Generic Connector
Overview#
Generic Connectors allow you to authenticate users against or migrate them from any user datasource accessible over HTTP or TLS.
Configuration#
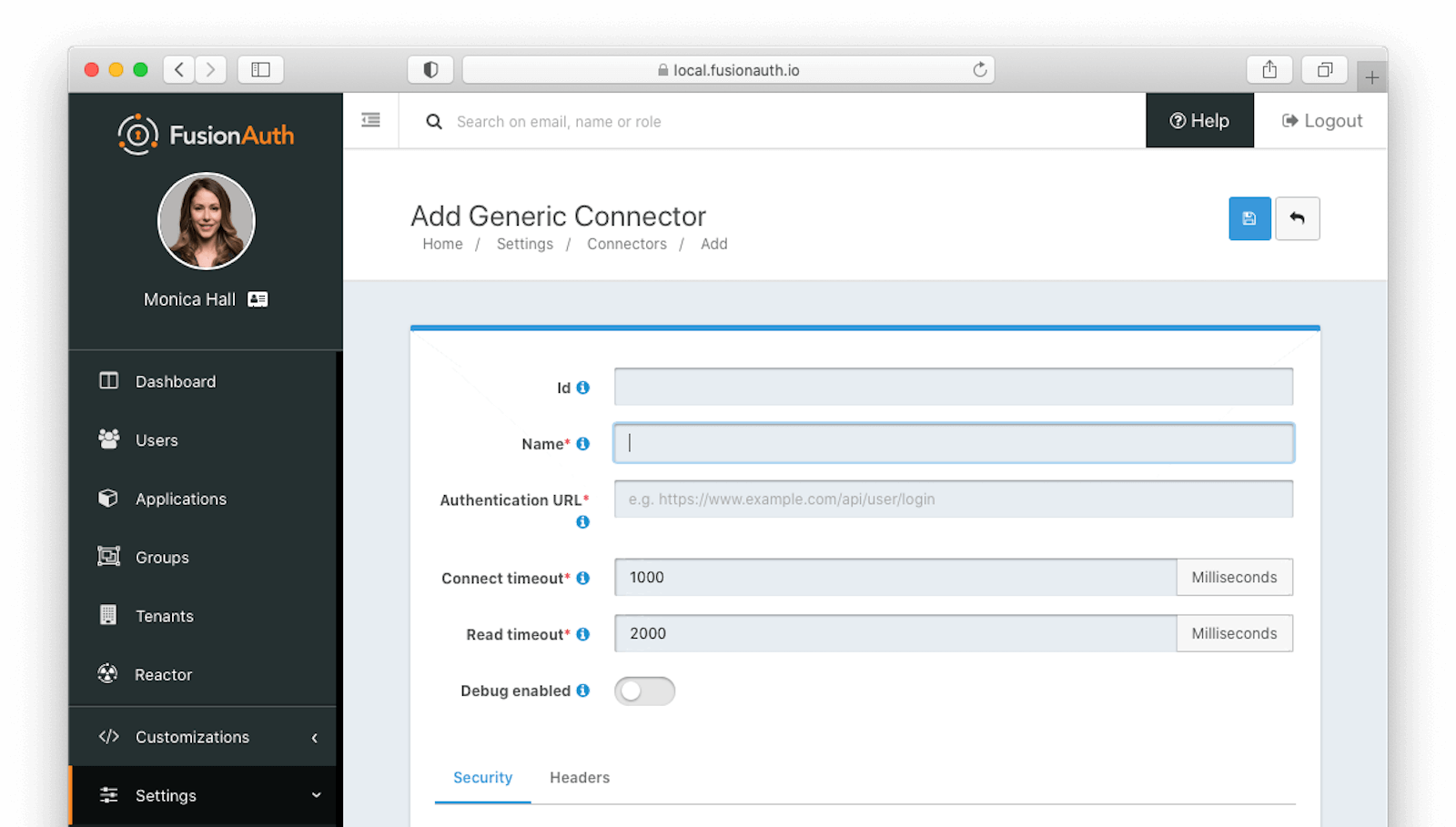
Form Fields#
IdAn optional UUID. When this value is omitted a unique Id will be generated automatically.
