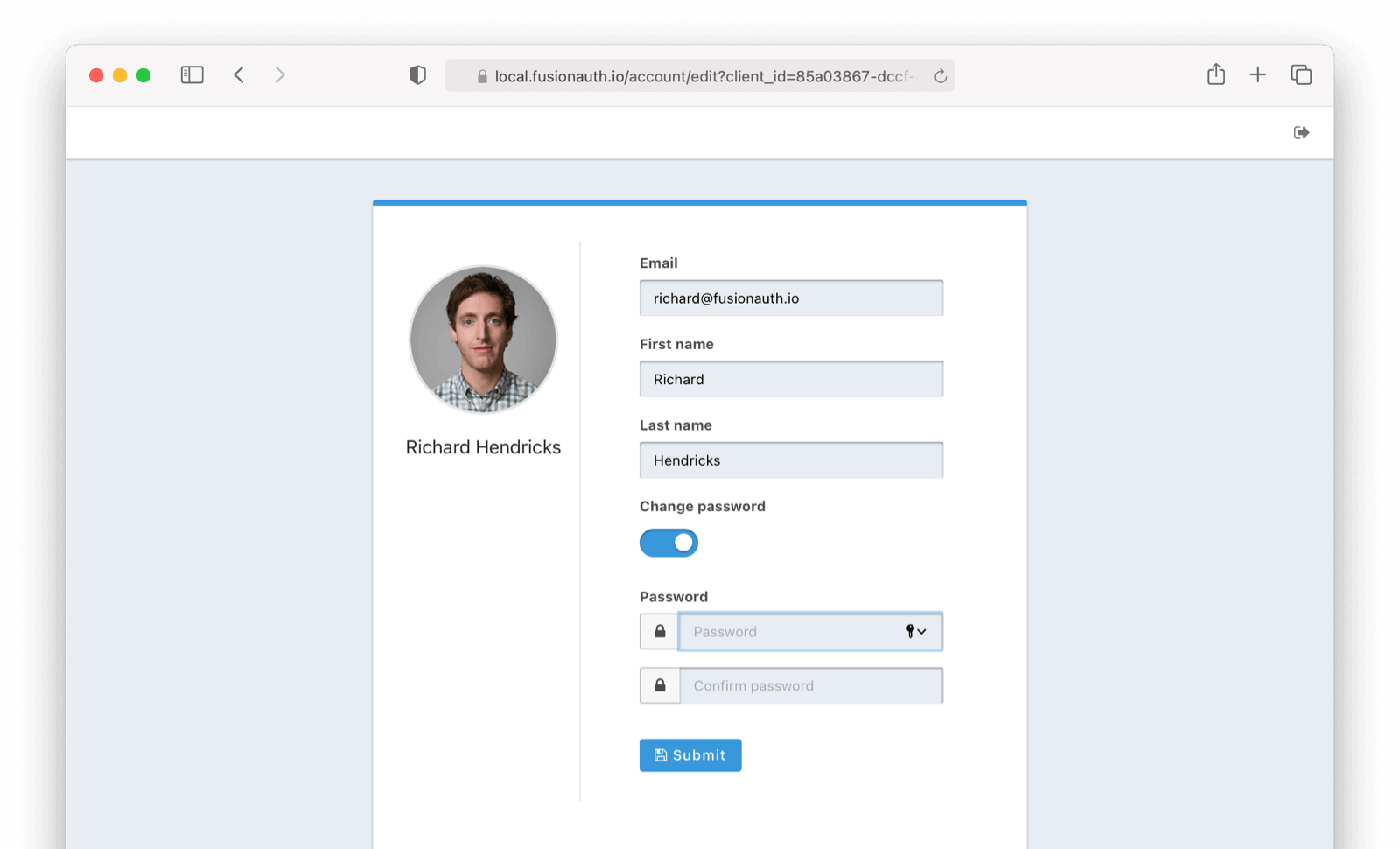
Update User Data and Password
FusionAuth Self Service Account Management allows users to easily update their user data and passwords. To adjust user profile data, click on the edit icon in the upper corner. From there a user will be presented with editable fields for user data and their password.
More information about updating user data and passwords can be found in the Updating User Data and Password section.