NamerequiredA unique name to identify the Connector. This name is for display purposes only and it can be modified later if desired.
Authentication URLrequiredThe fully qualified URL of the API endpoint. The connector will send an HTTP POST request to this URL to authenticate the user. The format returned will be identical to the Login API. See the response section for status codes accepted by FusionAuth from your connector.
Connect timeoutrequiredThe connect timeout in milliseconds, used when making the POST request.
Read timeoutrequiredThe read timeout in milliseconds, used when making the POST request.
Debug enabledEnable debug to create an event log to assist you in debugging integration errors.
Security#
The security settings may be used to require authentication in order to make the POST request to the authentication endpoint.
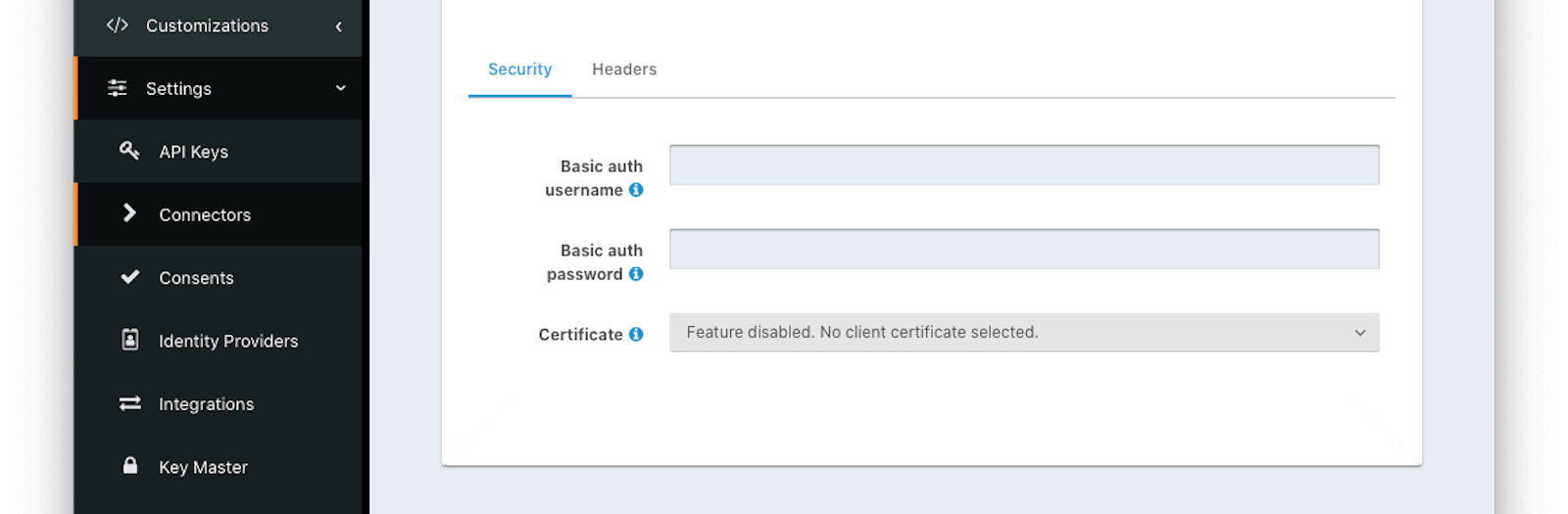
Form Fields#
Basic auth usernameThe username to be used for HTTP Basic Authentication.
Basic auth passwordThe password to be used for HTTP Basic Authentication.
CertificateThe SSL certificate to be used when connecting to the POST endpoint.
If you need to add a certificate for use with this connector, navigate to Settings -> Key Master and import a certificate. The certificate will then be shown as an option in this form control.
Headers#
You can configure arbitrary headers to be added to the HTTP POST request when making a request to the configured authentication endpoint.
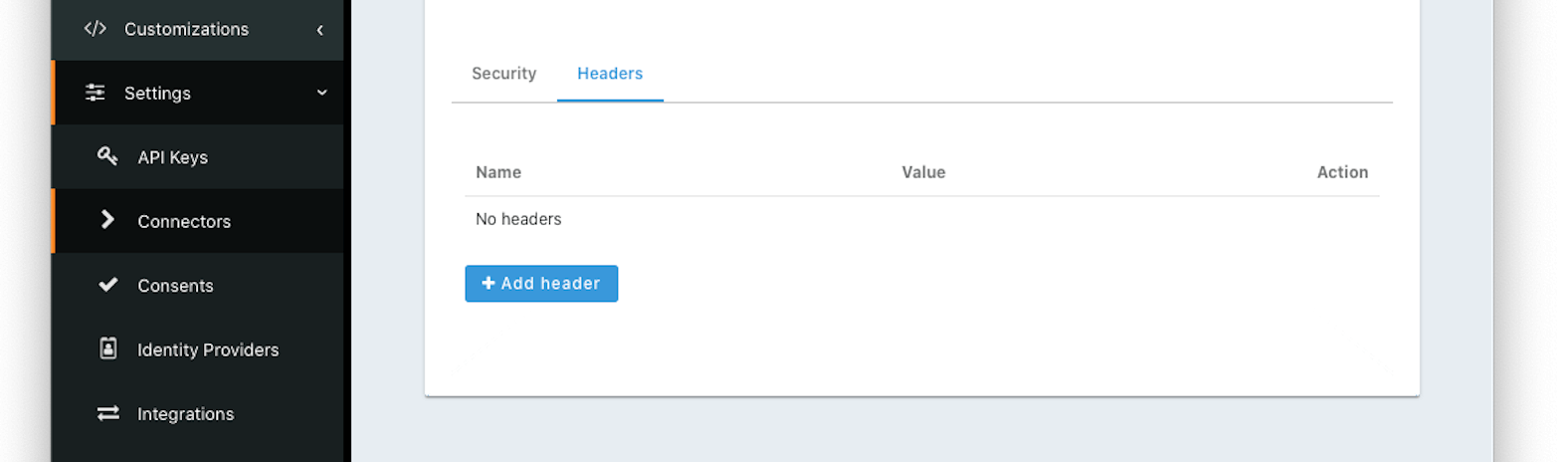
Form Fields#
NameThe name of the header to add to the HTTP request when authenticating.
ValueThe header value to add to the HTTP request when authenticating.
Using the Generic Connector#
To use a Generic Connector:
- Build a Generic Connector API endpoint in your application to expose your user data.
- Configure the Connector in Settings -> Connectors , including securing the endpoint.
- Add the Connector Policy in Tenants -> Your Tenant -> Connectors to configure to which domains the connector applies.
Request#
The request to your API endpoint will be delivered as JSON:
Example Request JSON
{
"applicationId": "10000000-0000-0002-0000-000000000001",
"eventInfo": {
"ipAddress": "127.0.0.1"
},
"loginId": "example@fusionauth.io",
"loginIdTypes": [
"email"
],
"newDevice": false,
"noJWT": false,
"password": "password"
}Your application will then look up the user and verify the correct credentials were provided. Then you can return the response.
Response#
Your API should return a valid FusionAuth user object with status code 200 if the user is found and authenticated.
While you may return any of the attributes of the user object, including nested objects such as application registrations with roles, only the required ones must be present. The only other status code FusionAuth will accept from your connector is a 404.
A valid user object must be returned with a FusionAuth compatible UUID in the user.id . This is a requirement whether you are authenticating but not migrating a user or migrating a user.
When you are authenticating but not migrating a user, the user.id must be the same across subsequent logins.