Enable or Disable MFA as a User
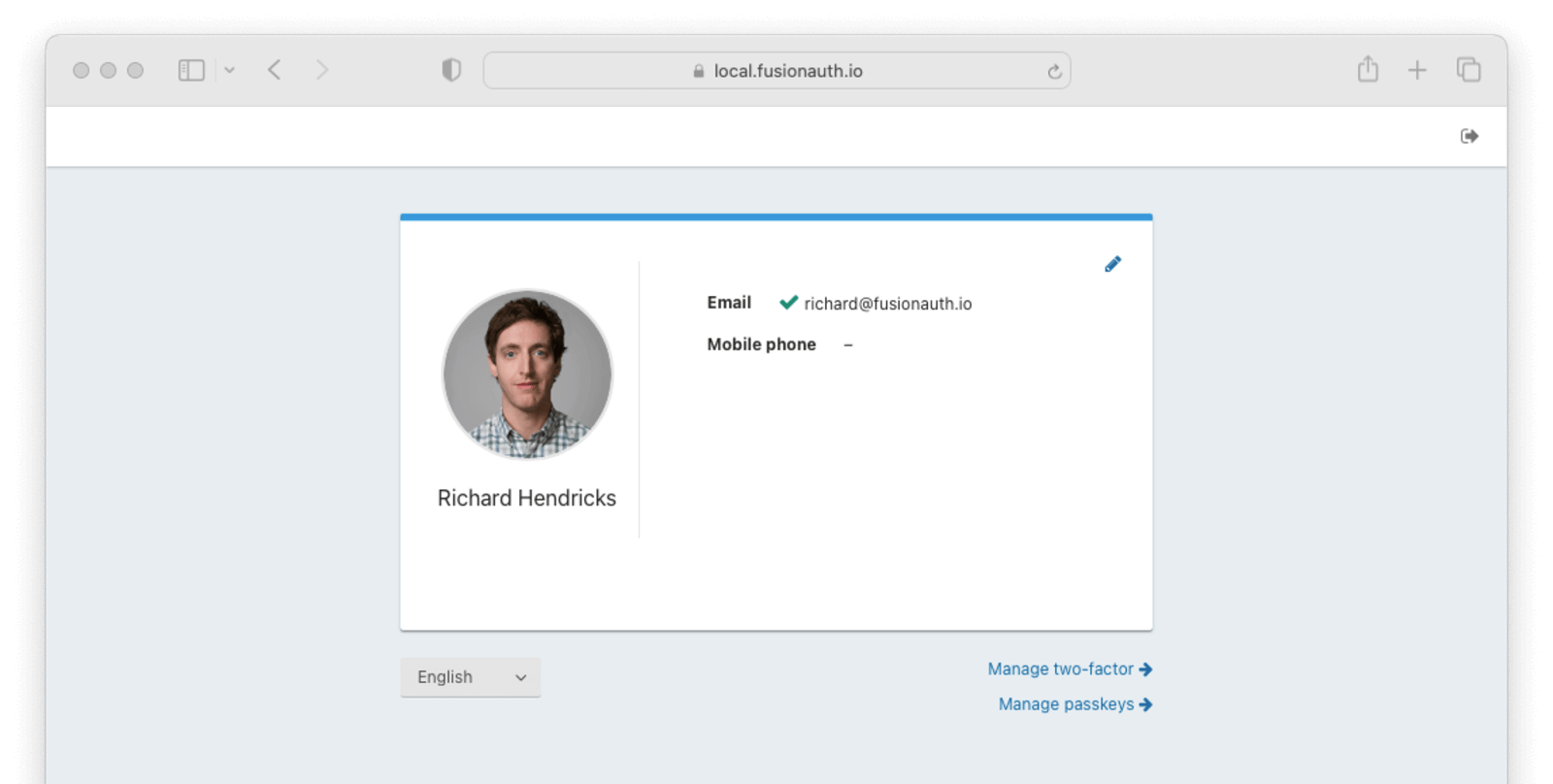
From click on Manage Two Factor
On this screen you can add Two Factor methods.
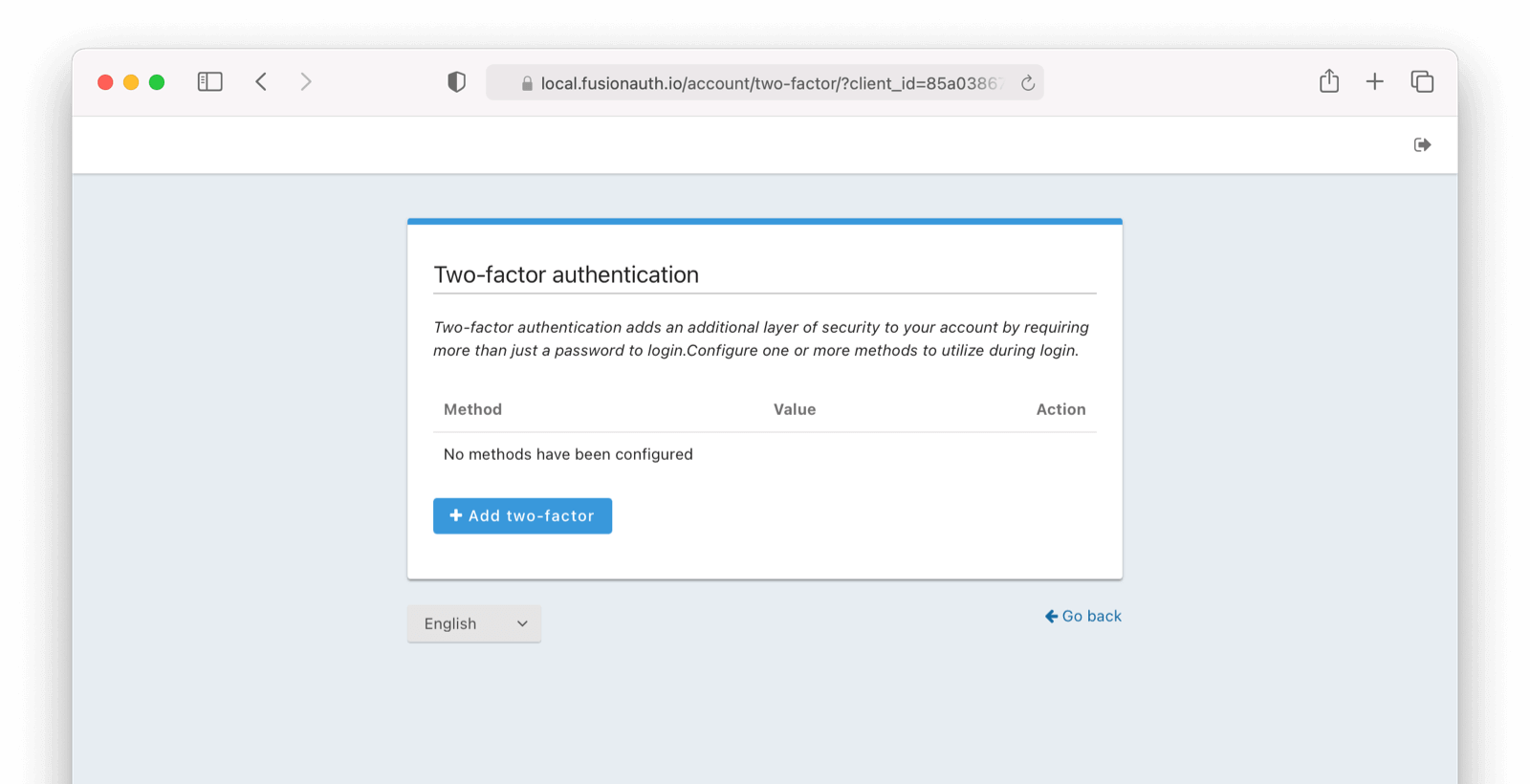
FusionAuth supports the following types of MFA:
- Authenticator
- SMS
If you are not seeing this screen, you may need additional configuration. Please see troubleshooting steps.
You can click on the links below for more about setting up each MFA method.