If the user cannot be authenticated, then you should return a 404.
| Code | Description |
|---|---|
| 200 | The request was successful. The response will contain a JSON body. |
| 404 | To prevent enumeration attacks, a 404 is returned for any non 200 status code returned from your connector. |
Example Successful Response JSON
{
"user": {
"active": true,
"birthDate": "1976-05-30",
"data": {
"displayName": "Johnny Boy",
"migrated": true,
"favoriteColors": [
"Red",
"Blue"
]
},
"email": "example@fusionauth.io",
"expiry": 1571786483322,
"firstName": "John",
"fullName": "John Doe",
"id": "00000000-0000-0001-0000-000000000000",
"imageUrl": "http://65.media.tumblr.com/tumblr_l7dbl0MHbU1qz50x3o1_500.png",
"lastLoginInstant": 1471786483322,
"lastName": "Doe",
"middleName": "William",
"mobilePhone": "303-555-1234",
"passwordChangeRequired": false,
"passwordLastUpdateInstant": 1471786483322,
"preferredLanguages": [
"en",
"fr"
],
"registrations": [
{
"applicationId": "10000000-0000-0002-0000-000000000001",
"data": {
"displayName": "Johnny",
"favoriteSports": [
"Football",
"Basketball"
]
},
"id": "00000000-0000-0002-0000-000000000000",
"insertInstant": 1446064706250,
"lastLoginInstant": 1456064601291,
"preferredLanguages": [
"en",
"fr"
],
"roles": [
"user",
"community_helper"
],
"username": "johnny123",
"usernameStatus": "ACTIVE",
"verified": true,
"verifiedInstant": 1698772159415
}
],
"timezone": "America/Denver",
"tenantId": "f24aca2b-ce4a-4dad-951a-c9d690e71415",
"twoFactor": {
"methods": [
{
"authenticator": {
"algorithm": "HmacSHA1",
"codeLength": 6,
"timeStep": 30
},
"id": "35VW",
"method": "authenticator"
},
{
"id": "V7SH",
"method": "sms",
"mobilePhone": "555-555-5555"
},
{
"email": "example@fusionauth.io",
"id": "7K2G",
"method": "email"
}
]
},
"usernameStatus": "ACTIVE",
"username": "johnny123",
"verified": true,
"verifiedInstant": 1698772159415
}
}Using the Generic Connector as the System of Record#
You can use this Connector as either a source of authentication or to migrate your users. In the former case, the backing database accessed via API remains the system of record (where the canonical user data exists). In the latter, the user is moved over once they have authenticated successfully one time, and FusionAuth becomes the system of record.
As documented, there are a number of differences between these two choices. However, one difference is worth emphasizing.
When you are not migrating the user and therefore using the backing database accessed via API as the system of record, the following user attributes will reset every time the user authenticates:
- Group memberships
- Application registrations
If, for instance, you were to register such a user for an application using the FusionAuth API or the administrative user interface, the next time they authenticated, they would not be registered for that application.
Since FusionAuth is not the system of record, the backing database accessed via API is the authoritative data source.
The correct way to maintain these attributes is to store them in the backing database, query them when the API is called, and deliver them as part of the User JSON object.
Security#
TLS v1.2#
The first step in securing your Generic Connector API endpoints is to ensure that they are using TLS v1.2 or higher. You should be using a web server that is configured with a certificate from a valid certificate authority and to only receive traffic from a secure connection. We also recommend that you disable all older secure protocols including SSL, TLS 1.0 and TLS 1.1.
If you need a certificate, most cloud providers offer them or you can use LetsEncrypt to generate a certificate and ensure it is always up-to-date.
Headers#
When you configure your Generic Connector API endpoint with FusionAuth, you should include a security header of some kind. There are two ways to define a security header:
- Add a Basic Authentication username and password under Security
- Define an HTTP header under the Headers tab
In either case, your Generic Connector API endpoint code should validate the security header to ensure the request is coming from FusionAuth. Here’s some example code that validates an Authorization header:
Example Generic Connector API endpoint
router.route('/fusionauth-user-api').post((req, res) => {
const authorization = req.header('Authorization');
if (authorization !== 'API-KEY') {
res.status(401).send({
'errors': [{
'code': '[notAuthorized]'
}]
});
} else {
// process the request
}
});
Certificates#
You may provide an X.509 certificate to use with your Generic Connector API endpoint. This must be an SSL certificate previously added to the Key Master. It is used to establish a TLS connection to the Generic Connector API endpoint endpoint. Use this option if FusionAuth cannot connect to your Generic Connector API endpoint without the certificate.
Providing this certificate will build a custom SSL context for requests made for the Generic Connector API endpoint. Therefore, any other JDK keystores and certificate authority chains will be bypassed for this request.
Firewalls#
In addition to using TLS and a security header, you might also want to put a firewall in front of your Generic Connector API endpoint. In most cases, this firewall will only allow traffic to your Generic Connector API endpoint that originated from your FusionAuth instance. Depending on how you are hosting your Generic Connector API endpoint, you might be able to lock down the URL for your Generic Connector API endpoint specifically. You might also leverage an API gateway or a proxy to ensure that only traffic coming from FusionAuth is routed to your Generic Connector API endpoint. The exact specifics of deploying and configuring a Firewall are outside the scope of this document, but you can consult the documentation for your proxy, API Gateway or hosting provider to determine how to manage it.
As an example, you can configure an AWS Application Load Balancer so that traffic coming from the IP address of your FusionAuth servers with a URL of https://apis.mycompany.com/fusionauth-user-api is routed through. You can then configure the Application Load Balancer so that all other traffic to that URL is rejected.
Controlling Traffic with a Proxy#
Since version 1.31.0, FusionAuth can be configured to send all outbound HTTP traffic, including that from a Generic Connector API endpoint, through a proxy. This allows you examine any messages sent from FusionAuth. You can audit them, only allow connections to certain hosts, or otherwise modify them.
To configure a proxy for FusionAuth outbound traffic, use the proxy.* configuration options.
Performance Considerations#
Enabled Connectors are in the critical path of the login experience and therefore should have low latency.
Set a low timeout; under one second is ideal. Increasing the timeout can result in resource starvation in FusionAuth, as more and more resources are spent on slow requests.
Here are some things to do to improve performance of your Generic Connector.
Network Connection#
There are three phases of the Connector network connection, from FusionAuth connector to the API endpoint:
- Initial connection to the API endpoint
- First byte read from the connection
- Response complete and returned from the API endpoint
The first two have configurable timeouts, the Connect timeout and the Read timeout fields. For Connect timeout , if the timeout expires before the connection can be established, the login fails. For Read timeout , if the timeout expires before there is data available to be read, the login fails. The default values for these timeouts are typically adequate, but you may want to tune them if there is resource contention on your server.
However, neither timeout prevents the HTTP request from taking as long as it needs to in order to respond once the API endpoint has begun to write bytes to the output stream. If a Connector is not correctly terminating the HTTP response or taking an excessive time to process the login request, then this can cause issues under load.
You can avoid issues by having your API endpoint write login data and completely close the connection as quickly as possible. You can load test your Connector using FusionAuth’s load testing framework or any other HTTP based load testing framework. Additionally, ensure the API endpoint is sized correctly and not starved of resources. You should return the appropriate status code and data as quickly as possible. Using the correct status code for each response ensures that FusionAuth handles the response appropriately.
Add Database Indices#
If you are querying a database to determine whether a user can authenticate, use database tooling such as explain plan and make sure that appropriate indices have been added.
Disable Logging#
Turning on the Connector’s Debug Enabled field during development is useful for troubleshooting. However, once you deploy a Connector to production, enable debugging only when troubleshooting. Debugging writes to the System -> Event Log and this causes additional load on the database.
Perform Optional Actions Out Of Band#
Your connector may need to do certain other tasks after a successful login occurs. This could include calling APIs or sending messages. If these actions don’t affect the result of the authentication, have these take place after a response has been sent to FusionAuth.
One way to accomplish this is to use a queue to store relevant data, which can then be read later by a different process.
Load Test#
You can load test your connector using a staging environment and the Login API. Configure the tenant to use your connector, create users in your system, and use a load testing tool to make repeated login requests of FusionAuth through your connector.