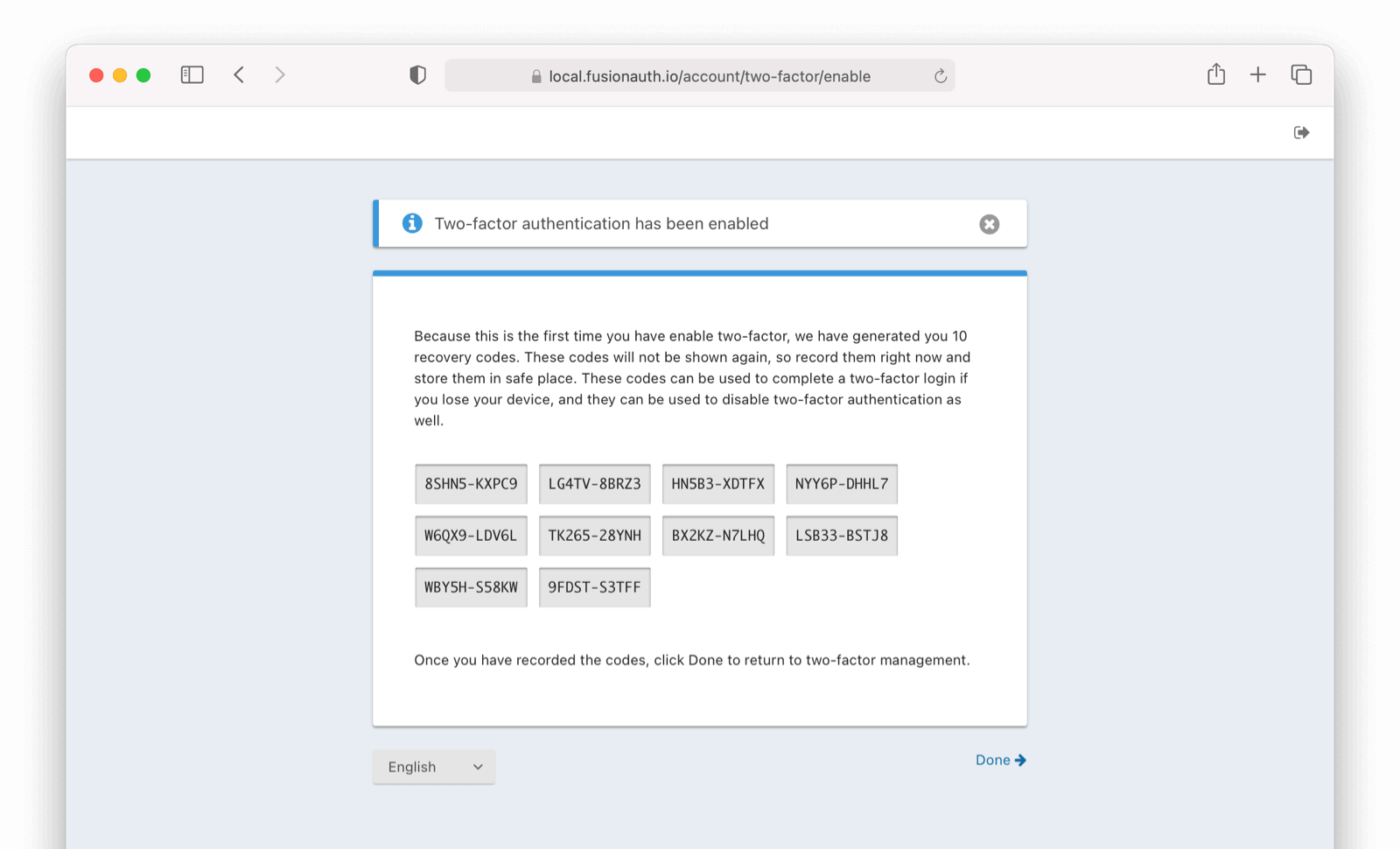
Recovery Codes
Please note that once an authenticator is enabled, users will be displayed recovery codes similar to what is shown below.
Please encourage your users to save these in a secure location, as they can be used to recover an account, should one of their second factors fail to be available. For example, if an email or sms service is “down” and users still want to use your application, or if a user loses their phone, a recovery code allows access.
Logout
If you have enabled the self-service account management functionality of FusionAuth, this has a separate session from the FusionAuth SSO session or your application session.
You must use the account logout endpoint to end this session.
To do so, redirect the user to /account/logout?client_id=... where the client_id is the application Id for which you have set up self-service account management.
This behavior is explained further in this GitHub issue.

